Internet of things
The Internet of Things (IoT) is a system of interconnected devices and objects that communicate and interact with each other through a network. IoT changes everyday objects into “smart” ones, by embedding them with electronics like sensors, monitors, processors, microchips, and other forms of hardware. IoT devices can transmit real-time data, perform analytic functions, and utilize AI-based machine-learning algorithms to become “smarter” and create more value for the user as well as the manufacturer of the product. IoT is meant to transform real-world information into digital data, giving insight into how users interact with their devices as well as determine where product improvements can be made and deliver real time software updates as needed. Although IoT presents consumer and provider benefits, it also raises ethical questions that relate to privacy, security, agency, and identity - potentially violating concepts of informational privacy, physical privacy, and decisional privacy.
History
While the concept of connecting ordinary objects has existed since the 1970s in the form of embedded internet and pervasive computing innovations, IoT’s modern roots began in the 1990s. In 1990, Epilogue Technology computer programmer John Romkey, engineered a networked toaster to display at the Interop Internet networking show. Romkey was able to remotely turn the toaster on and off through an internet connection. [1]Although the device was rudimentary, it demonstrated how everyday objects could be embedded with electronics and network connectivity to function remotely.
In 1998, Mark Weiser, Chief Scientist at XEROX PARC, engineered a water fountain with internet connectivity. It was designed to access online financial information about the New York Stock Exchange, and the flow and height of the water corresponding to the market’s changes in volume and price changes. [2]
The term “IoT” was attributed to Kevin Ashton in 1999. While working at Procter & Gamble, Ashton wanted to incorporate tracking capabilities into P&G’s products. He advocated inserting radio-enabled frequency microchips (RFID) into lipstick packages so that stores could improve inventory tracking, and helped pioneer smart packaging systems. Ashton’s contributions exemplified the benefits that IoT technology could provide to retail and inventory control, enabling companies to act on real-time data metrics. [3]
In 2000, LG Electronics released the Digital DIOS, which was an internet-connected refrigerator. The fridge contained an LCD panel on its door, which had video-messaging, electronic writing, data memo, and MP3 functions. The fridge could also provide information that includes: internal temperature, the freshness of foods, nutrition levels, and recipes. It also contained an internal webcam that scanned and tracked food content. Ultimately, the fridge was considered a failure due to its high price and the fact that it required a network connection; however, it symbolized new innovations that were developing in kitchen appliance IoT devices. [4]
How IoT Works
IoT functionality has four main components which work together to make IoT systems work: hardware, connectivity, data processing, and user interface output.
Hardware
Hardware is an important aspect of all IoT devices. Sensors, monitors, microchips, and other hardware collect data. They are present in any IoT object - if it is an oven, internal sensors collect heat information and cameras collect images. If it is a wearable IoT device, sensors collect heartbeat and sleeping pattern information, while microchips collect geolocation tracking data. [5]
Connectivity
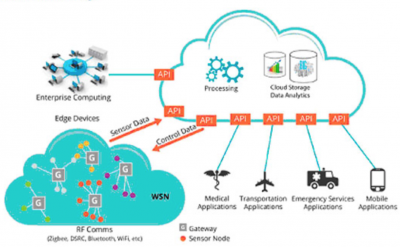
Network connectivity is the foundation on which IoT is built upon, it allows communication of difference devices through network packets. IoT devices can communicate via a range of networks, such as cellular, satellite, WiFi, Bluetooth, Ethernet, and others. Each type of network has its advantages and disadvantages in regards to network range, power consumption, and bandwidth. Cellular and satellite networks offer high range, and high bandwidth capabilities, yet they consume large amounts of power. WiFi, Bluetooth, and Ethernet networks have low power consumption and high bandwidth, yet they have low range, and can only transmit data locally. Modern IoT devices transmit data to Cloud applications, which offers centralized high data storage capacity, and analytic functions. [6]
Data Processing
Once the data gets transferred to Cloud storage applications via network APIs, it can perform data processing functions with analytic software. During this process, data architecture systems filter, aggregate, route, store, analyze, process, model, and then share data with user devices. Data is cleaned and inaccurate or missing data is improved. Notable technology companies, such as Salesforce, Amazon, and Oracle have developed Cloud software applications that specifically manage large volumes of data and provide real-time outputs. [7]
User Interface
An IoT user interface can take many forms, whether it be a text, notification, feed or browser. For example, if you have an IoT based thermostat that is preset to maintain a range of temperatures, the Cloud will process the temperature data received from the thermostat’s sensors and will alert the user via a phone notification or automatically change the temperature if it falls outside of the range. User interface design can be cross-device interactional, personalized, and provide the user with a unique experience. [8]
Applications
The nature of IoT, with its ability to connect any type of object to produce real-world data and increase value, means that it can be applied to virtually any industry or sector. Certain industries, however, have been particularly successful in integrating IoT solutions.
Smart Home
There are over 250 companies in the Smart Home application industry that collectively received over $2.5 billion in startup funding in 2018. IoT appliances include refrigerators, microwaves, ovens, sinks, and mirrors: virtually all household appliances. All of these devices generate real-time data and help homeowners better understand their use of these products, or maintain product usage at a certain level. [9] Popular applications of IoT technologies include: smart thermostats, connected lights, smart refrigerators and ovens, and smart door locks.
Another example of smart home technology occurs from the assistance of elderly individuals and those with disabilities. Assistive technology can be used to accommodate needs. For example applications that take advantage of Voice Control Systems allow for individuals with motor impairments to make their home more accessible. Smart home technology combined with health concerns can allow for more freedom in one's home to a larger population of individuals who have varying needs.
AI Assistants
Although AI Assistants and Internet of Things components are different in ways, there is an undeniable overlap via the interaction of objects and people without physical interaction. AI Assistants in the modernized, IoT home act as a nexus for control and major touchpoint for the user experience. In this realm, Amazon's Echo and Google's Google Home product are the market leaders. AI Assistants also serve a dual purpose to being simply the user interface to IoT components of an individual’s home. Through usage and going about our everyday lives, AI Assistants can record massive datasets on user behavior. The information is increasingly valuable as marketing efforts hone in on the AI Assistant realm. [10]
Wearables
Smart Clothing and wearable devices have become trendy in the marketplace after the highly-anticipated and publicized releases of the Apple Watch and the Sony Smart Trainer. These devices collect data on fitness and health metrics to provide insight on user wellbeing. For example, tracking a person's body temperature can provide an early indication of whether a sickness is coming. [11] The Apple Watch is even capable of detecting when its wearer falls and may subsequently alert emergency services.
Urban Design
IoT applications are also utilized in the designing of Smart Cities, which allow administrators and public workers to remotely control and maintain public utilities and infrastructure. City officials can embed sensors into traffic lights to reduce traffic congestion, outside of industrial plants to monitor and reduce pollution, and around high volume crime areas to improve policing.
Energy

Smart Grid IoT applications utilize electricity supplier and consumer information to improve efficiency, reliability, and cost. Suppliers can use IoT applications to measure and analyze the duration and location of power outages, and consumers can better monitor their energy consumption levels. Utilizing smart grid technology means that drastic changes will need to take place in the industry of electricity services, not only in the infrastructure department.
Environmental monitoring
Applications of IoT in the environment use sensors to assist in environmental protection. This includes the monitoring of air and water quality, atmospheric or soil conditions and can even monitor wildlife migration. The fact that IoT connects multiple devices can also encourage the use of IoT for earthquake and tsunami detection in order to provide emergency services and alerts to the public.
Transport and Logistics
Vehicle manufacturers have heavily invested in the use of IoT sensors in personal vehicles to increase operation, maintenance, and safety metrics. Side-door sensors detect oncoming vehicles, remote devices unlock doors and start engines, and cloud-connected applications monitor maintenance levels and warn of needed repairs.[12] Cars used to have one purpose, get the passengers from point A to point B. Now, cars have "'a series of interconnected software applications and capabilities' involving a host of remote connections." This shift from horse-and-buggy to IoT cars has allowed for data collection that could eventually lead to autonomous vehicles.[13]
Equally as important to data collection for cars, one of the main uses of IoT connectivity is the ability to deliver software updates. Cars today are as much computer as they are machine and they utilize many softwares to run. Programs like parking assist, self driving, navigation, cruise control, and so much more are software based and need to be updated regularly. One of the largest internet content delivery networks, Akamai Technologies, Inc., has partnered with car manufactures to create their OTA network (Over the Air). The goal of this network is to deliver real-time automatic updates to vehicles and more using IoT protocol and networks [14]. This would reduce costs for manufacturers and increase ease of mind for drivers by not having to go to the dealership to have updates done manually and not deployed in real time. This effort is also critical for getting ahead of recalls and wanting to create a safer driving experience.
As trading and shipping becomes more complex, the interest in IoT has grown in transportation and logistics. The technology allows for precise tracking during the transport process. Companies can monitor data from their cargo on ships or trucks during transit and make adjustments to the climate or other sustainability variables [15]. This control is known as [Remote Control Management (RCM)]. IoT allows for better management of the supply chain and quality control to ensure sustainability between the origin and the consumer.
IoT has also had a significant impact on the growth of scooter-sharing systems across the United States and in other countries. Scooter sharing services began in 2012 when "Scoot Networks" launched in San Francisco. [16] Since then, scooter sharing has grown rapidly among urban cities with companies such as Bird, Lime, and Lyft releasing their own, rechargeable electric scooters that pedestrians can gain access to through proprietary mobile applications.
Healthcare
Connected healthcare systems can remotely monitor and measure patient health. This information can be used by doctors to recommend treatments, the healthcare industry to measure the usefulness and effect of products and drugs, and individual users to monitor their own health metrics. One example is GE Healthcare's AutoBed, which helps assign ER patients to beds using an algorithm taking both patient data, obtained from digital medical records and environmental factors, determined from IoT sensors. This software was able to help reduce waiting time in New York City's Mt. Sinai Hospital by at least an hour for over half of applicable patients[17].
Ethical Implications
Privacy
While IoT presents many consumer benefits, the fact that it connects inanimate objects to the internet presents privacy challenges. IoT devices generate more data and network that data to Cloud applications and connected devices. This creates a space for third-party actors to access more data, which before the invention of IoT, was nonexistent and unattainable. The mass blind transfer of data to third party sources could violate Luciano Floridi's concept of informational privacy, which is "the freedom from informational interference or intrusion."[18] Whenever consumers agree to third-party data access, the legal Third-Party Doctrine states that they lose some expectation of privacy. Consumers may unknowingly consent to IoT companies and Cloud providers establishing backdoor channels to analyze the data generated by their consumers - and sell or share said data without the knowledge of the original owner. First-party providers could also market IoT-generated data to advertisers and data brokers. Additionally, more information enables third parties to create highly accurate predictive outcomes. IoT devices bridge informational gaps between users and providers, reduce transparency and erase informational frictions, which help preserve consumer privacy of sensitive information. This could potentially erase any concept of online anonymity or informational control for users, since data gathered from interactions between connected devices can now be found online - in a new infosphere - and could be accessed and/or exposed by first and third party providers, data processors, and rogue agents. Given the intimate environments in which IoT devices exist (i.e., homes), users likely assume that their personal data is well protected. However, the fact that it is common practice for IoT companies to share data with third parties suggests that this intimate data is of high value. Simply put, consumers cannot be naive when it comes to the privacy of sensitive information.
Security
Network connectivity enables IoT devices to communicate with users, but it also presents network and/or data breach liabilities. IoT devices generally function on lower cybersecurity standards. Some IoT devices still use low-grade, 2G and 3G networks to transmit data, which are less secure than the more recent generations of networks. Faulty cybersecurity standards open up possible hacking and cyber attacks for IoT devices. For example, the Mirai botnet was able to exploit IoT devices which used default security passwords and just by doing this was able to take over 380,000 IoT devices[19]. Hackers are then able to control these IoT "bots" and execute a Distributed Denial of Service attack on networks.
IoT security liabilities, specifically regarding wearable IoT devices, interfere with Floridi's concept of physical privacy, which is the "freedom from sensory interference and intrusion." [18] Consumers would not want data exposed regarding their IoT heart monitor, connected household security system, or smart car. Wearable device information can transmit data on one's exact location, and where they have previously walked. Malicious actors would have the ability to invade personal space and gain insight and information on personal bodily functions and interactions. Even non-crucial information, such as data from a connected household lighting system, can indicate when a house is empty or not. Poor IoT security makes breaches of privacy possible that could create major security concerns. [20]
Hacking
According to certain researchers, home automation devices can leave homes susceptible to hackers intruding. There has been claims that a single innocuous device such as a smart lightbulb or a smart electric switch could be an entry point for a hacker, trying to break into a home. This has to do with the fact that most "smart" devices work in tandem with a central hub or port, that has certain settings and routines. If a hacker is able to intercept and manipulate the connection between the hub and device, he or she has access to the settings of the automated home. [21] This hacking of smart appliances allows malicious actors to spy (surveillance), broadcast sound, and stalk victims, among other harmful activities. For instance, a fake warning of an incoming nuclear missile was broadcasted[22] over one family's Nest system camera - causing them great distress. People are more vulnerable than ever before. Statista estimates that by the end of 2019, there will be about 42 million smart homes. However, according to the New York Times, the "vast majority" of smart home users have not been victims of hacking[23]
Another instance of hacking smart devices is the hacking of cars. Touched on earlier, delivering software updates to cars in real time through IoT enabled networks is a great stride towards improving driver safety. However, this improvement is a double-edged sword. By connecting cars to virtually open networks, it leaves them open to various forms of hacking [24]. These hacks can turn off certain aspects of the car, such as safety systems like air bags. Working on providing a closed network for cars to utilize, like the one Akamai is working on with OTA, will help minimize the effects of hacking on driver safety.
Nevertheless, smart home and/or device users should err on the side of caution when purchasing and setting up these appliances to ensure that said they are not leveraged for harassment, control - or a means for other criminal purposes. Accordingly, there are multiple strategies of which smart device users - or smart home owners - can employ to protect themselves from intrusions. Individuals are advised to (1) strengthen the barriers of their WiFi networks (i.e., use effective passwords), (2) use unique passwords for different sites and appliances, and (3) and purchase devices only from credible and respected brands.
Agency
In 2019, nearly two-thirds of American households will contain some IoT appliance. [25]Consumers have a more comfortable and luxurious experience with appliances when they delegate the activation and maintenance to third parties. However, they lose some agency, independence, and empowerment to make personal decisions. IoT devices delegate agency from individuals, and potentially violate Floridi's concept of decisional privacy, which is "the freedom from procedural interference and intrusion." [18] When appliance functionally and maintenance are delegated to others, users are excluded from those decision making processes, lose insight on how to use devices themselves, and lose the significance and meaning of the information they are gaining. Users may begin to delegate more crucial tasks to third parties, who may not have the user's best interest at heart. This also creates an issue of informational ownership. As more functions are delegated to IoT devices, more data is transferred to third-party hands. Although users are generating the data, the companies which manage IoT systems are performing statistical analysis and data management functions. Does the analyzed data truly belong to the user or the organization which receives the raw data and performs its own analysis? This produces a grey area of intellectual property ownership, since data is being constantly transferred between IoT provider and data managers, and the data is being critically changed and edited at every step of the process. Increasingly delegating functions to others depreciates the abilities and capacities of the user, transfers ownership to third-party IoT providers, and could render users completely reliant and dependent on unconscious IoT systems.
Identity
Like many other forms of ICTs, IoTs collect and aggregate large amounts of data based on user interactions in order to create an accurate representation of the user, as well as his/her behaviors and tendencies. These digital representations of user-IoT interactions create a certain narrative about the user, and an online digital identity based on IoT generated data. David Shoemaker claims that these digital portrayals violate a user's sense of self-identity, because they capture narrow zones and aspects of user behaviors, appropriate identity management rights, and create a subjective identity of the user based on non-instrumental information. Bits and pieces of information about a user do not necessarily indicate an accurate or comprehensive representation of his/her identity, but can instead create a certain pattern that associates unrelated pieces of information - which ultimately generates an inaccurate representation of the user's identity. [26] If IoT providers present inaccurate and incomplete digital identities to crucial service providers, such as insurers and creditors, they may derive conclusions of their own (that are not grounded in truth and context) that could harm consumers. The right and value of identity management is not inherently part of IoT design since the nature of IoTs only allow them to capture bits of pieces of information in limited contexts; which may reveal its value sensitive design. Such practices that result in the inaccurate representations of a user - and invasions of his/her privacy, damage the individual's ability and autonomy to create and publicize their own self-identity.
Connectedness
As the Internet of Things continues to grow, so does our intertwining of real life and virtual life via technology. Having a device strapped to your wrist at all times, or readily available upon a shout from the kitchen, increases connectivity to the internet around the clock. This is a concern because it makes individuals less present mentally on what is in front of them in real life, and more focused on the web of users online. They may not be able to perform adequately with this distraction all the time or could potentially disregard interpersonal relations that they ignore while focused on a device.
References
- ↑ Castro, Ethan. Hidden History: John Romkey and the Internet toaster, Tech News, Fall 2017, Issue 11.
- ↑ CONNECTING THE PAST TO THE FUTURE – THE ORIGINS AND EVOLUTION OF IOT, Open Connectivity Foundation, May 10, 2018.
- ↑ Engineering and Technology History Wiki: Kevin Ashton, ETHW
- ↑ Kanellos, Michael. "Hold The Laughter: Why The Smart Fridge Is A Great Idea," Forbes, 1/13/16.
- ↑ McClelland, Calum. IoT Explained — How Does an IoT System Actually Work?, Medium, November 20, 2017
- ↑ McClelland, Calum. Types of Network Connectivity for the Internet of Things (IoT) – A Simple Explanation, IoTForAll, January 6, 2019.
- ↑ ''Building an Open Data Processing Pipeline for IoT, Cloudera, September 11, 2018.
- ↑ Lazarevich, Katherine. 5 Keys to Designing User Experience for IoT Products, IotForAll, March 30, 2018.
- ↑ Lueth, Knud Lasse. The 10 most popular Internet of Things applications right now, IoT Analytics, February 2, 2015.
- ↑ Mapping the Smart-Home Market. (n.d.). Retrieved from https://www.bcg.com/publications/2018/mapping-smart-home-market.aspx
- ↑ "Wearable Devices and the Internet of Things", https://www.mouser.com/applications/article-iot-wearable-devices/
- ↑ Kashyap, Swati. 10 Real World Applications of Internet of Things (IoT), Analytics Vidyha, August 26, 2016.
- ↑ Shaw, Johnathan. "The Watchers Assaults on Privacy in America". Harvard Magazine. 2017.
- ↑ “OTA Updates.” Akamai, www.akamai.com/us/en/products/performance/over-the-air-updates.jsp#akamai-ota-updates-explainer.
- ↑ Frye, Christopher. “Evolution of IoT in Shipping: Current and Future Trends.” The Kolabtree Blog, The Kolabtree Blog, 28 Aug. 2018, blog.kolabtree.com/evolution-of-iot-and-shipping-current-and-future-trends/
- ↑ Lawler, Ryan. "'Zipcar For Scooters' Startup Scoot Networks Launches To The Public In San Francisco." TechCrunch. https://techcrunch.com/2012/09/26/scoot-sf-launch/. Accessed April 22, 2019.
- ↑ Gittleson, Kim. "How tracking technology can better fill hospital beds", BBC "https://www.bbc.com/news/business-25059166 November 26, 2013
- ↑ 18.0 18.1 18.2 Floridi, Luciano. "Protection of Information and the Right to Privacy - A New Equilibrium?" Springer International Publishing, 6/5/14.
- ↑ “Alert (TA16-288A).” Heightened DDoS Threat Posed by Mirai and Other Botnets, www.us-cert.gov/ncas/alerts/TA16-288A.
- ↑ Richardson, Alex. Ethical Pitfalls and the Internet of Things, Aquicore.
- ↑ "How one lightbulb could allow hackers to burgle your home" https://qz.com/1493748/how-one-lightbulb-could-allow-hackers-to-burgle-your-home/
- ↑ https://www.mercurynews.com/2019/01/21/it-was-five-minutes-of-sheer-terror-hackers-infiltrate-east-bay-familys-nest-surveillance-camera-send-warning-of-incoming-north-korea-missile-attack/
- ↑ Cericola, R. (2019, March 28). How to Protect Your Smart Home From Hackers. Retrieved from https://www.nytimes.com/2019/03/27/smarter-living/wirecutter/how-to-protect-your-smart-home-from-hackers.html.
- ↑ Paul, Fredric. “Connected Cars Have an 'Indefensible' Security Vulnerability.” Network World, Network World, 23 Aug. 2017, www.networkworld.com/article/3218712/connected-cars-have-an-indefensible-security-vulnerability.html.
- ↑ Walter, Jesse. Is Law Catching Up Fast Enough with IoT Integration in the Home? Law Technology Today, September 21, 2018.
- ↑ Shoemaker, David W. "Self-exposure and exposure of the self: informational privacy and the presentation of identity," Spring Science and Business Media, 2009.


