Difference between revisions of "Tor"
| Line 4: | Line 4: | ||
==Overview== | ==Overview== | ||
| − | Tor software is a free downloadable and open source browser for Windows, Mac, Linux/Unix, and [[Android]] <ref> https://www.torproject.org/</ref>. | + | Tor software is a free downloadable and open source browser for Windows, Mac, Linux/Unix, and [[Android]] <ref> https://www.torproject.org/</ref>. The name "Onion Routing" refers to the specific way the data is encrypted in various layers. It works by preventing traffic analysis of packets being sent from the user's computer. Tor routes the packets through a route that is hard to follow for trackers, and periodically erases the online 'footprint' <ref name="tor" />. The packets take a route through the computers of various volunteers who have [https://www.torproject.org/download/download.html.en downloaded] Tor and set it up as a relay. Tor uses the same circuit for connections for 10 minutes to ensure privacy and security<ref name="tor" />. |
| + | |||
| + | While Tor is able to scramble data through its routes to ensure that user's packets are anonymous, Tor does nothing to monitor attempts to identify traffic entering the site, providing a means of identification and accountability for interested parties. | ||
[[File:htw1.png|200px|thumb|right|Information graphic on how Tor works]] | [[File:htw1.png|200px|thumb|right|Information graphic on how Tor works]] | ||
Revision as of 19:46, 16 December 2011
Tor (The Onion Router) is a web browser that uses a distributed network of relays run by volunteers all around the world to enhance privacy online [1]. It is used for many different types of projects, all for which privacy is a major concern. Tor also lets users publish web sites and other services without needing to reveal the location of the site [2].Overview
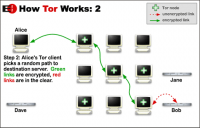
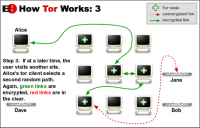
Tor software is a free downloadable and open source browser for Windows, Mac, Linux/Unix, and Android [3]. The name "Onion Routing" refers to the specific way the data is encrypted in various layers. It works by preventing traffic analysis of packets being sent from the user's computer. Tor routes the packets through a route that is hard to follow for trackers, and periodically erases the online 'footprint' [2]. The packets take a route through the computers of various volunteers who have downloaded Tor and set it up as a relay. Tor uses the same circuit for connections for 10 minutes to ensure privacy and security[2].
While Tor is able to scramble data through its routes to ensure that user's packets are anonymous, Tor does nothing to monitor attempts to identify traffic entering the site, providing a means of identification and accountability for interested parties.
Uses of Tor
Tor is used to improve privacy on the Internet by individuals, journalists, companies, and the government [2]. Individuals can use Tor to access content blocked by local internet providers, as well as browse the internet with privacy and security. Journalists use Tor to communicate more safely with whistleblowers and dissidents [2]. Companies use the service to allow their workers to connect to their home website while they're in a foreign country, without notifying everybody nearby that they're working with that organization[2]. The government has implemented the use of Tor in open source information gathering, including a branch of the U.S. Navy [2]. Due to the private nature of Tor, it is also used by criminals for uses such as assassination markets, drug trafficking, password cracking discussion, and child pornography.
Ethics
The anonymous nature of Tor makes it a place for criminal activity to happen on the internet. The approach the Tor website takes on this issue is that "Criminals can already do bad things", and "Tor aims to provide protection for ordinary people who want to follow the law. Only criminals have privacy right now, and we need to fix that." [4]. The platform itself is not meant for criminal activity, as it does allow for moral action by users. The ethical use of Tor would be to use it to keep information safe that could be tracked otherwise. This includes the use by journalists to keep informants safe, as well as activist groups who need to stay anonymous or face arrest. The Tor site also mentions that individuals also use Tor for socially sensitive communication: chat rooms and web forums for rape and abuse survivors, or people with illnesses [2]. The issue focuses mainly about online privacy, in this case an extreme case of it. It is difficult for the government to track criminals who use Tor for illegal activity, which could be argued to be a reason that it is ethically wrong. Meanwhile, it does serve moral purposes, and in itself is not a morally wrong object.