Difference between revisions of "Cookies"
| Line 1: | Line 1: | ||
{{nav-Bar|topics#I}} | {{nav-Bar|topics#I}} | ||
| − | '''Cookies''' are text files that are sent from a website and uploaded to a user's browser when they enter the website<ref>Wikipedia: HTTP Cookie http://en.wikipedia.org/wiki/HTTP_cookie</ref>. They allow the process of storing information on websites that require users to | + | '''Cookies''' are text files that are sent from a website and uploaded to a user's browser when they enter the website<ref>Wikipedia: HTTP Cookie http://en.wikipedia.org/wiki/HTTP_cookie</ref>. They allow the process of storing information on websites that require users to log in to be easier and more efficient.<ref name="wac">What Are Cookies Website: Computer Cookies Explained http://www.whatarecookies.com/</ref> and navigating a website.<ref name="HSW">How Stuff Works Website: "How Internet Cookies Work" http://computer.howstuffworks.com/cookie.htm</ref> Cookies identify a user through a name-value pair <ref name="HSW"/>. Cookies are assigned times when they will be discontinued or expired. A user can be notified when a website sets a cookie or they have the option to choose settings that prevent cookies from being implemented. The tracking of cookies poses ethical concerns such as issues with user privacy and the ability for parties using cookies to see what sites the user has previously visited.<ref name="wac"/> |
[[File:Cookie.png|thumb|450px| Example of a cookie]] | [[File:Cookie.png|thumb|450px| Example of a cookie]] | ||
| Line 15: | Line 15: | ||
==Uses== | ==Uses== | ||
| − | Cookies allow websites to easily maintain a user’s preferences whenever a user logs in or visits that site. Cookies | + | Cookies allow websites to easily maintain a user’s preferences whenever a user logs in or visits that site. Cookies ensure that preference is maintained for the duration of future visits to that site. For example, [[Facebook]] uses cookies to customize its advertisements, products, and features to a particular user, maintaining the user's privacy and other various settings. After the user logs out, Facebook would alert the user if someone tries to get through the same account or violates Facebook's policies <ref>Facebook Website: Cookies, Pixels, and Similar Technologies: "How Cookies Work" http://www.facebook.com/help/cookies/</ref>. Cookies can also be used for browser-based gaming so that games might store a player’s state and allow returns for more play. E-commerce sites use cookies as a "shopping cart". This allows a server to hold on to the items that the user picked out to purchase while continuing to shop for other items. Cookies are a means of distributing some of the burden of information management to the client, the user’s browser, rather than the e-commerce business using costly server-side operations to save all data. If it were not for cookies, servers would have a difficult time retrieving the user's information.<ref name="wac"/> |
==Types== | ==Types== | ||
===Session Cookies=== | ===Session Cookies=== | ||
| − | Session cookies, also called transient cookies, are temporarily stored on a person's computer while the user is browsing on the site. This allows the user to move from page to page on the site. The session cookie is deleted upon closing the browser | + | Session cookies, also called transient cookies, are temporarily stored on a person's computer while the user is browsing on the site. This allows the user to move from page to page on the site. The session cookie is deleted upon closing the browser and is not saved to a user's hard drive. |
===Persistent Cookies=== | ===Persistent Cookies=== | ||
| Line 44: | Line 44: | ||
====Session Hijacking==== | ====Session Hijacking==== | ||
| + | Session Hijacking is used to gain access to information or services that are not directly provided. Session attackers duplicate data from a user to mislead to communication receiver to be believed that the attacker is the original user. The data obtained by the attacker is then replicated and authenticated for future use. <ref> “Cookie Hijacking: Learning through Replay Attack Examples !” Cookie Hijacking: Learning through Replay Attack Examples ! | TCS Cyber Security Community, securitycommunity.tcs.com/infosecsoapbox/articles/2017/01/05/cookie-hijacking-learning-through-replay-attack-examples.</ref>Cookies, and sessions are not encrypted and make it easier for online predators to access unauthorized information and services. There are many different ways to hijack a session. Once the predator obtains the cookie information they now have the ability to monitor and trace a user network traffic that could potentially contain sensitive information. <ref> Sivakorn, Suphannee, et al. “The Cracked Cookie Jar: HTTP Cookie Hijacking and the Exposure of Private Information.” 2016 IEEE Symposium on Security and Privacy (SP), 2016, doi:10.1109/sp.2016.49. </ref> | ||
===Exploitation=== | ===Exploitation=== | ||
| − | Users can opt to disable cookies from websites but some functionalities will be disabled. Users are often times not made aware of that a website is collecting cookies. Cookie policies are hidden in the privacy policy of a website. <ref> Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues." </ref> Cookies collect behavioral data from each site a user visits through tracking. These behaviors and trends curate specific ads as a user browses from site to site. This data can be sold to increase a websites new visitors and sales. This subtle explanation is not made aware by a user. There is no information transparency between websites and its users. Users are unaware of how their data is being collected, stored, and used when visiting new and old websites. Per the Privacy and Electronic Communication Regulations, users have the right to know when information is being stored and how it is being used. <ref> Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues."</ref> | + | Users can opt to disable cookies from websites but some functionalities will be disabled. Users are often times not made aware of that a website is collecting cookies. Cookie policies are hidden in the privacy policy of a website. <ref> Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues." </ref> Cookies collect behavioral data from each site a user visits through tracking. These behaviors and trends curate specific ads as a user browses from site to site. This data can be sold to increase a websites new visitors and sales. This subtle explanation is not made aware by a user. There is no information transparency between websites and its users. Users are unaware of how their data is being collected, stored, and used when visiting new and old websites. Per the Privacy and Electronic Communication Regulations, users have the right to know when information is being stored and how it is being used. It violates a users rights ethically.<ref> Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues."</ref> |
| Line 61: | Line 62: | ||
==== Vulnerabilities ==== | ==== Vulnerabilities ==== | ||
| − | Browser cookies give attackers the opportunity to steal private information about one's personal life, sensitive finances, and even identity. In September 2015, The US Computer Emergency Response Team ([[Cert]]) found a loophole in major browsers like Internet Explorer, Mozilla Firefox, and Apple Safari that allows remote attackers to essentially bypass industry-secure HTTPS protocol to reveal confidential data.<ref name="Cert">Exploiting Browser Cookies to Bypass HTTPS and Steal Private Information, The Hacker News, Swati Khandelwar, September 25th, 2015 </ref>. A website that uses cookies can be exploited through common vulnerabilities if the website is not developed with common attacks in mind. An attacker can use common attacks such as Cross Site Scripting and Cookie Poisoning<ref>Surajit Sarma, A study on Common Web Based Hacking and Preventive Measure, July 2017 [[http://ijsrcseit.com/paper/CSEIT172449.pdf ijsrcseit.com]]</ref>. To reduce threat, the content of cookies can be encrypted. Additionally, evaluating the vulnerabilities through penetration testing can reduce the risk of an attack. | + | Browser cookies give attackers the opportunity to steal private information about one's personal life, sensitive finances, and even identity. In September 2015, The US Computer Emergency Response Team ([[Cert]]) found a loophole in major browsers like Internet Explorer, Mozilla Firefox, and Apple Safari that allows remote attackers to essentially bypass industry-secure HTTPS protocol to reveal confidential data.<ref name="Cert">Exploiting Browser Cookies to Bypass HTTPS and Steal Private Information, The Hacker News, Swati Khandelwar, September 25th, 2015 </ref>. A website that uses cookies can be exploited through common vulnerabilities if the website is not developed with common attacks in mind. An attacker can use common attacks such as Cross Site Scripting and Cookie Poisoning<ref>Surajit Sarma, A study on Common Web Based Hacking and Preventive Measure, July 2017 [[http://ijsrcseit.com/paper/CSEIT172449.pdf ijsrcseit.com]]</ref>. To reduce the threat, the content of cookies can be encrypted. Additionally, evaluating the vulnerabilities through penetration testing can reduce the risk of an attack. |
===Laws Regarding Online Privacy=== | ===Laws Regarding Online Privacy=== | ||
Revision as of 09:41, 24 April 2018
Cookies are text files that are sent from a website and uploaded to a user's browser when they enter the website[1]. They allow the process of storing information on websites that require users to log in to be easier and more efficient.[2] and navigating a website.[3] Cookies identify a user through a name-value pair [3]. Cookies are assigned times when they will be discontinued or expired. A user can be notified when a website sets a cookie or they have the option to choose settings that prevent cookies from being implemented. The tracking of cookies poses ethical concerns such as issues with user privacy and the ability for parties using cookies to see what sites the user has previously visited.[2]
Setup of a Cookie
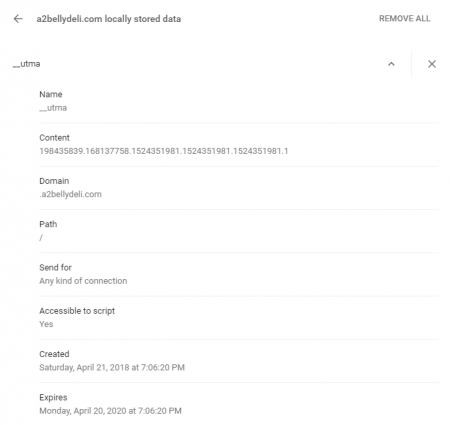
Cookies are set using a name-value pair. For example, a sample of a cookie used by goto.com:
UserID A9A3BECE0563982D
In this case, "UserID" is the "name" part of the name-value pair and "A9A3BECE0563982D " is the "value" [3]. A cookie also contains a domain, the website that issued the cookie. The domain allows the browser to send the right cookies as a user browses a site, and prevent websites from viewing cookies of another domain. A path value is also stored, to specify which pages within a website the cookie should be sent.
Uses
Cookies allow websites to easily maintain a user’s preferences whenever a user logs in or visits that site. Cookies ensure that preference is maintained for the duration of future visits to that site. For example, Facebook uses cookies to customize its advertisements, products, and features to a particular user, maintaining the user's privacy and other various settings. After the user logs out, Facebook would alert the user if someone tries to get through the same account or violates Facebook's policies [4]. Cookies can also be used for browser-based gaming so that games might store a player’s state and allow returns for more play. E-commerce sites use cookies as a "shopping cart". This allows a server to hold on to the items that the user picked out to purchase while continuing to shop for other items. Cookies are a means of distributing some of the burden of information management to the client, the user’s browser, rather than the e-commerce business using costly server-side operations to save all data. If it were not for cookies, servers would have a difficult time retrieving the user's information.[2]
Types
Session Cookies
Session cookies, also called transient cookies, are temporarily stored on a person's computer while the user is browsing on the site. This allows the user to move from page to page on the site. The session cookie is deleted upon closing the browser and is not saved to a user's hard drive.
Persistent Cookies
Persistent cookies--also called permanent cookies or stored cookies--are not deleted when you leave a website. They allow the site to identify individual users. These cookies allow a site to keep track of and maintain a user's settings or preferences when the user logs out of a website and later logs back in.[5] The permanent cookie is given a specified time to live (TTL) before it expires, specified by the website issuing the cookie. The cookie remains on a user's browser until it runs out, allowing the user to authenticate themselves with the cookie instead of using their username and password.
First Party Cookies
First party cookies have the same domain that a user is currently browsing. For example, if a user is on Amazon.com, the cookie will have the same domain name: Amazon.com.
Third Party Cookies
Third party cookies have a different domain than what is in the user's address bar. For example, a user may be on Amazon.com, but the cookie could have a domain name other than Amazon.com. Third Party Cookies are the subject of debate when it comes to cookies and privacy. Browsers such as Firefox, Internet Explorer and Google Chrome allow the use of third-party cookies by default but give users the option to turn third-party cookies off.[6]
Zombie Cookies
These are cookies that automatically recreate themselves after a user initially destroys them.[3] They are stored outside of allocated cookie storage locations and this allows them to persist after a user deletes their cookies. They can be stored either online or on your computer, and because they do not behave like traditional cookies, they can be attached to your browser even if you have chosen not to allow cookies.[7] This type of cookie was first discovered at UC Berkley when researchers found they could not delete cookies as they kept returning.[8]
Ethical Concerns
Cookies are not viruses, but there have been concerns about privacy on the internet, especially with Third Party Cookies. Cookies of this sort can have the capability to track what other sites a user browses and allow other sites access to a user's information without the user going on to the site and/or give a user's information to another site without the knowledge and consent of the user. Zombie cookies can track users across different browsers used by the same computer because the cookies are stored in places that are common between browsers.[7]
Privacy
There is a concern that data about a user can be intercepted as the connection between the browser and the user is not encrypted. This would give them access to sensitive cookie data including anything a user has entered them-self into a website, for example filling out a form online.[9]
In regards to privacy, a major ethical concern regarding Third Party Cookies is the ability for them to track a user's frequently visited websites as well as store data and patterns about that user's activity online on various web pages. These functions are often used by advertisers to watch what other sites and products the user is viewing. It is often advised to turn off cookies or only accept cookies from trusted or frequently visited sites. Within these sites, cookies help a user who visits the webpage often by remembering their specific information for the frequently visited website. Zombie cookies are also considered a privacy breach as they can be stored right on your computer and are not removed when a user explicitly expects to do so.[8]
Session Hijacking
Session Hijacking is used to gain access to information or services that are not directly provided. Session attackers duplicate data from a user to mislead to communication receiver to be believed that the attacker is the original user. The data obtained by the attacker is then replicated and authenticated for future use. [10]Cookies, and sessions are not encrypted and make it easier for online predators to access unauthorized information and services. There are many different ways to hijack a session. Once the predator obtains the cookie information they now have the ability to monitor and trace a user network traffic that could potentially contain sensitive information. [11]
Exploitation
Users can opt to disable cookies from websites but some functionalities will be disabled. Users are often times not made aware of that a website is collecting cookies. Cookie policies are hidden in the privacy policy of a website. [12] Cookies collect behavioral data from each site a user visits through tracking. These behaviors and trends curate specific ads as a user browses from site to site. This data can be sold to increase a websites new visitors and sales. This subtle explanation is not made aware by a user. There is no information transparency between websites and its users. Users are unaware of how their data is being collected, stored, and used when visiting new and old websites. Per the Privacy and Electronic Communication Regulations, users have the right to know when information is being stored and how it is being used. It violates a users rights ethically.[13]
Cookie tracking
Cookies that are used to authenticate a user to a website (such as Facebook) can be used to track user behavior on third-party websites. A third party website may contain images that are pulled from Facebook, such as the like button. When the image is downloaded from the browser, Facebook identifies the user's cookie and associates that third party website visit to the user.[14] Facebook is able to identify the user without them clicking or interacting with the page. Simply loading the page allows for data collection. Browser extensions such as Ghostery[15] allow a user to block tracking technologies.
Airline prices
Consumers have long accused airline companies of using internet cookies to unfairly price tickets. Robert Weiss, an attorney who published a how airlines exploit cookies to price gouge tickets, found that travel sites used cookies to actually determine their pricing of tickets. Bill McGee, a journalist with USA Today and researcher for Consumers Union, conducted an experiment to demonstrate this phenomenon. McGee searched one major travel site for a ticket from New York City to Sydney, Australia with two different browsers (one was clear of all cookies and one had a history of purchasing flights).[16] McGee ultimately found that the browser with no history offered fares ranging from $1,770 to $1,950 while the browser that had past history had fares listing at $2,116.[16] This experiment proved how the use of cookies and other tracking information raises serious ethical issues about privacy and the use of stored information.[16]
Consumers have since been adapting to practices like these from major online commerce sites. A common solution is to simply delete your cookie history. Another solution is to use Google Chrome Incognito. Chrome Incognito ensures that your browsing history, cookie storage, and other sensitive information will not be kept.
Such behavior arises the debate whether or not agencies and companies have the moral right to use user-specific data. Many situations are viewed on a case-by-case basis. For instance, the NSA has in the past used Google cookies to pinpoint targets to "hack" and surveil.[17] The NSA has found particular use in a Google-specific tracking technology called the "PREF" cookie, which contains numeric code that allows the NSA to specifically track an individual's browsing data.[17]
Vulnerabilities
Browser cookies give attackers the opportunity to steal private information about one's personal life, sensitive finances, and even identity. In September 2015, The US Computer Emergency Response Team (Cert) found a loophole in major browsers like Internet Explorer, Mozilla Firefox, and Apple Safari that allows remote attackers to essentially bypass industry-secure HTTPS protocol to reveal confidential data.[18]. A website that uses cookies can be exploited through common vulnerabilities if the website is not developed with common attacks in mind. An attacker can use common attacks such as Cross Site Scripting and Cookie Poisoning[19]. To reduce the threat, the content of cookies can be encrypted. Additionally, evaluating the vulnerabilities through penetration testing can reduce the risk of an attack.
Laws Regarding Online Privacy
Europe
In 2002, the European Union made rules regarding the use of cookies. In particular, "the user is provided information about how this data is used" and the opportunity to deny a website from storing their information. In 2009, the European Union amended this law to include giving "a user advanced written notice that a cookie is being placed on his or her device and describes what the cookie is doing" and "obtains the user’s consent to the placement of the cookie before placing the cookie on the user’s device". On May 26, 2011, the European Union set guidelines for websites about using cookies. In order for a site to keep cookies on a user's hard drive, the website must get the consent of the user and gain acceptance.[3][5][6][20]
United States
The site of the National Security Agency was caught putting cookies on user's computers that were capable of tracking a user's web activities.[21] There currently exist no laws in the U.S. that directly target the use of cookies.
See Also
References
- ↑ Wikipedia: HTTP Cookie http://en.wikipedia.org/wiki/HTTP_cookie
- ↑ 2.0 2.1 2.2 What Are Cookies Website: Computer Cookies Explained http://www.whatarecookies.com/
- ↑ 3.0 3.1 3.2 3.3 3.4 How Stuff Works Website: "How Internet Cookies Work" http://computer.howstuffworks.com/cookie.htm
- ↑ Facebook Website: Cookies, Pixels, and Similar Technologies: "How Cookies Work" http://www.facebook.com/help/cookies/
- ↑ 5.0 5.1 About Cookies Website: Frequently Asked Questions http://www.aboutcookies.org/default.aspx?page=5
- ↑ 6.0 6.1 Open Tracker Website: "Third-Party Cookies vs. First-Party Cookies" http://www.opentracker.net/article/third-party-cookies-vs-first-party-cookies
- ↑ 7.0 7.1 Wikipedia: Zombie Cookies http://en.wikipedia.org/wiki/Zombie_cookie
- ↑ 8.0 8.1 Helium Website: "Zombie Cookies: What zombie cookies are and how to delete them" http://www.helium.com/items/1905717-zombie-cookies-what-zombie-cookies-are-and-how-to-delete-them
- ↑ Cookie Central Website: Frequently Asked Questions http://www.cookiecentral.com/n_cookie_faq.htm#sens_info
- ↑ “Cookie Hijacking: Learning through Replay Attack Examples !” Cookie Hijacking: Learning through Replay Attack Examples ! | TCS Cyber Security Community, securitycommunity.tcs.com/infosecsoapbox/articles/2017/01/05/cookie-hijacking-learning-through-replay-attack-examples.
- ↑ Sivakorn, Suphannee, et al. “The Cracked Cookie Jar: HTTP Cookie Hijacking and the Exposure of Private Information.” 2016 IEEE Symposium on Security and Privacy (SP), 2016, doi:10.1109/sp.2016.49.
- ↑ Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues."
- ↑ Jegatheesan, Sowmyan. "Cookies Invading Our Privacy for Marketing Advertising and Security Issues."
- ↑ Charlotte Rottgen, Like or Dislike - Web Tracking, October 18 2017 [link.springer.com]
- ↑ Ghostery home page, faster, safer, and smarter browsing [ghostery.com]
- ↑ 16.0 16.1 16.2 Airfare Expert: Do cookies really raise airfares?, http://www.usatoday.com/story/travel/columnist/seaney/2013/04/30/airfare-expert-do-cookies-really-raise-airfares/2121981/, Bill McGee, April 30th, 2013
- ↑ 17.0 17.1 NSA uses Google cookies to pinpoint targets for hacking, The Washington Post, Ashkan Soltani, December 10, 2013
- ↑ Exploiting Browser Cookies to Bypass HTTPS and Steal Private Information, The Hacker News, Swati Khandelwar, September 25th, 2015
- ↑ Surajit Sarma, A study on Common Web Based Hacking and Preventive Measure, July 2017 [ijsrcseit.com]
- ↑ Open Tracker Website http://www.opentracker.net/
- ↑ Dummies Website: "Defining and Dealing with Web Cookies http://www.dummies.com/how-to/content/defining-and-dealing-with-web-cookies.html