Difference between revisions of "QR Codes"
| Line 1: | Line 1: | ||
| − | A QR (Quick Response) code is a | + | A QR (Quick Response) code is a two-dimensional [[Wikipedia:barcode|barcode]].<ref>Gregersen, Erik. (n.d.). QR Code. Encyclopedia Britannica. https://www.britannica.com/technology/QR-Code.</ref> This code is a form of [[wikipedia:information technology|information technology]] that stores [[Wikipedia:alphanumeric|alphanumeric]] characters as text or [[Wikipedia:URL|URLs]], allowing [[Wikipedia:smartphone|smartphone]] users to be redirected to a link provided by an organization or person. This eliminates the need to type out a long URL. Barcodes only use horizontal information, but QR codes can contain information that is both horizontal and vertical. <ref name="History">Stein, Adriana. (2020, January 1). How QR Codes Work and Their History. QR Code Generator. https://www.qr-code-generator.com/blog/how-qr-codes-work-and-their-history/</ref> During the [[Wikipedia:COVID-19 pandemic|COVID-19 pandemic]], QR codes experienced a rise in popularity as a solution to avoid multiple customers handling the same menus or employees having to sanitize menus in between customers.<ref>Luna, N. (2020, July 14). <i>Tech tracker: restaurants are turning to QR codes during the coronavirus pandemic for digital menus and contactless payment</i>. Restaurant Hospitality. https://www.restaurant-hospitality.com/technology/tech-tracker-restaurants-are-turning-qr-codes-during-coronavirus-pandemic-digital-menus</ref> They allow customers to use their phones to view a menu within a few seconds.[[File:Multipleqr.png|thumb|right|400px||center|QR Codes and their amount of data.<ref>Taylor, Lee. (2017, February). How Much Data Can a QR Code Hold? http://qrcode.meetheed.com/question7.php</ref>]] |
==Background== | ==Background== | ||
| − | |||
[[File:1Dbarcode.png|thumb|right|300px||center|A standard one-dimensional barcode.<ref name="Premier"/>]] | [[File:1Dbarcode.png|thumb|right|300px||center|A standard one-dimensional barcode.<ref name="Premier"/>]] | ||
| − | In 1994, under lead developer Masahiro Hara, the company [[Wikipedia:Denso Wave|Denso Wave]] invented QR codes as an improved version of barcodes.<ref name="Education">Law, Ching-yin and So, Simon (2010). QR Codes in Education. Journal of Educational Technology Development and Exchange (JETDE): Vol. 3 : Iss. 1 , Article 7. https://aquila.usm.edu/cgi/viewcontent.cgi?article=1011&context=jetde</ref>. | + | In 1994, under lead developer Masahiro Hara, the company [[Wikipedia:Denso Wave|Denso Wave]] invented QR codes as an improved version of barcodes.<ref name="Education">Law, Ching-yin and So, Simon (2010). QR Codes in Education. Journal of Educational Technology Development and Exchange (JETDE): Vol. 3 : Iss. 1 , Article 7. https://aquila.usm.edu/cgi/viewcontent.cgi?article=1011&context=jetde</ref>. Regular barcodes could not store enough information, which limited their usage.<ref name="History"/> For example, a Code-129 barcode is a high-density, one-dimensional barcode that can encode letters, numbers, special characters, and control codes. These barcodes can hold 48 characters of information. The most sophisticated one-dimensional barcode can hold up to 85 characters.<ref name="Premier">Premier Electronics Inc. (n.d.). Barcode Types - Identification and Understanding. Premier Electronics Inc. https://www.premierelectronics.com/blog/barcode-types-identificaton-understanding#</ref> A QR code can hold up to 7,089 characters— almost 150 times as much information as a one-dimensional Code-129 barcode.<ref name="Education"/>. |
| − | === | + | == How QR Codes Work == |
| − | + | QR codes are read by mobile phones with camera capabilities or QR scanners. Humans cannot manually interpret QR codes, nor can they be read by traditional [[Wikipedia:laser scanning|laser scanners]].<ref>Rouillard, José. (2009, October 11). Contextual QR Codes. 2008 The Third International Multi-Conference on Computing in the Global Information Technology (iccgi 2008), Athens, Greece, 2008, pp. 50-55. https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=4591344</ref> Position detection patterns at three corners of the code are used to read them at any orientation and direction. Tilting a QR code of placing it on a curved surface will not effect the success of scanning it, and the information embedded within the code will still be displayed. The device used to read the code then interprets the message and displays information or performs an action on the user's device.<ref name="Education"/> [[File:Positionpatterns.png|thumb|left|250px||center|Position Detecting Patterns on a QR Code<ref>Chiampo M., Raman A., Roest J. (2017, November 30). Inside QR Codes: How Black & White Dots Simplify Digital Payments. https://www.cgap.org/blog/inside-qr-codes-how-black-white-dots-simplify-digital-payments</ref>]] | |
| − | QR codes are read by mobile phones with camera capabilities or QR scanners. Humans cannot manually interpret QR codes, nor can they be read by traditional [[Wikipedia:laser scanning|laser scanners]].<ref>Rouillard, José. (2009, October 11). Contextual QR Codes. 2008 The Third International Multi-Conference on Computing in the Global Information Technology (iccgi 2008), Athens, Greece, 2008, pp. 50-55. https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=4591344</ref> | + | |
| − | == | + | ==Uses== |
| − | + | QR codes can be used to link to URLs, for payment, to log in to a website, to view a restaurant menu, to display [[Wikipedia:multimedia|multimedia]] content, and more. | |
| + | ==Types of QR Codes== | ||
| + | There are many types of QR codes. The original QR code was called Model 1, able to store up to 1,167 numerals.<ref> Chang, Jae Hwa. (2014, July 30). An introduction to using QR codes in scholarly journals. Science Editing. https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.986.6494&rep=rep1&type=pdf</ref>. The most commonly used version today is the Model 2, with a limit of 7,089 characters.<ref name="Education"/> There is a smaller version of the standard QR code called the Micro QR code, which is limited to 35 numeric characters. It is smaller, allowing it to be displayed in smaller spaces as compared to the Model 1 and Model 2. In total, there are forty different varieties of QR codes with distinct data capacities. Those include QR, Frame QR, Secure QR Code, and LogoQ.<ref name="Security">Krombholz K., Frühwirt P., Kieseberg P., Kapsalis I., Huber M., Weippl E. (2014). QR Code Security: A Survey of Attacks and Challenges for Usable Security. Human Aspects of Information Security, Privacy, and Trust. https://link.springer.com/content/pdf/10.1007%2F978-3-319-07620-1_8.pdf</ref>. | ||
==Ethical Implications== | ==Ethical Implications== | ||
| − | + | QR codes are a versatile and quick method of connecting users to information because they require minimal technical skills to use.<ref name="Education"/> There are several ethical concerns surrounding QR codes. The primary challenge associated with maliciously compromised QR codes is informing the user of the incident. Krombholz et. al suggest that it would be beneficial to add a verification process that is transparent to the user, or warnings to let them know of possible threats before they open dangerous URLs or media.<ref name="Security"/> | |
| − | A Consumer Report by the [[Wikipedia:Better Business Bureau|Better Business Bureau]] describes how blindly scanning QR codes entails risks that are akin to the risks of blindly clicking links in received emails.<ref name='Newman-R'>Newman, R. (2011, June 23). Consumer Alert: QR Code Safety. Better Business Bureau. https://archive.is/20120715010216/http://sandiego.bbb.org/article/consumer-alert-qr-code-safety-28037</ref> | + | === Blindly Scanning === |
| − | + | A Consumer Report by the [[Wikipedia:Better Business Bureau|Better Business Bureau]] describes how blindly scanning QR codes entails risks that are akin to the risks of blindly clicking links in received emails.<ref name='Newman-R'>Newman, R. (2011, June 23). Consumer Alert: QR Code Safety. Better Business Bureau. https://archive.is/20120715010216/http://sandiego.bbb.org/article/consumer-alert-qr-code-safety-28037</ref> While users have the ability to reason that links within a [[Wikipedia:spam email|spam email]] could be dangerous or suspicious, and thus users can choose to avoid following such links, users are unable to decipher the integrity of a given QR code as QR codes are not designed to be human-readable, and thus users cannot learn anything about the nature of a QR code unless they scan it with their device.<ref name='Newman-R'></ref><ref name='Kieseberg-P'>Kieseberg, P., Schrittwieser, S., Leithner, M., Mulazzani, M., Weippl, E., Munroe, L., & Sinha, M. (2012, January). ''Malicious Pixels Using QR Codes as Attack Vector''. Research Gate. https://www.researchgate.net/publication/303653249_Malicious_Pixels_Using_QR_Codes_as_Attack_Vector</ref> | |
| + | This vulnerability can happen when a user relies on the native QR scanning functionality built into their device’s camera application. There are several downloadable applications that counteract this hazard by granting users a preview of information about the webpage that the QR code points to before opening a potentially dangerous webpage instead of immediately just reading and loading the website pointed to by the QR code.<ref name='Newman-R'></ref> | ||
| − | + | === Hacking === | |
| + | Some individuals override QR codes. [[Wikipedia:Social engineering (security)|Social engineering]] is the most common type of attack.<ref name="Security"/> [[Wikipedia:Phishing|Phishing]] is a type of social engineering and a common practice used by hackers in which the attacker attempts to steal the information by pretending to be an organization or person that the subject trusts.<ref>Jagatic, T., Johnson, N. et al. (2007, October). Social Phishing Volume 50 Issue 10. Communications of the ACM. https://dl.acm.org/doi/fullHtml/10.1145/1290958.1290968?casa_token=aKPSW2sVqnMAAAAA:OH7v7hXko3P8lyga-GNd8zQMqD_AS_QcAULLPg3M7Ln17OeJ9uLZHogaIJhtgc97saukLp3-A8up</ref><ref>Cybersecurity and Infrastructure Security Agency. (2020, August 20). <i>Avoiding Social Engineering and Phishing Attacks</i>. https://us-cert.cisa.gov/ncas/tips/ST04-014</ref> Information that could be stolen is usernames, passwords, addresses, contacts, credit card information, and more. People can also exploit users who scan their QR codes by redirecting them to spoofed websites that distribute [[Wikipedia:malware|malware]].<ref name='Liebowitz-M'>Liebowitz, M. (2011, September 13). ''QR Tags Can Be Rigged to Attack Smart Phones''. Scientific American. https://www.scientificamerican.com/article/qr-tags-can-be-rigged-to/</ref> People also hijack or tamper with existing QR codes to enact forms of [[Wikipedia:culture jamming|culture jamming]].<ref name='Liebowitz-M'></ref><ref name='Elster-K'>Elster, K. (n.d.). ''QR Codes Vulnerable To Hijack Via Slap-Tagging''. EtherCycle. https://ethercycle.com/blog/156 </ref> | ||
| − | === | + | ====Forms of Attack==== |
| − | + | ===== ''1)'' Replacing the entire QR code ===== | |
| + | When the attacker replaces the entire code, rather than eliminate the old one entirely, they layer a new QR code with the malicious link encoded over the pre-existing one.<ref name="Security"/> Attackers can do this by printing their own QR code stickers and placing them directly over publicly accessible QR codes<ref name='Liebowitz-M'></ref><ref name='Elster-K'></ref> They may also design their custom QR code stickers to be the same size as the pre-existing QR code that they are targeting in an attempt to better disguise the integration of their malicious QR code.<ref name='Liebowitz-M'></ref><ref name='Elster-K'></ref> QR codes that are physically accessible in public areas with high volumes of foot-traffic, such as on public posters or signs at bus stops or retail locations, are more susceptible to this form of QR code hijacking.<ref name='Liebowitz-M'></ref><ref name='Elster-K'></ref><ref name='Kennon-M'>Kennon, M. (n.d.). ''What is a QR Code?''. Parnassus Creative. http://www.printmedia.parnassuscreative.com/index.php/diy/print-media/13-what-is-a-qr-code</ref> | ||
| − | + | ===== ''2)'' Modifying individual parts of a QR code ===== | |
| − | + | This form of attack involves modifying the encoded content by inverting the color of a pixel in the QR code: i.e., turn a black pixel into a white pixel or turn a white pixel into a black pixel.<ref name="Security"/><ref name='Liebowitz-M'></ref>. | |
| − | + | ||
===Twitter Incident 2012=== | ===Twitter Incident 2012=== | ||
[[File:Jestertwitter.png|thumb|right|350px|center|Screenshot of The Jester's Current Twitter Profile<ref>JΞSŦΞR ✪ ΔCŦUΔL³³°¹, @th3j35t3r. (2021, March). Screenshot. Twitter. https://twitter.com/th3j35t3r</ref>]] | [[File:Jestertwitter.png|thumb|right|350px|center|Screenshot of The Jester's Current Twitter Profile<ref>JΞSŦΞR ✪ ΔCŦUΔL³³°¹, @th3j35t3r. (2021, March). Screenshot. Twitter. https://twitter.com/th3j35t3r</ref>]] | ||
| − | The Jester, a "self-described patriotic hacker" (@th3j35t3r on [[Wikipedia:Twitter|Twitter]]), used QR code technology in an alleged multi-layered attack against world leaders in which he broke into their mobile phones and copied incriminating data.<ref name="NBC">Wagenseil, Paul. (2012, March 13). Anti-Anonymous hacker threatens to expose them. NBC News. SecurityNewsDaily. https://www.nbcnews.com/id/wbna46716942</ref> [[Wikipedia:NBC|NBC]] reported that the Jester’s main targets were websites that recruited followers for [https://en.wikipedia.org/wiki/Al-Qaeda Al-Qaeda]. According to NBC, to execute the attack, he changed his Twitter profile picture to a QR code. When users went to the website from the QR code, it connected them to a server that determined if the user had a Twitter account and if their device was a target phone. The Jester's server then received the target usernames and used them to analyze if the usernames were associated with "Anonymous news sites and chat rooms, Islamist recruiting sites and WikiLeaks." The Jester then attempted to steal phone data, including messages, emails, contacts, and call logs, from the targeted phones.<ref name="NBC"/> These "hacktivists" have been surrounded by ethical questions about | + | The Jester, a "self-described patriotic hacker" (@th3j35t3r on [[Wikipedia:Twitter|Twitter]]), used QR code technology in an alleged multi-layered attack against world leaders in which he broke into their mobile phones and copied incriminating data.<ref name="NBC">Wagenseil, Paul. (2012, March 13). Anti-Anonymous hacker threatens to expose them. NBC News. SecurityNewsDaily. https://www.nbcnews.com/id/wbna46716942</ref> [[Wikipedia:NBC|NBC]] reported that the Jester’s main targets were websites that recruited followers for [https://en.wikipedia.org/wiki/Al-Qaeda Al-Qaeda]. According to NBC, to execute the attack, he changed his Twitter profile picture to a QR code. When users went to the website from the QR code, it connected them to a server that determined if the user had a Twitter account and if their device was a target phone. The Jester's server then received the target usernames and used them to analyze if the usernames were associated with "Anonymous news sites and chat rooms, Islamist recruiting sites and WikiLeaks." The Jester then attempted to steal phone data, including messages, emails, contacts, and call logs, from the targeted phones.<ref name="NBC"/> These "hacktivists" have been surrounded by ethical questions about morality, with some arguing they have no moral code and some claiming they follow their own societal norms.<ref>Scott, T., Cupp, O. (2018). <i>Ethics of Hacktivism.</i> The Simons Center. https://thesimonscenter.org/wp-content/uploads/2018/05/Ethics-Symp-pg143-148.pdf</ref> |
==References== | ==References== | ||
Revision as of 22:57, 8 April 2021
A QR (Quick Response) code is a two-dimensional barcode.[1] This code is a form of information technology that stores alphanumeric characters as text or URLs, allowing smartphone users to be redirected to a link provided by an organization or person. This eliminates the need to type out a long URL. Barcodes only use horizontal information, but QR codes can contain information that is both horizontal and vertical. [2] During the COVID-19 pandemic, QR codes experienced a rise in popularity as a solution to avoid multiple customers handling the same menus or employees having to sanitize menus in between customers.[3] They allow customers to use their phones to view a menu within a few seconds.
Contents
Background

In 1994, under lead developer Masahiro Hara, the company Denso Wave invented QR codes as an improved version of barcodes.[6]. Regular barcodes could not store enough information, which limited their usage.[2] For example, a Code-129 barcode is a high-density, one-dimensional barcode that can encode letters, numbers, special characters, and control codes. These barcodes can hold 48 characters of information. The most sophisticated one-dimensional barcode can hold up to 85 characters.[5] A QR code can hold up to 7,089 characters— almost 150 times as much information as a one-dimensional Code-129 barcode.[6].
How QR Codes Work
QR codes are read by mobile phones with camera capabilities or QR scanners. Humans cannot manually interpret QR codes, nor can they be read by traditional laser scanners.[7] Position detection patterns at three corners of the code are used to read them at any orientation and direction. Tilting a QR code of placing it on a curved surface will not effect the success of scanning it, and the information embedded within the code will still be displayed. The device used to read the code then interprets the message and displays information or performs an action on the user's device.[6]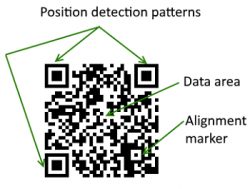
Uses
QR codes can be used to link to URLs, for payment, to log in to a website, to view a restaurant menu, to display multimedia content, and more.
Types of QR Codes
There are many types of QR codes. The original QR code was called Model 1, able to store up to 1,167 numerals.[9]. The most commonly used version today is the Model 2, with a limit of 7,089 characters.[6] There is a smaller version of the standard QR code called the Micro QR code, which is limited to 35 numeric characters. It is smaller, allowing it to be displayed in smaller spaces as compared to the Model 1 and Model 2. In total, there are forty different varieties of QR codes with distinct data capacities. Those include QR, Frame QR, Secure QR Code, and LogoQ.[10].
Ethical Implications
QR codes are a versatile and quick method of connecting users to information because they require minimal technical skills to use.[6] There are several ethical concerns surrounding QR codes. The primary challenge associated with maliciously compromised QR codes is informing the user of the incident. Krombholz et. al suggest that it would be beneficial to add a verification process that is transparent to the user, or warnings to let them know of possible threats before they open dangerous URLs or media.[10]
Blindly Scanning
A Consumer Report by the Better Business Bureau describes how blindly scanning QR codes entails risks that are akin to the risks of blindly clicking links in received emails.[11] While users have the ability to reason that links within a spam email could be dangerous or suspicious, and thus users can choose to avoid following such links, users are unable to decipher the integrity of a given QR code as QR codes are not designed to be human-readable, and thus users cannot learn anything about the nature of a QR code unless they scan it with their device.[11][12] This vulnerability can happen when a user relies on the native QR scanning functionality built into their device’s camera application. There are several downloadable applications that counteract this hazard by granting users a preview of information about the webpage that the QR code points to before opening a potentially dangerous webpage instead of immediately just reading and loading the website pointed to by the QR code.[11]
Hacking
Some individuals override QR codes. Social engineering is the most common type of attack.[10] Phishing is a type of social engineering and a common practice used by hackers in which the attacker attempts to steal the information by pretending to be an organization or person that the subject trusts.[13][14] Information that could be stolen is usernames, passwords, addresses, contacts, credit card information, and more. People can also exploit users who scan their QR codes by redirecting them to spoofed websites that distribute malware.[15] People also hijack or tamper with existing QR codes to enact forms of culture jamming.[15][16]
Forms of Attack
1) Replacing the entire QR code
When the attacker replaces the entire code, rather than eliminate the old one entirely, they layer a new QR code with the malicious link encoded over the pre-existing one.[10] Attackers can do this by printing their own QR code stickers and placing them directly over publicly accessible QR codes[15][16] They may also design their custom QR code stickers to be the same size as the pre-existing QR code that they are targeting in an attempt to better disguise the integration of their malicious QR code.[15][16] QR codes that are physically accessible in public areas with high volumes of foot-traffic, such as on public posters or signs at bus stops or retail locations, are more susceptible to this form of QR code hijacking.[15][16][17]
2) Modifying individual parts of a QR code
This form of attack involves modifying the encoded content by inverting the color of a pixel in the QR code: i.e., turn a black pixel into a white pixel or turn a white pixel into a black pixel.[10][15].
Twitter Incident 2012
The Jester, a "self-described patriotic hacker" (@th3j35t3r on Twitter), used QR code technology in an alleged multi-layered attack against world leaders in which he broke into their mobile phones and copied incriminating data.[19] NBC reported that the Jester’s main targets were websites that recruited followers for Al-Qaeda. According to NBC, to execute the attack, he changed his Twitter profile picture to a QR code. When users went to the website from the QR code, it connected them to a server that determined if the user had a Twitter account and if their device was a target phone. The Jester's server then received the target usernames and used them to analyze if the usernames were associated with "Anonymous news sites and chat rooms, Islamist recruiting sites and WikiLeaks." The Jester then attempted to steal phone data, including messages, emails, contacts, and call logs, from the targeted phones.[19] These "hacktivists" have been surrounded by ethical questions about morality, with some arguing they have no moral code and some claiming they follow their own societal norms.[20]
References
- ↑ Gregersen, Erik. (n.d.). QR Code. Encyclopedia Britannica. https://www.britannica.com/technology/QR-Code.
- ↑ 2.0 2.1 Stein, Adriana. (2020, January 1). How QR Codes Work and Their History. QR Code Generator. https://www.qr-code-generator.com/blog/how-qr-codes-work-and-their-history/
- ↑ Luna, N. (2020, July 14). Tech tracker: restaurants are turning to QR codes during the coronavirus pandemic for digital menus and contactless payment. Restaurant Hospitality. https://www.restaurant-hospitality.com/technology/tech-tracker-restaurants-are-turning-qr-codes-during-coronavirus-pandemic-digital-menus
- ↑ Taylor, Lee. (2017, February). How Much Data Can a QR Code Hold? http://qrcode.meetheed.com/question7.php
- ↑ 5.0 5.1 Premier Electronics Inc. (n.d.). Barcode Types - Identification and Understanding. Premier Electronics Inc. https://www.premierelectronics.com/blog/barcode-types-identificaton-understanding#
- ↑ 6.0 6.1 6.2 6.3 6.4 Law, Ching-yin and So, Simon (2010). QR Codes in Education. Journal of Educational Technology Development and Exchange (JETDE): Vol. 3 : Iss. 1 , Article 7. https://aquila.usm.edu/cgi/viewcontent.cgi?article=1011&context=jetde
- ↑ Rouillard, José. (2009, October 11). Contextual QR Codes. 2008 The Third International Multi-Conference on Computing in the Global Information Technology (iccgi 2008), Athens, Greece, 2008, pp. 50-55. https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=4591344
- ↑ Chiampo M., Raman A., Roest J. (2017, November 30). Inside QR Codes: How Black & White Dots Simplify Digital Payments. https://www.cgap.org/blog/inside-qr-codes-how-black-white-dots-simplify-digital-payments
- ↑ Chang, Jae Hwa. (2014, July 30). An introduction to using QR codes in scholarly journals. Science Editing. https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.986.6494&rep=rep1&type=pdf
- ↑ 10.0 10.1 10.2 10.3 10.4 Krombholz K., Frühwirt P., Kieseberg P., Kapsalis I., Huber M., Weippl E. (2014). QR Code Security: A Survey of Attacks and Challenges for Usable Security. Human Aspects of Information Security, Privacy, and Trust. https://link.springer.com/content/pdf/10.1007%2F978-3-319-07620-1_8.pdf
- ↑ 11.0 11.1 11.2 Newman, R. (2011, June 23). Consumer Alert: QR Code Safety. Better Business Bureau. https://archive.is/20120715010216/http://sandiego.bbb.org/article/consumer-alert-qr-code-safety-28037
- ↑ Kieseberg, P., Schrittwieser, S., Leithner, M., Mulazzani, M., Weippl, E., Munroe, L., & Sinha, M. (2012, January). Malicious Pixels Using QR Codes as Attack Vector. Research Gate. https://www.researchgate.net/publication/303653249_Malicious_Pixels_Using_QR_Codes_as_Attack_Vector
- ↑ Jagatic, T., Johnson, N. et al. (2007, October). Social Phishing Volume 50 Issue 10. Communications of the ACM. https://dl.acm.org/doi/fullHtml/10.1145/1290958.1290968?casa_token=aKPSW2sVqnMAAAAA:OH7v7hXko3P8lyga-GNd8zQMqD_AS_QcAULLPg3M7Ln17OeJ9uLZHogaIJhtgc97saukLp3-A8up
- ↑ Cybersecurity and Infrastructure Security Agency. (2020, August 20). Avoiding Social Engineering and Phishing Attacks. https://us-cert.cisa.gov/ncas/tips/ST04-014
- ↑ 15.0 15.1 15.2 15.3 15.4 15.5 Liebowitz, M. (2011, September 13). QR Tags Can Be Rigged to Attack Smart Phones. Scientific American. https://www.scientificamerican.com/article/qr-tags-can-be-rigged-to/
- ↑ 16.0 16.1 16.2 16.3 Elster, K. (n.d.). QR Codes Vulnerable To Hijack Via Slap-Tagging. EtherCycle. https://ethercycle.com/blog/156
- ↑ Kennon, M. (n.d.). What is a QR Code?. Parnassus Creative. http://www.printmedia.parnassuscreative.com/index.php/diy/print-media/13-what-is-a-qr-code
- ↑ JΞSŦΞR ✪ ΔCŦUΔL³³°¹, @th3j35t3r. (2021, March). Screenshot. Twitter. https://twitter.com/th3j35t3r
- ↑ 19.0 19.1 Wagenseil, Paul. (2012, March 13). Anti-Anonymous hacker threatens to expose them. NBC News. SecurityNewsDaily. https://www.nbcnews.com/id/wbna46716942
- ↑ Scott, T., Cupp, O. (2018). Ethics of Hacktivism. The Simons Center. https://thesimonscenter.org/wp-content/uploads/2018/05/Ethics-Symp-pg143-148.pdf