Difference between revisions of "Low Orbit Ion Cannon"
| (24 intermediate revisions by 9 users not shown) | |||
| Line 1: | Line 1: | ||
| + | {{Nav-Bar|Topics##}}<br> | ||
{{SoftwareInfoBox | {{SoftwareInfoBox | ||
|NAME=Low Orbit Ion Cannon (LOIC) | |NAME=Low Orbit Ion Cannon (LOIC) | ||
| − | |HEIGHT= | + | |HEIGHT=480 |
|LOGO=Loiclogo.png | |LOGO=Loiclogo.png | ||
|SCREENIMAGE=Loic.jpg | |SCREENIMAGE=Loic.jpg | ||
|CAPTION=''The Low Orbit Ion Cannon is free to download and easy to use.'' | |CAPTION=''The Low Orbit Ion Cannon is free to download and easy to use.'' | ||
|IMAGEURL=https://www.google.com/url?sa=i&rct=j&q=&esrc=s&source=images&cd=&cad=rja&uact=8&ved=0ahUKEwiU-9KM1fnRAhXr7YMKHSz4CvcQjRwIBw&url=https%3A%2F%2Fsourceforge.net%2Fprojects%2Floic%2F&psig=AFQjCNHn4v5gk789NOmmSD5uwuJC9S7FUg&ust=1486408424520383 | |IMAGEURL=https://www.google.com/url?sa=i&rct=j&q=&esrc=s&source=images&cd=&cad=rja&uact=8&ved=0ahUKEwiU-9KM1fnRAhXr7YMKHSz4CvcQjRwIBw&url=https%3A%2F%2Fsourceforge.net%2Fprojects%2Floic%2F&psig=AFQjCNHn4v5gk789NOmmSD5uwuJC9S7FUg&ust=1486408424520383 | ||
| + | |TEXT=Site | ||
|TYPE=Network Stress-Testing Software | |TYPE=Network Stress-Testing Software | ||
|COMPANY=Praetox Technologies | |COMPANY=Praetox Technologies | ||
| Line 13: | Line 15: | ||
|PRODUCT=Praetox Technologies | |PRODUCT=Praetox Technologies | ||
|SITEURL=https://sourceforge.net/projects/loic/ | |SITEURL=https://sourceforge.net/projects/loic/ | ||
| + | |URLTEXT=https://sourceforge.net/projects/loic/ | ||
}} | }} | ||
| − | '''{{initial|L}}ow Orbit Ion Cannon''' (LOIC) | + | '''{{initial|L}}ow Orbit Ion Cannon''' (LOIC) is an online tool used to automate a computer to make HTTP, UDP, or TCP requests to a website at a certain frequency as determined by the user <ref name="infosec">{{cite web |
| + | | url = http://resources.infosecinstitute.com/loic-dos-attacking-tool/#gref | ||
| + | | title = LOIC (Low Orbit Ion Cannon) - DOS attacking tool | ||
| + | | author = Deepanker Verma | ||
| + | | date = December 20, 2011 | ||
| + | | website = www.resources.infosecinstitute.com | ||
| + | | publisher = Infosec Institute | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref>. Created by Praetox Technologies in 2014, LOIC is free to download and is not illegal to have on your machine in principle.<ref>https://sourceforge.net/projects/loic/</ref> This tool also has potential to be used maliciously. If coordinated with sufficient users and/or machines, LOIC can be utilized to DDoS a targeted website. As of now, LOIC is one of the most powerful DOS attacking tools freely available for people to download. Yet, one of it's biggest drawbacks is that the attacker is very vulnerable to being identified as LOIC does not hide the IP (Internet Protocol) address of the attacker. While the tool can be used to test a website's defenses, it can also be used to take down sites and threaten open internet status. | ||
| + | ==History of Use== | ||
| + | ===Anonymous, Project Chanology=== | ||
| + | The most notable usage of the LOIC client was by hacktivist group [[Anonymous (group)|Anonymous]] during [[Anonymous (group)#Operation Payback|Operation Payback]] in September of 2010. One company that was targeted during this campaign was Amazon, since it was one of the companies that attempted to censor Wikileaks. However, the attack appeared to have failed. Anonymous started attacking the company's website at 11am EST, but upon realizing how little impact they were doing, stopped the attack. <ref>{{cite web | ||
| + | | url = http://www.techworld.com/news/security/amazoncom-appears-to-repel-anonymous-ddos-attack-3252813 | ||
| + | | title = Amazon.com appears to repel Anonymous DDoS attack | ||
| + | | author = Jaikumar Vijayan | ||
| + | | date = December 10, 2010 | ||
| + | | website = www.techworld.com | ||
| + | | publisher = Computerworld US | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> The attack barely made any impact on the Amazon.com, which makes sense considering how big Amazon's network infrastructure is. With the failed attempt, Anonymous focused instead on api.Paypal.com | ||
| + | ===Operation Payback=== | ||
| + | Operation Payback was a coordinated cyber attack carried about by a group of computer scientists and hackers. The members identified themselves as part of the hacking group "Anonymous" and carried out the attacks from approximately September 2010 to January 2011<ref>Vaas, Lisa. ''US indicts 13 suspected Anonymous members for Operation Payback''. 0 Oct. 2013. [https://nakedsecurity.sophos.com/2013/10/07/us-indicts-13-suspected-anonymous-members-for-operation-payback/ "SOPHOS - Naked Security"]</ref>. The Window's version of LOIC has a "Hivemind" feature, allowing a user to point their copy of LOIC at an Internet Relay Chat server, which allows someone else to control what site all the connected LOIC clients are aimed at. This tactic of letting a central administrator control where everything is targeted was used for Operation Payback. | ||
| + | |||
| + | The attacks were carried out in the name of defending computer piracy and targeted those who supported its end. Using the Low Orbit Ion Cannon, hackers performed Distributed Denial of Service (DDoS) on multiple websites. Notable attack targets included banking websites such as Paypal, Visa, and MasterCard as well as the Recording Industry Association of America and The Motion Picture Association of America; two groups that directly fought piracy. The attacks were made in retaliation of efforts from Aiplex Software (hired by Bollywood companies) to DDoS various illegal video and music torrenting websites. Other motivations for the attack included MasterCard's cutoff of funding to "Wikileaks"<ref>Theriault, Carole. ''Hackers bring down Mastercard site for cutting off WikiLeaks''. 08 Dec. 2010. [https://nakedsecurity.sophos.com/2010/12/08/hackers-bring-down-mastercard-for-cutting-off-wikileaks/ "SOPHOS - Naked Security"]</ref>. | ||
| + | |||
| + | While the targeted sites reported over 1,000 individual attackers, only 13 were charged. All 13 were charged with one count of "conspiracy to intentionally cause damage to a protected computer". Paypal stated it accumulated up $5.6 in losses as a result of the attacks<ref>Schwartz, Matthew. ''Operation Payback: Feds Charge 13 On Anonymous Attacks''. 4 Oct. 2013. [http://www.darkreading.com/attacks-and-breaches/operation-payback-feds-charge-13-on-anonymous-attacks/d/d-id/1111819 "DARK Reading"]</ref>. | ||
| − | |||
| − | |||
| − | |||
| − | ==The GUI== | + | ==The Graphical User Interface (GUI)== |
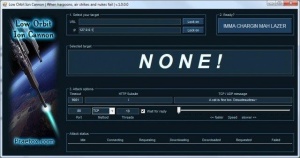
A guide<ref name="infosec"/> to the LOIC [[#Terms|GUI]]: | A guide<ref name="infosec"/> to the LOIC [[#Terms|GUI]]: | ||
* '''"Manual Mode (for pussies)"''' - Select this mode to manually select target and settings. | * '''"Manual Mode (for pussies)"''' - Select this mode to manually select target and settings. | ||
* '''"FUCKING HIVE MIND"''' - Select this mode to volunteer your computer to the [[#Terms|hive mind]], and allow it to select the target URL. Note this only allows control of the local LOIC client, and not the full machine.<ref>https://en.wikipedia.org/wiki/Internet_Relay_Chat</ref> | * '''"FUCKING HIVE MIND"''' - Select this mode to volunteer your computer to the [[#Terms|hive mind]], and allow it to select the target URL. Note this only allows control of the local LOIC client, and not the full machine.<ref>https://en.wikipedia.org/wiki/Internet_Relay_Chat</ref> | ||
| − | * ''' | + | * '''Internet Resource Chat (IRC) server''' - Location where all machines (potentially a botnet) connect to be controlled by server administrator. |
* '''Port''' - A electronic gate/path which information flows into or out of.<ref>http://whatismyipaddress.com/port</ref> Defaults to port 80. | * '''Port''' - A electronic gate/path which information flows into or out of.<ref>http://whatismyipaddress.com/port</ref> Defaults to port 80. | ||
# "Select your target" | # "Select your target" | ||
| − | #* ''' | + | #* '''URL (Uniform Resource Locator)''' - The name (reference) of the website you want to target.<ref>https://docs.oracle.com/javase/tutorial/networking/urls/definition.html</ref> |
| − | #* '''IP''' - Numerical reference to a machine on a network (where DNS is not being used).<ref>https://en.wikipedia.org/wiki/IP_address</ref> | + | #* '''IP''' - Numerical reference to a machine on a network (where DNS (Domain Name Servers) is not being used).<ref>https://en.wikipedia.org/wiki/IP_address</ref> |
# "Ready?" | # "Ready?" | ||
| − | #* '''"IMMA CHARGIN MAH LAZER"''' - Begin the HTTP/UDP/TCP bombardment of the specified address. | + | #* '''"IMMA CHARGIN MAH LAZER"''' - Begin the '''H'''yper'''t'''ext '''T'''ransfer '''P'''rotocol/'''U'''ser '''D'''atagram '''P'''rotocol/'''T'''ransmission '''C'''ontrol '''P'''rotocol (HTTP/UDP/TCP) bombardment of the specified address. |
# "Attack options" | # "Attack options" | ||
#* Allows selection of TCP/UDP message on request log (that can be used to [[#Terms|troll]]), timeout value, number of threads, and other customizations. | #* Allows selection of TCP/UDP message on request log (that can be used to [[#Terms|troll]]), timeout value, number of threads, and other customizations. | ||
| − | == | + | ==Denial of Service/Distributed Denial of Service== |
| − | DoS is an acronym that stands for "Denial of Service," and is often classified as a cyber attack. When a user attempts to visit a website, <span class="plainlinks">[http://www.google.com www.google.com]</span> for example, they are making a request to that page for information (ask for information that is stored in Google's servers to be loaded on the user's browser). The concept behind DoSing is that malicious attackers can continually send these HTTP/UDP/TCP requests to a website, and overload the site's capability to process all of the requests. If the attacker is able to achieve a sufficient threshold of requests, the site may "shut down" and be unable to process requests made by any user. This is where the attack coins its name as once the site is down, users that attempt to access the site are ''denied service'' to that page. <ref>https://www.us-cert.gov/ncas/tips/ST04-015</ref> | + | DoS is an acronym that stands for "Denial of Service," and is often classified as a cyber attack. When a user attempts to visit a website, <span class="plainlinks">[http://www.google.com www.google.com]</span> for example, they are making a request to that page for information (ask for information that is stored in Google's servers to be loaded on the user's browser). The concept behind DoSing is that malicious attackers can continually send these HTTP/UDP/TCP requests to a website, and overload the site's capability to process all of the requests. If the attacker is able to achieve a sufficient threshold of requests, the site may "shut down" and be unable to process requests made by any user. This is where the attack coins its name as once the site is down, users that attempt to access the site are ''denied service'' to that page. <ref>{{cite web |
| + | | url = https://www.us-cert.gov/ncas/tips/ST04-015 | ||
| + | | title = Security Tip (ST04-015) - Understanding Denial-of-Service Attacks | ||
| + | | author = United States Computer Emergency Readiness Team (US-CERT) | ||
| + | | date = November 04, 2009, Last Revised: February 06, 2013 | ||
| + | | website = www.us-cert.gov | ||
| + | | publisher = US-CERT | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
| − | DDoS stands for "Distributed Denial of Service," and refers to a combined effort of multiple machines attempting to shut down (DoS) a site. This set of multiple machines can take the form of multiple users with individual machines, a single user with a bot-net (link/elaborate), or a combination of the two. By utilizing more than one machine, this gives the attacker(s) the ability to send more HTTP/UDP/TCP requests. The more machines, the more requests per minute, and the more likely the site will be successfully shut down. <ref name="dig">http://www.digitalattackmap.com/understanding-ddos/</ref> | + | DDoS stands for "Distributed Denial of Service," and refers to a combined effort of multiple machines attempting to shut down (DoS) a site. This set of multiple machines can take the form of multiple users with individual machines, a single user with a bot-net (link/elaborate), or a combination of the two. By utilizing more than one machine, this gives the attacker(s) the ability to send more HTTP/UDP/TCP requests. The more machines, the more requests per minute, and the more likely the site will be successfully shut down. <ref name="dig">{{cite web |
| + | | url = http://www.digitalattackmap.com/understanding-ddos/ | ||
| + | | title = What is a DDoS Attack? | ||
| + | | author = Digital Attack Map | ||
| + | | date = 2013 | ||
| + | | website = www.digitalattackmap.com | ||
| + | | publisher = Digital Attack Map | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
| − | Additionally, a potential attacker may want to send more complicated queries, instead of basic call-and-response requests. If the functionality of the website is well known, there is the possibility of taking advantage of database and search mechanics. For example, rather than asking the website to ping the attacker back, the request (which is sent multiple times per minute) could be: a search that returns a million results, a complicated search that eats up computing power, or a combination of the two. <ref>https://www.pluralsight.com/blog/it-ops/ethical-hacking-how-to-create-a-dos-attack</ref> | + | Additionally, a potential attacker may want to send more complicated queries, instead of basic call-and-response requests. If the functionality of the website is well known, there is the possibility of taking advantage of database and search mechanics. For example, rather than asking the website to ping the attacker back, the request (which is sent multiple times per minute) could be: a search that returns a million results, a complicated search that eats up computing power, or a combination of the two. <ref>{{cite web |
| + | | url = https://www.pluralsight.com/blog/it-ops/ethical-hacking-how-to-create-a-dos-attack | ||
| + | | title = Ethical Hacking: How to Create a DoS Attack | ||
| + | | author = Mike Danseglio | ||
| + | | date = November 16, 2012 | ||
| + | | website = www.pluralsight.com | ||
| + | | publisher = Plural Sight | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
Where there is power there is money: DDoS attacks can be purchased on the black market using [[Tor|Tor]] browsers. Customers can "purchase" DDoS attacks of various strengths and duration, which have an additional set of [[#Ethical Implications|ethical implications]]. The attacks are fairly cheap to purchase: "$150 can buy a week-long DDoS attack on the black market," which increases the accessibility to a powerful tool by the general public.<ref name="dig"/> | Where there is power there is money: DDoS attacks can be purchased on the black market using [[Tor|Tor]] browsers. Customers can "purchase" DDoS attacks of various strengths and duration, which have an additional set of [[#Ethical Implications|ethical implications]]. The attacks are fairly cheap to purchase: "$150 can buy a week-long DDoS attack on the black market," which increases the accessibility to a powerful tool by the general public.<ref name="dig"/> | ||
| Line 48: | Line 97: | ||
===Damage=== | ===Damage=== | ||
| − | + | From a user point-of-view, a service-denial attack makes the website that the user is trying to visit inaccessible. Examples of outcomes would be as subtle as the inability to read an article online, or as extremely disruptive as having a bank's login portal be unreachable. From the website owner's point-of-view, a service-denial attack can potentially be catastrophic. On the mildest end, the server would just need to be rebooted and brought back online, on the most extreme end, this attack could potentially bring down a company. | |
| − | Perhaps even more | + | Perhaps even more detrimental than monetary losses is the exposure of a company's online weaknesses . Websites can be brought online again and systems rebooted, but once a website is shown to be insecure, a company's goods and services may also be deemed insecure. For example, on New Years Eve 2015, BBC.com, the website of one of the largest public service broadcasters in the United Kingdom, was taken down because of major DoS attack<ref>{{cite web |
| + | | url = http://www.telegraph.co.uk/news/bbc/12075679/BBC-website-crashes-and-Twitter-goes-into-meltdown.html | ||
| + | | title = BBC's network of websites and iPlayer service suffers DDoS attack | ||
| + | | author = Lexi Finnigan, and Mark Mollow | ||
| + | | date = December 31, 2015 | ||
| + | | website = www.telegraph.co.uk | ||
| + | | publisher = The Telegraph | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref>. This attack targeted BBC's entire network of websites as well as their iPlayer streaming service and thousands of users were reporting having "Internal Server Errors" at 8:30AM on New Years Day. BBC later published an apology and article of the attack, but the attack did hurt the public image, as security experts noted that BBC should have been protected against such an attack because of how much data is requested every day. Many Twitter users tweeted out various jokes about the website with the hashtag #bbcdown. | ||
| + | |||
| + | While perpetrators can usually get away with attacks while remaining in the shadows, the true damage of the attack comes from shining the spotlight upon the company's weaknesses. Even if only a small amount of data is leaked after a LOIC attack (granted that the attack yields some publishable material), the loss in customer trust in the future can potentially be far more economically crippling than the cost of a server reboot.<ref>{{cite web | ||
| + | | url = http://www.tandfonline.com/doi/full/10.3402/egp.v6i4.22527 | ||
| + | | title = Is it OK to be an Anonymous? | ||
| + | | author = Philip Serracino-Inglott | ||
| + | | date = December 13, 2013 | ||
| + | | website = www.tandfonline.com | ||
| + | | publisher = Taylor & Francis Online | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
*Loss of intellectual property | *Loss of intellectual property | ||
*Infection of viruses | *Infection of viruses | ||
| − | <ref>https://lp.incapsula.com/rs/incapsulainc/images/eBook%20-%20DDoS%20Impact%20Survey.pdf</ref> | + | <ref>{{cite web |
| + | | url = https://lp.incapsula.com/rs/incapsulainc/images/eBook%20-%20DDoS%20Impact%20Survey.pdf | ||
| + | | title = Incapsula Survey: What DDoS Attacks Really Cost Businesses | ||
| + | | author = Tim Matthews | ||
| + | | date = 2014 | ||
| + | | website = www.lp.incapsula.com | ||
| + | | publisher = Incapsula | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
| − | ===Defenses Against DoSing/DDoSing:=== | + | ===Defenses Against DoSing / DDoSing:=== |
| − | One of the first lines of defense when protecting against a DoS or a DDoS attack is filtering the traffic that is coming through the network. This can take the form of having either the ISP (internet service provider) buffering the users attempting to connect or firewalls that sit on the edge of the network that attempt to identify suspicious users. By attempting to identify users that have previous association with BotNets or spamming, websites can preemptively prevent attacks. This can either take the form of rejecting requests outright, or simplify flagging them for investigation by an administrator.<ref name="biz">http://www.biztechmagazine.com/article/2013/02/three-elements-defense-against-denial-service-attacks</ref> | + | One of the first lines of defense when protecting against a DoS or a DDoS attack is filtering the traffic that is coming through the network. This can take the form of having either the ISP (internet service provider) buffering the users attempting to connect or firewalls that sit on the edge of the network that attempt to identify suspicious users. By attempting to identify users that have previous association with BotNets or spamming, websites can preemptively prevent attacks. This can either take the form of rejecting requests outright, or simplify flagging them for investigation by an administrator.<ref name="biz">{{cite web |
| + | | url = http://www.biztechmagazine.com/article/2013/02/three-elements-defense-against-denial-service-attacks | ||
| + | | title = The Three Elements of Defense Against Denial-of-Service Attacks | ||
| + | | author = Mike Chapple | ||
| + | | date = February 28, 2013 | ||
| + | | website = www.biztechmagazine.com | ||
| + | | publisher = BizTech | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
| − | Another takes advantage of the optional message that is attached to any HTTP request. By default, LOIC inputs “Somos legión!” (“We are legion!”) in this message box. Therefore, one way to defend against floods that attempt to DDoS is by scrubbing requests and searching for well known strings. Scrubbing for “Somos legión!” hopefully removes many first time users that didn't change the default message, and likely don't understand the consequences of their actions. Other popular strings are “U dun goofed” and similar messages, which were popular during the Wikileaks attacks of 2010. The difficulty of this type of security comes both the inability to predict all strings that attackers could use, and the double edged sword of accidentally refusing connection to legitimate users that unfortunately have a matching blacklisted string in their URL.<ref>https://devcentral.f5.com/articles/defending-against-the-low-orbit-ion-cannon-loic</ref> | + | Another takes advantage of the optional message that is attached to any HTTP request. By default, LOIC inputs “Somos legión!” (“We are legion!”) in this message box. Therefore, one way to defend against floods that attempt to DDoS is by scrubbing requests and searching for well known strings. Scrubbing for “Somos legión!” hopefully removes many first time users that didn't change the default message, and likely don't understand the consequences of their actions. Other popular strings are “U dun goofed” and similar messages, which were popular during the Wikileaks attacks of 2010. The difficulty of this type of security comes both the inability to predict all strings that attackers could use, and the double edged sword of accidentally refusing connection to legitimate users that unfortunately have a matching blacklisted string in their URL.<ref>{{cite web |
| + | | url = https://devcentral.f5.com/articles/defending-against-the-low-orbit-ion-cannon-loic | ||
| + | | title = Defending against the Low-Orbit-Ion-Cannon (LOIC) | ||
| + | | author = Mike Chapple | ||
| + | | date = February 28, 2013 | ||
| + | | website = www.biztechmagazine.com | ||
| + | | publisher = BizTech | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
A last resort to resisting being taken offline, websites can bolster their defenses through the purchase of adequate bandwidth. Because LOIC - used as a method for DoSing/DDoSing - relies mainly on congesting HTTP traffic, possessing enough bandwidth can foil most attacks made using the client. Unless the LOIC attack utilizes thousands or tens-of-thousands of machines, companies with enough money and important websites to protect can purchase enough bandwidth to resist an average LOIC attack while still hosting usual traffic. The downside to this is cost, and usually only larger companies will have the capital to use this as a last resort.<ref name="biz"/> | A last resort to resisting being taken offline, websites can bolster their defenses through the purchase of adequate bandwidth. Because LOIC - used as a method for DoSing/DDoSing - relies mainly on congesting HTTP traffic, possessing enough bandwidth can foil most attacks made using the client. Unless the LOIC attack utilizes thousands or tens-of-thousands of machines, companies with enough money and important websites to protect can purchase enough bandwidth to resist an average LOIC attack while still hosting usual traffic. The downside to this is cost, and usually only larger companies will have the capital to use this as a last resort.<ref name="biz"/> | ||
| Line 66: | Line 157: | ||
* tollgate | * tollgate | ||
| − | ==HOIC== | + | ==High Orbit Ion Cannon (HOIC)== |
| − | The High Orbit Ion Cannon (HOIC) is the "big brother" of LOIC. While the low orbit cannon focuses mainly on TCP/UDP attacks, HOIC is the HTTP focused cannon.<ref name="symantec">https://www.symantec.com/connect/blogs/high-orbit-vs-low-orbit-ion-cannonglimps-some-hacking-techniques</ref> | + | The High Orbit Ion Cannon (HOIC) is the "big brother" of LOIC. While the low orbit cannon focuses mainly on TCP/UDP attacks, HOIC is the HTTP focused cannon.<ref name="symantec">{{cite web |
| + | | url = https://www.symantec.com/connect/blogs/high-orbit-vs-low-orbit-ion-cannonglimps-some-hacking-techniques | ||
| + | | title = High Orbit Vs Low Orbit .....ION Cannon........glimps into some hacking techniques | ||
| + | | author = Avkash K | ||
| + | | date = March 15, 2012 | ||
| + | | website = www.symantec.com | ||
| + | | publisher = Symantec Corporation | ||
| + | | accessdate = Retrieved on April 17, 2017 }} | ||
| + | </ref> | ||
==Ethical Implications== | ==Ethical Implications== | ||
===Pros=== | ===Pros=== | ||
| − | * | + | * '''Stress testing websites' abilities to handle large numbers of requests at a time''' |
| − | Another reason to allow LOIC to prevail on the internet simply falls back upon the First Amendment. The law promising freedom of religion, press, assembly, speech, and petetion of the government can be extrapolated to include the usage of LOIC. At its core, the Cannon is simply making requests to a webpage, just like any other user during that day. Opponents, however, argue that this is splitting hairs; the program may be built upon the legal accessing of a website, but attackers can't deny (especially if a site is brought down) that they used the tool for malicious activities. Clearly the hardpoint lies at the intersection of freedoms guarenteed by the First Amendment and the expectation of the website's owner that their website not be targeted and attacked.<ref>https://books.google.com/books?id=_5GtAwAAQBAJ&pg=PA136&lpg=PA136&dq=loic+and+first+amendment&source=bl&ots=fhvlREIcND&sig=Wi5qMZf2LCQWvLaQ65dC-tLw--s&hl=en&sa=X&sqi=2&ved=0ahUKEwiVkdbxvdHSAhVH74MKHfJ9DFgQ6AEILjAD#v=onepage&q=loic%20and%20first%20amendment&f=false</ref> | + | Another reason to allow LOIC to prevail on the internet simply falls back upon the [https://en.wikipedia.org/wiki/First_Amendment_to_the_United_States_Constitution First Amendment]. The law promising freedom of religion, press, assembly, speech, and petetion of the government can be extrapolated to include the usage of LOIC. At its core, the Cannon is simply making requests to a webpage, just like any other user during that day. Opponents, however, argue that this is splitting hairs; the program may be built upon the legal accessing of a website, but attackers can't deny (especially if a site is brought down) that they used the tool for malicious activities. Clearly the hardpoint lies at the intersection of freedoms guarenteed by the First Amendment and the expectation of the website's owner that their website not be targeted and attacked.<ref>https://books.google.com/books?id=_5GtAwAAQBAJ&pg=PA136&lpg=PA136&dq=loic+and+first+amendment&source=bl&ots=fhvlREIcND&sig=Wi5qMZf2LCQWvLaQ65dC-tLw--s&hl=en&sa=X&sqi=2&ved=0ahUKEwiVkdbxvdHSAhVH74MKHfJ9DFgQ6AEILjAD#v=onepage&q=loic%20and%20first%20amendment&f=false</ref> |
| − | * | + | * '''Uniting tech community/hackers''' |
===Cons=== | ===Cons=== | ||
* DDoSing a given website and "taking it down" | * DDoSing a given website and "taking it down" | ||
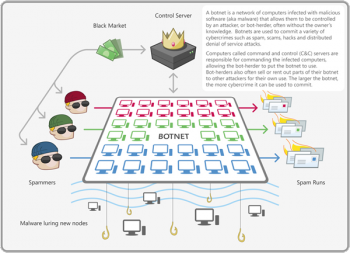
[[File:Botnet.png|right|350px|thumb|Botnets are often bought and sold on the Black Market. More "bots", means more power, which means more value.]] | [[File:Botnet.png|right|350px|thumb|Botnets are often bought and sold on the Black Market. More "bots", means more power, which means more value.]] | ||
| − | + | LOIC is more damaging when a computer cluster or botnet runs it while targeting a host. A botnet will create more internet traffic and is more effective in overwhelming a server than a single computer. Attackers attempt to control LOIC through many machines to utilize this property. Due to a high demand, botnets are rented and sold on the black market to attackers. In the scope of this article, there are two types of botnets: voluntary and involuntary (infected). As described above, LOIC's Hive Mind feature allows users to 'voluntarily' donate part of their machine to joining the botnet. However, there are also plenty of botnets that utilize machines - unbeknownst to their civilian users. Using injected malware, "botmasters" or "botherders" are able to control infected machines, usually through IRC servers. Once a couple machines are under control, it is even easier to use them to spam other computers, inject the same malware, and gain an even larger botnet. Therefore, the accumulation of larger and larger botnets are heavily incentivized as the ownership of them is very closely correlated to raw power.<ref>https://www.incapsula.com/ddos/ddos-attacks/botnet-ddos.html</ref> | |
* anyone can use: don't understand gravity of actions | * anyone can use: don't understand gravity of actions | ||
* furthering personal agendas/hurting competition/payback (all refer to purchasing of DDoS attacks) | * furthering personal agendas/hurting competition/payback (all refer to purchasing of DDoS attacks) | ||
==Terms== | ==Terms== | ||
| − | |||
* Hive Mind - The collective group of users/machines connected to LOIC IRC server | * Hive Mind - The collective group of users/machines connected to LOIC IRC server | ||
* [[Troll|Troll]] - Maliciously tease someone in order to achieve an aggressive response (that the "troll" deems to be comedic) | * [[Troll|Troll]] - Maliciously tease someone in order to achieve an aggressive response (that the "troll" deems to be comedic) | ||
==References== | ==References== | ||
| − | <references /> | + | {{resource| |
| + | <references/> | ||
| + | }} | ||
| + | |||
| + | [[Category: Software]] | ||
Latest revision as of 16:40, 17 April 2018
|
Contents
History of Use
Anonymous, Project Chanology
The most notable usage of the LOIC client was by hacktivist group Anonymous during Operation Payback in September of 2010. One company that was targeted during this campaign was Amazon, since it was one of the companies that attempted to censor Wikileaks. However, the attack appeared to have failed. Anonymous started attacking the company's website at 11am EST, but upon realizing how little impact they were doing, stopped the attack. [3] The attack barely made any impact on the Amazon.com, which makes sense considering how big Amazon's network infrastructure is. With the failed attempt, Anonymous focused instead on api.Paypal.com
Operation Payback
Operation Payback was a coordinated cyber attack carried about by a group of computer scientists and hackers. The members identified themselves as part of the hacking group "Anonymous" and carried out the attacks from approximately September 2010 to January 2011[4]. The Window's version of LOIC has a "Hivemind" feature, allowing a user to point their copy of LOIC at an Internet Relay Chat server, which allows someone else to control what site all the connected LOIC clients are aimed at. This tactic of letting a central administrator control where everything is targeted was used for Operation Payback.
The attacks were carried out in the name of defending computer piracy and targeted those who supported its end. Using the Low Orbit Ion Cannon, hackers performed Distributed Denial of Service (DDoS) on multiple websites. Notable attack targets included banking websites such as Paypal, Visa, and MasterCard as well as the Recording Industry Association of America and The Motion Picture Association of America; two groups that directly fought piracy. The attacks were made in retaliation of efforts from Aiplex Software (hired by Bollywood companies) to DDoS various illegal video and music torrenting websites. Other motivations for the attack included MasterCard's cutoff of funding to "Wikileaks"[5].
While the targeted sites reported over 1,000 individual attackers, only 13 were charged. All 13 were charged with one count of "conspiracy to intentionally cause damage to a protected computer". Paypal stated it accumulated up $5.6 in losses as a result of the attacks[6].
The Graphical User Interface (GUI)
- "Manual Mode (for pussies)" - Select this mode to manually select target and settings.
- "FUCKING HIVE MIND" - Select this mode to volunteer your computer to the hive mind, and allow it to select the target URL. Note this only allows control of the local LOIC client, and not the full machine.[7]
- Internet Resource Chat (IRC) server - Location where all machines (potentially a botnet) connect to be controlled by server administrator.
- Port - A electronic gate/path which information flows into or out of.[8] Defaults to port 80.
- "Select your target"
- "Ready?"
- "IMMA CHARGIN MAH LAZER" - Begin the Hypertext Transfer Protocol/User Datagram Protocol/Transmission Control Protocol (HTTP/UDP/TCP) bombardment of the specified address.
- "Attack options"
- Allows selection of TCP/UDP message on request log (that can be used to troll), timeout value, number of threads, and other customizations.
Denial of Service/Distributed Denial of Service
DoS is an acronym that stands for "Denial of Service," and is often classified as a cyber attack. When a user attempts to visit a website, www.google.com for example, they are making a request to that page for information (ask for information that is stored in Google's servers to be loaded on the user's browser). The concept behind DoSing is that malicious attackers can continually send these HTTP/UDP/TCP requests to a website, and overload the site's capability to process all of the requests. If the attacker is able to achieve a sufficient threshold of requests, the site may "shut down" and be unable to process requests made by any user. This is where the attack coins its name as once the site is down, users that attempt to access the site are denied service to that page. [11]
DDoS stands for "Distributed Denial of Service," and refers to a combined effort of multiple machines attempting to shut down (DoS) a site. This set of multiple machines can take the form of multiple users with individual machines, a single user with a bot-net (link/elaborate), or a combination of the two. By utilizing more than one machine, this gives the attacker(s) the ability to send more HTTP/UDP/TCP requests. The more machines, the more requests per minute, and the more likely the site will be successfully shut down. [12]
Additionally, a potential attacker may want to send more complicated queries, instead of basic call-and-response requests. If the functionality of the website is well known, there is the possibility of taking advantage of database and search mechanics. For example, rather than asking the website to ping the attacker back, the request (which is sent multiple times per minute) could be: a search that returns a million results, a complicated search that eats up computing power, or a combination of the two. [13]
Where there is power there is money: DDoS attacks can be purchased on the black market using Tor browsers. Customers can "purchase" DDoS attacks of various strengths and duration, which have an additional set of ethical implications. The attacks are fairly cheap to purchase: "$150 can buy a week-long DDoS attack on the black market," which increases the accessibility to a powerful tool by the general public.[12]
While there are many other types of DoS attacks and methods, we limit this article to the description above, as it relates most closely to LOIC.
Damage
From a user point-of-view, a service-denial attack makes the website that the user is trying to visit inaccessible. Examples of outcomes would be as subtle as the inability to read an article online, or as extremely disruptive as having a bank's login portal be unreachable. From the website owner's point-of-view, a service-denial attack can potentially be catastrophic. On the mildest end, the server would just need to be rebooted and brought back online, on the most extreme end, this attack could potentially bring down a company.
Perhaps even more detrimental than monetary losses is the exposure of a company's online weaknesses . Websites can be brought online again and systems rebooted, but once a website is shown to be insecure, a company's goods and services may also be deemed insecure. For example, on New Years Eve 2015, BBC.com, the website of one of the largest public service broadcasters in the United Kingdom, was taken down because of major DoS attack[14]. This attack targeted BBC's entire network of websites as well as their iPlayer streaming service and thousands of users were reporting having "Internal Server Errors" at 8:30AM on New Years Day. BBC later published an apology and article of the attack, but the attack did hurt the public image, as security experts noted that BBC should have been protected against such an attack because of how much data is requested every day. Many Twitter users tweeted out various jokes about the website with the hashtag #bbcdown.
While perpetrators can usually get away with attacks while remaining in the shadows, the true damage of the attack comes from shining the spotlight upon the company's weaknesses. Even if only a small amount of data is leaked after a LOIC attack (granted that the attack yields some publishable material), the loss in customer trust in the future can potentially be far more economically crippling than the cost of a server reboot.[15]
- Loss of intellectual property
- Infection of viruses
Defenses Against DoSing / DDoSing:
One of the first lines of defense when protecting against a DoS or a DDoS attack is filtering the traffic that is coming through the network. This can take the form of having either the ISP (internet service provider) buffering the users attempting to connect or firewalls that sit on the edge of the network that attempt to identify suspicious users. By attempting to identify users that have previous association with BotNets or spamming, websites can preemptively prevent attacks. This can either take the form of rejecting requests outright, or simplify flagging them for investigation by an administrator.[17]
Another takes advantage of the optional message that is attached to any HTTP request. By default, LOIC inputs “Somos legión!” (“We are legion!”) in this message box. Therefore, one way to defend against floods that attempt to DDoS is by scrubbing requests and searching for well known strings. Scrubbing for “Somos legión!” hopefully removes many first time users that didn't change the default message, and likely don't understand the consequences of their actions. Other popular strings are “U dun goofed” and similar messages, which were popular during the Wikileaks attacks of 2010. The difficulty of this type of security comes both the inability to predict all strings that attackers could use, and the double edged sword of accidentally refusing connection to legitimate users that unfortunately have a matching blacklisted string in their URL.[18]
A last resort to resisting being taken offline, websites can bolster their defenses through the purchase of adequate bandwidth. Because LOIC - used as a method for DoSing/DDoSing - relies mainly on congesting HTTP traffic, possessing enough bandwidth can foil most attacks made using the client. Unless the LOIC attack utilizes thousands or tens-of-thousands of machines, companies with enough money and important websites to protect can purchase enough bandwidth to resist an average LOIC attack while still hosting usual traffic. The downside to this is cost, and usually only larger companies will have the capital to use this as a last resort.[17]
- ip filtering
- tollgate
High Orbit Ion Cannon (HOIC)
The High Orbit Ion Cannon (HOIC) is the "big brother" of LOIC. While the low orbit cannon focuses mainly on TCP/UDP attacks, HOIC is the HTTP focused cannon.[19]
Ethical Implications
Pros
- Stress testing websites' abilities to handle large numbers of requests at a time
Another reason to allow LOIC to prevail on the internet simply falls back upon the First Amendment. The law promising freedom of religion, press, assembly, speech, and petetion of the government can be extrapolated to include the usage of LOIC. At its core, the Cannon is simply making requests to a webpage, just like any other user during that day. Opponents, however, argue that this is splitting hairs; the program may be built upon the legal accessing of a website, but attackers can't deny (especially if a site is brought down) that they used the tool for malicious activities. Clearly the hardpoint lies at the intersection of freedoms guarenteed by the First Amendment and the expectation of the website's owner that their website not be targeted and attacked.[20]
- Uniting tech community/hackers
Cons
- DDoSing a given website and "taking it down"
LOIC is more damaging when a computer cluster or botnet runs it while targeting a host. A botnet will create more internet traffic and is more effective in overwhelming a server than a single computer. Attackers attempt to control LOIC through many machines to utilize this property. Due to a high demand, botnets are rented and sold on the black market to attackers. In the scope of this article, there are two types of botnets: voluntary and involuntary (infected). As described above, LOIC's Hive Mind feature allows users to 'voluntarily' donate part of their machine to joining the botnet. However, there are also plenty of botnets that utilize machines - unbeknownst to their civilian users. Using injected malware, "botmasters" or "botherders" are able to control infected machines, usually through IRC servers. Once a couple machines are under control, it is even easier to use them to spam other computers, inject the same malware, and gain an even larger botnet. Therefore, the accumulation of larger and larger botnets are heavily incentivized as the ownership of them is very closely correlated to raw power.[21]
- anyone can use: don't understand gravity of actions
- furthering personal agendas/hurting competition/payback (all refer to purchasing of DDoS attacks)
Terms
- Hive Mind - The collective group of users/machines connected to LOIC IRC server
- Troll - Maliciously tease someone in order to achieve an aggressive response (that the "troll" deems to be comedic)
References
- ↑ 1.0 1.1 Deepanker Verma · (December 20, 2011) · LOIC (Low Orbit Ion Cannon) - DOS attacking tool · work · Infosec Institute · Retrieved on April 17, 2017
- ↑ https://sourceforge.net/projects/loic/
- ↑ Jaikumar Vijayan · (December 10, 2010) · Amazon.com appears to repel Anonymous DDoS attack · work · Computerworld US · Retrieved on April 17, 2017
- ↑ Vaas, Lisa. US indicts 13 suspected Anonymous members for Operation Payback. 0 Oct. 2013. "SOPHOS - Naked Security"
- ↑ Theriault, Carole. Hackers bring down Mastercard site for cutting off WikiLeaks. 08 Dec. 2010. "SOPHOS - Naked Security"
- ↑ Schwartz, Matthew. Operation Payback: Feds Charge 13 On Anonymous Attacks. 4 Oct. 2013. "DARK Reading"
- ↑ https://en.wikipedia.org/wiki/Internet_Relay_Chat
- ↑ http://whatismyipaddress.com/port
- ↑ https://docs.oracle.com/javase/tutorial/networking/urls/definition.html
- ↑ https://en.wikipedia.org/wiki/IP_address
- ↑ United States Computer Emergency Readiness Team (US-CERT) · (November 04, 2009, Last Revised: February 06, 2013) · Security Tip (ST04-015) - Understanding Denial-of-Service Attacks · work · US-CERT · Retrieved on April 17, 2017
- ↑ 12.0 12.1 Digital Attack Map · (2013) · What is a DDoS Attack? · work · Digital Attack Map · Retrieved on April 17, 2017
- ↑ Mike Danseglio · (November 16, 2012) · Ethical Hacking: How to Create a DoS Attack · work · Plural Sight · Retrieved on April 17, 2017
- ↑ Lexi Finnigan, and Mark Mollow · (December 31, 2015) · BBC's network of websites and iPlayer service suffers DDoS attack · work · The Telegraph · Retrieved on April 17, 2017
- ↑ Philip Serracino-Inglott · (December 13, 2013) · Is it OK to be an Anonymous? · work · Taylor & Francis Online · Retrieved on April 17, 2017
- ↑ Tim Matthews · (2014) · Incapsula Survey: What DDoS Attacks Really Cost Businesses · work · Incapsula · Retrieved on April 17, 2017
- ↑ 17.0 17.1 Mike Chapple · (February 28, 2013) · The Three Elements of Defense Against Denial-of-Service Attacks · work · BizTech · Retrieved on April 17, 2017
- ↑ Mike Chapple · (February 28, 2013) · Defending against the Low-Orbit-Ion-Cannon (LOIC) · work · BizTech · Retrieved on April 17, 2017
- ↑ Avkash K · (March 15, 2012) · High Orbit Vs Low Orbit .....ION Cannon........glimps into some hacking techniques · work · Symantec Corporation · Retrieved on April 17, 2017
- ↑ https://books.google.com/books?id=_5GtAwAAQBAJ&pg=PA136&lpg=PA136&dq=loic+and+first+amendment&source=bl&ots=fhvlREIcND&sig=Wi5qMZf2LCQWvLaQ65dC-tLw--s&hl=en&sa=X&sqi=2&ved=0ahUKEwiVkdbxvdHSAhVH74MKHfJ9DFgQ6AEILjAD#v=onepage&q=loic%20and%20first%20amendment&f=false
- ↑ https://www.incapsula.com/ddos/ddos-attacks/botnet-ddos.html