Hacking the 2016 US Presidential Election
In early 2016, the Russian Federation began a coordinated hacking effort against the Democratic National Committee and Presidential candidate Hillary Rodham Clinton. [1] This was a part of a larger effort to influence the 2016 Presidential election. Hackers used a diverse range of methods to gain access to confidential emails. In addition, they targeted election systems in numerous states. Close to 150,000 emails were stolen by Russian government-backed hacking groups and were posted online [2]. It is not believed that the efforts to tamper with voting systems were effective, but intelligence officials still have doubts.
Contents
Hacking The DNC and Hillary Clinton
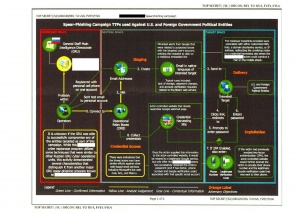
The first hacks began in March 2016 [3]. Clinton staffers and volunteers began to be targeted through email phishing. Over the course of five days, dozens of target emails were sent. Phishing is when hackers send out malicious emails that trick users into giving sensitive information. One common method is asking users to reset their password for their email through a phony form that sends credentials to a hacker. Through this process, the hackers were able to gain access to the email of John Podesta, who was Clinton’s campaign chairman at the time. Using credentials gained from phishing, the hackers were also able to log in as System Administrators on the Democratic Congressional Campaign Committee (DCCC) five days later and then, using information from there, the Democratic National Committee (DNC) network. Once on the networks, the hackers used Minikatz to collect login credentials, X-Agent to take screenshots and log keystrokes, and X-Tunnel to send information back to hacker-controlled servers. The data first went to middle servers hosted in Arizona. In the Mueller Report, it was stated that these servers worked as a buffer to avoid detection. [4] All the tools used were open sourced and readily available to the public. The stolen information was distributed first in June 2016 through a website that was created, DCLeaks.com. These leaks were claimed by a hacker going by the moniker “Guccifer 2.0”, who professed to be a lone Romanian. Eventually, Guccifer 2.0 got in contact with WikiLeaks. WikiLeaks asked for new material that could be released at the Democratic National Convention in order to sow discord. Thus, in late July, WikiLeaks started releasing documents, which included 20,000 of the Podesta emails. After 2016, it was found that two divisions directly connected to the Russian Military Intelligence Service (GRU) had been directly connected to the email hacks. The group known as Fancy Bear comprised multiple units with distinct tasks to interfere with the U.S. elections. In the Mueller report, Unit 26165 was blamed for overseeing the hacking of the DNC, while Unit 74455 oversaw the dissemination and publication of documents stolen in the hack. It was also found that Brittany Kaiser at Cambridge Analytica met Julian Assange of Wiki Leaks in February 2017. [5] Reporters also discovered that, in 2016, Cambridge Analytica reached out to Assange asking to index and distribute the emails that had been stolen. In October 2018, multiple GRU officers were charged by the U.S. Department of Justice with hacking and disinformation. [6]
Hacking of Voting Systems
In July 2019, the Senate Intelligence Committee concluded that, in 2016, election systems in all 50 states were targeted by hackers tied to the Russians. [7] The report concluded that there was no evidence of votes being changed. There was a strong belief, however, that Russian intelligence may have found a way into voting systems and had possibly decided not to act. It was revealed that close to ten phishing emails were sent to local election officials days before the 2016 election, and at least one U.S. voting software company was targeted. Local election officials were sent emails pretending to be from voting software companies to open Microsoft Word documents with malware. Through this, hackers possibly gained access to the voting systems. A leaked NSA report indicated that Russian hackers may have penetrated voting systems further than previously understood. [8] It is unknown, however, the extent and effect of these hacking efforts.
Ethics
The main ethical concerns in the 2016 election related to privacy and election integrity. Emails were illegally stolen from a private server that revealed campaign strategy and the Clinton campaign’s donor relationships. Additionally, efforts to undermine voting in the election have revealed flaws in current voting software and the private companies that make this software --flaws that experts believe could be exploited in the future.
Privacy
The release of the Podesta emails revealed Hillary Clinton’s distinct relationship with Clinton Foundation donors, with Wall Street, and with her staffers.[9] One email that was especially damning came from research director Tony Carrk. It was an email of a Clinton speech titled with the header Clinton Admits She Is Out of Touch. [10] In the speech to Wall Street donors, Clinton talked about how she had lost her connection to Middle Class America. The Republican National Committee used these emails to undermine Clinton’s campaign. RNC Chairman Reince Preibus stated,“The truth that has been exposed here is that the persona Hillary Clinton has adopted for her campaign is a complete and utter fraud.”
Integrity and Authenticity
In 2019, University of Michigan professor Alex Halderman made an important recommendation for 370 million dollars in federal funding to replace outdated voting machines. [11] This was after Halderman in 2018 showed how he was able to hack voting machines used in 10 states, to change the outcome of a fake University of Michigan vs. Ohio State University Election. [12] Much of the concern involves how this hacking undermines the democratic process. In the aftermath of the 2016 election, many cybersecurity companies have offered their services for free to help shore up election security. [13]
References
- ↑ “Russian Interference in the 2016 United States Elections.” Wikipedia, Wikimedia Foundation, 3 Mar. 2020, en.wikipedia.org/wiki/Russian_interference_in_the_2016_United_States_elections.
- ↑ Balsamo, Michael. “Thousands of Emails Stolen from Republican Committee's Aides.” AP NEWS, Associated Press, 5 Dec. 2018, apnews.com/cdcda481c0574b4da214703000e350b8.
- ↑ Chang, Alvin. “How Russian Hackers Stole Information from Democrats, in 3 Simple Diagrams.” Vox, Vox, 16 July 2018, www.vox.com/policy-and-politics/2018/7/16/17575940/russian-election-hack-democrats-trump-putin-diagram.
- ↑ Whittaker, Zack. “Mueller Report Sheds New Light on How the Russians Hacked the DNC and the Clinton Campaign.” TechCrunch, TechCrunch, 18 Apr. 2019, techcrunch.com/2019/04/18/mueller-clinton-arizona-hack/.
- ↑ Cadwalladr, Carole, and Stephanie Kirchgaessner. “Cambridge Analytica Director 'Met Assange to Discuss U.S. Election'.” The Guardian, Guardian News and Media, 7 June 2018, www.theguardian.com/uk-news/2018/jun/06/cambridge-analytica-brittany-kaiser-julian-assange-wikileaks.
- ↑ “U.S. Charges Russian GRU Officers with International Hacking and Related Influence and Disinformation Operations.” The United States Department of Justice, 4 Oct. 2018, www.justice.gov/opa/pr/us-charges-russian-gru-officers-international-hacking-and-related-influence-and.
- ↑ Sanger, David E., and Catie Edmondson. “Russia Targeted Election Systems in All 50 States, Report Finds.” The New York Times, 25 July 2019, www.nytimes.com/2019/07/25/us/politics/russian-hacking-elections.html.
- ↑ Esposito, Richard, et al. “Top-Secret NSA Report Details Russian Hacking Effort Days Before 2016 Election.” The Intercept, 5 June 2017, theintercept.com/2017/06/05/top-secret-nsa-report-details-russian-hacking-effort-days-before-2016-election/.
- ↑ Stein, Jeff. “What 20,000 Pages of Hacked WikiLeaks Emails Teach Us about Hillary Clinton.” Vox, 20 Oct. 2016, www.vox.com/policy-and-politics/2016/10/20/13308108/wikileaks-podesta-hillary-clinton.
- ↑ Cheney, Kyle, et al. “The Most Revealing Clinton Campaign Emails in WikiLeaks Release.” POLITICO, 8 Oct. 2016, www.politico.com/story/2016/10/john-podesta-wikileaks-hacked-emails-229304.
- ↑ Crang, Steve. “Election Security: Halderman Recommends Actions to Ensure Integrity of U.S. Systems.” Michigan Engineering, 27 Feb. 2019, news.engin.umich.edu/2019/02/election-security-halderman-recommends-actions-to-ensure-integrity-of-us-systems/.
- ↑ Halderman, J. Alex. “I Hacked an Election. So Can the Russians.” The New York Times, The New York Times, 5 Apr. 2018, www.nytimes.com/2018/04/05/opinion/election-voting-machine-hacking-russians.html.
- ↑ Yakowicz, Will. “The White Hats in the War Against Election Meddling.” Inc.com, Inc., 23 July 2018, www.inc.com/will-yakowicz/cyber-companies-offer-state-election-websites-free-security-software.html.