Morris Worm
The Morris worm was the name given to a computer worm that launched in November of 1988 from MIT. It is widely considered to be the first computer worm to truly spread and gain widespread notoriety, though the Creeper worm may be considered the first true worm.
In only the first three hours, it was able to affect some computers so severely that they could no longer be used at all until specialized steps were taken to remove the worm and prevent re-infection[1]. However, due to the large amount of system administrators who isolated their networks from the internet as a preventative measure, news of the worm spread slowly and detailed information on how to stop it spread even more so.
Background
Robert Morris was a first-year graduate student in Cornell University’s computer science Ph.D. program in 1988. In October of that year, Morris began working on what would eventually become the Morris worm. It was designed to spread to the internet and, Morris claimed,[2] demonstrate the inadequacies of current computer security protocols without causing any damage to systems or interrupting their use.
Architecture
Initial Steps
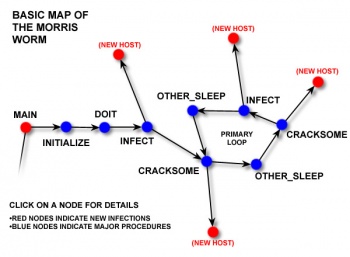
The worm itself was simple but employed a range of tactics to hide itself and operate with subtlety. The worm first began employing camouflage and defenses, which a well-written virus will use to hide itself from both the user and any security programs that may be running.
The Morris worm set the name of the process it was running as to “sh”. At the time, this was the same as the name of the Bourne Shell, which was a shell program used very commonly by UNIX users. As such, if a user were to check the list of running processes on their computer, they wouldn’t see anything out of the ordinary[3].
The next step taken was to reduce the size of the core dump to zero bytes. A core dump is when the processor’s running processes are “dumped” into memory for later analysis. Whenever a program crashes, or a user so chooses, a core dump can be performed so that the state of the computer can be analyzed. Robert Morris did not want the worm to be easily countered or stopped, so having the worm set the core dump size to zero bytes effectively stopped a user from being able to accidentally find the Morris worm in a core dump and analyze its code.[3]
Following this, the worm will attempt to load the files it needs to run and scan the network interfaces of the host machine. If there are missing files or there are no network interfaces present, the worm will quit.[4]
Main Actions
The worm then used a random number generator to determine whether or not to check the host machine for an already extant copy of the worm. Morris apparently included this check because he was worried that if the worm was analyzed, one could simply write a program to respond positively to the worm’s query infinitely, so that the machine would never become infected. The check had a 1 in 7 chance of being skipped, which meant that 1 in 7 machines that already had the worm would be re-infected. This would go on to become the biggest problem for the Morris worm.[3]
A procedure to send a byte to a specific address was also included, which was theorized as a way to monitor the overall progress of the worm. However, as it was incorrectly implemented, the procedure was incapable of working correctly.[5] The worm would then progress to the “main loop”, which was an infinite loop consisting of scans for vulnerable hosts and an infect routine. The infect routine would check to make sure the target was not the host machine, was vulnerable, and actually existed. The worm then attempted to access this target machine via three methods in the following order: try_rsh, try_fingerd, and try_sendmail. Each of these processes targeted a vulnerable service or protocol in an attempt to spread the worm in a variety of ways. If none of these methods were successful, the worm would mark the host as “immune” (see previous check for vulnerability) and return to the loop. If successful, the host infection would trigger the copy process and the worm would now begin operating on the target machine.
Results
The Spread of the Worm
Morris originally deployed the worm from MIT in an attempt to disguise its origins. However, when Morris first began to realize what was happening due to the inclusion of the re-infection chance, he contacted a friend at Harvard and together they anonymously released a message to the Harvard network detailing to programmers how to remove and halt the spread of the worm. Unfortunately, because of the load on the network due to the worm, this message was delayed and ultimately came too late.[6]
One of the largest causes of the uncontrolled spread was network administrators' improper identification that sendmail was the sole method of infection. Sysadmins and network staff who noticed that the worm was spreading through try_sendmail closed their mail servers in an attempt to halt the worm. Unfortunately, as there were several other methods by which the worm could spread, the result was that many networks were unable to receive emails from researchers and other professionals with instructions on how to stop the worm, while at the same time allowing the worm to continue spreading unchecked via try_rsh and try_fingerd.
Trial of Robert Morris
When Morris was eventually formally prosecuted, the case was done so under the 1986 Computer Fraud and Abuse Act, which had as of that point never been used in a conviction.
Morris attempted a defense based mainly around the grammar and wording of the law[2], which the courts found lacking as it mainly sought to argue that Morris' access was not "unauthorized", but that he instead "exceeded authorized access" because he was in fact an authorized user of the network.
Morris was found guilty of violations of the Computer Fraud and Abuse Act, and was sentenced to three years of probation, 400 hours of community service, a $10,050 fine, and cost of supervision.
Aftermath and Change in Computer Security Awareness
While Robert Morris had not intended for the worm to become the destructive force that it did, the U.S. Government Accountability Office estimated the damage caused by the worm to be between $100,000 and $10,000,000. While many people claim the worm affected around 6,000 major UNIX machines, Paul Graham said “I was there when this statistic was cooked up, and this was the recipe: someone guessed that there were about 60,000 computers attached to the Internet, and that the worm might have infected ten percent of them." The worm spread incredibly fast, and was the world’s first self-propagating worm to cause widespread damage.
The reason the worm became such a hazard was because of the aforementioned ability to skip the check for an already existing copy of the worm. Because the worm used system resources, multiple copies of the worm acting from the same host machine would have the same effect as another type of virus known as a “fork bomb”, consuming so many system resources that the host machine slows or crashes. Morris’ underestimation of the appropriate rate of automatic infection caused an estimated tens of thousands of computers to become incapacitated, and it was estimated that between $200 and $53,000 was required per facility to undo the damage caused by the Morris worm.[6]
Morris also set an important milestone for the United States justice system. Morris’ case was the first conviction ever under the 1986 Computer Fraud and Abuse Act[2], which provided a clear message to the public that even unintentional damage caused by computer tampering was punishable under the law.
Ethical Implications
When designing autonomous agents such as worms or artificial intelligences, it is always important to understand the implications of our actions. The programmer of the Morris worm did not intend the worm to run amok and create the damage that it did, but the courts did not find that this exonerated him of responsibility. An artificial agent that does not have the ability to change itself or make real decisions is likely bound in terms of responsibility to its creator. However, this creates the question of how the gradient itself works. Where does the line exist? Are we free to assign absolute responsibility to the creator of the program? In reality, the context and intent of the creation itself likely have a serious bearing on how we assign blame. Furthermore, the result of the Morris worm was the discovery of many flaws in UNIX and its related programs that changed the way Internet security progressed from that point on.