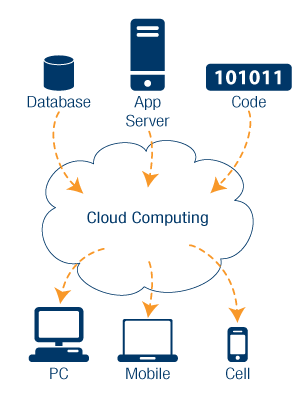
Cloud Computing
Cloud computing is the practice of offering shared computational resources to end-users by way of remote servers. Its basic premise includes offering storage, management, and processing of data to an end-user from a centralized location, without the need of powerful individual terminals to carry out computational tasks.[1] Transfer of the processed data files, in the form of documents, emails, or applications can then occur over a network connection.
Access and delivery of data is done through applications such as web browsers[2], which require far lower computational resources than individual terminals. The dispersal of computational resources from a central location is intended to be more cost-effective than individual-terminal forms of computing.[3]
Contents
Overview
Cloud computing delivers computational capability from a centralized source to an end-user via an internet connection. Once the connection from host to end-user is made through the connection, multiple levels of service can be achieved based on the user’s needs and the system’s specifications.
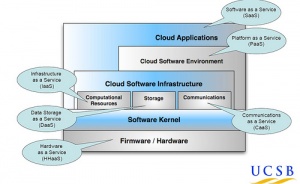
Layers of Cloud Computing
Shared cloud computing resources range from simple applications, in which users only have access to the functions provided by the application, all the way to shared operating systems which are run remotely on the server. The levels of software abstraction available to the user through the cloud are relative to the purpose of the system.
Characteristics of Cloud Computing
The National Institute of Standards and Technology, NIST, identifies 5 major characteristics that they believe are essential.[4]
1. Customer-initiated service that provides server time and network storage
2. Network access from different electronic devices (laptops, mobile phones)
3. Computer resources to be used for all different types of resources according to costumer demand
4. Capabilities for very easy revisions and access
5. Measured services that can be controlled and monitored by both the provider and customer so information will be stored accurately
“Software as a Service”
Through the process of centralized computation, cloud computing embodies a new model for the delivery of computational resources. Cloud computing often employs “Software as a Service” (SaaS)[5], in which software is “delivered” to end-users by way of network connections as opposed to being carried out locally. Contrasted with software being seen as a static part of the computational process, this shift in paradigm allows software’s computational nature to be seen as a resource.
"Platform as a Service"
Another delivery model that has been developed is "Platform as a Service" in which the customer can deploy services that use any type of programming languages and tools that the provider uses. Even though the customers gives access to the provider, they can maintain or gain back control of applications that have been created.
"Infrastructure as a Service"
This delivery model makes the customer more of the primary user and controller in the cloud. They can relinquish control to the management of the infrastructure but can gain control over more than just applications like operation systems, storage, and some network components.
Ethical Implications
There are many ethical concerns with the development of cloud computing. One of the largest concerns deals with the illegal exchange and sharing of information within the cloud interface. This issue is hotly debated and difficult to resolve due to various copyright and licensing regulations. Cloud computing presents users with ethical dilemmas about whether or not it is legal to gain access to certain materials through a cloud sharing interface. The monitoring of these central networks keep control of who has access and to what specific pieces of information can be obtained.
Most of the ethical implications can be attributed to the types of information that is stored on specific servers. Especially pieces of digital media, which are fully entitled to a single user, however, in the cloud many users can have access to a single media file, and the ownership is lost. The continued want for artists and publishers to maintain control over their works needs to be addressed for future implications of cloud computing.
Benefits of Cloud Computing
Efficiency & Cost Management
Cloud computing allows utilization of IT resources to be maximized. With all computation being done in a single locale, the cloud system can be engineered to fit the demand for resources. Resources over and above demand can be powered off, or utilized in other ways to make the cloud computing system more efficient.[6]
Ease of Maintenance
- With all software and hardware being stored in a single location, upgrading and updating of infrastructure must be done only one time at the central location, as opposed to multiple times at each individual terminal. Centralized control for maintenance allows for more uniformed upgrading as well.[7]
Redundancy
- The more cost-effective nature of centralized cloud resources allows system safe-falls to be put in place more easily. For instance, if one server fails, a secondary server can be used to take its place. In comparison, a set of dispersed individual computers that fail simultaneously are much more difficult to repair.[8]
System Access
- When companies hire new employees they must install various software packages onto their computers. This usually is a long and tiresome process because many of these packages require certain product licensing numbers. However with cloud computing they can establish an internal network where they can simply access these required programs with ease because they are stored online in the cloud network. This is quicker and easier than manually downloading them onto each specific computer.
Convenience
- Apple recently announced that as of October 12, 2011 that their iCloud will be available to users thus making it easier to manage data across a variety of their products such as the iPod, iPhone, and iPad. iCloud allows users to store their content, music, photos, documents, and files in one virtual location that can be accessed by the various apple devices mentioned previously. In addition to Apple's iCloud, Dropbox also offers a similar storage service for your music, photos, and important documents. These services have revolutionized and upgraded the utility and attractiveness of cloud computing for the average consumer. By offering a safe place to back-up files and storage, it allows consumers and companies to increase storage and capability without investing capital into new servers, infrastructure, information technology services, and licensing. Cloud computing eliminates the costly overhead for subscription servers and pay-per-use services, extending information technology's reach across the internet. Cloud services provide these ample, but innovative conveniences for users.
Drawbacks of Cloud Computing
Data Sharing & Copyright Infringement
Access to copyrighted material through the cloud raises complex legal concerns. The easy dispersion of digital material not owned by users of the cloud, but disseminated through its infrastructure can constitute copyright infringement for the user and bring legal ramifications for the cloud provider. Concerns also exist about the ownership of data stored on cloud servers. For instance, is information that is saved on the cloud the property of the individual that generated it, or property of the individual upon whose server the information is stored. [9]
Privacy Concerns
With all internet browsing flowing through a centralized location, the format of cloud computing can potentially allow system administrators easy unauthorized access to an individual's computing actions. Ethical concerns also exist because a level of trust is required when an individual's personal information is saved on physical hardware which they cannot access or protect.[10]
Security Concerns
Information stored in a single location can potentially be subject to easier breeches in security. Having all data exist centrally allows more users to access said information, while creating a one-stop-shop for hackers to obtain classified or potentially damaging data.
Examples of Cloud Computing Services
Amazon Web Services (AWS)
Amazon provides various cloud services, including the S3 (Simple Storage Service) that provides data storage and EC2 (Elastic Compute Cloud)that is a platform to run programs and computations.
Amazon has become the industry leader in the emerging market of cloud computing. Many emerging companies, particularly those with websites that have heavy traffic or deal with fast increases in production, have turned to AWS to handle their data storage. AWS has become the de facto cloud computing platform for many because of their reputation of dependability and security, as well as an easy to use interface.
The massive growth of AMS and Amazon has prompted ZDNet's Larry Dignan to state, "Amazon will be like a book store that sells cocaine out the back door. Books will be just a front to sell storage and cloud computing."
Apple's iCloud
 iCloud was released on June 6, 2011 at the Apple Worldwide Developers Conference. The free service allows users to store their mail, contacts, photos, calendar, and more information on Apple's cloud servers, and push the data to all iOS devices. This allows users' iPhones, iPads, and iMacs to be synced wirelessly and automatically. Developing from Apple's MobileMe software, iCloud is a huge improvement and makes Apple consumers' lives a lot easier.
iCloud was released on June 6, 2011 at the Apple Worldwide Developers Conference. The free service allows users to store their mail, contacts, photos, calendar, and more information on Apple's cloud servers, and push the data to all iOS devices. This allows users' iPhones, iPads, and iMacs to be synced wirelessly and automatically. Developing from Apple's MobileMe software, iCloud is a huge improvement and makes Apple consumers' lives a lot easier.
Dropbox
Dropbox is an application that can be installed on both your computer and your Android and iOS devices. It allows you to easily access files on the go. You can save something on your computer and access it on your mobile device.
Box.com
Box.com is a provider of cloud storage and seeks to differentiate itself among its competitors by targeting businesses and corporations. As part of the upcoming University of Michigan NextGen plan, the University of Michigan will utilize Box.com services for many of its backup data storage. As it spread throughout the neighbouring colonies, the news of Teach and Vane's impromptu party worried the Governor of Pennsylvania enough to send out two sloops to capture the pirates.[56] They were unsuccessful, but Governor of Virginia Alexander Spotswood was also concerned that the supposedly retired freebooter and his crew were living in nearby North Carolina. Some of Teach's former crew had already moved into several Virginian seaport towns, prompting Spotswood to issue a proclamation on 10 July, requiring all former pirates to make themselves known to the authorities, to give up their arms and to not travel in groups larger than three. As head of a Crown colony, Spotswood viewed the proprietary colony of North Carolina with contempt; he had little faith in the ability of the Carolinians to control the pirates, who he suspected would be back to their old ways, disrupting Virginian commerce, as soon as their money ran out.[57] Spotswood learnt that William Howard, the former quartermaster of Queen Anne's Revenge, was in the area, and believing that he might know of Teach's whereabouts had the pirate and his two slaves arrested. Spotswood had no legal authority to have pirates tried,[nb 7] and as a result, Howard's attorney, John Holloway, brought charges against Captain Brand of HMS Lyme, where Howard was imprisoned. He also sued on Howard's behalf for damages of £500, claiming wrongful arrest.[58] Spotswood's council claimed that Teach's presence was a crisis and that under a statute of William III, the governor was entitled to try Howard without a jury. The charges referred to several acts of piracy supposedly committed after the pardon's cut-off date, in "a sloop belonging to ye subjects of the King of Spain", but ignored the fact that they took place outside Spotswood's jurisdiction and in a vessel then legally owned. Another charge cited two attacks, one of which was the capture of a slave ship off Charleston Bar, from which one of Howard's slaves was presumed to have come. Howard was sent to await trial before a Court of Vice-Admiralty, on the charge of piracy, but Brand and his colleague, Captain Gordon (of HMS Pearl) refused to serve with Holloway present.[nb 8] Incensed, Holloway had no option but to stand down, and was replaced by the Attorney General of Virginia, John Clayton, who Spotswood described as "an honester man [than Holloway]".[59] Howard was found guilty and sentenced to be hanged, but was saved by a commission from London, which directed Spotswood to pardon all acts of piracy committed by surrendering pirates before 23 July 1718.[60][61] Meanwhile, Spotswood had obtained from Howard valuable information on Teach's whereabouts,[62] and he planned to send his forces across the border into North Carolina to capture him.[63] He gained the support of two men keen to discredit North Carolina's Governor—Edward Moseley and Colonel Maurice Moore. He also wrote to the Lords of Trade, suggesting that the Crown might benefit financially from Teach's capture. Spotswood personally financed the operation, possibly believing that Teach had fabulous treasures hidden away. He ordered Captains Gordon and Brand of HMS Pearl and HMS Lyme to travel overland to Bath. Lieutenant Robert Maynard of HMS Pearl was given command of two commandeered sloops, to approach the town from the sea.[nb 9] An extra incentive for Teach's capture was the offer of a reward from the Assembly of Virginia, over and above any that might be received from the Crown.[65] Maynard took command of the two armed sloops on 17 November. He was given 57 men—33 from HMS Pearl and 24 from HMS Lyme. Maynard and the detachment from HMS Pearl took the larger of the two vessels and named her Jane; the rest took Ranger, commanded by one of Maynard's officers, a Mister Hyde. Some from the two ships' civilian crews remained aboard. They sailed from Kecoughtan, along the James River, on 17 November.[66] The two sloops moved slowly, giving Brand's force time to reach Bath. Brand set out for North Carolina six days later, arriving within three miles of Bath on 23 November. Included in Brand's force were a number of North Carolinians, including Colonel Moore and Captain Jeremiah Vail, sent to put down any local objection to the presence of foreign soldiers. Moore went into the town to see if Teach was there, reporting back that he was not, but that the pirate was expected at "every minute." Brand then went to Governor Eden's home and informed him of his purpose. The next day, Brand sent two canoes down Pamlico River to Ocracoke Inlet, to see if Teach could be seen. They returned two days later and reported on what eventually transpired
See Also
References
- ↑ Cloud Computing
- ↑ Advanced Browsers Are Key To Mobile Cloud Computing
- ↑ In Cloud Computing We Trust—But Should We?
- ↑ The Real Realities of Cloud Computing: Ethical Issues for Lawyers, Law Firms, and Judges
- ↑ Cloud Computing: The Evolution of Software-as-a-Service
- ↑ The Six Benefits of Cloud Computing
- ↑ The Six Benefits of Cloud Computing
- ↑ The Six Benefits of Cloud Computing
- ↑ Cloud Computing, Digital Lockers and Copyright: The Cloudification of Entertainment
- ↑ The Privacy Implications of Cloud Computing