BitTorrent
BitTorrent, also known as Mainline by web developers is the peer-to-peer file sharing protocol used by many P2P clients. It was designed by computer programmer Bram Cohen in April 2001 [1]. The protocol permits users to connect across the internet and share certain files with other users within the torrent network. BitTorrent, one of the most prevalent protocols for moving big files, has been estimated to constitute 70% of all internet traffic. The first version of the BitTorrent was released on July 2, 2001; the current version is available for Mac OS X and Microsoft Windows.
Because Bittorrent is a client application that mainstreams peer-to-peer (P2P) file sharing through the torrent protocol, it can be easily used in the major controversial activity of piracy through the Internet. Due to this largely known illegal usage, the constant ethical battle between the fight against piracy and the freedom of peer-to-peer file sharing has created a huge riff between the two belief systems in how to use Bittorrent properly and even if it should be used at all.
Contents
Torrent
A torrent file is the basis of the peer-to-peer connection in that it holds a description of the location of the various pieces of the file that is being shared. The torrent is not the actual file being shared however, it is just a mapping of the smaller portions. Torrents are hosted by third parties online but it was made to be easily accessible and searchable by BitTorrent clients and torrent-specific search engines.
Mechanics
When a user downloads a torrent file, it contains a hash of the files to be downloaded. It also contains a list of servers, known as trackers, that the user can connect to in order to find BitTorrent users which are seeding the necessary files. After the user connects and receives the list of users sharing the file, the user's BitTorrent client will connect to these users. The aggregate of all the connections is known as the user's swarm. The client will begin by sending out requests to the swarm in order to obtain a list of which pieces are available to download, then it will make requests for those files. In turn, the swarm will begin sending its own requests for pieces which the user's client can then reciprocate. The process of downloading a file using a BitTorrent client is known as leeching. Once the files are finished downloading, the user can remain in the swarm and continue sharing pieces, also known as seeding. It is important for a torrent to always have at least several users who are seeding a file, or else the torrent will die. The torrent dies when new users are unable to download any pieces at all, or are stuck at a certain percentage and unable to obtain any further pieces.
Sharing
In regards to the BitTorrent protocol, uploading or sharing pieces is commonly referred to as seeding. When a user downloads without seeding, they are said to be leeching. Torrent files are designed so that users may seed portions before they have downloaded the entire file, meaning others can download parts of the file from the user, even before the user has finished downloading it. The fact that only portions of a file can be downloaded from multiple sources is a large factor in the popularity of BitTorrent applications. Since this method of file sharing aggregates pieces of files from many different locations, it also magnifies the risks and responsibilities associated with file sharing.
Seeding
Seeding is a way of reciprocating the effort of the users who originally made the files available. The intent is that they are passing the proverbial torch to you, so that they can move on to sharing other files. This results in a domino effect that increases the files' availability and results in faster downloads for all.[2] Most BitTorrent clients limit a user's download speed in correspondence with the frequency and capacity of their uploading. This reduces the amount of leechers , users who download files but do not contribute to the array of uploading hosts, by making contributions imperative to the system.
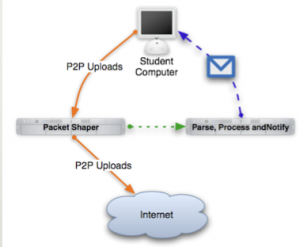
- Be Aware You're Uploading or more commonly referred to as BAYU is an initiative adopted by many large universities or organizations that actively seek ways to reduce the risk of students becoming affiliated and getting involved in piracy lawsuits. At the University of Michigan Ann Arbor, before the program shuts down, it alerts staff and students about their illegal uploading or downloading by sending email notifications until the system determines that they are aware of their actions. At this particular school, BAYU was not a disciplinary entity and was not responsible for handling any litigation regarding illegal file sharing. It was merely a courtesy service implemented in direct response to the large numbers of users on extensive networks that are unaware that they are currently uploading content regardless of the legality of such content. At the University of Michigan, students and staff had the ability to opt-out of having any future BAYU notifications.[3]
ISP Throttling
Internet Service Providers(ISP) have the ability to control exactly how much of their bandwidth is allotted for certain customer tasks, much like the throttle on a simple engine. The concept of throttling bandwidth by ISPs is nothing new and is done for reasons such as upholding contractual partnerships with certain websites as well as limiting the advantages of BitTorrent.
- Research published by Measurement Lab revealed statistics involving several large ISPs and their throttling procedures:[4]
- After an FCC investigation and being ordered to stop placing data caps on ports used for BitTorrent, Comcast is down to throttling only 3% of traffic from nearly 50% in early 2008[4]
- Comcast remains the ISP in the United States that limits BitTorrent traffic the least
- Clearwire remains the most throttled network with approximately 17% of all traffic throttled
- Canadian ISP Rogers limits 78% of all BitTorrent traffic
- Videotron limits only 3% of Canadian traffic
Legal Use
File sharing through the use of BitTorrent applications is currently legal, and is widely used by many organizations due to the benefit of having a large number of users willing to host files. This allows such organizations to cut costs by not hosting large files for a large pool of customers, and in turn dramatically increases the speed of downloads by utilizing multiple hosts simultaneously. BitTorrent is growing extremely popular with Open Source Software as well as with the commercial software industry.
- Blizzard Entertainment is just one example of a large commercial software company that distributes its extremely large files via BitTorrent. The reason downloading software that was originally intended to be shared via BitTorrent is currently legal is that companies often use activation or subscription codes in order to continually use the product. Without an active account or subscription, the downloaded software is useless.
- Many bands, both popular and rising, use legal file-sharing sites to spread their work and generate publicity. [5]
The use of such applications in order to share material protected under copyright is illegal. Despite being illegal, the use of torrents is constantly increasing due to the extreme ease and low risk with which one can obtain copyrighted material.
- As of Fall 2011, Voltage Pictures is currently involved in lawsuits against approximately 2,300 defendants in direct response to their use of BitTorrent clients to illegally share copies of the movie The hurt Locker. Although large numbers of IP addresses are being added to dismissed from Voltage's long list of defendants on a daily basis, a large number of their original 24,583 defendants have been dismissed. The list of IP addresses includes clients from most major service providers, some of which, have yet to be served. Settlements with Voltage Pictures are estimated to cost thousands of dollars.[6]
- In October 2011 Torrent Freak compiled a list of the top ten illegally downloaded movies using the BitTorrent protocol:[7]
Rank Movie Downloads Worldwide Grosses 1 Avatar(2009) 21 million $2,782,275,172 2 The Dark Knight(2008) 19 million $1,001,921,825 3 Transformers(2007) 19 million $709,709,780 4 Inception(2010) 18 million $825,408,570 5 The Hangover(2009) 17 million $467,483,912 6 Star Trek(2008) 16 million $385,680,446 7 Kick-Ass(2010) 15 million $96,188,903 8 The Departed(2006) 14 million $289,847,354 9 The Incredible Hulk(2006) 14 million $263,427,551 10 Pirates of the Caribbean: At World's End(2007) 14 million $963,420,425
You Have Downloaded
You Have Downloaded is a site that tracks about 20% of all downloads through torrents and tells users what they have torrented. According to Techcrunch "the site likely breaks down all of the new torrents to land on The Pirate Bay, and then holds on to the IP addresses it finds."[8] When you land on the homepage of Youhavedownloaded, a user is told whether YouHaveDownloaded has any information on them.
The service has proven to expose many people. It has been reported that employees from Sony, Universal, and Google have pirated content[8]. Additionally, it has been reported that IP addresses of an official residence belonging to the French President Nicholas Sarkozy have BitTorrented six files[9]. This information comes as a shock, since the Sarkozy government supports France's three strike rule that bans a user from the internet for up to 12 months if they are caught downloading copyrighted material illegally. Based on this law, Sarkozy's residence should go offline for the next 12 months[10].
Ethical Implications
There are a variety of ethical implications surrounding the use of BitTorrent applications.
Copyright
Although these torrenting applications are currently legal, it is illegal to share material that is protected under copyright. This bodes the questions whether or not users will abide by these loosely established laws. The BitTorrent software grants users the abilities to access data that they might not have permission to access and thus there are a variety of ethical concerns surrounding the use of torrenting applications. Is it the user's responsibility to properly use the software the way it was intended to be used? Should they be accountable if they abuse the software they are presented with? Or should the companies that produce the software be the ones held responsible when their software is misused? It is a tough and seemingly impossible question to fully resolve, but will most definitely be a topic of debate as torrenting continues to have more of an impact in today's society.
Recently, Congress has been discussing a bill called the SOPA Act or the Stop Online Piracy Act that, among various other things, will raise the power of law enforcement on technologies that support pirating, including BitTorrent. The bill marks a strong line about the ethics of pirating, indicating that it is morally wrong to share material. Companies like Google and Facebook have debated the merits of the bill.[11]
Alternate Models of Copyright
In light of new research indicating that filesharing leads to a growth in music sales [12], alternate interpretations of copyright law's ideal function deserve some consideration.
The current copyright model in the US protects the publishers and distributors of media by attempting to sanction any transaction other than direct purchase that spreads copies of media. Considering a consumer's perspective in assessing value of media, it stand to reason that less restrictions of copy distribution would increase the maximum price point; if John can only burn his CD onto one computer, why would he pay as much as if he could transfer it between all of his media equipment[13]?
From an artist's perspective, consider the Hip-Hop boom of the 1990s; sampling of copyrighted material was integral to the creation of new hip-hop. Without copyright infringement, the music industry would most likely not have had such an array of artists to market and revenue would suffer as a reult[13]. Additionally, artists have a longstanding tradition of freely borrowing each other's work in creating their own[13]. Notable for this practice are Morrisey, Oscar Wilde, and Jim Jarmusch. Considering the mass of creative work that depends on intertextual utilization of source material, looser copyright restrictions, or copyright restrictions designed to enable artists rather than staunchly protecting publisher's exclusive rights to control use, could actually benefit both the creative community and the publishing companies by enabling artists to create more media on their own terms.
File Sharing Culture
Torrenting has developed an entire culture around the ideas of reciprocity and the common good, an area of study which is common among the social sciences. Without generosity, torrenting communities and trackers would inevitably become obsolete. Specifically, if most users were to only leech files and never seed them, the file swarms would quickly dissolve and the torrents would slowly die. Over time, this would lead to a reduction in both the quantity and quality of available material. There are not many ways to force users to upload the torrents that they have downloaded, but one way that has seemed effective is by using private tracking websites.
Private trackers are communities where users have to be invited by current members. Most private trackers are very exclusive, requiring an invitation, in order to preserve the integrity inside the community since every user is vouched for by the person who invited them. These invitations are usually handed out to trusted users who have achieved a certain status inside the community, which is evaluated based on their overall contributions to the community. The only time that these trackers hold open registrations is when they perform mass deletions of accounts that have not been active, and certain highly-exclusive trackers do not ever have open registrations. In order to make sure that all users upload the torrents that they download, these trackers maintain enforced sharing ratios for all users, where the ratio is defined as amount uploaded divided by the amount downloaded, usually in megabytes or gigabytes. Most private trackers enforce a threshold, usually .60 or in the worst cases 1.00, that users must maintain their ratio above in order to continue downloading torrents. In addition to this rule, private trackers require the user to seed the downloaded torrent for at least one full copy (the size of the file) or for a certain amount of time, which varies amongst different trackers. If a user falls under the threshold that the tracker has set, they will go on "ratio watch," or in other words, they will be warned that their ratio is too low and that they must increase it. Users are generally given a certain amount of time to increase their ratio above the threshold before their account is suspended or banned. Thus, if a user only leeches files and never seeds them, their ratio will consistently fall under the threshold and will eventually lead to a ban. Some private trackers have "free leech" torrents where the download does not count towards your ratio but any subsequent amount that is uploaded does. This allows users to build up their ratio.
Hacking and Viruses
Many of the most popular torrenting websites, The Pirate Bay in particular, are littered with viruses developed by hackers. These viruses can be simple viruses that will shut down users computers or simply troll users as well as incredibly powerful viruses that will steal users information, banking and credit information in particular, resulting in significant money being lost. There are two main methods that hackers use to get viruses onto torrent seekers and users devices:
Malvertisements
Malvertisements are advertisement banners or other forms of ads that spread viruses into users devices either by a user clicking the add or in rare cases even viewing the add in the browser. Malvertisements can be found in any ad program however, because torrenting sites like The Pirate Bay usually does not screen their advertisers these infected ads are far more prominent on their site. In May of 2016 a massive virus called "The Cerber Virus" was released on The Pirate Bay in the form of a Malvertisement and resulted in millions of dollars being stolen from users. According to ZDNet, malvertisements infect 12 million computers every month [14].
Torrent Downloads
In addition to malicious advertisements, hackers can also embed viruses in the torrents that are being downloaded off of these sites. The most commonly used pieces of software that hackers use are "Crackers" or "KeyGens". Common steps to ensure you do not download an infected torrent is to check the release group, check the file format, and check the comments section. [14]
See Also
External Links
References
- ↑ "A History of BitTorrent on Mozy.com"Mozy: A History of BitTorrent
- ↑ "Utorrent Beginner's Guide on Seeding"uTorrent: Beginner's Guide
- ↑ 3.0 3.1 3.2 http://www.rfrost.people.si.umich.edu/courses/SI110/slides/bayu_si110.pdf
- ↑ 4.0 4.1 Torrent Freak: BitTorrent Throttling Internet Providers Exposed
- ↑ TechDirt.com | Article on Legal Issues of BitTorrent" Yes, There Are Many, Many, Many, Many Legal Uses Of BitTorrent
- ↑ "Article on Breaking BitTorrent Lawsuit"Torrent Freak: Record-Breaking BitTorrent Lawsuit Decimated
- ↑ "Top 10 Most Pirated Movie on BitTorrent"Torrent Freak: Top 10 Most Pirated Movies of All Time
- ↑ 8.0 8.1 TechCrunch: YouHaveDownloaded.com Knows What You (And Google, And Sony, And…) Have DownloadedTechCrunch: YouHaveDownloaded.com Knows What You (And Google, And Sony, And…) Have Downloaded
- ↑ "The Verge Article on French President Scandal regarding BitTorrent"The Verge: French President Sarkozy's residence implicated in torrenting scandal
- ↑ Geek: French president Nicolas Sarkozy has broken his own three-strikes piracy rules
- ↑ The Washington Post: Stop Online Piracy Act (SOPA) sparks backlash from Facebook, Google
- ↑ Tech.Blorge: Government study proves illegal file sharing increases music sales
- ↑ 13.0 13.1 13.2 Snapper, John. The Matter of Plagarism: What, Why, and If? in The Handbook of Information and Computer Ethics. Himma, K. and Tavani, H., eds. Hoboken, NJ: Wiley-Interscience. 2008.
- ↑ 14.0 14.1 Can You Get a Virus From Downloading Torrents? Everything You Need to Know Can You Get a Virus From Downloading Torrents? Everything You Need to Know
| ←Back • ↑Top of Page |