Remote Access
Remote access, also known as remote desktop, is the ability to access a computer or device from any remote location.[1] Using remote access software installed on a computer, it is possible to gain full control of a secondary device, including running applications and accessing files. Remote access is typically used to allow employees to access company data or servers from different locations, but may also be used as a form of remote administration.[2]
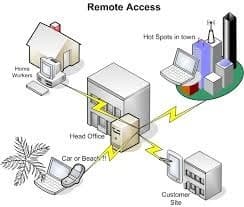
Contents
Requirements
Remote access software has become exponentially implemented since the start of the COVID-19 pandemic as a means of employees completing work while maintaining CDC social distancing guidelines. While individual applications function differently across devices, certain procedures must be followed that are uniform among all remote access platforms. [4] [5]
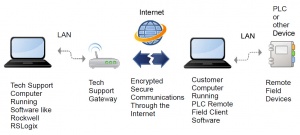
Remote Access Application
To access any device remotely the correct software must first be downloaded and installed on all of the devices involved in the remote access program. Remote desktop products are typically available in three models: hosted service, software, and appliance.[7]
Internet connection
A stable internet connection is needed in order to effectively use remote access features. Once the proper applications are installed, the software on the device can be opened and used to remote into the device of a user’s choice. The remote connection should be instant and continuous as long as neither computer is turned off or disconnected from the internet.
Implementation
Businesses
Remote Workers
Many businesses have taken advantage of the accessibility of remote access software to hire employees that do not live near their office of employment.[8] This has resulted in workers to accessing company servers and data across distances and time zones, allowing for a much broader and diverse workforce of employees. Similarly, remote administration has also been implemented by many businesses as a means of solving IT issues that arise. While previous models required on-site technical support, remote access applications have allowed support staff to access user devices from an external site. This, in turn, has streamlined the troubleshooting process as it allows for technical support workers to implement shutdown functions, access peripheral networks, and view and modify files and data stored on the user computer. [9]
Accessibility
One notable development in the accessibility of remote working is the potential for physically handicapped workers to work from home. It is estimated that only 40% of adults aged 25 to 54 in the United States with disabilities have a job. [10] This is mainly due to the barriers posed to people with disabilities in the conventional working environment. The use of remote access software has allowed for handicapped workers that are unable to physically enter a workplace environment to work from home instead.[11]
Education
Remote access schooling has become commonplace since the start of the COVID-19 pandemic. As of September 2020, students have used remote access software as a means of accessing school computers in order to access homework and educational material provided by the school district. Through remote access, programs that would otherwise require purchasing more licenses, such as video editing, animation, 3D designing, and other resources, are available to educators and students. [12] [13]
Education has also been facilitated through remote access learning by introducing one on one communication between students and teachers. Remote access software has been used by educators to remote into student devices in order to perform demonstrations for concepts directly onto a student's screen.
Associated Risks
Cyber Security
Remote access client devices generally have weaker protection than standard client devices. Many devices used with remote access software are not managed by the enterprise, resulting in no protection from existing firewalls and antivirus present on corporate-owned devices.[14] Additionally, client remote access devices often lack physical security controls. These devices are more commonly stored in bags or homes which are not afforded the same physical protection that is provided to devices stored in an enterprise building. Finally, remote access communications can be carried over untrusted networks, increasing the risk of losing private or personal data while communicating with a remote device.[15]
A brief overview of the risks associated with remote access software include:
- Monitoring of communications over a network
- Deployment of rogue wireless access points
- The exploitation of client devices through other practices designed to collect sensitive data (phishing, keylogging, etc.)
- Unauthorized access to resources by a third-party
- Loss of remote access devices to untrusted parties
Privacy
With the implementation of remote access software allowing employees to work from anywhere, employees are able to access intellectual property information from unsecured remote locations, outside perimeter-based security measures that have been implemented within office environments. As a result, these unsecured work environments can lead to inadvertent and nefarious unauthorized data leaks. As noted by data ethics experts, employees can use their remote access positions to leak or sell sensitive information to consumers. [17]
Steps taken to mitigate the unethical use of sensitive data by employees include using the REVISE framework in order to guide intervention policies. [18]
Malicious variants
Remote Access Trojans (RATs) are a form of malicious software that allows an outside source to gain unauthorized access to a user’s device in a similar manner to remote access software. Known for their longevity and ability to reemerge after time spent dormant, RATs are one of the most dangerous forms of cybercriminal activity. [19]
This malicious software type is bound by the same requirements as typical, legal remote software programs. However, RATs tend to be installed without user knowledge, avoiding firewalls and anti-virus scans in order to collect sensitive user data and control outside devices.
Notable examples of RATs include:
- Snort
- OSSEC
- Zeek
- Suricata
- Sagan
References
- ↑ Jackins, T. (2021, March 09). What is remote access? Connect to your computer from anywhere. Retrieved March 12, 2021, from https://www.splashtop.com/what-is-remote-access
- ↑ Rosencrance, L. (2020, April 14). What is remote access? - definition from whatis.com. Retrieved March 12, 2021, from https://searchsecurity.techtarget.com/definition/remote-access#:~:text=Remote%20access%20is%20the%20ability,they%20are%20physically%20far%20away
- ↑ Editor. (2019, August 24). Remote access Service (RAS). Retrieved March 12, 2021, from https://networkencyclopedia.com/remote-access-service-ras/
- ↑ Covid-19 guidance: Businesses and employers. (n.d.). Retrieved March 12, 2021, from https://www.cdc.gov/coronavirus/2019-ncov/community/guidance-business-response.html
- ↑ Written by Jennifer van der Kleut for NortonLifeLock. (n.d.). Remote computer access: What is it and what are the risks? Retrieved March 12, 2021, from https://us.norton.com/internetsecurity-how-to-remote-computer-access.html
- ↑ How it works. (n.d.). Retrieved March 12, 2021, from http://plcremote.net/how-it-works/
- ↑ Ken. (2019, April 23). How to ensure better productivity? Vpn access vs. remote access. Retrieved March 12, 2021, from https://remoteaccess.itarian.com/blog/how-to-ensure-better-productivity-vpn-access-vs-remote
- ↑ Is it time to let employees work from anywhere? (2020, March 04). Retrieved March 12, 2021, from https://hbr.org/2019/08/is-it-time-to-let-employees-work-from-anywhere
- ↑ FinSMEs. (2020, April 21). The benefits of IT support in a remote environment. Retrieved March 12, 2021, from https://www.finsmes.com/2020/04/the-benefits-of-it-support-in-a-remote-environment.html
- ↑ Stengel, G. (2020, April 20). Working from home opens the door to employing people with disabilities. Retrieved March 12, 2021, from https://www.forbes.com/sites/geristengel/2020/04/20/working-from-home-opens-the-door-to-employing-people-with-disabilities/?sh=6502eb5414bf
- ↑ For those with disabilities, shift to remote work has opened doors (video). (2020, October 27). Retrieved March 12, 2021, from https://www.csmonitor.com/Business/2020/1027/For-those-with-disabilities-shift-to-remote-work-has-opened-doors-video
- ↑ Jackins, T. (2021, February 24). Remote access in education - CLASSROOM, EdTech, and support. Retrieved March 12, 2021, from https://www.splashtop.com/remote-access-education-uses
- ↑ School Computer Labs Made Inaccessible by COVID-19 Generate Increased Demand for Splashtop Remote-Access Software, uk.advfn.com/stock-market/stock-news/83272466/school-computer-labs-made-inaccessible-by-covid-19.
- ↑ Lisa Ashjian Mar 11. “Secure Remote Access Explained.” AT&T Cybersecurity, cybersecurity.att.com/blogs/security-essentials/secure-remote-access-explained.
- ↑ “Security Concerns with Remote Access.” Https://Csrc.nist.gov/CSRC/Media/Events/HIPAA-Security-Rule-Implementation-and-Assurance/Documents/NIST_Remote_Access.Pdf, NIST, csrc.nist.gov/CSRC/media/Events/HIPAA-Security-Rule-Implementation-and-Assurance/documents/NIST_Remote_Access.pdf.
- ↑ “Corporate Firewall.” Corporate Firewall - an Overview | ScienceDirect Topics, www.sciencedirect.com/topics/computer-science/corporate-firewall
- ↑ Khan, Roomy. “Work From Anywhere Trend Intensifying Ethics, And Compliance Issues.” Forbes, Forbes Magazine, 10 Nov. 2020, www.forbes.com/sites/roomykhan/2020/11/06/work-from-anywhere-trend-intensifying-ethics-and-compliance-issues/?sh=4d734e412f38.
- ↑ Ayal, Shahar, et al. “Three Principles to REVISE People’s Unethical Behavior.” SAGE Journals, journals.sagepub.com/doi/full/10.1177/1745691615598512.
- ↑ “Remote Access Trojan Detection: Software & RAT Protection Guide.” DNSstuff, 2 Feb. 2021, www.dnsstuff.com/remote-access-trojan-rat.