Behavioral biometrics
Behavioral Biometrics refers to the study of measuring analyzing patterns in human activity to identify individuals with an exceedingly high degree of accuracy. Patterns include keystroke, speech, gait, signature and cognition, helping capture an array of human interactions between a device and an application. By measuring how consumers hold phones, swipe screens, use keyboard or gestural shortcuts, software algorithms build a unique user profile, which is then used to confirm an individual’s identity. [1] Behavioral biometrics has several advantages including increased data security, easy user accessibility, decreased susceptibility to frauds and high identification accuracy resulting in its widespread use across different industries.
Behavioral biometrics is currently used on several platforms including online banking, e-commerce, and high-security authentication. [2] Behavioral Biometrics' effective features of Continuous Authentication and Risk-based Authentication help create an additional and continuous layer of identity assurance and security. As a result, banks are moving towards applications where users can pay with a glance, companies are incorporating identification systems for classified areas only open to cleared personnel and voting centers are adopting biometrics as a means to prevent proxy voting. As greater number of applications progress to the online space, there is higher consumer demand for the ability of functions in their digital worlds to match their physical worlds, resulting in biometrics growing popularity. However, behavioral biometrics faces several ethical challenges with regards to storage issues, vulnerability to hackers or malicious third parties and lack of stringent regulation, which exposes users to data infringement and fraud. Although behavioral biometrics provides numerous benefits, measures should be taken to increase the security and privacy of biometric data. [3]
Contents
History
The initial use of behavioral biometrics to measure patterns in human activity dates back to the 1860s with the invention of the telegraph. In World War II, allied forces would use the telegraph to verify legitimacy of messaged received by testing the method of transmission. In the 1960s, the advent of computers allowed for the first model of acoustic speech production followed by the earliest signature recognition system. Today, behavioral biometrics extends beyond signature, voice and speech, as modern systems are able to identify an array of data and end-point interactions. [4]
Types of Biometric Identifiers
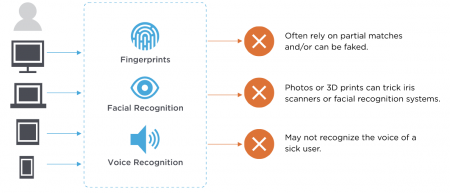
Biometric identifiers are the distinctive, measurable characteristics used to label and describe individuals and are often categorized as physiological versus behavioral characteristics. Physiological characteristics are related to the shape of the body, some of the most common include: voice recognition, facial recognition, fingerprinting and iris scanning. There are advantages and disadvantages to each type, depending on the specific purpose of biodata for a company, app, government, etc. Fingerprinting is easiest to install and has a reliable accuracy as a non-invasive feature while facial recognition provides ease of interaction but can more subjective and hence, sometimes inaccurate. Similarly, voice recognition provides simple user interaction but can be imprecise due to maturity or illness. Iris scanning is the process of using visible and near-infrared light to take a high-contrast photograph of a person's retina, analyzing the patterns found in the picture then turning them into code. Iris scanning is the most futuristic form of biodata and very accurate as the iris is resistant to change and therefore, best for longevity. [5] On the other hand, behavioral characteristics are related to the pattern of behavior of a person, including but not limited to typing rhythm, gait, and voice. [6]
Mechanics behind Behavioral Biometrics
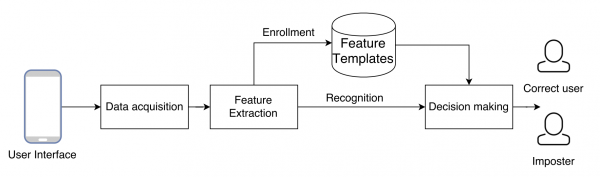
Though computer algorithms for biometric technology are complex, the base process is relatively straightforward, as laid out by the following steps: [7]
- Data acquisition module – an individual’s raw unique biodata (face scan or fingerprint) is collected through a sensor and stored alongside information such as name or identification (ID) number.
- Rescanning – once an individual is placed in the system and they try to access the locked application, they must rescan the feature.
- Feature templates – the computer algorithm performs a one-to-one comparison of the captured scan sample and the previously stored data.
- Identification – the system performs several comparisons with the extracted data and feature templates existing in the data base to find a match. The result then validates the claimed identity, hence unlocking or restricting access to the task.
Recent developments in advanced technology such as deep learning enable the process to become more user-specific, allowing artificial intelligence to identify and model aspects of a user’s behavior that are most unique. This leads to better differentiation between users resulting in better performance of the overall system.[8]
Use cases and benefits
Continuous Authentication
The nature of data capture in behavioral biometrics ensures persistent or continuous authentication. In comparison, legacy authentication, referring to protocols using basic one-step authentication, only verified user’s identity at one point of time and not thereafter. Continuous authentication provides assurance of an individual’s identity at all times, thereby fulfilling a crucial gap in many current security systems. Continuous authentication provides a layered security system through PINs, card access, two-factor authorization, and periodic forced password changes. [9]
Risk-based Authentication
Behavioral biometrics is key in increasing risk-based authentication particularly in web-based transactions and mobile platforms. Risk-based authentication ensures the data retrieved is analyzed in conjunction with other relevant authentication methods. For example, when a smartphone user accesses a banking application through username and password information, authentication mechanisms also investigate:
- Behavioral qualities of the data (typing speed, touchscreen interactions etc.)
- Supporting contextual factors (IP address, geolocation etc.)
- Historical behavioral factors (typical timing of user access, prior access patterns etc.)
The combination of these factors ensures the individual accessing the platform is an authorized user. Hence, behavioral biometrics provides several tiers to existing ID techniques to ensure maximal certainty for identity decisions.
Behavioral biometrics technology offers robust anti-fraud measures to protect users against violations by providing a holistic picture of a biometric identifier. The system’s flexibility, convenience, efficiency and security allow for identity verification and protection without interrupting user’s experience. [10]
Privacy concerns and ethical implications
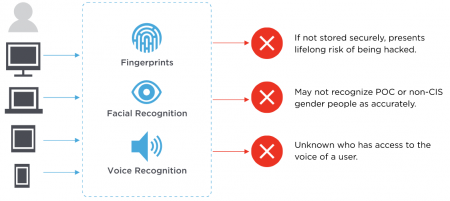
The convenience of unlocking your phone with facial recognition or purchasing an app with the double-click of your finger is undeniable. One of the biggest benefits of biometric signatures is that it is unique to each individual and cannot be altered over time. Ironically, the unchangeable nature of the system is also one of behavioral biometrics’ biggest vulnerabilities because if a user’s biometric data has been breached, it is comprised forever.
Privacy implies that users are predominately in control over how and when they are represented to others. However, behavioral biometrics infringes on that fundamental principal as users do not have control over the collection, storage or use of their identity. Hence, though field of behavioral biometrics exemplifies numerous benefits, it also faces several outstanding ethics and privacy questions and concerns. [11]
Storage
Secure data storage is vital for behavioral biometrics given the level of personal and unique information collected from each individual. The hacks of Chipotle and LinkedIn highlight that despite high-level secure measures taken to protect user’s information, data breaches can occur. Despite the security of the system, biometrics sensors can be deceived, making readings inaccurate. For example, DeepMasterPrint, created by machine learning technique, highlighted that it is possible to exploit biometrics’ systems by hacking cellphone fingerprints with an error rate of one in five. Since biometrics is a fast-growing form of authentication, the method of data storage is essential to protect user’s privacy. [12]
Hackers and scammers adapt in response to advancements in technology. This was seen when 5.6 million people’s fingerprints were jeopardized when the Office of Personnel Management was hacked in 2015. Though companies aim to ensure the privacy of their customers, there are still susceptible to hacking. [13] Fingerprinting is a more secure more of biodata in comparison to PINs, but researchers from a mobile security firm “were able to break into Apple’s Touch ID system with a small piece of Play Doh.” [14] Experiments such as these highlight the gaping holes in behavioral biometrics that allow for large amount of data to be compromised and wrongfully be used without user consent. This is particularly dangerous because unlike PINs which can be changed, information such as fingerprints, faces, and voices, cannot be changed. Though companies use multiple forms of biometric data to confirm identity such increases the difficulty in using or accessing data, but the issue is in relation to secure storage to prevent misuse. Companies have an ethical obligation to their users to protect their data, but many companies are setting this aside in favor of technological innovation.
Exposure to third parties
The storage of large amounts of data in databases makes biodata more exposed to access by malicious third parties. An example of this is the Aadhaar card in India, one of the world’s largest biometric databases consisting of 1.2 billion enrollments. The system is a 12-digit unique identity number issued to all citizens, requiring the collection of citizens’ fingerprints, retina scans as well as their face photos. Originally, it was originally meant to be an optional program for citizens, but it is now a standard in order to receive school meals or open bank accounts, making its participation a mandatory function in society. Several non-governmental agencies were able to access the database for purposes without user’s consent. [15] Though its use as a substitute for photo-ID is beneficial, it introduces several dangers including threat to privacy, unethical use of data for AI software development and potential to turn the system into oppressive surveillance. Hence, behavioral biometrics allows for the unauthorized use of personal data that can be manipulated and used for private purposes. [16]
Expanding on the unauthorized use of data, an individual’s biometric data can be wrongfully manipulated for private motives. This is seen in examples of target advertising where companies use characteristics such as age and gender, which can be automatically detected by a face or voice recognition software and send advertising material for specific products and services to select individuals. This also opens scope for increased biases as algorithmic content can provide people with skewed information about different subjects. [17] Private organizations having the ability to use biometric data to manipulate individuals is ethically contentious.
Regulation
As behavioral biometrics is a novel technology that is rapidly growing across several industries, the government is struggling to enforce regulation, which comprises user’s security. There are regulations specifying how biometric data can be recorded but limited laws surrounding its storage and protection. Furthermore, there is lack of clarity of what falls under biometrics and if all forms of biometric data should be evaluated the same. An analysis of the European Union (EU) regulations found that it is imperative to have a well-defined distinction between various types of biometric data. However, the EU regulations fail to provide transparent rules and protection for the fundamental rights of privacy when it comes to biometric data. Legally, it is generally agreed upon that different types of biodata should be treated differently than others, but governments have been unable to dictate laws that respect those distinctions.
As a result of loose regulation, technology companies are using the freedom to introduce new ethnically contentious technologies with concern of user privacy. Without clear regulation, companies and organizations are not transparent with the storage and use of biometric data. This creates many ethical concerns because biodata can be used to access bank accounts, emails, and other sensitive materials, causing further harm and danger to the user.[18]
The Future of Behavioral Biometrics
Biometrics is a rapidly growing field, and biometric systems are progressively being used in an array of settings. Biometric technology has potential to be a more efficient and secure method to confirm identity and authenticate users. However, the ethical complications of biometric technology must also be considered. The obscure methods of biodata storage, vulnerability to abuse by third parties and lack of regulation leads to greater potential for violation of user’s personal information. Behavioral biometrics delivers technological advancement in the identification and security industry but with that power comes the vital need for accountability and close ethical inspection.
See also
Artificial Intelligence and Technology
References
- ↑ Introduction to Behavioral Biometrics - Article by the International Biometrics Identity Association 2005
- ↑ Applications of Behavioral Biometrics - Article by Stacy, Cowley, New York Times 2018
- ↑ Behavioral Biometrics: Emerging Trends and Ethical Risks (March 2012)
- ↑ History of Behavioral Biometrics -1858 - 2013
- ↑ Pro/Con Analysis of Different Types of Biodata
- ↑ Different Types of Biometrics – Biometrics Institute
- ↑ Behavioral Biometric Authentication and Recognition Process
- ↑ AI in Biometrics and Security
- ↑ Continuous Authentication Using Behavioral Biometrics, article published 2013
- ↑ Online Risk-Based Authentication Using Behavioral Biometrics, published in 2013 (Springer)
- ↑ Ethical Issues in Biometrics – published by Isaac Cooper, M.S.; Jimmy Yon, M.S. in 2019 pg. 1 - 7
- ↑ Biometric Recognition: Challenges and Opportunities - Chapter 4: Cultural, Social, and Legal Considerations (2010)
- ↑ Office of Personnel Management data breach in 2015
- ↑ Touch ID gets breached by experiment using Play-Doh
- ↑ The Aadhaar Card: Cybersecurity Issues with India’s Biometric Experiment (May 2019)
- ↑ The Biometric Threat, CPO Magazine (2019)
- ↑ A Review of Continuous Authentication Using Behavioral Biometrics
- ↑ Ethical Issues in Governing Biometric Technologies by Margit Sutrop pg. 102-114