James Benjey
Contents
Abstract
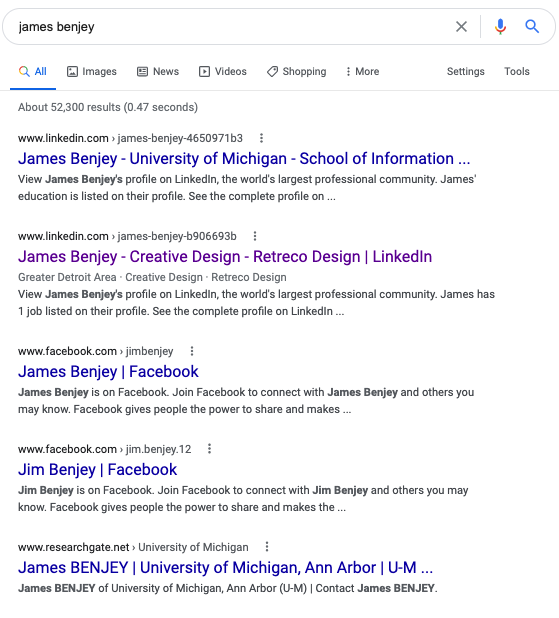
While researching “James Benjey” through google and other search engines, I compared publicly available and private data to help understand the relationship between my physical self, digital self, and the data that inforgs use to define me. I seek to understand control of data within an infosphere. Why is it difficult to create a system of data privacy when engaging with interconnected inforgs?
I organized my data into three categories: “Public data”, “Protected data”, and “Private data” to help compare characteristics of how and where my data exists and how it is used. Public data is information that exists in the public area of our infosphere, I have no control over how this information is copied and shared. Protected data is information that is not in the public area of the infosphere, I have some control over where this information is shared but less control over where it is stored. Private data is information that I have almost complete control of where it is stored and shared. This gives insight into the relationship between my online identity and other inforgs within our infosphere. The accuracy of my online identity compared to my physical identity (Physical embodiment vs. Digital embodiment) raises more questions when addressing what data inforgs use to define us. Such as, “what are the consequences of being defined by potentially inaccurate information?”.
In conclusion, I discovered obstacles that inhibit my feeling of data privacy when engaging with inforgs:
- Lack of understanding of how data is stored and used
- Lack of agency over digital embodiment.
As well as potential solutions:
- "Zero-Knowledge platform"
- The ability to control and “hold” data - and know where it is stored
Data
Methods:
- I used https://www.fastpeoplesearch.com/ to understand what information is available publicly within our infosphere.
- Google searching my name gave further public information.
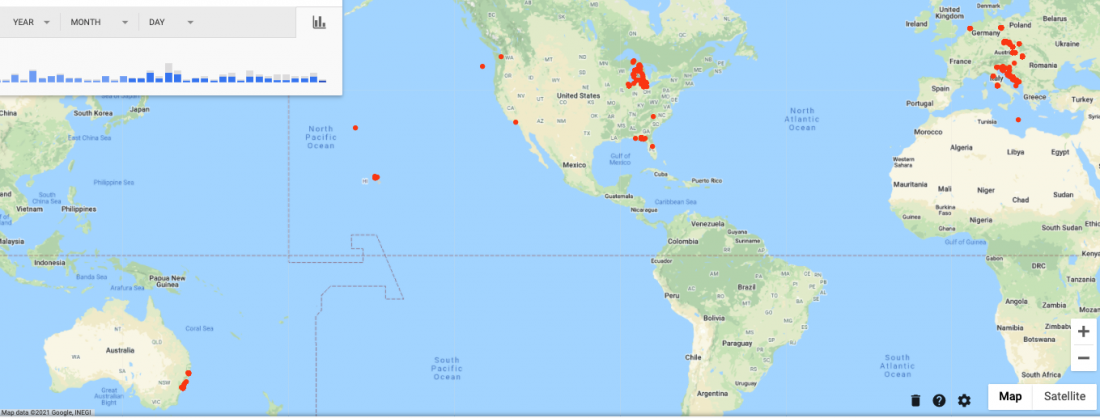
- Google’s Timeline service allows for location tracking - I used this service to review my past location history. This data is considered sensitive by Google in their policies handbook.
- Attempting to access medical records online through https://www.myuofmhealth.org/ to understand who ultimately controls my health records and information.
Public data:
- Images uploaded to public sites/servers
- Info I can find in a public search
- Address
- Phone numbers
- Past addresses
Protected data:
- Location data
- Social Security Number
- EU considers sensitive information as:
- personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs;
- trade-union membership;
- genetic data, biometric data processed solely to identify a human being;
- health-related data;
- data concerning a person’s sex life or sexual orientation.
Private data:
- My thoughts
Comparison of data
Physical embodiment vs. Digital embodiment
- The relationship between myself and my digital embodiment is somewhat accurate - there is enough inaccurate information and lack of information to question whether it can be used to represent the physical self without context. Looking closer at the details publicly available information illustrates the holes in the story. For example, I moved residences over four times during 2013 but none of those residences are listed in public records that I discovered. My thoughts are that because I did not use the addresses to receive mail or enter them online to any inforgs, they were never recorded. This is an illustration of discord between my physical and digital self. I have memories of those places however I can’t prove that I lived there unless I dig up old rent receipts. There was no digital record so it did not happen according to my digital self. In the opposite way, there are some records that I’m not sure are accurate such as a “relative” found on fastpeoplesearch.com named Cecil Mcgranahan (https://www.fastpeoplesearch.com/cecil-mcgranahan_id_G9156151579029466321). According to my digital embodiment, this person is connected to me though they do not come up in analog genealogy records.
Conclusion
Obstacles:
I believe it is difficult to control data privacy for multiple reasons.
It is difficult to understand where and how data will be shared within the infosphere: When I give my data to an inforg, it is difficult to know who else it will be shared with unless they explicitly state their intent. Engaging with some inforgs for services can involve terms and conditions that hide their intent while advertising a different service such as Robinhood, that advertises itself as a barrier free trading platform but sells your data and activity to larger trading organizations. (robinhood).
It is difficult to understand where and how data will be stored within the infosphere: It can be difficult to understand how my data will be stored. Many companies suffer data security breaches which can lead to sensitive data being released publicly into the infosphere. Some of these breaches are non-malicious human error such as Michigan Medicine releasing over 1000 email addresses of patients to the public infosphere, (https://www.uofmhealth.org/news/archive/202010/michigan-medicine-notifies-patients-email-information-breach).
These obstacles lead to a lack of agency over digital embodiment. It is difficult to control where my data is stored, shared, and used which leads to difficulty controlling data privacy.
Solutions:
In order to start feeling more in control of my data, I need to understand:
Who the data is shared with
- Clear regulatory data sharing standards among inforgs (to create trust)
- With impactful consequences for inforgs
- Consumer protection from larger inforgs
Where is the data stored
- Reduce copies of sensitive data
- Back up where I feel secure
- I want to hold an encrypted copy of data.
- Back up where I feel secure
P3 Platforms have been created to mitigate this issue.