Difference between revisions of "Mirai Botnet"
| Line 1: | Line 1: | ||
| − | The Mirai botnet is a network of Internet of Things (IoT) devices infected with Mirai malware, used for massive | + | The Mirai botnet is a network of Internet of Things (IoT) devices infected with Mirai malware, used for massive distributed denial of service (DDoS) attacks. The Mirai malware was discovered in August 2016 by MalwareMustDie<ref>http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html</ref>, and it’s first major attack was on computer security expert Brian Krebs’s personal website <ref>http://www.computerworlduk.com/security/krebs-ddos-aftermath-industry-in-shock-at-size-depth-complexity-of-attack-3646809/</ref>. The botnet gained mainstream notoriety after performing the largest DDoS attack in history against DNS provider Dyn in October 2016 <ref>https://www.flashpoint-intel.com/action-analysis-mirai-botnet-attacks-dyn/</ref>. The Mirai Botnet is now being rented on dark web for performing DDoS attacks for high paying clients <ref>https://www.cyberscoop.com/mirai-botnet-for-sale-ddos-dark-web/</ref> |
==Technical Notes== | ==Technical Notes== | ||
| + | ===Distributed denial-of-service (DDoS) attacks=== | ||
| + | A denial-of-service (DoS) attack is an attack that sends excessive amounts of requests from a device on the Internet to flood a victim network with traffic. The intent of a DoS attack is to create enough congestion to render a service or website unusable. A distributed denial-of-service (DDoS) attack uses a collection of devices on the Internet to flood the victim with traffic from many devices. The collection of devices used in a DDoS attack are often referred to as a botnet, and are often exploited without their owner's consent.<ref>https://www.us-cert.gov/ncas/tips/ST04-015</ref> | ||
| + | |||
| + | ===Mirai Malware=== | ||
Mirai malware targets poorly secured IoT devices by brute-forcing into them with a list of common usernames and passwords. Mirai then infects the device with software which gives control of the its network resources to a central server. Devices will remain infected until they are rebooted. Mirai’s inventor claims that the botnet uses upwards of 380,000 devices in an attack at a rate of 620 Gbps <ref>https://krebsonsecurity.com/2016/10/source-code-for-iot-botnet-mirai-released/</ref>. | Mirai malware targets poorly secured IoT devices by brute-forcing into them with a list of common usernames and passwords. Mirai then infects the device with software which gives control of the its network resources to a central server. Devices will remain infected until they are rebooted. Mirai’s inventor claims that the botnet uses upwards of 380,000 devices in an attack at a rate of 620 Gbps <ref>https://krebsonsecurity.com/2016/10/source-code-for-iot-botnet-mirai-released/</ref>. | ||
refInterestingly, Mirai has a list of hardcoded IP addresses in the source code to avoid attacking. The list includes Hewlett-Packard, General Electric, and the US Postal Service. <ref>https://www.incapsula.com/blog/malware-analysis-mirai-ddos-botnet.html</ref> | refInterestingly, Mirai has a list of hardcoded IP addresses in the source code to avoid attacking. The list includes Hewlett-Packard, General Electric, and the US Postal Service. <ref>https://www.incapsula.com/blog/malware-analysis-mirai-ddos-botnet.html</ref> | ||
| Line 7: | Line 11: | ||
==Krebs Attack== | ==Krebs Attack== | ||
| − | The September 20th attack on computer security blogger Brian Krebs's website, KrebsOnSecurity.com, was the first major attack of the Mirai Botnet. The attack was estimated to have been around 620 gbps, which was approximately twice as large than any prior DDoS attack on record. Content Distribution Network provider Akamai thwarted the attack | + | The September 20th attack on computer security blogger Brian Krebs's website, KrebsOnSecurity.com, was the first major attack of the Mirai Botnet. The attack was estimated to have been around 620 gbps, which was approximately twice as large than any prior DDoS attack on record. Content Distribution Network provider Akamai thwarted the attack, and released a special State of the Internet report following it. |
| − | + | ||
| − | + | ||
==Dyn Attack== | ==Dyn Attack== | ||
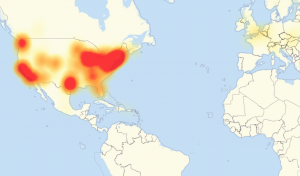
| + | [[File:DynAttack.png|thumb|right]] | ||
| + | On October 21st, the Mirai botnet performed one of the most disruptive DDoS attacks in Internet history. The attack took down Domain Name Service (DNS) provider Dyn, a major backbone for many websites. DNS is a service that translates human readable URLs to IP addresses. When Dyn went down, many sites including Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix were rendered unreachable for most users. Estimates report that up to 100,000 IoT devices were used to power the attack which attained a throughput of up to 1.2 TBPS. <ref>http://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack/</ref> | ||
Revision as of 19:43, 20 February 2017
The Mirai botnet is a network of Internet of Things (IoT) devices infected with Mirai malware, used for massive distributed denial of service (DDoS) attacks. The Mirai malware was discovered in August 2016 by MalwareMustDie[1], and it’s first major attack was on computer security expert Brian Krebs’s personal website [2]. The botnet gained mainstream notoriety after performing the largest DDoS attack in history against DNS provider Dyn in October 2016 [3]. The Mirai Botnet is now being rented on dark web for performing DDoS attacks for high paying clients [4]
Contents
Technical Notes
Distributed denial-of-service (DDoS) attacks
A denial-of-service (DoS) attack is an attack that sends excessive amounts of requests from a device on the Internet to flood a victim network with traffic. The intent of a DoS attack is to create enough congestion to render a service or website unusable. A distributed denial-of-service (DDoS) attack uses a collection of devices on the Internet to flood the victim with traffic from many devices. The collection of devices used in a DDoS attack are often referred to as a botnet, and are often exploited without their owner's consent.[5]
Mirai Malware
Mirai malware targets poorly secured IoT devices by brute-forcing into them with a list of common usernames and passwords. Mirai then infects the device with software which gives control of the its network resources to a central server. Devices will remain infected until they are rebooted. Mirai’s inventor claims that the botnet uses upwards of 380,000 devices in an attack at a rate of 620 Gbps [6]. refInterestingly, Mirai has a list of hardcoded IP addresses in the source code to avoid attacking. The list includes Hewlett-Packard, General Electric, and the US Postal Service. [7]
Krebs Attack
The September 20th attack on computer security blogger Brian Krebs's website, KrebsOnSecurity.com, was the first major attack of the Mirai Botnet. The attack was estimated to have been around 620 gbps, which was approximately twice as large than any prior DDoS attack on record. Content Distribution Network provider Akamai thwarted the attack, and released a special State of the Internet report following it.
Dyn Attack
On October 21st, the Mirai botnet performed one of the most disruptive DDoS attacks in Internet history. The attack took down Domain Name Service (DNS) provider Dyn, a major backbone for many websites. DNS is a service that translates human readable URLs to IP addresses. When Dyn went down, many sites including Twitter, Amazon, Tumblr, Reddit, Spotify and Netflix were rendered unreachable for most users. Estimates report that up to 100,000 IoT devices were used to power the attack which attained a throughput of up to 1.2 TBPS. [8]- ↑ http://blog.malwaremustdie.org/2016/08/mmd-0056-2016-linuxmirai-just.html
- ↑ http://www.computerworlduk.com/security/krebs-ddos-aftermath-industry-in-shock-at-size-depth-complexity-of-attack-3646809/
- ↑ https://www.flashpoint-intel.com/action-analysis-mirai-botnet-attacks-dyn/
- ↑ https://www.cyberscoop.com/mirai-botnet-for-sale-ddos-dark-web/
- ↑ https://www.us-cert.gov/ncas/tips/ST04-015
- ↑ https://krebsonsecurity.com/2016/10/source-code-for-iot-botnet-mirai-released/
- ↑ https://www.incapsula.com/blog/malware-analysis-mirai-ddos-botnet.html
- ↑ http://dyn.com/blog/dyn-analysis-summary-of-friday-october-21-attack/