Difference between revisions of "Quantum Computing"
(minor edits on wording and paragraph structure) |
|||
| Line 1: | Line 1: | ||
Quantum computers are a developing technology that has ramifications in any sector that is reliant on processing power or cryptographic security. | Quantum computers are a developing technology that has ramifications in any sector that is reliant on processing power or cryptographic security. | ||
| − | + | Quantum computers possess exponentially stronger computational power due to the use of quantum bits, or qubits, which double the processing power of each bit used because of a phenomenon known as superposition. This method of processing can lead to faults in computer security that are currently indefensible. There are ethical concerns with the capacity for such large breaches in data security to occur when quantum processing power is only accessible to the select few entities or individuals that have the means of developing and utilizing quantum computing. | |
== '''History''' == | == '''History''' == | ||
Revision as of 09:44, 30 March 2021
Quantum computers are a developing technology that has ramifications in any sector that is reliant on processing power or cryptographic security. Quantum computers possess exponentially stronger computational power due to the use of quantum bits, or qubits, which double the processing power of each bit used because of a phenomenon known as superposition. This method of processing can lead to faults in computer security that are currently indefensible. There are ethical concerns with the capacity for such large breaches in data security to occur when quantum processing power is only accessible to the select few entities or individuals that have the means of developing and utilizing quantum computing.
Contents
History
Moore's Law and the Quantum Fix
Classical computing power has been on an exponential increase over the past 50 years. Evidence of this can be seen using Moore’s Law [1], which states that “the number of transistors in an integrated circuit doubles about every two years.” This decrease in transistor size forces quantum mechanical action to be accounted for. Eventually, these transistors will become too small, meaning quantum tunneling[2] could limit the ability for Moore’s Law to continue. To overcome this, quantum computers instead manipulate qubits, rather than their classical counterparts’ use of transistors. Qubits[3] are the quantum equivalent of classical computer’s bits, where everything is represented in two states: ‘1’ and ‘0’, or ‘true’ and ‘false’. Unlike their bit counterparts, qubits are capable of being three states: ‘1’, ‘0’, and ‘both’ (or equivalently, ‘true’, ‘false’, and ‘both’). The resulting difference in computational power can be seen in any tree branching structure, like maze solving. Where a classical computer would have to check a path, return when its algorithm hit a dead end, and repeat until the correct end is reached, a quantum computer can instead check both routes concurrently until the end is reached [4]. Google’s quantum processor, Sycamore, “completed a task in 200 seconds that Google claimed would take state-of-the-art supercomputers 10,000 years to finish” [5]. This computational power has large implications in data security, as many cryptographically secure algorithms are based on the fact that their inherent mathematical assumptions are computationally taxing.
Quantum Solvable Cryptography
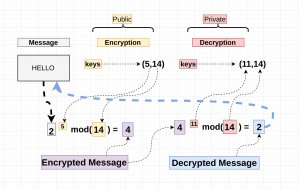
RSA[7] is a widely-used public-key cryptosystem which relies on the “factoring problem[8]” RSA allows for cryptographically secure communication because, on state-of-the-art classical supercomputers, the work it takes to generate a key from two prime numbers (what the users would do) is exponentially easier than the work it takes to factor the resulting number into its two primes (what an attacker would have to do to break RSA).
Step by Step RSA[9]:
1. Select two large prime numbers: P and Q
2. Calculate N and O where N = P * Q and O is (P - 1)(Q - 1)
3. Select an E where E is relatively prime to O
4. Find D where (E * D) mod O ≡ 1
5. Public Key: (E, N)
Private Key: (D, N)
6. To encrypt message x: x^E mod N
To decrypt message x: x^D mod N
With sufficiently high prime numbers, classical computers are currently incapable of breaking RSA encryption in polynomial time, but this is not the case for quantum computers. As a result of quantum computer’s computational power, the factoring problem is no longer sufficiently hard to be cryptographically secure. This lack of security will have large-scale implications as RSA encryption is a cryptographic primitive utilized in a large amount of HTTPS websites[10].
Ethical Concerns
International abuse of power
RSA is currently being utilized world-wide under the belief that it is cryptographically secure. There are cryptographers currently working to build post-quantum secure cryptography, but there is no countermeasure to quantum computing as of yet[11]. If one country has access to quantum computing before other countries have it, and there is no countermeasure in place, the post-quantum country has uninhibited access to a majority of the world’s internet traffic. Data kept secure by companies and governments utilizing currently cryptographically-secure algorithms like RSA are no longer viable, and without ethical guidelines in place to prevent abuse, the country with access to quantum factorization will be able to view large amounts of private information. Sensitive government information being transmitted between officials can be seen without their knowledge.
Government on citizen
Citizen data is protected from the government as channels of communication utilize commercial companies, so businesses like VPNs, Apple, Android, or any third party provider, are not required by law to give up incriminating data, or anything that citizens do not want the government to have. If the government were to have quantum computing capable of decrypting RSA computations, the citizens’ online traffic would no longer have to be requested from these companies, and instead could be immediately taken and viewed by the government. Without proper ethical guidelines to the use of quantum computing, internet use and the people’s compartmentalized data identities are at stake. Use of the internet is implicitly anonymous to an extent, so the deanonymization of it via quantum factorization would result in the people’s data identities being able to be pieced together. Quantum computers will withdraw the need for citizens or companies to consent to the government viewing online transmissions.
The Future
The creation of a broad use-case usable quantum computer would be an exponential step in computational power that the world does not have the proper infrastructure to account for. This comes with ethical concerns as there are currently little or no legislative defenses or guidelines to restrict the use of a power like this. The future of data security is reliant on whether or not quantum-secure cryptography is widely established before the creation of quantum computers.
References
- ↑ Britannica, The Editors of Encyclopaedia. "Moore's law". Encyclopedia Britannica, 26 Dec. 2019, https://www.britannica.com/technology/Moores-law. Accessed 26 March 2021.
- ↑ Britannica, The Editors of Encyclopaedia. "Tunneling". Encyclopedia Britannica, 24 Oct. 2016, https://www.britannica.com/science/tunneling. Accessed 26 March 2021.
- ↑ Holton, William Coffeen. "Quantum computer". Encyclopedia Britannica, 16 Aug. 2020, https://www.britannica.com/technology/quantum-computer. Accessed 26 March 2021.
- ↑ Bashuk, Mark. “Solving a Maze with a Quantum Computer.” ResearchGate, 2003, www.researchgate.net/publication/2190201_Solving_a_Maze_With_a_Quantum_Computer.
- ↑ “Quantum Supremacy Using a Programmable Superconducting Processor.” Google AI Blog, 23 Oct. 2019, ai.googleblog.com/2019/10/quantum-supremacy-using-programmable.html.
- ↑ Uk, Garciaj. “Simple Version of How RSA Works.” Hackernoon, 23 June 2017, hackernoon.com/how-does-rsa-work-f44918df914b.
- ↑ Simmons, Gustavus J.. "RSA encryption". Encyclopedia Britannica, 3 Aug. 2012, https://www.britannica.com/topic/RSA-encryption. Accessed 26 March 2021.
- ↑ Rembert, Ludovic. “Prime Factorization.” Privacy Canada, 25 Nov. 2020, privacycanada.net/mathematics/prime-factorization/.
- ↑ Honeyman, Alexander. "Public Key Cryptography." 19 Sept. 2019, University of Michigan, Michigan. Class lecture.
- ↑ B, Bobby. “How Does HTTPS Work? RSA Encryption Explained.” TipTopSecurity, 10 Sept. 2017, tiptopsecurity.com/how-does-https-work-rsa-encryption-explained/.
- ↑ Castellanos, Sara. “Quantum Computing Scientists Call for Ethical Guidelines.” The Wall Street Journal, Dow Jones & Company, 1 Feb. 2021, www.wsj.com/articles/quantum-computing-scientists-call-for-ethical-guidelines-11612155660.