Internet of things
The Internet of Things (IoT) is a system of interconnected devices and objects that communicate and interact through a network. IoT enhances normal everyday objects into “smart” ones, by imbedding them with electronics such as sensors, monitors, processors, microchips, and other forms of hardware. IoT devices can transmit real-time data, perform analytic functions, and utilyze AI-based machine-learning algorithms to become “smarter” and create more value for the user. IoT is meant to transform real world information into digital data, which can give insight in how users interact with their devices. Although IoT presents consumer and provider benefits, it also creates issues of privacy, security, agency, and identity; which potentially violate concepts of informational privacy, physical privacy, and decisional privacy.
Contents
History
While the concept of connecting ordinary objects had been around since the 1970s and 1980s, such as embedded internet and pervasive computing innovations, IoT’s modern roots began in the 1990s. In 1990, Epilogue Technology computer programmer, John Romkey, engineered a networked toaster to display at the Interop Internet networking show. Romkey was able to remotely turn the toaster on and off through an internet connection. [1]Although the device was rudimentary, it demonstrated how basic everyday objects, such as kitchen appliances, could be embedded with electronics and network connectivity to function remotely.
In 1998, Mark Weiser, Chief Scientist at XEROX PARC, engineered a water fountain with internet connectivity. It was designed to access online financial information about the New York Stock Exchange, and the flow and height of the water corresponded to the market’s changes in volume and price changes. [2]
The term “IoT” has been attributed to Kevin Ashton in 1999. While working at Procter & Gamble, Ashton wanted to incorporate tracking capabilities into P&G’s products. He advocated inserting radio-enabled frequency microchips into lipstick packages (RFID) so that stores could better track inventory, and helped pioneer smart packaging systems. Ashton’s contributions exemplified the benefits that IoT technology could provide to retail and inventory control, by enabling companies to act on real-time data metrics. [3]
In 2000, LG Electronics released the Digital DIOS, which was an internet-connected refrigerator. The fridge contained an LCD panel on its door, which had video-messaging, electronic writing, data memo, and MP3 functions. The fridge could also provide information such as its inside temperature, freshness of foods, nutrition levels, and recipes. It also contained an internal webcam that scanned and tracked food content. The fridge ultimately failed due to its high price and required network connection, but it symbolized new innovations that were developing in kitchen appliance IoT devices. [4]
How IoT Works
IoT functionality has four main components: hardware, connectivity, data processing, and user interface output.
Hardware
Sensors, monitors, microchips, and other hardware, are the actual components that collect data. If the IoT object is an oven, internal sensors can collect heat information and cameras can collect images. If the IoT object is a wearable, sensors can collect heartbeat and sleeping pattern information, while microchips collect geolocation tracking data. [5]
Connectivity
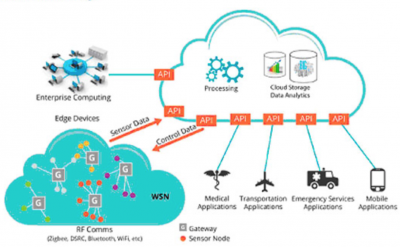
Network connectivity transmits data collected by IoT hardware to the user. IoT devices can communicate via a range of networks, such as cellular, satellite, WiFi, Bluetooth, Ethernet, and others. Each type of network has its advantages in network range, power consumption, and bandwidth. Cellular and satellite networks offer high range, and high bandwidth capabilities, yet they consume large amounts of power. WiFi, Bluetooth, and Ethernet networks have low power consumption and high bandwidth, yet they have low range, and can only transmit data locally. Modern IoT devices transmit data to Cloud applications, which offers centralized high data storage capacity, and analytic functions. [6]
Data Processing
Once the data gets transferred to Cloud storage applications via network APIs, it can perform data processing functions with analytic software. During this process, data architecture systems filter, aggregate, route, store, analyze, process, model, and then share data with user devices. Data is cleaned, and inaccurate or missing data is improved. Notable tech companies, such as Salesforce, Amazon, and Oracle have developed Cloud software applications that specifically manage large volumes of data and provide real-time outputs. [7]
User Interface
That information can then be accessed in a user-friendly interface, which may be through a text, notification, feed, or browser. An IoT user interface can take many forms. For example, if you have an IoT based thermostat that is preset to maintain a range of temperatures, the Cloud will process the temperature data received from the thermostat’s sensors, and will alert the user via a phone notification or automatically change the temperature if it falls outside of the range. User interface design can be cross-device interactional, personalized, and provide the user with a unique experience. [8]
Applications
The nature of IoT, and its ability to connect any type of object to produce real world data and increase value, means that it can be applied to virtually any industry or sector. Particular industries, however, have been especially successful in integrating IoT solutions.
Smart Home
There are over 250 companies in the Smart Home application industry that collectively received over $2.5 billion in startup funding in 2018. IoT appliances include refrigerators, microwaves, ovens, sinks, mirrors, and virtually every other household appliance. All of these devices generate real time data and help homeowners better understand their use of the products, or maintain product usage at a certain level. [9] Popular applications are smart thermostats, connected lights, smart refrigerators and ovens, and smart door locks.
Wearables
Smart Clothing and wearable devices have become trendy in the marketplace after the highly-anticipated and publicized releases of the Apple Watch and the Sony Smart Trainer. These devices collect data on fitness and health metrics to provide insight on user wellbeing.
Urban Design
IoT applications are used to designed Smart Cities, which allow administrators and public workers to remotely control and maintain public utilities and infrastructure. City officials can embed sensors into traffic lights to reduce traffic congestion, outside of industrial plants to monitor and reduce pollution, and around high volume crime areas to improve policing.
Energy

Smart Grid IoT applications utilize electricity supplier and consumer information to improve efficiency, reliability, and cost. Suppliers can use IoT applications to measure and analyze the duration and location of power outages, and consumers can better monitor their energy consumption levels.
Transport and Logistics
Vehicle manufacturers have heavily invested in the use of IoT sensors in personal vehicles to increase operation, maintenance, and safety metrics. Side-door sensors detect oncoming vehicles, remote devices unlock doors and start engines, and cloud-connected applications monitor maintenance levels and warn of needed repairs. [10]
As trading and shipping becomes more complex, the interest in IoT has grown in transportation and logistics. The technology allows for precise tracking during the transport process. Companies can monitor data from their cargo on ships or trucks during transit and make adjustments to the climate or other sustainability variables [11]. This control is known as [Remote Control Management (RCM)]. IoT allows for better management of the supply chain and quality control to ensure sustainability between the origin to the consumer.
Healthcare
Connected healthcare systems can remotely monitor and measure patient health. This information can be used by doctors to recommend treatments, the healthcare industry to measure the usefulness and effect of products and drugs, and users to monitor their own health metrics.
Ethics
Privacy
While IoT presents many consumer benefits, the fact that it connects inanimate objects to the internet presents privacy challenges. IoT devices generate more data and network that data to Cloud applications and connected devices. This creates a space for third party actors to access more data, which before the invention of IoT, was nonexistent and unobtainable. The mass blind transfer of data to third party sources could violate Luciano Floridi's concept of informational privacy, which is "the freedom from informational interference or intrusion." [12] Whenever consumers agree to third party data access, the legal Third-Party Doctrine states that they lose some expectation of privacy. Consumers may unknowingly consent to IoT companies and Cloud providers establishing backdoor channels to analyze the data generated by their consumers. First-party providers could additionally market IoT-generated data to advertisers and data brokers. Additionally, the more information that third parties contain enables them to create highly accurate predictive outcomes. IoT devices bridge informational gaps between users and providers, reduce transparency, and erase informational frictions, which help preserve consumer privacy of sensitive information. This could potentially erase any concept of online anonymity and informational control for users, since information on interactions with connected devices are now online in a new infosphere, and could be accessed and exposed by first and third party providers, data processors, and rogue agents.
Security
Network connectivity enables IoT devices to communicate with users, but it also presents network/data breach liabilities. IoT devices generally function on lower cybersecurity standards. Some IoT devices still uses low-grade, 2G and 3G networks to transmit data, which are less secure than than new generation networks. Faulty cybersecurity standards open up possible hacking and cyberattacks. IoT security liabilities, specifically regarding wearable IoT devices, interfere with Floridi's concept of physical privacy, which is the "freedom from sensory interference and intrusion." [13] Consumers would not want data exposed regarding their IoT heart monitor, connected household security system, or smart car. Wearable device information can transmit data on one's exact location, and where they have previously walked. Other actors would have the ability to invade personal space, and gain insight and information on personal bodily functions and interactions. Even non-crucial information, such as data from a connected household lighting system, can indicate when a house is empty or not. Poor IoT security makes breaches of privacy possible that could create major security concerns. [14]
Agency
In 2019, nearly two-thirds of American households will contain some IoT appliance. [15]Consumers have a more comfortable and luxurious experience with appliances when they delegate the activation and maintenance to third parties. However, they lose some agency, independence, and empowerment to make personal decisions. IoT devices delegate agency from individuals, and potentially violate Floridi's concept of decisional privacy, which is "the freedom from procedural interference and intrusion." [16] When appliance functionally and maintenance are delegated to others, users are excluded from those decision making processes, lose insight on how to use devices themselves, and lose the significance and meaning of the information they are gaining. Users may begin to delegate more crucial tasks to third parties, who may not have the user's best interest at heart. This also creates an issue of informational ownership. As more functions are delegated to third parties IoT data managers, more data is transferred to third party hands. Although users are generating the data, the companies which manage IoT systems are performing statistical analysis and data management functions. Does the analyzed data truly belong to the user, or the organization which receives the raw data and performs its own analysis? This creates a grey area of intellectual property ownership, since data is being constantly transferred between IoT provider and data managers, and the data is being critically changed and edited at every step of the process. Increasingly delegating functions to others depreciates the abilities and capacities of the user, transfers ownership to third party IoT providers, and could render users completely reliant and dependent on unconscious IoT systems.
Identity
Like many other forms of ICTs, IoTs collect large amounts of data, based on user interactions, and aggregate it to create an accurate representation of the user and its behaviors and tendencies. These digital representations of user-IoT interactions create a certain narrative about the user, and an online digital identity based on IoT generated data. David Shoemaker claims that these digital portrayals violate a user's sense of self-identity, because they capture narrow zones and aspects of user behaviors, appropriate identity management rights, and create a subjective identity of the user based on non-instrumental information. Bits and dollops of information about a user do not necessarily implicate anything about their identity, but can instead, create a certain pattern that associate unrelated pieces of information to create an inaccurate representation of the user's life. [17] If IoT providers present inaccurate and incomplete digital identities to crucial service providers, such as insurers and creditors, they may derive adverse impressive conclusions that could harm consumers. The right and value of identity management is not inherently part of IoT design, since the nature of IoTs only allow them to capture bits of pieces of information in limited contexts; which may reveal its values-sensitive design. IoT can cause invasions of identity privacy, and create inaccurate representations, which remove an individual's ability and autonomy to create and publicize their own self-identity.
References
- ↑ Castro, Ethan. Hidden History: John Romkey and the Internet toaster, Tech News, Fall 2017, Issue 11.
- ↑ CONNECTING THE PAST TO THE FUTURE – THE ORIGINS AND EVOLUTION OF IOT, Open Connectivity Foundation, May 10, 2018.
- ↑ Engineering and Technology History Wiki: Kevin Ashton, ETHW
- ↑ [Kanellos, Michael. "Hold The Laughter: Why The Smart Fridge Is A Great Idea," Forbes, 1/13/16.]
- ↑ McClelland, Calum. IoT Explained — How Does an IoT System Actually Work?, Medium, November 20, 2017
- ↑ McClelland, Calum. Types of Network Connectivity for the Internet of Things (IoT) – A Simple Explanation, IoTForAll, January 6, 2019.
- ↑ ''Building an Open Data Processing Pipeline for IoT, Cloudera, September 11, 2018.
- ↑ Lazarevich, Katherine. 5 Keys to Designing User Experience for IoT Products, IotForAll, March 30, 2018.
- ↑ Lueth, Knud Lasse. The 10 most popular Internet of Things applications right now, IoT Analytics, February 2, 2015.
- ↑ Kashyap, Swati. 10 Real World Applications of Internet of Things (IoT), Analytics Vidyha, August 26, 2016.
- ↑ Frye, Christopher. “Evolution of IoT in Shipping: Current and Future Trends.” The Kolabtree Blog, The Kolabtree Blog, 28 Aug. 2018, blog.kolabtree.com/evolution-of-iot-and-shipping-current-and-future-trends/
- ↑ Floridi, Luciano. "Protection of Information and the Right to Privacy - A New Equilibrium?" Springer International Publishing, 6/5/14.
- ↑ Floridi, Luciano. "Protection of Information and the Right to Privacy - A New Equilibrium?" Springer International Publishing, 6/5/14.
- ↑ Richardson, Alex. Ethical Pitfalls and the Internet of Things, Aquicore.
- ↑ Walter, Jesse. Is Law Catching Up Fast Enough with IoT Integration in the Home? Law Technology Today, September 21, 2018.
- ↑ Floridi, Luciano. "Protection of Information and the Right to Privacy - A New Equilibrium?" Springer International Publishing, 6/5/14.
- ↑ Shoemaker, David W. "Self-exposure and exposure of the self: informational privacy and the presentation of identity," Spring Science and Business Media, 2009.


