Difference between revisions of "Online Identity Theft"
(→Causes) |
|||
| Line 27: | Line 27: | ||
== Causes == | == Causes == | ||
One way of obtaining information is by phishing. This involves sending spoof emails to people impersonating a business or institution. Spoof emails typically involve a user receiving an email to change his/her password after clicking the link. It takes the user to what appears to be a legitimate site; however it belongs to the thief. After the user enters his/her information, it is now in the hands of the criminal. Examples of this occur with online stores and financial merchants. Another cause of online identity theft can be phishing websites themselves, without sending emails. These types of websites put up a front of a legitimate business, but really have the intention of obtaining some information from you, whether it be credit card information, social security numbers, or personal identification numbers. | One way of obtaining information is by phishing. This involves sending spoof emails to people impersonating a business or institution. Spoof emails typically involve a user receiving an email to change his/her password after clicking the link. It takes the user to what appears to be a legitimate site; however it belongs to the thief. After the user enters his/her information, it is now in the hands of the criminal. Examples of this occur with online stores and financial merchants. Another cause of online identity theft can be phishing websites themselves, without sending emails. These types of websites put up a front of a legitimate business, but really have the intention of obtaining some information from you, whether it be credit card information, social security numbers, or personal identification numbers. | ||
| + | |||
| + | A second, increasingly common way of perpetrating identity theft is by social engineering, or tricking a user into giving up sensitive information. The process of social engineering relies on the user to make the mistake of trusting the criminal with information that normally would not be divulged. One method of social engineering would be to email the administrator of a network pretending to be a user who got locked out of their account, in order to trick the administrator into either giving up a valid password or getting the administrator to create the criminal an account on the network. Phishing, as discussed above, could be considered a form of social engineering. <ref name= "Social Engineering Fundamentals">http://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics</ref> | ||
| + | |||
| + | Social engineering is extremely difficult to defend against with technology systems, since the entire premise is based around exploiting human error and ignorance. Many users appear not to guard their passwords well enough, leading to potential identity theft by malicious users. In fact, many people will give away their passwords in exchange for a gift as trivial as a pen <ref name="Office workers give away passwords for a cheap pen">http://www.theregister.co.uk/2003/04/18/office_workers_give_away_passwords/</ref>. | ||
== Effects == | == Effects == | ||
Revision as of 18:37, 5 December 2012
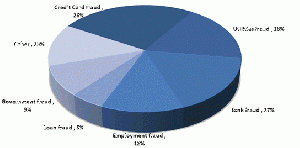
Online Identity Theft is a form of fraud where a criminal impersonates another person by obtaining their personal information through the Internet. Typically, criminals steal another’s identity for financial gain such as applying for loans or credit cards without the person’s knowledge. Information gained from online identity theft includes but is not limited to social security numbers, signatures, names, addresses, phone numbers, credit card information, etc. Because there are so many types of online identity theft (see pie chart below to the right), criminals have more options in how they commit identity theft online, resulting in more and more cases of this crime. In order to combat the increasing frequency of online identity theft, the government is making the consequences for online identity theft more severe.
Contents
Background
The Internet has given people new ways of accessing information, however, the growing use of the Internet has led to an increase in online crimes. Online identity fraud is one of the fastest growing crimes in the online environment. The aftermath of being a victim of identity theft can be expensive and traumatic. Before computers and the Internet, criminals had to go “dumpster diving” or steal one's mail in order to gain his or her personal information. Now, with the advent of the internet, people are at risk in a number of more ways. All of the information that users share through social networks, online job and bank applications, and emails is vulnerable to theft by hackers from a remote location, making identity theft online far easier than in the real-world.
Types of identity theft
The most common forms of identity theft are listed below:
Financial Identity Theft
Financial identity theft, the most common form of online identity theft, occurs when someone illegally gains possession of another person's financial information, enabling the thief access to the victim's bank accounts and/or credit cards. Thieves have the ability to completely wipe the victim's entire bank account within hours or apply for numerous credit cards or loans using the victim's name and information. The rise in online banking and shopping has facilitated the increase in financial identity theft.
Criminal identity Theft
This occurs when a criminal gives another person’s name and personal information, such as a Social Security Number, to a law enforcement officer during an investigation. In some cases, the victim may not know their identity was stolen. In situations like this, the victim may not know there is a warrant out for his/her arrest and could lose unemployment or banking privileges. Criminals who steal another’s identity use the information it to open new accounts impersonating the victim.
Identity Cloning
Identity cloning is the use of another person's information to assume their identity. This can be done by obtaining their social security number, passwords, or PIN numbers. Cloning someone's identity can have devastating effects to the actual person. Identity cloners can pay bills as you, work as you, start a family as you, and have children as you. They essentially are living your life in another location.[1]
Medical Identity Theft
This is a subset of identity cloning which is used to obtain prescription medication or other drugs otherwise unattainable. This type of identity theft involves more investigation by the attacker on which medicine is trying to be obtained and which type of people use this medication. This can be done by stealing your health insurance information and making insurance claims using your identity.[2] Not only can this affect your finances, it can also have major effects on your health. For example, a medical insurance provider could drop you from your plan if faulty information is being provided to them or if bills are not getting paid properly.
Child Identity Theft
A rising trend in the world of identity theft is for adults to use their children's social security number to secure credit. Unfortunately, these parents oftentimes ruin their children's credit scores and when the children come of age and discover this, they are put into a perplexing situation; very few kids are willing to press charges against their parents, even though their identity was stolen. This type of theft is especially worrisome because it is often years before they discover the damage that has been done.
Causes
One way of obtaining information is by phishing. This involves sending spoof emails to people impersonating a business or institution. Spoof emails typically involve a user receiving an email to change his/her password after clicking the link. It takes the user to what appears to be a legitimate site; however it belongs to the thief. After the user enters his/her information, it is now in the hands of the criminal. Examples of this occur with online stores and financial merchants. Another cause of online identity theft can be phishing websites themselves, without sending emails. These types of websites put up a front of a legitimate business, but really have the intention of obtaining some information from you, whether it be credit card information, social security numbers, or personal identification numbers.
A second, increasingly common way of perpetrating identity theft is by social engineering, or tricking a user into giving up sensitive information. The process of social engineering relies on the user to make the mistake of trusting the criminal with information that normally would not be divulged. One method of social engineering would be to email the administrator of a network pretending to be a user who got locked out of their account, in order to trick the administrator into either giving up a valid password or getting the administrator to create the criminal an account on the network. Phishing, as discussed above, could be considered a form of social engineering. [3]
Social engineering is extremely difficult to defend against with technology systems, since the entire premise is based around exploiting human error and ignorance. Many users appear not to guard their passwords well enough, leading to potential identity theft by malicious users. In fact, many people will give away their passwords in exchange for a gift as trivial as a pen [4].
Effects
The effects of online identity theft are severe. People hesitate to use online banking, make financial transactions, and shop online. Identity thieves can cause financial and physiological damage. The financial damage can increase ones debt by thousands of dollars and severely damage the victim's credit score. Victims of identity theft claim they feel “violated” after having their identity stolen by an unknown person.[5]
Prevention[6]
In order to protect an identity, people need to protect their personal information, especially online. The most common information stolen online is account numbers, passwords, personal identification numbers (PIN), and Social Security Numbers (SSN). The most effective way is to never post this information in an online environment. However, there are professional companies with proven strategies to help people detect online identity theft. Likewise, many credit card companies have implemented fraud detection programs that help catch identity thieves by identifying fraudulent charges and contacting the cardholder.[7] Here are some easy steps to prevent your identify from being stolen:
1. Stay away from phishing websites
- Phishing websites are sites that look like they are a legitimate business, but really is looking to steal your information. Make sure you are familiar with a website before giving them information, such as a username and password, credit card information, address, or social security number. After investigating the legitimacy of the website, if you are still unsure, call their number to find out more information.
2. Utilize some sort of antivirus and anti-malware software.
- Computer viruses are easily spreadable and can gain access to personal information stored on your system. In order to prevent this from occurring it is essential to have these types of programs running on your computer at all times. A list of the best antivirus software of 2012 can be found at that link.
3. Password protection
- When creating passwords, make sure they have at least one capital letter, numbers, letters, as well as some sort of symbol (%, &, ?). Creating different passwords for each site is also beneficial. Do not use any personal information in your passwords, such as your birthdate, childrens' names, pets' names, or your name.
4. Shop only at encrypted websites.
- When a website is encrypted, the data you input into it will be secured. An encrypted website is identified by a small lock in the corner of your screen. When clicking this lock, a security certificate will appear, indicating that it is safe for you to input information. Shopping on these types of websites will ensure the safety of your personal information.
5. Limit the amount of personal information you input into social media websites
- Although social media websites are an amazing form of communication and have drastically changed, and continue to change, how people interact with each other, it is important to limit the amount of personal information you allow people to see. Putting the proper privacy settings on these websites is also important, so people you do not know are unable to access the information you have posted.
6. Use a secured wireless network
- While some people still used a wired connection, most people are using wireless connections. It is important to have a password on your wireless network not only to prevent others from using your network and taking up bandwidth, but also to prevent these users from seeing which webpages you visit. Giving attackers access to this type of information makes it easier to build an informative profile of yourself, thus making it easier to steal your identity.
7. Download software from reputable sites
- This goes along the same lines as shopping through encrypted websites. Make sure the software you download is not a virus or other form of detrimental software. These types of programs may contain workarounds that antivirus or anti-malware software cannot detect.
Ethics
It is a federal crime to “knowingly transfer, possess, or use without lawful authority, a means of identification of another person”.[8] Whether it's stealing credit card and Social Security Numbers stolen or bank account information, the government and media have made it clear that any form of identity theft is a crime. An individual is allowed to do what he or she pleases as long as it does not harm others in society. When a criminal hacks into another person’s account to steal personal information for their own gain, the victim is left hurt both financially and emotionally. Peoples' lives and welfare are harmed by identity theft if their money is stolen or they are unable to get a job. Stealing and using a person's information is considered unethical in most societies, and more attention should be placed on preventing this serious crime.
Due to the fact that many identity thefts occur online and user's information is generally taken from the online world, information security online is becoming critical. Victims may feel as if banks, companies or other trustworthy places may not have secured their information properly. After the Playstation network was hacked April 20, 2011, many user's credit card information was taken[9]. As a result, there was a large outcry that their security should be revamped. Obviously identity theft is considered immoral and unethical by most individuals of society, but the instances of identity theft are increasing and this is putting pressure on companies to improve their security plans. Ethically speaking, the battle against identity theft will require both collaboration from the people as well as companies to protect important data. Even with the increase in punishment for thieves, anonymity online has made it hard for the culprits to be tracked down and prosecuted.
The generative nature of the internet is also said to aid identity theft. It is hard to protect identity and the associated personal information if the internet is an open arena.
See Also
References
- ↑ http://www.spamlaws.com/identity-cloning.html
- ↑ http://www.ftc.gov/bcp/edu/pubs/consumer/idtheft/idt10.shtm
- ↑ http://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics
- ↑ http://www.theregister.co.uk/2003/04/18/office_workers_give_away_passwords/
- ↑ Internet Identity Theft - A Tragedy for Victims, Software and Information Industry Association. May 26, 2011.
- ↑ http://www.makeuseof.com/tag/9-ways-prevent-identity-theft-online-activities/
- ↑ Identity Crime Research and Coordination, Australasian Center for Policing Research. June 30, 2006.
- ↑ Internet Identity Theft - A Tragedy for Victims, Software and Information Industry Association. May 26, 2011.
- ↑ http://www.pcworld.com/article/226128/sony_makes_it_official_playstation_network_hacked.html