Carding Fraud
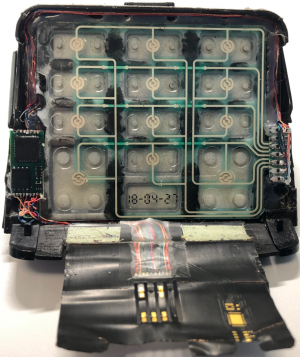
Carding refers to a type of fraudulent activity involving the theft and unauthorized use of credit cards. Typically, carding involves using the stolen card to purchase prepaid gift cards or other merchandise that can be resold, or reselling the card information in online markets. The term "carders" refers to criminals who engage in carding related activities.[2] The Nilson Report states that "Gross fraud losses to issuers, merchants and acquirers of card transactions from merchants, as well as acquirers of card transactions from ATMs reached $28.65 billion" in 2019, and that 33.57% of these losses came from the United States. These losses do not include the costs of fraud prevention and detection to retailers.[3]
Contents
Carding Methods
Carding begins with carders obtaining card numbers and other information that allows them to impersonate the card holder. There are a variety of methods used to acquire card numbers and other information.[4]
Online forums & Marketplaces
Forums and Markets on the Web as well as hosted as hidden services on the dark web provide carders with resources as well as opportunities to buy and sell stolen credit card information.[5] Estimates for the total sales of personal information on the dark web is roughly one billion dollars per year. This information can be used to take over financial accounts.[6] The carding community using these sites remains resilient to raids by law enforcement. Following raids, the number of carding markets has historically decreased temporarily before recovering again.[7] While raids do not eliminate markets all-together, they do decrease market activity as smaller markets compete for new business.[8] Due to lack of regulation, scams are common on these illegal markets, however, some vendors do provide legitimate products as good reputation can be more lucrative.[9] Many of the operators of these markets conduct their business with a high degree of professionalism in an effort to compete for customers. For example, some sites advertise refunds to customers that purchase card information that does not work.[10]
Skimming
Skimming is the technique of modifying point of sale devices to steal data. This is commonly done with an overlay terminal that reads data from the magnetic strip on credit cards. Overlay terminals are designed to fit over, and appear like, a regular point of sale device as to avoid detection. Popular skimming targets among carders include card readers in stores, gas pumps, and ATM machines.[11] Modern skimming devices are often very difficult to detect, sometimes even fitting inside the reader itself, and using tiny cameras to capture PIN numbers. The design of point-of-sale devices are often designed to be compatable with older card technology, such as cards with raised text. These design features are well known to skimmer creators, who utilize this extra space to create deep insert skimmers that fit entirely inside the reader. Some designs can be so thin that they don't even have room for their own power supply, instead utilizing the NFC waves from the card chip itself for power.[12] The exact origin of skimming is unclear, but the back and fourth battle of detection and evasion is not new. Carders operating skimmers have even found ways to bypass protections for some smart chip cards by exploiting flaws in the verification done by financial institutions.[13]
Data Breaches
Credit card information can be leaked after retailers that store payment data become victims of hackers. In 2014, large U.S. based retailer Home Depot suffered a data breach due to hackers using custom exploits to gain access to their payment data. The breach exposed the information of over 40 million customers.[14] The number of data breaches has reached record highs in recent years, and shifts towards supply chain attacks indicate that data breaches will continue to be an issue in the foreseeable future.[15] Data breaches can also occur due to employees rather than hackers. One example of this happened in New York where employees of Saks Fifth Avenue use customer's credit card information to make $400,000 worth of purchases. The breach was not discovered for four months.[16]
Social Engineering
Social Engineering encompasses practices involving deceiving and manipulating card holders or businesses to gather information. Social engineering is a growing problem, with malicious emails increasing in frequency by 600% during the coronavirus pandemic.[17] One case of carders employing social engineering occurred at a Hilton Garden Inn in Dallas Texas when the carders called hotel guests and pretended they were a hotel employee verifying credit card numbers after a computer issue.[18] There are many other ways that carders can use such as Email or text, usually involving impersonating a trusted institution.[19]
BIN Attack
BIN or Bank Identification Number is used to indicate what financial institution a credit card belongs to.[20] A BIN attack is where carders use a valid BIN number to generate lots of random credit card numbers, then test these numbers to find valid numbers. Generally, computers are used to automate the generation and testing of the card numbers.[21] BIN attacks are one of the simplest ways to find valid cards as cards can be tested in large quantities by computers that submit test payments with real merchants. If the information is valid and the transaction is not flagged as fraudulent, then the attack operator can use or sell the card information.[22] BIN attacks can be harmful to online merchants as they can be difficult to detect without proper fraud detection.[23]
Cashing Out
A common method carders use to make profit is the following:
- Carders create listings for easily sellable items on markets such as Ebay.
- When a bidder wins a bid for the carder's listing, the carder places an order with a real vendor of the item with the stolen credit card information
- If the payment is successful, the real vendor will ship the item to the bidder.
In this scheme the bidder is not aware of any fraudulent activity, and either the real card holder will not notice the charge, or will file a fraud claim and the real vendor will be required to cover the loss.[24]
Prevention
Merchant Mitigations
Due to substantial losses, merchants employ numerous strategies to make carding fraud difficult, and detection easier. Card processors use Address Verification Systems so that merchants can check a provided billing address against the billing address on file with the issuing bank.[25] This strategy makes it more difficult for carders, but can be circumvented by using social engineering or other methods to get the correct billing address. CVV security codes also add additionally security to transactions because are on the opposite side of the card as the card number and therefore require access to both sides. CVVs are used to verify that the purchase was made by the real card owner. Online merchants do not store CVVs with credit card information, thus requiring CVVs can be an effective measure against data breaches as the leaked data will not include CVVs with card information.[26] Even though CVVs add additional requirements for carders to complete fraudulent card-not-present transactions, techniques like BIN attacks can still be used to generate and test CVVs.[27] Merchants using physical point-of-sale devices should regularly check for skimmers, and keep devices in view of employees. Merchants should also be explicit about policies for when, where, and what information will be required from customers so that customers can be aware of social engineering attempts that conflict with these policies. Merchants should also collect and store as little personal information as required, and only provide access to trusted employees, as to limit the damage of a potential data breach.
Card Holder Mitigations
Many card issuers have zero liability policies that protect card holders from being responsible for carding fraud in most cases. Fraud victims should contact their bank immediately if suspicious activity is spotted on their account. Risk of fraud can be reduced by checking for skimmers at point-of-sale devices and ATMs, keeping all personal information private, and being aware of common social engineering techniques such as fake emails asking for personal information.[28] Covering the PIN pad when using an ATM or point-of-sale device is also an effective protection against hidden cameras or bystanders.[29] If the option is available, making payments by tapping contactless cards is more secure than cards that only swipe. Card holders have fewer mitigations available to prevent data breaches and BIN attacks because they involve the systems used by merchants and card networks.
Card Issuer Mitigations
Card Issuers provide some security built into cards and networks. Anti-fraud detection systems built into the networks of card issuers analyze transactions using AI or other analytic tools in order to try and spot potential fraud. These algorithms can consider factors like transaction amount, time, and place.[30] Other solutions to add security include virtual cards, such as those provided by Privacy, that have more restrictions and options for user control. These options include spending restrictions, as well as creating single use cards that allows users to make single transactions without worrying about future fraudulent charges as a result.[31]
Card Design
Card Issuers have also made use of smart chip cards that allow for contactless payment, EMVs, which have become common in the United States.[32] Use of EMV cards has seen quicker adoption in Europe. [33] EMV cards contain a microprocessor that verifies each transaction by providing a unique code, called an iCVV, or dynamic CVV.[34] The iCVV is not able to be reused in the case that it is recovered by an attacker, thus providing extra security.[35] Some of these improved security features are not as effective in practice, as many cards still have magnetic strips that are easily skimmed. In addition, some verification implementations do not properly distinguish between iCVVs used in contactless payments and CVVs used for swipes. This implementation flaw has been found to allow adversaries to successfully approve transactions made with clones of EMV cards.[36] Despite some issues, smart chip cards are much more secure than magnetic swipe cards, and are more difficult and costly to clone. Other techniques used by carders is creating skimmers that block contactless cards from being read, forcing users to swipe their card so the skimmer can read the magnetic strip.[37] Newer developments allow technologies like Apple's Advanced Fraud Protection setting, which takes advantage of the phone's NFC capabilities to automatically change CVV codes periodically.[38]
Ethics & Legality
Generally, the act of obtaining card information of someone else without authorization is illegal. In the United States, criminals charged with operating skimming devices are charged with access device fraud conspiracy and can face up to ten years in prison.[39] The Computer Fraud and Abuse Act establishes a maximum of 10 or 20 years for hacking related crimes, depending on specifics.[40] Punishments for unauthorized use of a credit card can range widely depending on the amount, as well as if the crime is classified as a felony or misdemeanor. Fines can range from $1,000 to $25,000 and prison time can range from 0 to 25 years, but these are subject to variation by state.[41]
In the United States, the Fair Credit Billing Act protects card holders that fall victim to carding fraud from paying more than $50.[42] Much of the losses from carding fraud fall on card issuers, about 68.39% of worldwide gross losses. The rest mostly harms merchants.[43] While much of the monetary costs do not fall directly on the card holder, merchants and card issuers may respond to losses by increasing prices rather than security measures. Card holders may also face other challenges, for example Merchants using Address Verification Systems can require card holders to update their billing address before using their card after changing residence.[44] In addition, card issuers may require fraud claims to be disputed due to chargeback fraud. Chargeback fraud occurs when a card holder claims that a purchase they made was fraudulent, and requests a chargeback from their bank with the hopes of getting the money back while keeping the merchandise. Card issuers investigate fraud claims for this reason, and the investigation takes time before the bank makes a decision meaning card holders must wait for, and may be declined, their chargeback.[45]
American beneficiaries of the Supplemental Nutrition Assistance Program (SNAP) May be at a higher risk of becoming a victim to carders using skimmers. SNAP provides low income with cards that are like prepaid debit cards and can be used to purchase necessary food items.[46] These issued cards do not have smart chip technology in most states, and some experts argue that this makes they easier targets for carders.[47] In addition, U.S. federal law restricts states from using federal funding to cover the costs of stolen aid, leaving the responsibility of covering and preventing losses to the low income families most affected.[48] One documented case where a woman had almost $3k worth of SNAP benefits stolen occurred in Baltimore County. Her benefits have not been reimbursed even after Police found a card skimmer and surveillance footage of the suspects purchasing large quantities of baby formula was found.[49] Low income families that rely on SNAP becoming victims of card skimming is a growing problem in many states including Massachusetts, where The Massachusetts Law Reform Institute has filed a class action law-suite against the Department of Transitional Assistance on behalf of these victims.[50] Their aim is to increase the accountability of the involved government entities and simplify the process of restoring stolen benefits.
Because of zero liability policies, the Fair Credit Billing act, and other security features of card networks, most users are at low risk of real harm from carding fraud. The same cannot be said for users of SNAP, as many are required to use low security cards without any chip technology. SNAP users are also not protected in the case of carding fraud because the Fair Credit Billing Act does not apply, instead the law restricts federal funding to be used this way.
Studies conducted by the Federal Trade Commission have consistently found across multiple studies that Black and Latino consumers are more likely to have experienced fraud. The FTC also reports that Black and Latino communities are less likely to report fraud. The report also found Black and Latino communities more likely to use debit cards than credit cards.[51] While both types of cards are susceptible to fraudulent charges, the law for debit card fraud liability, The Electronic Funds Transfer Act, is not as protective as The Fair Credit Billing Act. If fraudulent transactions are not noticed quickly, the liability of the card owner can increase up to the full amount lost after 60 days.[52]
See Also
References
- ↑ Checkout Skimmers Powered by Chip Cards Krebs on Security https://krebsonsecurity.com/wp-content/uploads/2021/02/overlay-shim.png
- ↑ https://www.investopedia.com/terms/c/carding.asp
- ↑ https://nilsonreport.com/mention/1313/1link/
- ↑ https://www.forbes.com/advisor/credit-cards/how-credit-card-information-is-stolen-and-what-to-do-about-it/
- ↑ https://eprints.soton.ac.uk/413441/1/Final_Paper_After_Acceptance.pdf
- ↑ https://nilsonreport.com/mention/1313/1link/
- ↑ https://aisel.aisnet.org/wisp2018/20/
- ↑ https://blog.chainalysis.com/reports/how-darknet-markets-fought-for-users-in-wake-of-hydra-collapse-2022/
- ↑ https://web.archive.org/web/20151105234414/http://www.mcafee.com/us/resources/reports/rp-hidden-data-economy.pdf
- ↑ https://krebsonsecurity.com/2020/03/russians-shut-down-huge-card-fraud-ring/
- ↑ https://abcnews.go.com/GMA/News/video/credit-card-skimming-crimes-rise-96656884
- ↑ https://krebsonsecurity.com/2022/09/say-hello-to-crazy-thin-deep-insert-atm-skimmers/
- ↑ https://krebsonsecurity.com/2020/07/is-your-chip-card-secure-much-depends-on-where-you-bank/
- ↑ https://www.reuters.com/article/us-home-depot-cyber-settlement-idUSKBN2842W5
- ↑ https://www.idtheftcenter.org/wp-content/uploads/2023/01/ITRC_2022-Data-Breach-Report_Final.pdf
- ↑ https://www.esecurityplanet.com/networks/insider-credit-card-breach-leads-to-400000-saks-shopping-spree/
- ↑ https://www.businessinsider.com/top-un-official-warned-of-cybercrime-spike-during-pandemic-2020-5
- ↑ https://www.nbcnews.com/id/wbna43662080
- ↑ https://lifelock.norton.com/learn/identity-theft-resources/what-is-carding
- ↑ https://www.investopedia.com/terms/b/bank-identification-number.asp
- ↑ https://www.ascentra.org/learn/news-blogs/article/2022/07/26/credit-card-fraud-bin-attacks
- ↑ https://thepointsguy.com/guide/bin-attack-credit-card/
- ↑ https://news.toolcase.com/2022/06/23/bank-identification-number-bin-attacks-how-to-detect-and-prevent-them/
- ↑ https://krebsonsecurity.com/2015/11/how-carders-can-use-ebay-as-a-virtual-atm/
- ↑ https://www.investopedia.com/terms/a/address-verification-system.asp
- ↑ https://www.americanexpress.com/en-us/credit-cards/credit-intel/what-is-cvv/?linknav=creditintel-cards-article
- ↑ https://insights.co-opfs.org/blog/bin-attacks-are-rising-heres-how-your-credit-union-can-fight-back-against-card-fraud
- ↑ https://www.emerald.com/insight/content/doi/10.1108/13590790810907236/full/html#idm46555354902368
- ↑ https://krebsonsecurity.com/2017/08/dumping-data-from-deep-insert-skimmers/
- ↑ https://usa.visa.com/visa-everywhere/security/outsmarting-fraudsters-with-advanced-analytics.html
- ↑ https://support.privacy.com/hc/en-us/articles/360046205473-What-is-Privacy-
- ↑ https://www.forbes.com/advisor/credit-cards/contactless-credit-cards/
- ↑ https://www.theguardian.com/commentisfree/2014/jan/27/target-credit-card-breach-chip-pin-technology-europe
- ↑ https://krebsonsecurity.com/2020/07/is-your-chip-card-secure-much-depends-on-where-you-bank/
- ↑ https://usa.visa.com/content/dam/VCOM/Media%20Kits/PDF/PaymentSecurity_Infographic.pdf
- ↑ https://krebsonsecurity.com/2020/07/is-your-chip-card-secure-much-depends-on-where-you-bank/
- ↑ https://krebsonsecurity.com/2021/02/bluetooth-overlay-skimmer-that-blocks-chip/
- ↑ https://support.apple.com/guide/security/apple-card-security-secb29b74e98/web
- ↑ https://www.law.cornell.edu/uscode/text/18/1029
- ↑ https://www.nacdl.org/Landing/ComputerFraudandAbuseAct
- ↑ https://legalbeagle.com/13720951-california-credit-card-fraud-laws-an-overview.html
- ↑ http://uscode.house.gov/view.xhtml?req=granuleid%3AUSC-prelim-title15-chapter41-subchapter1-partD&edition=prelim
- ↑ https://nilsonreport.com/mention/1313/1link/
- ↑ https://www.investopedia.com/terms/a/address-verification-system.asp
- ↑ https://chargebacks911.com/credit-card-fraud-investigation/
- ↑ https://www.benefits.gov/benefit/361
- ↑ https://krebsonsecurity.com/2022/10/how-card-skimming-disproportionally-affects-those-most-in-need/
- ↑ https://krebsonsecurity.com/2022/11/lawsuit-seeks-food-benefits-stolen-by-skimmers/
- ↑ https://www.thebaltimorebanner.com/community/criminal-justice/one-womans-quest-for-justice-after-almost-3000-of-benefits-were-stolen-LHIKMQZSNJBULC7LXCEIE264OA/
- ↑ https://drive.google.com/file/d/1R11j74KZsBRLJAyHlBYiRBQTxJQSfdkc/view
- ↑ https://www.ftc.gov/system/files/documents/reports/serving-communities-color-staff-report-federal-trade-commissions-efforts-address-fraud-consumer/ftc-communities-color-report_oct_2021-508-v2.pdf
- ↑ https://www.experian.com/blogs/ask-experian/are-credit-cards-safer-than-debit-cards/