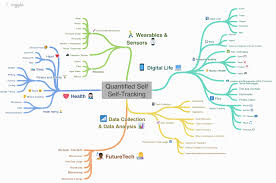
Quantified Self Movement
The Quantified Self (QS) refers to individuals that engage in keeping track of their daily activities systematically, in an attempt to better understand their bodies and their needs, ultimately seeking fulfillment. The data tracked can take many forms: it can be biological, physical, behavioral, or environmental information [1]. The QS movement relies on different self‐tracking tools, such as bracelets, smartwatches, sensors, fitness trackers or any other device that can measure biological attributes. A branch of the Internet of Things, QS focuses on the data generated by human bodies[2]. The movement became more structured as mobile apps dedicated to keeping track of sleep, mood, health related issues, and smart watches like Fitbit became available and now has international communities of self-trackers that focus on data sharing.
Founding and Origins
The Quantified Self was founded in 2007 by Gary Wolf and Kevin Kelly, two editors of Wired magazine, who felt that the rise of self-tracking in their San Francisco environment deserved a website and a place where enthusiasts could meet, share their self-tracking experiences, and discuss their findings. Since then, the group has expanded internationally and currently includes over 60,000 members across the globe, organized in over 200 groups that hold regular meetings, as well as two international conferences a year[3]. The explicit motto of the Quantified Self movement, branded as a tagline on its official website, is “self-knowledge through numbers."
Self-Tracking Practices
Self-tracking practices include the use of personal data-gathering apps, wearable devices, and data analysis tools to record patterns from daily activities, as well as the organization, visualization, and analysis of this data. Many of the most popular self-tracking apps and devices focus on health and fitness and productivity and time management. While some self-trackers develop their own tools for data collection and analysis, the most popular self-tracking activities are conducted using popular apps and platforms such as Apple HealthKit, Fitibit, GoogleFit, and RunKeeper (health and fitness tracking), Clue (menstruation tracking), MoodPanda (mental health tracking), and RescueTime and Toggl (productivity tracking). Health and fitness self-tracking covers a broad range of categories, such as hours slept, calories expended, food and water consumed, and steps taken. Many apps also enable integration between different platforms, thus allowing self-trackers to analyze correlations between, for example, fitness levels, and work productivity.
Dataveillance and Privacy
Digitized self-tracking is a form of dataveillance, or the watching of people using technologies that generate data, increasingly in digitized formats [4]. In the age of Quantified Self devices and analytics, informed consent for end users becomes even more crucial. Massive databases provide exhaustive pictures of users’ biometric statistics mapped to their geocoded locations. These reserves of information are too often siloed, with their company’s data practices hidden from the public[5]. Additionally, the QS community’s fondness for gamification and sometimes competition brings individuals’ data into intertwined relationships and configurations. The QS movement is driven by an enthusiastic desire to remove constraints to ubiquitous tracking, which could appear to conflict with the core principles of classic data privacy frameworks[6].
Personal Data Security
There are many significant issues concerning the security and privacy of the personal information that self-trackers upload to apps and other software. Data security is becoming increasingly more difficult to protect as ‘smart’ online objects connect with each other and share data, and as personal data are uploaded to cloud computing archives in increasingly large amounts[7]. Hackers can gain access to personal data at two key points: when these are being transmitted from one location to another, such as from a personal device to a cloud computing database; and when they are kept in databases[8]. If strong data encryption and authentication protocols are not employed, hackers are able to gain access to personal data more readily.
Communal Self Tracking
Communal self-tracking involves the consensual sharing of a tracker's personal data with other people, as a central feature of self-tracking practice. Notions of privacy are challenged and transformed by the interplay of personal information about the individual that is generated via self-tracking and the movement of this information into social media sites, into dedicated self-tracking platforms, or simply into the archives of the computing cloud, where it becomes open to access and can be seen by others. When self-tracking practices involve collecting and recording information on other people, then they may also involve sousveillance, either carried out deliberately or emerging as an unintended outcome of using these technologies. The use of digital self-tracking technologies blurs the spatial boundaries between public and private surveillance, bringing public surveillance into the domestic sphere but also often extending private surveillance out into public domains.
Exploitation of Self Tracking
The exploitation of people's personal information by second and third parties is significant because of the ways in which people's personal information has become valuable for third parties. The collection of personal data is now not only a mode of consensual, individually driven imperatives for self-improvement, but also an element of (sometimes illegal) commercial profiteering, population monitoring and governance. The movement of self-tracking cultures into commercial, managerial and government domains combines the rationalities of biocapital with those of the digital data economy[9]Biocapital involves the derivation of value from biological entities such as human bodies, while the digital data economy positions digital data objects as valuable. The burgeoning business of data harvesting and data brokering involves a process whereby companies are scraping the web for whatever they can find about people; in other words it involves the sale of the data that have been generated through the use of apps and other software[10]
Responses and Resistance
The ontological issues surrounding the data privacy field are complex, however the stopgap solutions to these problems are relatively simple. While people can no longer escape being the subjects of dataveillance, they can to some extent make choices about the self-tracking practices in which they may engage and about the devices they decide to use. They may seek out developers and manufacturers who are responding to consumers' concerns about data privacy and security. There have also been calls for the use of the policy of ‘privacy by design’ when developing digital devices. These discussions refer to the notions of the ‘user-centric internet’ and ‘controlled computing’, where people's personal data will be protected by the judicious structuring of information systems engineering, above the demands of those who wish to profit from or otherwise use these data[11].
References
- ↑ Swan, M. (2013). The Quantified Self: Fundamental Disruption in Big Data Science and Biological Discovery. Big Data, 1(2), 85-99. doi:10.1089/big.2012.0002
- ↑ Marcena, M. B., Wueest, C., & Lau, H. (2014, August 11). How safe is your quantified self? Retrieved March 25, 2021, from https://paper.bobylive.com/Meeting_Papers/BlackHat/Europe-2014/eu-14-Wueest-Quantified-Self-A-Path-To-Self-Enlightenment-Or-Just-A-Security-Nightmare-wp.pdf from Symantec System
- ↑ Show & Tell Projects Archive. (2016, April 14). Retrieved March 25, 2021, from https://quantifiedself.com/show-and-tell/?project=1121
- ↑ Dijck, J. V. (2013). Disassembling Platforms, Reassembling Sociality. The Culture of Connectivity, 24-44. doi:10.1093/acprof:oso/9780199970773.003.0002
- ↑ Lupton, D. (2013). The digitally engaged patient: Self-monitoring and self-care in the digital health era. Social Theory & Health, 11(3), 256-270. doi:10.1057/sth.2013.10
- ↑ Matarić, M. J. (2019). Human-Machine and Human-Robot Interaction for Long-Term User Engagement and Behavior Change. The 25th Annual International Conference on Mobile Computing and Networking. doi:10.1145/3300061.3300141
- ↑ Marcena, M. B., Wueest, C., & Lau, H. (2014, August 11). How safe is your quantified self? Retrieved March 25, 2021, from https://paper.bobylive.com/Meeting_Papers/BlackHat/Europe-2014/eu-14-Wueest-Quantified-Self-A-Path-To-Self-Enlightenment-Or-Just-A-Security-Nightmare-wp.pdf from Symantec System
- ↑ Ibid.
- ↑ Kitchin, R. (2011). Conceptualising Data. The Data Revolution: Big Data, Open Data, Data Infrastructures & Their Consequences, 3(11), 1-26. doi:10.4135/9781473909472.n1
- ↑ Lupton, D. (2013). The digitally engaged patient: Self-monitoring and self-care in the digital health era. Social Theory & Health, 11(3), 256-270. doi:10.1057/sth.2013.10
- ↑ Barrett, M. A., Humblet, O., Hiatt, R. A., & Adler, N. E. (2013). Big Data and Disease Prevention: From Quantified Self to Quantified Communities. Big Data, 1(3), 168-175. doi:10.1089/big.2013.0027.