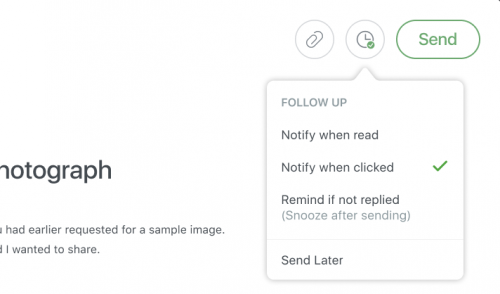
Read Receipts (Message-Delivery & Seen-Status Tracking)
A read receipt, or return receipt, is a notification, indicative of seen status, returned to the sender of a message once the receiver has opened said message. Often this technology is inaccurate, especially in emailing. Whether it's accurate or not, the tech can be intrusive of receivers' private information and presents an ongoing and widely disputed debate. Princeton researchers revealed in 2017 that there has been very little research done on email tracking, despite the vast focus on revealing the technology behind web tracking. Because of the lack of research and heavily debated methodology behind its use, this Wiki article explores the information publicly known on the subject. The following will reveal the gears and functionality behind message-delivery and seen-status tracking software and the legal, cultural, moral, and psychological implications of its use in various forms of digital messaging.
Contents
History
Instant Messaging's delivery tracking and SMS's receipt-sending software have been around for a long time, with email trackers going back even farther in history. As Guinness World Records points out, the first email correspondence was made in 1971 by Ray Tomlinson, a computer engineer, when he sent "QWERTYIOP or something similar" to another computer he was working on. Tomlinson successfully built the software while working for the United States Defense Department building a message service in ARPANET using Cambridge's early computer tech.[1] Long after this breakthrough, various parties began building web mail in 1993.[2] The introduction of web mail allowed for companies to add emailing to web browsers. Since web browser technology was so robust at the time, and would only continue to grow, email creators had a new toy—HTML. The addition of HTML, CSS, and other web programming technologies was a game changer for marketing and intelligence departments. These programs support image and file embedding on browsers. By writing and sending emails using these browser programs and only a tiny chunk of code, various government organizations, companies, and unidentifiable parties were able to privately create and implement a secret and intrusive method to track email data. This method was called Tracking Pixels and it is still used in email today. The tracking technology was unknown to the mass public until Hewlett-Packard, the global information and computer hardware company often referred to as HP, screwed up by inadvertently releasing their secret affairs in 2006.[3] HP partnered with a company named Read Notify who developed a powerful and reliable program that used 36 different methods to track information, a few of which used tracking pixels for email tracking. ReadNotify was used by HP to track a scandalous email leaked to press. The technology was revealed in HP's lawsuit that followed and spread shock amongst the tech community and email users that their private emailing habits could be tracked.
Meanwhile, SMS was born. iMessage read receipts (2011) Informed delivery (2014)
Technologies & How It Works
Delivery tracking is nowadays used in Instant Messaging (IM), Short Message Service (SMS) and Multimedia Messaging Service (MMS), but originally began with email tracking software.[4] Email tracking technology was limited to monitoring delivery status before the introduction of “seen”-status tracking. Depending on the platform used and method that receipts are fetched, other robust forms of data points can be obtained using more modern code that track the receiver’s Internet Protocol (IP) address. Beyond the status of whether the message has been seen by the receiver, the notification returned to the sender may include embedded information like reception time, the time that the message has been opened, and location data indicating the receiver’s continent, country, state, city, zip code, or even rough coordinates within a multi-square-mile radius of where the message was opened from your IP address and other embedded email information.[5]
Dependent on the platforms used in exchanging read receipts, tracking isn’t considered to be perfectly accurate. Some products function better than others, especially with internal end-to-end encryption like Apple iMessage, but other software, like email tracking, fails to scrape IPs and return the data successfully.
SMS/MMS & Instant Message Tracking
Email Tracking
- Reads one-pixel image
Reliability
- Reliable for iOS texting and Instant Messaging - Unreliability ties into legal
The Internet Engineering Task Force (IETF)is an organization that develops and regulates protocols for securely packaging and transporting messages across the Internet. The IETF indicates the lack of reliability and high fluctuation rate of tracking software’s success in Message Disposition Notification RFC 3798.
“MDNs may be forged as easily as ordinary Internet electronic mail and whilst they can provide valuable information to the mail user, they cannot be relied upon as a guarantee that a message was or was not seen by the recipient. Even if MDNs are not actively forged, they may be lost in transit.”
- Sources: (RFC 3798, IETF, https://datatracker.ietf.org/doc/html/rfc3798), (Use of Message Disposition Notifications, IBM, https://www.ibm.com/docs/en/b2b-integrator/5.2?topic=higher-use-message-disposition-notifications) Google explains that Gmail’s email tracking is not always reliable.
“Don't rely on receipts to certify delivery. Getting a read receipt doesn't always mean the recipient read your message. How a receipt works depends on which email system your recipient uses. For example, you may get a read receipt if a person using an IMAP-based email client marks your message as read, but doesn't open it. Some non-IMAP mobile email systems may not return receipts at all.”
Read receipts in email have multiple reasonings to fail. Read receipts may be deactivated by the internal software built by an organization to manage how email is received and sent. Other ways could be technical error in sending or receiving an email. Some email services allow the user to manage the settings and controls behind how read receipts are used and how certain data is tracked.
Here's an example from Google of a read receipt not functioning due to receiver's settings: Imagine that you send an email that contains a tracking pixel – a very tiny image inserted in the email to track emails. Your experience tells you that when the recipient opens the email, the pixel will get activated and you will be notified. But what you don’t know is that the email server of the recipient has the image preview function disabled, so when the recipient opens the email, the pixel won’t be activated.
- Sources: (Request or return a read receipt, Google, https://support.google.com/mail/answer/9413651?visit_id=637395923678980799-3760639549&hl=en&rd=2)
What are the stakes of an unreliable read receipt?
SMS/MMS & Instant Message Tracking
Products & Implementation
Apple iMessage
In October of 2011, Apple released iMessage. The messaging platform uses Instant Messaging over Wi-Fi or texting over cellular-data networks.[6] iMessages are sent and received using end-to-end encryption that even Apple itself cannot decode in conversations. When texting non-Apple phones, messages will turn green—the default is blue—to indicate that messages are being sent via non-encrypted SMS/MMS texting. To use SMS/MMS on an Apple device, one needs a text-messaging plan, but not with Instant Messaging. While not all mobile phone users have iPhone’s closed iMessage platform, read receipts only function on iMessage’s Instant Messaging—with blue text bubbles—when sent to other iPhones. Read receipts are an optional implementation that must be activated by the receiver to reveal to the sender that they have read the sent message.
- Sources: (What is the difference between iMessage and SMS/MMS?, Apple, https://support.apple.com/en-us/HT207006#:~:text=If%20you%20aren't%20using,need%20a%20text%2Dmessaging%20plan.)
Facebook Messenger
Gmail
Gmail Help: Request or return a read receipt
Newton Mail
Superhuman
Legal
"If you were to write a letter on paper, seal it in an opaque envelope and mail it, the content is legally protected. No one can open that envelope without a search warrant issued on probable cause.
This is NOT true for email or any other form of digital communications except the content of telephone calls. Legally, they are naked."
- Are read receipts legally binding? “Read receipts aren't a reliable way to prove email delivery and obviously they don't constitute legal evidence. … Email Tracking: Read Receipts Are Not Reliable Proof To Prove Email Delivery. Relying on read receipts to prove email delivery or that your message has been read isn't recommended. In fact, Google advises not to rely on read receipts for certifying the delivery of an email.” - Sources: Email Tracking: Read Receipts Are Not Reliable Proof To Prove Email Delivery
Privacy Concerns
Email alone can provide a decent amount of information about a user. By collecting one's IP address, an email can provide enough data to then be used to connect and access other data in the sending-party's records. Check your own IP address on iplocation.net to get a glimpse of what your IP alone can tell others about you. On top of collecting information from email, specifically through IP addresses, many external programs may also be used to identify and connect personal information. This is most commonly done via partnerships with other parties.
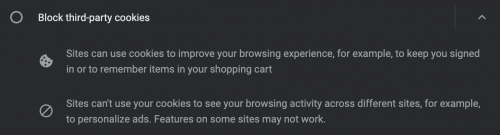
What some may consider an egregiously sized breach of privacy, a significant amount of private, identifiable information may be obtained from users depending on the existence of external partnerships with the sender of an email. Browsers collect cookies. Apps collect other forms of data. Some of the cookies placed in browsers may be fully accessible to be collected by other organizations. Khan Academy explains the two common forms of data placing and fetching in browsers called first-party and third-party cookies. First-party cookies are used by the visited site in a browser when visiting said site directly. Third-party cookies may be placed in someone's browser by sites partnered with the visited site which can provide trackable data on user history to these partnered websites.[7] If other companies or suspicious individuals have information-sharing agreements with the interacted website, third-party cookies may be sent to a user's browser cache and provide this tracking data to partnered parties to then be tied to other data.[8] These agreements can grant others access to a user's information using external processes to email sharing called UID2. UID2 is a series of protocols that can be used to collect, analyze, and share users’ personally-identifying information that can be used in connecting email addresses, IP addresses, cookies, and other identifiable technologies that identify users and their other private information.[9] Correlations of data on a single user can then be made between third-party, cookie-placing agreements from a browser or app and the pixel-tracking and IP-scraping technologies installed in the email a user may open. Unless cookie collection is turned off in browsers, a firewall is used, and the user has tracking turned off using a robustly built email client, the user has no control over who can breach their privacy by collaborating externally to merge identifiable data and collect information about them.
The best method to prevent the majority of one's data from being collected, analyzed, and connected together to develop a persona of data is to use a VPN, blocking IP collection on email and browsers and corrupting much—not all—cookie collection.
Cultural Effects (maybe change this?)
Cross-Platform Exclusion
Psychological Implications
Emotional & Cognitive Engagement
How Do Instant Messages Reduce Psychological Withdrawal Behaviors?—Mediation of Engagement and Moderation of Self-Control
Psychological Manipulation
• People killed themselves after being left on read • Jobs apps, being left on read became more common
References
- ↑ "1971: First Ever Email," Guinness World Records (Rachel Swatman), https://www.guinnessworldrecords.com/news/60at60/2015/8/1971-first-ever-email-392973
- ↑ "How did email grow from messages between academics to a global epidemic?, The Guardian, https://www.theguardian.com/technology/2016/mar/07/email-ray-tomlinson-history
- ↑ "How HP bugged e-mail," CNET Tech (Joris Evers), https://www.cnet.com/tech/services-and-software/how-hp-bugged-e-mail/
- ↑ "What is SMS & MMS?," T-Mobile, https://www.t-mobile.com/resources/what-is-an-SMS
- ↑ "What does an IP address tell you and how it can put you at risk?" Norton, https://us.norton.com/internetsecurity-privacy-what-does-an-ip-address-tell-you.html#:~:text=What%20information%20does%20my%20IP,or%20other%20precise%20personal%20information.
- ↑ "What is the difference between iMessage and SMS/MMS?," Apple, https://support.apple.com/en-us/HT207006#:~:text=If%20you%20aren't%20using,need%20a%20text%2Dmessaging%20plan.
- ↑ "Web Cookies," Khan Academy, https://www.khanacademy.org/computing/computers-and-internet/xcae6f4a7ff015e7d:online-data-security/xcae6f4a7ff015e7d:user-data-tracking/a/web-cookies
- ↑ "How to Surf the Web Anonymously," How Stuff Works, https://electronics.howstuffworks.com/how-to-tech/how-to-surf-the-web-anonymously.htm
- ↑ "After Cookies, Ad Tech Wants to Use Your Email to Track You Everywhere," EFF, https://www.eff.org/deeplinks/2021/04/after-cookies-ad-tech-wants-use-your-email-track-you-everywhere