Orwell (Video Game)
|
Orwell is an episodic series of video games developed by German indie developer Osmotic Studios[1] which released its first episode on October 20, 2016. In Orwell, the player assumes the role of an operator of the Orwell surveillance system, who is not a citizen of the Nation, where together with a handler from the Nation you solve who organized the recent terrorist bombing of the Freedom Plaza. The Orwell surveillance system is able to create and store profiles for persons of interest and builds these profiles by collecting information about them online. The Orwell system is also able to tap into online messaging and phone calls and collect information on the targets that way. It may also access computers and phones and collect information gathered from the files on these devices. As the operator of the Orwell system is it your job to look at all these pieces of information and figure out which pieces of information you want to upload to the system for your handler to look at. Your handler is unable to access any of the information you see and is only able to see the things which you upload to the system which drives the choices the player has to make of whether the information is relevant to the case or is needless snooping.
Contents
Plot
Keeping an Eye on You
Episode 1
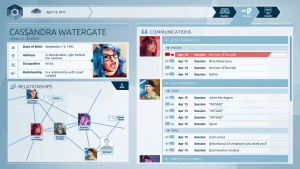
Following the recent bombing of the Freedom Plaza you are introduced to your handler, Symes, who instructs you on your new job asks you to investigate Cassandra Watergate, a person with known anti-government sentiments and was seen at Freedom Plaza before the bombing. Watergate is eventually brought in on a charge of assault against the police she had done before and was dropped because of lack of evidence but due to a private conversation with her friend we find out that it was intentional. However the ending shows another bomb going off at Stelligan University and Watergate is ruled out as the suspect for the bombings.
Episode 2
The player learns about the activist group called Thought who's leader, Abraham Goldfels, is a lecturer at Stelligan University and many members are students at Stelligan. Upon further investigation we learn about initiate, a hacker who has expressed interest in Thought. The ending of this chapter has the player trying to find the location of the third bomb before it goes off. Based on the actions of the player the player either the bomb is found and defused or the player gives the wrong information and the bomb explodes with many causalities.
Episode 3
Regardless of what happened the previous episode, the player is tasked with finding out more about Nina, the suspected bomber. We discover that she was a soldier in the army and in an operation her fiance, also in the army, was killed in combat and due to this she developed anti-government sentiments. Due to the actions of initiate and the player, Nina discovers that she is being watched and tries to escape with her son out of the country. Based on the actions of the player either Nina escapes, or is found by the police where she is either fatally shot or is arrested. After this the player finds an email from Goldfels detailing the bombings.
Episode 4
Symes tasks the player with discovering the location of Goldfels with the intention of bringing him in. It is discovered that Goldfels had died several years ago due to an inoperable cancer and that someone else was instead impersonating Goldfels and planning the bombings. Also after a hack on the government servers by initiate, Symes's true identity is doxed to the public.
Episode 5
Based on whether Nina escaped in Episode 3, Symes's house is either defaced by the public or he is found shot dead in his home. Regardless your handler is replaced by the Minister of Security and the person behind Orwell, Delacroix. After intercepting a message to Thought members about a meeting at 4PM the player is tasked with discovering the true identity of Goldfels and where the meeting will take place. At 4 the meeting proceeds and in the meeting Orwell gets hacked by initiate and the true leader of Thought gets revealed. They then explain that they were behind everything that had happened and that their goal was to convince the operator, the player, that Orwell was a flawed system and asks them to make a choice. Based on what the player does next; you can listen to Delacroix and find out the identity and location of initiate and announce Thought as a terrorist group, causing all the members to be arrested, Orwell being revealed as a success, and the player being given a promotion and an opportunity to immigrate to the Nation; you can listen to initiate and investigate Delacroix and discover that Delacroix believed the bombings to be a good thing. This leads to Delacroix resigning after this gets released to the public, Orwell being shut down, and the player being wanted for their involvement with Orwell. You can listen to "Goldfels" and reveal that while Orwell was only designed to spy on citizens of the Nation, it actually keeps records on everyone. This leads to global outcry and the governing Party to be ousted, Orwell shut down, and Thought taking over the government.
Reception
Orwell falls into the genre known as simulation video games, which are designed to simulate real world activities and situations. Metrics for games in this category led Orwell to receive mostly positive reviews, including a 9/10 on the popular video game platform Steam[2]. Many of the reviews lauded Orwell's developer, Osmotic Studios, for the game's relevance to contemporary privacy issues and its take on the seemingly ubiquitous idea of "Big Brother". PC Gamer gave the game a score of 78%[3], gamespot awarded it an 8/10[4], and metacritic's approved critics gave it an aggregated score of 74%[5]. Polygon commended the indie game's emphasis on issues of free speech[6].
Ethical Issues
Privacy Concerns
Online privacy is a topic closely related to the premise of the game. As the operator of the Orwell system, your job is to intrude on the online privacy of persons of interest. Privacy is having control over your personal information and losing this control is a violation.[7] Our identities are the combination of our information, this is especially true in this game where we never physically meet any of the characters, the characters are literally the information we gathered on them and if conflicting information exists then we as an outside party are creating an identity without consent.
Computer Surveillance
Computer surveillance is an ability of the Orwell surveillance system that gets used to find private information in the game. If the player is able to find the MAC address of a device, they are then able to hack into that device and start going through the files stored on the device. After the revelations of Edward Snowden and the practices of the NSA many companies have pursued better encryption technology to protect its users from these backdoor attacks.[8]Some countries are against this and believe that having backdoors are necessary in order for the necessary parties to get the information they need to stop disasters from happening. [9] The situation is complicated and while there are perceived benefits to making sure technology isn't hindering justice, there are also concerns about invasions of privacy to consider as well.[10]
Doxing
The ending of the third episode where Symes gets doxed is a very real issue that happens with modern internet culture. In 2014 after the Boston Marathon tragedy, certain groups in Reddit became convinced that Sunil Tripathi was one of the Boston Bombers. This turned out to be false after further investigations by legal authorities but it was already too late as the damage was already done and Tripathi was found to have committed suicide after having his reputation ruined by the internet.[11]. This act of vigilante doxing directly led to the death of an innocent person. Another case of when doxing led to the death of an innocent person was in the 2017 Wichita swatting incident. Swatting is the harassment tactic when someone calls local law enforcement claiming that there is a situation which requires immediate police action often at the house of the person of a doxed person. In the 2017 Wichita swatting incident, two players were playing an online game which escalated to where one of the players calling a domestic violence at the home of what he thought was the home of the other player. When police arrived they assumed the suspect was violent and shot on sight which led to the fatal shot of Andrew Finch. [12]
Voyeurism
As the operator of Orwell, we act as voyeurs to private correspondence on many occasions. We spy on the characters and their online usage habits as well as their conversations with each other. Orwell is designed to give the operator perfect voyeurism. [13] However as we see in the game when perfect voyeurism goes wrong there are grave consequences such as when Nina tries to run from the authorities. The system itself is flawed and even though it aims for perfect voyeurism it fails as one of the characters finds out someone is spying on him as his bank informs him of a suspicious login after we as the player had just looked at his bank account. Perfect voyeurism is unethical because of the disaster that can happen when the voyeur gets caught.
References
- ↑ “Orwell.” Fellow Traveller, fellowtraveller.games/games/orwell/.
- ↑ “Orwell: Keeping an Eye On You on Steam.” Welcome to Steam, store.steampowered.com/agecheck/app/491950/.
- ↑ Savage, Phil. “Orwell Review.” Pcgamer, PC Gamer THE GLOBAL AUTHORITY ON PC GAMES, 13 Dec. 2016, www.pcgamer.com/orwell-review/.
- ↑ O'Connor, James. “Orwell Review.” GameSpot, GameSpot, 30 Nov. 2016, www.gamespot.com/reviews/orwell-review/1900-6416580/.
- ↑ “Orwell: Ignorance Is Strength.” Metacritic, 22 Feb. 2018, www.metacritic.com/game/pc/orwell-ignorance-is-strength.
- ↑ Campbell, Colin. “Orwell Review.” Polygon, 29 Nov. 2016, www.polygon.com/2016/11/29/13769024/orwell-review-PC.
- ↑ Shoemaker, D. W. (2009). Self-exposure and exposure of the self: Informational privacy and the presentation of identity. Ethics and Information Technology, 12(1), 3-15. doi:10.1007/s10676-009-9186-x
- ↑ Cuthbertson, Anthony. “Snowden 'Sped up Encryption' by Seven Years.” Newsweek, 8 June 2016, www.newsweek.com/snowden-sped-encryption-seven-years-452688.
- ↑ Whittaker, Zack. “'Five Eyes' Governments Call on Tech Giants to Build Encryption Backdoors - or Else.” TechCrunch, TechCrunch, 3 Sept. 2018, techcrunch.com/2018/09/03/five-eyes-governments-call-on-tech-giants-to-build-encryption-backdoors-or-else/.
- ↑ Lyon, D., & Zureik, E. (Eds.). (1996). Computers, surveillance, and privacy. U of Minnesota Press.
- ↑ “The Boston Bombing's Forgotten Victim.” WebCite Query Result, www.webcitation.org/6TjkHiR9g?url=http%3A%2F%2Farticles.philly.com%2F2014-04-30%2Fnews%2F49497042_1_sunil-tripathi-providence-river-sunny.
- ↑ Stevens, Matt, and Andrew R. Chow. “Man Pleads Guilty to 'Swatting' Hoax That Resulted in a Fatal Shooting.” The New York Times, The New York Times, 14 Nov. 2018, www.nytimes.com/2018/11/13/us/barriss-swatting-wichita.html.
- ↑ Doyle, T. (2009). Privacy and perfect voyeurism. Ethics and Information Technology, 11(3), 181-189. doi:10.1007/s10676-009-9195-9