Difference between revisions of "Autonomous Systems"
m (added citations needed) |
m |
||
| Line 32: | Line 32: | ||
([[Topics|back to index]]) | ([[Topics|back to index]]) | ||
| − | [[Category: | + | [[Category:Citations Needed]] |
Revision as of 23:13, 5 December 2012
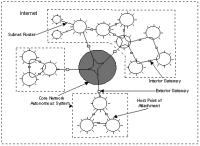
Autonomous Systems are collections of routers that deal with the same traffic and belong to the same organization. They are organized to make setting up routing tables for a group of computers easier, and provide a nice level of abstraction for routing services such as Border Gateway Protocol. Autonomous System's are assigned an Autonomous System Number from the Internet Corporation for Assigned Names and Numbers.
Contents
Background
The protocol connecting networks to make up the collective Internet is called the Border Gateway Protocol or BGP. With this protocol, comes some well known, but unsolved security vulnerabilities. [1] BGPs are made up of individual networks called autonomous systems and security vulnerabilities lie in the fact that each individual system is trusted to release accurate routing information. "These networks can operate independently, under no authority, inciting self interest and competition. The current success of the Internet and widespread adoption of BGP are evidence that this level of trust is not entirely unwarranted."[1]
Ethical Implications
Because each individual system is responsible for releasing accurate information, little mistakes that are made can have large consequences. Making a typing error when configuring a router can monopolize traffic intended for other networks. [1] People can also hijack maliciously as well. A documented example is when an autonomous system might display that it is the origin for IP addresses that it does not own, and this could spread to other networks. [1]
Additionally, another feature of the Border Gateway Protocol is the autonomous system path. The Autonomous System path is a list of autonomous systems that an update message is signified to have traveled through. It is used for detecting loops and selection routes.[1] Autonomous systems that travel along a given route add their own number to the path but leave it in place. Some routers, however, can be made to maliciously manipulate and change the path, making it invalid. [1] Invalid paths can steal multitudes of internet traffic.
Solutions to Ethical Problems
Cryptographic Protection
"Cryptographic approaches involve an authenticated registry that maps IP prefixes to their proper origin autonomous systems."[1] Global cooperation between the autonomous systems is required so that registries can be actively built and maintained, requiring the use of a public key infrastructure that secures and distributes the registry.[1] Because parts of the operational community cannot be trusted and due to some inaccuracies, the creation of registries suffer. [1]. Cryptographic solutions, however, are hard to deploy because of the need to change the Border Gateway Protocol system. [1]
Anomaly Detection
Systems have been developed that include anomaly detection algorithms. These algorithms discover origin autonomous system attacks and invalid paths by looking at the past history of valid routes.[1]. Another mechanism, called the soft-response mechanism, combines with the algorithm to slow the spread of anomalous routes so that humans can have enough time repair the invalid routes before traffic increases and is spread unnecessarily.[1] Additionally, in combination with the algorithm and mechanism, an alert system has been designed which spreads the alert notifications to multiple operators not including the local operator, because other operators are the ones who have the ability to repair an invalid route.[1]