Difference between revisions of "QR Codes"
m |
|||
| Line 1: | Line 1: | ||
| − | A QR | + | A QR (Quick Response) code is a unique, two-dimensional barcode.<ref>Encyclopedia Britannica. (n.d.). QR Code. In <i>britannica.com</i>. Retrieved March 18, 2020, from https://www.britannica.com/technology/QR-Code.</ref> It is a form of information technology that stores alphanumeric characters in the form of text or URLs, making it easy for smartphone users to be directed to a link provided by an organization or person. Barcodes only use horizontal information, whereas a QR code can contain information that is both horizontal and vertical <ref name="History">Stein, Adriana. (2020, January 1) How QR Codes Work and Their History. QR Code Generator. https://www.qr-code-generator.com/blog/how-qr-codes-work-and-their-history/</ref>. QR codes have become increasingly popular throughout the COVID-19 pandemic in places like restaurants, so customers no longer have to physically hold a dirty menu that has been held by many other customers. Now, they can use their phone to scan over the small black and white matrix barcode and almost immediately get taken to the menu. While they may be convenient, they also have their drawbacks as there are ethical implications to this form of information technology. [[File:Multipleqr.png|thumb|right|400px||center|QR Codes and their amount of data.<ref>http://qrcode.meetheed.com/question7.php</ref>]] |
==Background== | ==Background== | ||
Revision as of 17:43, 18 March 2021
A QR (Quick Response) code is a unique, two-dimensional barcode.[1] It is a form of information technology that stores alphanumeric characters in the form of text or URLs, making it easy for smartphone users to be directed to a link provided by an organization or person. Barcodes only use horizontal information, whereas a QR code can contain information that is both horizontal and vertical [2]. QR codes have become increasingly popular throughout the COVID-19 pandemic in places like restaurants, so customers no longer have to physically hold a dirty menu that has been held by many other customers. Now, they can use their phone to scan over the small black and white matrix barcode and almost immediately get taken to the menu. While they may be convenient, they also have their drawbacks as there are ethical implications to this form of information technology.
Contents
Background
History

The QR code was invented by the company DENSO WAVE in 1994, more specifically it can be noted that their lead developer was Masahiro Hara [5]. People found that barcodes could not store enough information, which led to limitations on their usage [2]. A code 129 (as seen on the right), a one-dimensional barcode, is considered to be a high-density barcode that can encode letters, numbers, special characters, and control codes that are primarily used in supply chains (inventory, warehousing, industrial uses). It can only hold 48 characters worth of information [4]. A QR code can hold up to 7,089 characters, which is almost 150 times as much information as a one-dimensional barcode [5].
Usage
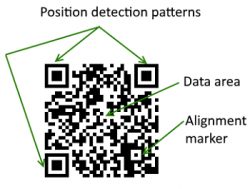
A QR code is readable by mobile phones with cameras and QR scanners. It is not possible for a human to manually decode a QR code [7]. They can be read in any direction in 360 degrees via position detection patterns at three corners of the symbol [5]. QR codes can even be tilted or on a curved surface and still, successfully display the information embedded within the code [5]. For successful usage, the device interprets the message and further displays, manipulates, or stores the information on the users’ mobile device [5]. Some of the ways QR codes can be utilized are as follows: URLs, QR code payment, website login, restaurant menus and ordering, joining a wifi network, loyalty programs, and displaying multimedia content (such as videos, audio, images, and documents)[8].
Types of QR Codes
There are many types of QR codes. The original QR code is called Model 1, which can store up to 1,167 numerals [9]. Model 2 is the improved version of Model 1, and it is the commonly used version that can hold up to 7,089 characters [5]. Additionally, there is the Micro QR code, which is a smaller version of the standard QR code and symbol size is limited to 35 numeric characters. The benefit is that it can be printed in a smaller amount of space as compared to the other models. Typically organizations utilize Model 2, but there are 40 different versions of QR codes with different data capacities aside from the ones described above such as: iQR, Frame QR, Secure QR Code, LogoQ, etc. [10].
Ethical Implications
QR codes have a variety of uses and can connect users to information very easily and quickly. Since they require minimal technical skills to utilize, they can be applicable to a variety of settings as mentioned above [5]. However, it is crucial to note the ethical implications of QR codes, particularly because they can be used for malicious intent and phishing.
Attackers that intend to override QR codes in some fashion are likely doing it for malicious intent. The most frequently reported attack is social engineering, which is the art of manipulating people to reveal confidential information to the social engineer for the engineer to in turn steal their data [10]. A common practice utilized by these hackers is phishing, which is when the attacker attempts to steal information by impersonating a trustworthy entity [11]. Information that could be stolen could include but is not limited to usernames, passwords, addresses, contacts, and credit card information.
Two Forms of Attack
The two main attack vectors to exploit QR codes are where the attacker replaces the entire QR code and when the attacker modifies individual modules of the QR code [10]. When the attacker replaces the entire QR code, they create a new QR code with a malicious link encoded and paste it over an already existing QR code [10]. The other form of attack involves modifying the encoded content by changing the color of specific modules of the QR Code, where the user will be directed after scanning the code [10].
Twitter Incident 2012
The Jester, a self-described patriotic hacker (@th3j35t3r on Twitter), claimed to have executed a multilayered attack where he broke into mobile phones of various leaders and copied incriminating data [13]. Data is valuable, hence why there are hackers who try to steal it. The Jester’s main targets were English-language websites that recruit followers for al-Qaida (a militant Islamic movement) [13]. To execute his hack, he changed his Twitter profile picture to a QR code. When users went to the website from the QR code, it connected the user to a server network named Netcat [13]. Further, Netcat would see if the user’s device had Twitter and if it was a target phone, then it would send the username to the Jester’s server. The Jester used these usernames to analyze if they were associated with Anonymous news sites and chat rooms, Islamist recruiting sites, and WikiLeaks [13]. Lastly, the Jester would try to steal the data from the targeted phone, which could include messages, call logs, emails, and contacts [13]. This invasion of privacy is unethical and the convenience of making and implementing a QR has potential dangers and harms for smartphone users.
Conclusion of Ethical Implications
While the ethical implications presented could, unfortunately, reveal confidential information to a malicious hacker, QR codes provide a fast and convenient means to give information from one user to the next. Instead of having to type in a long URL, the users can hold their phone over a QR code at any angle for a moment and the link is brought up. The primary challenge associated with harmful QR codes is informing the user of the incident, and it would be beneficial to add a verification process that is transparent to the user and/or warnings to let the user know of possible threats before they enter the dangerous URL or open the media [10].
References
- ↑ Encyclopedia Britannica. (n.d.). QR Code. In britannica.com. Retrieved March 18, 2020, from https://www.britannica.com/technology/QR-Code.
- ↑ 2.0 2.1 Stein, Adriana. (2020, January 1) How QR Codes Work and Their History. QR Code Generator. https://www.qr-code-generator.com/blog/how-qr-codes-work-and-their-history/
- ↑ http://qrcode.meetheed.com/question7.php
- ↑ 4.0 4.1 Premier Electronics Inc. (n.d.). Barcode Types - Identification and Understanding. Premier Electronics Inc. https://www.premierelectronics.com/blog/barcode-types-identificaton-understanding#:~:text=Code%2039%20barcodes%20are%20variable,five%20bars%20and%20four%20spaces.&text=Code%20128%20is%20a%20one,special%20characters%20and%20control%20codes.
- ↑ 5.0 5.1 5.2 5.3 5.4 5.5 5.6 Law, Ching-yin and So, Simon (2010) QR Codes in Education. Journal of Educational Technology Development and Exchange (JETDE): Vol. 3 : Iss. 1 , Article 7. https://aquila.usm.edu/cgi/viewcontent.cgi?article=1011&context=jetde
- ↑ https://www.cgap.org/blog/inside-qr-codes-how-black-white-dots-simplify-digital-payments
- ↑ Rouillard, José. (2009, October 11). Contextual QR Codes. 2008 The Third International Multi-Conference on Computing in the Global Information Technology (iccgi 2008), Athens, Greece, 2008, pp. 50-55. https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=4591344
- ↑ QR Code. (2021, February 7). Wikipedia. https://en.wikipedia.org/wiki/QR_code
- ↑ Chang, Jae Hwa. (2014, July 30) An introduction to using QR codes in scholarly journals. Science Editing. https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.986.6494&rep=rep1&type=pdf
- ↑ 10.0 10.1 10.2 10.3 10.4 10.5 Krombholz K., Frühwirt P., Kieseberg P., Kapsalis I., Huber M., Weippl E. (2014). QR Code Security: A Survey of Attacks and Challenges for Usable Security. Human Aspects of Information Security, Privacy, and Trust. https://link.springer.com/content/pdf/10.1007%2F978-3-319-07620-1_8.pdf
- ↑ Jagatic, T., Johnson, N. et al. (2007, October). Social Phishing Volume 50 Issue 10. Communications of the ACM. https://dl.acm.org/doi/fullHtml/10.1145/1290958.1290968?casa_token=aKPSW2sVqnMAAAAA:OH7v7hXko3P8lyga-GNd8zQMqD_AS_QcAULLPg3M7Ln17OeJ9uLZHogaIJhtgc97saukLp3-A8up
- ↑ https://twitter.com/th3j35t3r
- ↑ 13.0 13.1 13.2 13.3 13.4 Wagenseil, Paul. (2012, March 13). Anti-Anonymous hacker threatens to expose them. NBC News. SecurityNewsDaily. https://www.nbcnews.com/id/wbna46716942