Difference between revisions of "Hacking security"
| Line 52: | Line 52: | ||
====Facebook and Amazon==== | ====Facebook and Amazon==== | ||
In 2019, hundreds of millions of users were affected by a Facebook data breach involving Amazon's cloud service. This was caused by two third-party app developers using the software for their applications, and users' account names, passwords, friends, photos, and other information were exposed. Facebook is now under investigation regarding its deals with other electronic companies that could be involved in the data breach. <ref> Silverstein, Jason. "Hundred of millions of Facebook user records were exposed on Amazon cloud server." 4 Apr 2019. CBS News. https://www.cbsnews.com/news/millions-facebook-user-records-exposed-amazon-cloud-server/.</ref> | In 2019, hundreds of millions of users were affected by a Facebook data breach involving Amazon's cloud service. This was caused by two third-party app developers using the software for their applications, and users' account names, passwords, friends, photos, and other information were exposed. Facebook is now under investigation regarding its deals with other electronic companies that could be involved in the data breach. <ref> Silverstein, Jason. "Hundred of millions of Facebook user records were exposed on Amazon cloud server." 4 Apr 2019. CBS News. https://www.cbsnews.com/news/millions-facebook-user-records-exposed-amazon-cloud-server/.</ref> | ||
| + | |||
| + | ===Target=== | ||
| + | In 2013, discount retailer, Target, was hacked and the CEO wrote to his customers explaining what had happened and greatly apologizing for the breach that Target went through. This data breach occurred during the holiday season, one of the busiest times of the year for Target <ref> Pigni, Frederico, "Targeting Target with a 100 million dollar data breach," Journal of Information Technology Teaching Cases, https://journals.sagepub.com/doi/abs/10.1057/s41266-017-0028-0 </ref>. A lot of the attacking occurred during Black Friday as well. The hackers stole data, specifically credit card information, of roughly 70 million customers. These hackers were able to access customer’s names, credit card numbers, expiration dates, and card verification value. Target lost millions of dollars through this and their share values have decreased significantly <ref> McGrath, Maggie, "Target Data Breach Spilled Info On As Many As 70 Million Customers," Forbes, https://www.forbes.com/sites/maggiemcgrath/2014/01/10/target-data-breach-spilled-info-on-as-many-as-70-million-customers/#73502a97e795 </ref>. | ||
==Ethical Issues== | ==Ethical Issues== | ||
Revision as of 08:14, 16 April 2019
Hacking security is the invasion of an individual's privacy through a technological medium. The definition of hacking security is derived from the definition of hacking, referring to the unauthorized intrusion into a computer or a network, and the definition of security, the state of being defined as a state free from danger or threat.[1]
This invasion can expose important information about an individual's identity including financial, health, or personal data. Alessandro Acquisti, Professor of Information Technology and Public Policy at Carnegie Mellon University, states that as information friction decreases in the infosphere, secrets can no longer be kept, because individuals will constantly be exposed to more exposure online.[2] Therefore, hacking security has become easier as information technology advances and informational flows of technology increase. Information exposed online through hacking security, can have detrimental effects on an individuals personal and professional or academic lifestyles.
Contents
History
The term "hacking" originated at the Massachusetts Institute of Technology (MIT) in the mid-1950s and the original intent of the term was " to describe technology-based practical jokes played at the school [MIT]". The computers in use at that time were large mainframe computers, which had limited functions and long processing times. Programmers would design "hacks" as shortcuts to adjust and improve computer operating systems and applications. [3]
In the 1960s and 1970s, engineers, such as Steven Wozniak and Ralph Barclay, developed a device that could "hack" the old analog telephone systems by creating a certain frequency sound. The "Blue Box" produced a 2600-hertz frequency, which analog phone system were programmed to register in order to connect users to a line. Hackers used the Blue Box to access free long-distance calls. Wozniak, along with his friend and future business partner, Steve Jobs, began to produce larger quantities of the Blue Box and commercialize it, which was their first partnership that progressed towards the creation of Apple, Inc. [4]
As the computer industry started to become established in the 1980s and 1990s, many of the original hackers of academia started to apply their abilities to the manipulation of hardware and technology systems and became exceedingly innovative coders constantly searching for knowledge and information through computer programming. [5]
In the early 1980s, some hackers provided a dangerous threat but hackers did not have the negative connotation that they do today. Once hackers became more synonymous with "hacking" into unauthorized sites and the criminalization of hacking started evolving, the concept of hacking security emerged as counteraction. With the intelligence and skills that hackers possess, security hackers are able to retrieve information from many sites in cyberspace through bypassing the specific security measurements and protocols within an informational database.[5]
In 1979-1983, various groups of teenage hackers were apprehended by the FBI and tried on federal crimes of hacking into the computer systems of large companies and organizations. In 1983, a group of six Milwaukee teenagers, known as the "414s," were arrested by the FBI for hacking into over 60 computer systems, including those of Los Alamos National Laboratory, Sloan-Kettering Cancer Center, and the Security Pacific Bank. [6] That same year, a group of 15 hackers based all over the country, called "The Inner Circle," had their homes in California, New York, and Michigan raided by the FBI in a coordinated plan for hacking into computer networks. The Inner Circle hacked into the computer network system, GTE Telemail and Telenet, which hosted companies like Coca-Cola, Raytheon, Citibank, and NASA, as well as the Arpanet. The group would change administrator passwords, account names, and delete emails. Since there did not exist any comprehensive national hacking laws at the time, their arrest prompted a national initiative to better police cybercrime and computer hacking. [7]
In 1986, as a response to the computer hacking activities of 414s, the Inner Circle, and other hacking groups and individuals, Congress passed the Computer Fraud and Abuse Act and the Electronics Communications Privacy Act. These legislation criminalized the act of hacking, such as the unauthorized entry into computer systems and networks, and provided data privacy protections.
Types of Attacks
There are a number of different tactics hackers can use to meddle with networks, systems, and servers. These tactics give hackers the ability to access networks and obtain the personal information of individuals. Hacker security infiltration tactics include SQL injection, cross-site scripting, malware, man-in-the-middle, phishing, doxxing, and zero-day exploit. They are described below:
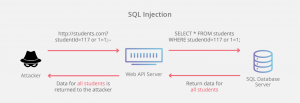
SQL Injection: Hackers use SQL injections in order to take advantage of systems with unsecure databases which use SQL as their framework. By using the search bar or login bar on sites with poor security, hackers can type SQL code into the search bar which is then executed on the system. The systems will interpret what should be data as code and will execute it within their framework. Hackers can thus use this tactic to retrieve all of the information within a database which they should not have access to.
Cross-Site Scripting: Cross-site scripting is another tactic hackers use to take advantage of websites that fail to cleanse input to their site. Similar to an SQL Injection, hackers can enter code into search or login bars on a website which will then be executed as the servers interpret the data entered on their site as code which should be executed on their systems. Hackers can make use of this tactic in order to steal information from clients. Most notably, hackers are able to get the cookies of other users and impersonate them on certain websites.
Malware: Examples of malware include software, spyware, viruses, bugs, worms, and ransomware. Malware is often able to permeate a network through links or email attachments that sometimes install dangerous software without the user’s knowledge. Malware can block access to the network, install additional software, transfer and send out secure data from the hard drive, and fry the system. Malware can also often duplicate itself in order to further spread the malicious software and make it more difficult to remove from a users computer or network.
Man-in-the-Middle (MitM): These cyberattacks are categorized by a hacker sneaking into seemingly-two-party transactions. This type of attack relies on the user believing that they are connecting to their intended party, when in reality the information is going to the "man-in-the middle" and then to the final destination. Attackers are essentially eavesdropping in an effort to steal information. Advanced hackers can use man-in-the-middle attacks in order to change the information sent between two parties and redirect users to a potentially malicious site. Common points of entry for these types of cyberattacks are public Wi-Fi networks that are not secure, and after malware has gotten into a network.
Phishing: Phishing usually happens through email when a hacker sends a fraudulent message that seems to be from a legitimate source but is not. It generally uses "click-bait" titles in order to get users to visit the malicious site due to their curiosity. Usually, the goal is to get credit card information or website login credentials or to have them open a file or link that will install malware on their computer.
Doxxing: When a user researches or obtains someone's private information and posts it publicly online. Information can be harvested using malware, publicly available social media, or online metadata such as an IP address.
Cross-site Scripting: Similar to an SQL injection, segments of Javascript or other pieces of scripting code can be directly inserted into user interfaces. This code may then capture information that is held on a backend server or database.
Zero-Day Exploit: When a network’s vulnerability is announced publicly allowing for attackers to find an exploit. Hackers using this method launch an attack before the owner of the network has the chance to create a solution or fix whatever created the vulnerability.
Targets and Attacks
Government Services
In 2018, sixty million users were affected due to the unsubstantial security measures on the USPS website. This security vulnerability exposed the USPS database that consisted of emails to phone numbers, mailing campaign data, social security numbers, possible credit card numbers, access to street addresses, and access to personal data of everyone who lived in the same household as who logged onto the site through the main user's account. This vulnerability also allowed requests to be made by the user's to change other user's account information such as email addresses and phone numbers. Although these issues were known, the organization took a year to resolve this data breach.[8]
Safety Ethics
High vulnerability should not be expected from certain government informational systems, considering that USPS has access to personal data points which can lead to identity theft. This leads to concerns in ethics regarding safety in governmental measures within other branches of the government because it is possible for “hackers” to gain access to other branches of the government that may have a similar vulnerability. Most people wouldn’t have considered this being a potential situation as sending and retrieving mail is such a common day to day task. With USPS the most common concern would be worrying about important packages or mail sent to the wrong address and one will open that information. However, this rarely occurs and it's taken seriously as its a federal offense to open someone’s mail or packages as it’s a matter of privacy. In other words, it was least expected that this situation would occur and the lack of timing and care for handling this situation. Contrasty, using USPS alone is a higher security threat, since it is possible for security hackers to break in and retrieve personal information from the database.
Healthcare
Healthcare companies are easy targets for hacking because its maximized vulnerability stemming from a lack of IT investment and training is information systems and the value of the data. Since companies only spend 3% of their IT budget on security[citation needed] and a majority of security breaches come from internal organization intrusion, it can easily take weeks or months before an organization realizes there is a data breach although there are security measures that are put in place to alleviate the effects of internal threats. This gives hackers a large time frame to access as much information as they want or need. The type of information contained in medical documents, such as a PHI or PII, is highly accurate and valuable data containing social security numbers and dates of birth which can be sold on the black market for upwards of $20,000.[9]
One would assume that healthcare companies would contribute more funds towards security as there is so much prevalent information that both medical professionals and clients receive and share. It makes one wonder why these companies are still vulnerable and not respecting the idea of anonymity and keeping information discreet. Most people wouldn’t want their medical conditions or health-related information exposed the public as they may be embarrassed or are hiding it for professional or personal reasons. Example, one may not want their job to know they are battling cancer in fear of losing their job and not having financial security for the medical treatments.
It’s best for people to be aware and concerned that healthcare companies are easy targets. So many people rely on healthcare regardless if services are obtained at a clinic or hospitals or local medical centers, these attract a large population, especially in United States. People are vulnerable and not only will their medical information be exposed it is also their unpaid or extensive healthcare bills may be shown as well. This can look bad on the person financially in terms of current or potential employment.
Personal Accounts
Yahoo
In 2013, there was a data breach that affected all three billion Yahoo! users around the world, leaving the users' data in a vulnerable state. Two additional attacked occurred in 2014 and 2016. This caused users' personal information, including names, email addresses, telephone numbers, birth dates, and some encrypted security questions and answers.[10] This caused multiple lawsuits to be filed against Yahoo! from multiple countries.
Facebook and Amazon
In 2019, hundreds of millions of users were affected by a Facebook data breach involving Amazon's cloud service. This was caused by two third-party app developers using the software for their applications, and users' account names, passwords, friends, photos, and other information were exposed. Facebook is now under investigation regarding its deals with other electronic companies that could be involved in the data breach. [11]
Target
In 2013, discount retailer, Target, was hacked and the CEO wrote to his customers explaining what had happened and greatly apologizing for the breach that Target went through. This data breach occurred during the holiday season, one of the busiest times of the year for Target [12]. A lot of the attacking occurred during Black Friday as well. The hackers stole data, specifically credit card information, of roughly 70 million customers. These hackers were able to access customer’s names, credit card numbers, expiration dates, and card verification value. Target lost millions of dollars through this and their share values have decreased significantly [13].
Ethical Issues
Anonymity
Anonymity, defined as inability to coordinate some known trait(s) with other traits of the individual such that the person can’t be identified. Many people in the US do not have the flexibility of online anonymity. Many of the cyber attacks are examples that reflect that people are no longer anonymous or have a minimum amount of other individuals who can gain access to their personal information. Because of the lack of, or limited security measures across many organizations and companies, this has led to the vulnerability and exposure of personal information more prevalent.
It is clear based on data breaches that occurred for the US Postal Services and Healthcare companies reflect how rare anonymity is. Exposure of social security numbers will potentially lead to many identity thefts which often take a long time to recover from. Due to the exposure from the data breach, it’s possible that more than one person will have that identity which makes it that much harder to track down the person who actually “stole” one’s identity.
Privacy
Alessandro Acquisti shares how there is no such thing as hiding your secrets or being anonymous because of our online era [14].The truth is; from having an image of a person using facial recognition, finding a name and public information about that name and person can form into non-publicly available information even the more sensitive information. Example, using one’s image found on their Facebook account or an app that uses phone’s internal camera taking images of the user and the information shared on Facebook led to more help for determining their social security number. With these tools, there is a 27% chance of determining their first five SSN digits within four attempts. This is just one of his many experiments in regards to anonymous and how to gather information to uncover their information.
Evidently, this tool is clever and innovative yet alarming. This is something that should concern many people as it allows people to use simplified information to their advantage. This is beyond unethical and one would think that people would spend more time and effort into improving online security. One may wonder should people not post anything at all whereas others wonder what is even allowed to post online. Some may wonder if social security numbering policy may need to change so there is barely any “margin” to guess its number after multiple tries. It may need to get more complicated by having a combination of numbers, letters, and characters to limit these unethical issues.
Based on Acquisti’s claims in regards to how it’s becoming easier to discover more personal information about people. However, these data breaches don’t help considering we are already vulnerable to these security concerns. These data breaches along with the online presence of people make it that much harder for people to remain anonymous or limit their anonymity from the least amount of people as possible. One can only hope that online security will improve so that people remain anonymous if any at all.
As technology advances and more inventions are brought up, more threats of privacy invasion arise. Technology created to advance subjects such as health or education can hold the risk of hackers invading three of the four levels of privacy of the technology's users; mental, decisional, and informational [15]. The mental privacy of a user is invaded by hackers if there is a manipulation of a user's personal details that can affect their lives in the real world. Decisional privacy can be affected if there is an intrusion of private documents, like healthcare for example, and an alteration of a user's data affecting very personal decisions. Last, a user's informational privacy can be affected by a hacker as there can be a breach to personal and sensitive information on the user.
Conclusion
Overall, one can suggest that it's prevalent for companies to become more serious in terms of online security as one will have personal information that can potentially not be retrieved once its been exposed. It’s necessary that companies maximize their budget and efforts to ensure the safety of their online users to avoid or limit the number of data breaches if this is possible. This would be useful as people are already sharing minimal information online with the lack of awareness that no one is truly anonymous and there is a small chance of one finding more personal information about them.
References
- ↑ What is Hacking? Technopedia. https://www.techopedia.com/definition/26361/hacking.
- ↑ “The 4th Revolution: How the Infosphere Is Reshaping Human Reality.” The 4th Revolution: How the Infosphere Is Reshaping Human Reality, by Luciano Floridi, Oxford University Press, 2016, pp. 101–128.
- ↑ Devitt, Michael, "A Brief History of Computer Hacking," Dynamic Chiropractor, https://www.dynamicchiropractic.com/mpacms/dc/article.php?id=18078
- ↑ Hackett, Stephen. "Concerning Steve Wozniak's Blue Boxes," 512 Pixels, https://512pixels.net/2018/03/woz-blue-box/
- ↑ 5.0 5.1 A Brief History of Hacker Culture. Cyber Security Masters Degree.org. https://www.cybersecuritymastersdegree.org/a-brief-history-of-hacker-culture/
- ↑ Stori, Will. "The kid hackers who starred in a real-life WarGames," Telegraph, https://www.telegraph.co.uk/film/the-414s/hackers-wargames-true-story/
- ↑ Novak, Matt. "The Untold Story of the Teen Hackers Who Transformed the Early Internet," Gizmodo, 4/14/16, https://paleofuture.gizmodo.com/the-untold-story-of-the-teen-hackers-who-transformed-th-1770977586
- ↑ Liao, Shannon. USPS took a year to fix a vulnerability that exposed all 60 million users' data. 22 Nov 2018. The Verge. https://www.theverge.com/2018/11/22/18107945/usps-postal-service-data-vulnerability-security-patch-60-million-users
- ↑ Alford, Allan. Why Hackers Love Healthcare. 26 April 2018. DARKReading. https://www.darkreading.com/endpoint/why-hackers-love-healthcare/a/d-id/1331537
- ↑ Brodkin, Jon. "Yahoo tries to settle 3-billion-account data breach with $118 million payout." 10 Apr 2019. Ars Technica. https://arstechnica.com/tech-policy/2019/04/yahoo-tries-to-settle-3-billion-account-data-breach-with-118-million-payout/.
- ↑ Silverstein, Jason. "Hundred of millions of Facebook user records were exposed on Amazon cloud server." 4 Apr 2019. CBS News. https://www.cbsnews.com/news/millions-facebook-user-records-exposed-amazon-cloud-server/.
- ↑ Pigni, Frederico, "Targeting Target with a 100 million dollar data breach," Journal of Information Technology Teaching Cases, https://journals.sagepub.com/doi/abs/10.1057/s41266-017-0028-0
- ↑ McGrath, Maggie, "Target Data Breach Spilled Info On As Many As 70 Million Customers," Forbes, https://www.forbes.com/sites/maggiemcgrath/2014/01/10/target-data-breach-spilled-info-on-as-many-as-70-million-customers/#73502a97e795
- ↑ Acquisti, Alessandro. What will a future without secrets look like? June 2013. TED. https://www.ted.com/talks/alessandro_acquisti_why_privacy_matters/up-next
- ↑ Floridi, Luciano. Ethics after the Information Revolution. pp 102-103. 2014.