Stuxnet Trojan
|
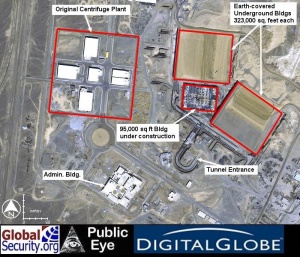
Stuxnet is the one of the most complex computer worm to date. This worm targeted and destroyed a real-world infrastructure and as long as a worm remains undetected, attackers can steal information, halt production, and compromise the safety of workers. Most notably, this sophisticated piece of malware shut down 1,000 IR-1 centrifuges at the Fuel Enrichment Plant in Natanz, Iran[3].1 This worm was the first of its kind to not only include malicious STL (Statement List), complicated assembly line code, but also include programmable logic controller (PLC) rootkit, which hid the code[4]. Because of the advanced technologies of rootkit, Stuxnet went unnoticed while, with STL code, infecting Windows systems in search for industrial control systems. With PLC/STL rootkit giving Stuxnet almost full coverage, over 60% of Iran became infected in a relatively short amount of time[5]. Among the many things that make Stuxnet unique is the fact that it contains 50 times more information in the code than a typical virus [6]. People speculate many reasons why this attack occurred and the reasons why, however a unanimous decision has yet to be reached.
Former National Coordinator for Security, Infrastructure Protection and Counter-terrorism Richard Clarke confirmed U.S.-Israeli cooperation on Stuxnet. Sources such as the New York Times suggest that Israel’s role was more significant due to a file buried within the Stuxnet worm that contained an indirect reference to Esther, the biblical heroine in the struggle against the genocidal Persians. However, Clarke claims that there was only some minor Israeli role in the attack and that it was predominantly conducted by the U.S. government. [7]
Contents
History
The code name, “Olympic Games” is what Stuxnet was referred to by cyber officials at the Pentagon[8]. The actual name “Stuxnet” was derived from keywords in the code[9]. Stuxnet was discovered in June 2010 by VirusBlokAda, a security firm based in Belarus[10]. On June 17th, 2010, two new malware samples were found that were capable of infecting a Windows 7 machine which ultimately led to the destruction of centrifuges[11]. The centrifuges, where were located in Natanz, Iran, were housed in bunkers 1.8 meters tall and 10 centimeters in diameter. These centrifuges are important because they gradually increase the proportion of uranium-235. The centrifuges were configured to run between 800-1400 Hz[12].
Implementation
There are two theories as to how Stuxnet enters a system; either through a USB drive or by sharing networks between printers[13]. In the first situation, once the infected USB drive is inserted, shortcut files are immediately opened, and programs are executed (5). Shortcut files, link to icons that in turn link to a certain executable program. For Stuxnet to work, the computer needs to have some sort of display icons so it can immediately start infecting[14]. The second possibility of infection would be an instance where Stuxnet exploits a hole in the Windows printing software. RPC is a service that allows two computers to interact, but when left unsecured, can be hacked and was improperly secured. This could have allowed Stuxnet to break into the main computer and spread to the network[15].
Windows
Stuxnet was able to enter Windows by using digitally signed certificates that contain encryption keys[16]. Without these keys, the computer flags the program as malware. The rootkit included two of these certificates which meant Stuxnet passed through the first line of defense on a Windows computer[17]. These private keys were stolen from JMicron and Realtek, which are technological companies based in Taiwan[18]. Once inside of Windows, the malware copies itself to open file share. Files are then copied from drive to drive because Stuxnet has the capability to find open shares and automatically propagate to those computers; it does not need any interaction[19]. Stuxnet automatically copies itself to any subsequent files that are shared, therefore infecting the next consumer on launch. If connected to the network, Stuxnet will update itself and spread this way through Windows.
Step 7 and PLC
Step 7, a product from the data base software company Siemens, is used to program industrial control systems[20]. After building software on Step 7, the information is transferred over to PLC to implement the code and run the centrifuges or any other machinery. Stuxnet was able to invade PLC using the manufactures password from Siemens, which is considered a zero-day exploit[21] . Once in the PLC system, Stuxnet verifies that PLC controls at least 155 total frequency converters[22]. Consequently the Uranium Fuel Enrichment Plant uses 160 centrifuges, which could indicate this was a pointed attack.
Plan of Attack
Symantec Chief Architect Carey Nachenberg outlined the plan of attack[23].
- Downloads malicious logic onto PLC.
- Measures operating speed of frequency converters for 13 days, making sure it is 800-1200 Hz. This check confirms that these are indeed centrifuges.
- Raises the spin rate to 1410 Hz for 15 minutes.
- Sleeps for 27 days.
- Lowers the spin rate to 2 Hz for 50 minutes.
- Sleeps for 27 days.
- Repeat 3-6.
During steps 2 and 5, Stuxnet was able deceive the alert system by sending prerecorded data to the system management screens[24].
Damage
Changing the spin rate ultimately led to the centrifuges breaking down. The excessive centrifugal forced caused the aluminum tubes to expand (11). Different parts of the centrifuge came into contact with each other, destroying
References
- ↑ Anderson, Nate · (2012 [last update]) · Confirmed: US and Israel created Stuxnet, lost control of it | Ars Technica · arstechnica.com · 7 December 2012
- ↑ Sanger, David E. · (june 1, 2012) · Obama Ordered Wave of Cyberattacks Against Iran - NYTimes.com · The New York Times · New York Times · December 7, 2012
- ↑ Institute for Science and International Security Report, Did Stuxnet Take Out 1,000 Centrifuges at the Natanz Enrichment Plant?
- ↑ Virus Bulletin, An indepth look into Stuxnet
- ↑ Center for International Security and Cooperation - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ Center for International Security and Cooperation - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ Rosenbaum, R. (2012, April 01). Richard Clarke on Who Was Behind the Stuxnet Attack. Retrieved from https://www.smithsonianmag.com/history/richard-clarke-on-who-was-behind-the-stuxnet-attack-160630516/
- ↑ The Daily Beast - Why Was Stuxnet Attack Called Operation Olympic Games? | http://www.thedailybeast.com/articles/2012/06/10/why-was-stuxnet-attack-called-operation-olympic-games.html
- ↑ The Economist - A Worm in the Centrifuge | http://www.economist.com/node/17147818
- ↑ http://www.infoworld.com/print/137598
- ↑ Krebs on Security - Experts Warn of New Windows Shortcut Flaw | http://krebsonsecurity.com/2010/07/experts-warn-of-new-windows-shortcut-flaw/
- ↑ Krebs on Security - Experts Warn of New Windows Shortcut Flaw | http://krebsonsecurity.com/2010/07/experts-warn-of-new-windows-shortcut-flaw/
- ↑ ESET - Stuxnet Under The Microscope | http://go.eset.com/us/resources/white-papers/Stuxnet_Under_the_Microscope.pdf
- ↑ Krebs on Security - Experts Warn of New Windows Shortcut Flaw | http://krebsonsecurity.com/2010/07/experts-warn-of-new-windows-shortcut-flaw/
- ↑ ESET - Stuxnet Under The Microscope | http://go.eset.com/us/resources/white-papers/Stuxnet_Under_the_Microscope.pdf
- ↑ Stanford University - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ ESET - Stuxnet Under The Microscope | http://go.eset.com/us/resources/white-papers/Stuxnet_Under_the_Microscope.pdf
- ↑ ESET - Stuxnet Under The Microscop | http://go.eset.com/us/resources/white-papers/Stuxnet_Under_the_Microscope.pdf
- ↑ Stanford University - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ Siemans Automation - Building a Cyber Secure Plant | http://www.totallyintegratedautomation.com/2010/09/building-a-cyber-secure-plant/
- ↑ National Vulnerability Database - Vulnerability Summary for CVE-2010-2772 | http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2010-2772
- ↑ Stanford University - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ Stanford University - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/
- ↑ Stanford University - A Forensic Dissection of Stuxnet | http://cisac.stanford.edu/events/a_forensic_dissection_of_stuxnet/