Difference between revisions of "Circumventing Internet Censorship"
| Line 1: | Line 1: | ||
| − | '''Circumventing Internet censorship''' is the process of using anti-censorship tools or software to bypass Internet [[censorship]] and filters. Certain countries like China and Iran have governments that enforce filters to censor what people can access on the Web. However, there are ways to get around these filters. Websites such as [http://www.circumventor.com/Circumventor.com] and [[Wikipedia:Peacefire|Peacefire.org]] are dedicated to distributing anti-censorship tools to users in these countries so that they may roam the | + | '''Circumventing Internet censorship''' is the process of using anti-censorship tools or software to bypass Internet [[censorship]] and filters. Certain countries like China and Iran have governments that enforce filters to censor what people can access on the Web. However, there are ways to get around these filters. Websites such as [http://www.circumventor.com/Circumventor.com] and [[Wikipedia:Peacefire|Peacefire.org]] are dedicated to distributing anti-censorship tools to users in these countries so that they may roam the internet freely. The use of using these tools explore the ethical issues of protecting children's welfare, ensuring physical safety for individuals using tools that are against government policies and invoking misconceptions towards the U.S. Constitutions. |
== Censorship == | == Censorship == | ||
| Line 5: | Line 5: | ||
=== Methods used by Governments to Censor the Web === | === Methods used by Governments to Censor the Web === | ||
| − | Often times, governments will directly contact certain web sites and request to censor | + | Often times, governments will directly contact certain web sites and request to censor internet content. Within the first six months of 2012, [[Google]] received more than 1,000 requests from governments around the world to remove items such as [[YouTube]] videos and search listings.<ref>[http://news.cnet.com/8301-1023_3-57454920-93/google-sees-alarming-level-of-government-censorship/ CNET News: Google sees 'alarming' level of government censorship]</ref> Most of the time, Google will consent to a majority of those orders and requests; however, certain countries, such as China and Iran, block content without notifying Google. |
== Circumvention technologies == | == Circumvention technologies == | ||
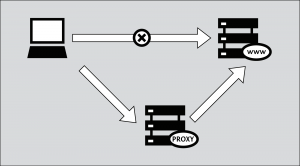
| − | The tools, methods, and strategies that are used to by-pass | + | The tools, methods, and strategies that are used to by-pass internet content filtering are referred to as circumvention technologies. Because of the growing global problem of censorship and abuses of free speech, citizens around the world are fighting to avoid government filters and be able to exercise free speech and have free access to the information of their own choosing. [[File:Circumvention.png|thumb|Method to bypass filtering]] |
=== How circumvention works === | === How circumvention works === | ||
| − | Users are blocked from connecting directly to the website, so they must connect through some third party site or machine outside of that country | + | Users are blocked from connecting directly to the restricted website, so they must connect through some third party site or machine, which is outside of that country, and which fetches the desired content to send it back to the requesting user.<ref>[http://www.igniteseattle.com/2011/12/bennett-haselton-circumventing-internet-censorship-around-the-world/ Ignite Seattle: Bennett Haselton – Circumventing Internet censorship around the world] </ref> It is relatively simple to disable most blocking programs, and there are numerous ways to beat a smart filter under a variety of circumstances and by a wide range of users. Typically it takes only four or five steps to do so, depending on how the user is accessing the internet. This is either done through software that is installed on the user's computer, or manually, when the user goes through a third-party proxy server to avoid having to use the server on which the smart filter or censoring operates. Most proxy sites will allow users to enter their email so that they can receive new proxy sites if and when the first site gets blocked. Although there are many ways to gain access to a blocked site, it is important to find a secure method and to fully understand the technology used for circumvention. |
==== Other tools to defeat censorship ==== | ==== Other tools to defeat censorship ==== | ||
| Line 26: | Line 26: | ||
=== Issues with children === | === Issues with children === | ||
| − | The use of censorship techniques oftentimes | + | The use of censorship techniques oftentimes is deployed against the user's will, in order to protect their welfare and safety. In the Information Age, children have access to a nearly unlimited amount of information, and most Americans have agreed that exposure to sexual imagery will do irreparable harm to their children. Therefore, censorship is appropriate for them and widely accepted in this context. Opponents of censorship, such as [[Wikipedia:Bennett_Haselton|Bennett Haselton]], creator of Circumventor.com, and Peacefire.org, want to create awareness and report imperfections in regards to internet blocking programs. Haselton believes the internet is not dangerous to children and that it is unfair to deprive them because of their youth. Despite the criticism of circumvention, there has been little evidence that children are harmed from unfiltered graphic material, or which proves that the internet should be seen as a detrimental tool. Some believe it is important for children to have access to new information so they will be able to thrive culturally and succeed educationally and economically.<ref>[http://www.freedomforum.org/templates/document.asp?documentID=11141 Freedom Forum: Peacefire: Unblocking information]</ref> |
=== Issues with countries that censor === | === Issues with countries that censor === | ||
| − | Trying to access content that is highly critical and is considered a security threat to the country can be a dangerous practice and a serious violation of the law. High profile human rights organizations and groups may be on the government’s watch list and constantly monitored. Internet users need to take extreme | + | Trying to access content that is highly critical of a government and is considered a security threat to the country can be a dangerous practice and a serious violation of the law. High profile human rights organizations and groups may be on the government’s watch list and constantly monitored. Internet users need to take extreme caution when choosing to use circumvention technologies that offer anonymity and security, because the government may seize the computer at any time and may even have a precedent for arrests for the practice of circumventing internet censorship.<ref>[http://www.masternewmedia.org/privacy_security/bypass-internet-censorship/bypass-internet-filters-anonymous-browsing-guide-20071118.htm Master Media: How To Bypass Internet Censorship And Filters]</ref> |
=== Misconceptions === | === Misconceptions === | ||
| − | According to the [http://www.law.cornell.edu/constitution/first_amendment First Amendment] | + | According to the [http://www.law.cornell.edu/constitution/first_amendment First Amendment] of the U.S. Constitution, congress shall make no law which prohibits free speech.<ref>[http://www.law.cornell.edu/constitution/first_amendment Cornell University Law School: First Amendment]</ref> However, there are certain cases that the first amendment does not protect. Laws exist regarding libel, obscenity, national security, access to government information, and regulation of electronic mass communications.<ref>[http://courses.cs.vt.edu/cs3604/lib/Censorship/notes.html The Internet Censorship Controversy]</ref> |
=== Battle between the censors and the circumventors === | === Battle between the censors and the circumventors === | ||
Revision as of 12:37, 26 April 2019
Circumventing Internet censorship is the process of using anti-censorship tools or software to bypass Internet censorship and filters. Certain countries like China and Iran have governments that enforce filters to censor what people can access on the Web. However, there are ways to get around these filters. Websites such as [1] and Peacefire.org are dedicated to distributing anti-censorship tools to users in these countries so that they may roam the internet freely. The use of using these tools explore the ethical issues of protecting children's welfare, ensuring physical safety for individuals using tools that are against government policies and invoking misconceptions towards the U.S. Constitutions.
Contents
Censorship
Many countries have filtering policies to block users from visiting certain sites used for gaming, entertainment, and social networking. The main reason for doing this is so that they prevent dissidents from posting rebellious, threatening, or undesirable material that is critical of those countries. In the United States, public institutions such as schools and libraries are required to use filtering software to block access to certain existing public content such as obscene, pornographic, or other materials related to the sexual exploitation of children.
Methods used by Governments to Censor the Web
Often times, governments will directly contact certain web sites and request to censor internet content. Within the first six months of 2012, Google received more than 1,000 requests from governments around the world to remove items such as YouTube videos and search listings.[1] Most of the time, Google will consent to a majority of those orders and requests; however, certain countries, such as China and Iran, block content without notifying Google.
Circumvention technologies
The tools, methods, and strategies that are used to by-pass internet content filtering are referred to as circumvention technologies. Because of the growing global problem of censorship and abuses of free speech, citizens around the world are fighting to avoid government filters and be able to exercise free speech and have free access to the information of their own choosing.How circumvention works
Users are blocked from connecting directly to the restricted website, so they must connect through some third party site or machine, which is outside of that country, and which fetches the desired content to send it back to the requesting user.[2] It is relatively simple to disable most blocking programs, and there are numerous ways to beat a smart filter under a variety of circumstances and by a wide range of users. Typically it takes only four or five steps to do so, depending on how the user is accessing the internet. This is either done through software that is installed on the user's computer, or manually, when the user goes through a third-party proxy server to avoid having to use the server on which the smart filter or censoring operates. Most proxy sites will allow users to enter their email so that they can receive new proxy sites if and when the first site gets blocked. Although there are many ways to gain access to a blocked site, it is important to find a secure method and to fully understand the technology used for circumvention.
Other tools to defeat censorship
- Cached pages
- Translation services
- RSS Aggregators
- Alternate Domain Names
- Web Accelerator
- Virtual Private Networks
- Proxies
Developers of circumvention software
Ethical Issues
Issues with children
The use of censorship techniques oftentimes is deployed against the user's will, in order to protect their welfare and safety. In the Information Age, children have access to a nearly unlimited amount of information, and most Americans have agreed that exposure to sexual imagery will do irreparable harm to their children. Therefore, censorship is appropriate for them and widely accepted in this context. Opponents of censorship, such as Bennett Haselton, creator of Circumventor.com, and Peacefire.org, want to create awareness and report imperfections in regards to internet blocking programs. Haselton believes the internet is not dangerous to children and that it is unfair to deprive them because of their youth. Despite the criticism of circumvention, there has been little evidence that children are harmed from unfiltered graphic material, or which proves that the internet should be seen as a detrimental tool. Some believe it is important for children to have access to new information so they will be able to thrive culturally and succeed educationally and economically.[3]
Issues with countries that censor
Trying to access content that is highly critical of a government and is considered a security threat to the country can be a dangerous practice and a serious violation of the law. High profile human rights organizations and groups may be on the government’s watch list and constantly monitored. Internet users need to take extreme caution when choosing to use circumvention technologies that offer anonymity and security, because the government may seize the computer at any time and may even have a precedent for arrests for the practice of circumventing internet censorship.[4]
Misconceptions
According to the First Amendment of the U.S. Constitution, congress shall make no law which prohibits free speech.[5] However, there are certain cases that the first amendment does not protect. Laws exist regarding libel, obscenity, national security, access to government information, and regulation of electronic mass communications.[6]
Battle between the censors and the circumventors
See Also
External links
- How to Beat a Smart Filter - eHow
- Bennett Haselton - Wikipedia the free encyclopedia
- Wikipedia:Peacefire Peacefire - Wikipedia the free encyclopedia
References
- ↑ CNET News: Google sees 'alarming' level of government censorship
- ↑ Ignite Seattle: Bennett Haselton – Circumventing Internet censorship around the world
- ↑ Freedom Forum: Peacefire: Unblocking information
- ↑ Master Media: How To Bypass Internet Censorship And Filters
- ↑ Cornell University Law School: First Amendment
- ↑ The Internet Censorship Controversy
http://www.flossmanuals.net/bypassing-censorship/
| ←Back • ↑Top of Page |