Difference between revisions of "Internet Censorship in South Korea"
(Changed "Mechanism" section to more accurately describe HTTP and HTTPS) |
|||
| Line 8: | Line 8: | ||
=== Politics === | === Politics === | ||
Since 1948, the Republic of Korea has actively exercised the National Security Act (NSA)<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref>, which states that those who show empathy or favoritism for pro-North Korean materials can be criminally prosecuted. This is based on the fact that the government of South Korea is established under the ideology of liberalism; an ideology strongly opposed to communism, which is the fundamental basis of the North Korean government infrastructure. The 1990 Act on Exchanges and Collaboration<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref> depicts that citizens of South Korea should report to the government should they interact in any way with North Korean citizens or come in contact with materials related to them on any level. This act was passed by the government in an effort to hinder South Koreans from the spreading North Korean communist ideologies. The Information and Communications Network Act (ICNA)<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref> also acts as a barrier in the realm of the Internet by promoting website hosts to censor illegal or problematic materials as soon as they detect them. In addition, the Information and Communications Network Act (ICNA) made a significant contribution towards founding legislative bills protecting politicians, as well as effectively censoring people who produce and distribute fake information about politicians during a presidential election<ref name="ICNA">“Amendment of the ICNA and the Korean Government’s plan to expand restrictions on the use and collection of resident registration numbers” LEXOLOGY, July. 2012, https://www.lexology.com/library/detail.aspx?g=94a8ed9d-31b4-4eda-8763-3053730fa511</ref>. In cases where there is a dispute regarding whether a content online is inappropriate, legal protection is provided in court to those conforming to this law. | Since 1948, the Republic of Korea has actively exercised the National Security Act (NSA)<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref>, which states that those who show empathy or favoritism for pro-North Korean materials can be criminally prosecuted. This is based on the fact that the government of South Korea is established under the ideology of liberalism; an ideology strongly opposed to communism, which is the fundamental basis of the North Korean government infrastructure. The 1990 Act on Exchanges and Collaboration<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref> depicts that citizens of South Korea should report to the government should they interact in any way with North Korean citizens or come in contact with materials related to them on any level. This act was passed by the government in an effort to hinder South Koreans from the spreading North Korean communist ideologies. The Information and Communications Network Act (ICNA)<ref name="political censorship">“Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship</ref> also acts as a barrier in the realm of the Internet by promoting website hosts to censor illegal or problematic materials as soon as they detect them. In addition, the Information and Communications Network Act (ICNA) made a significant contribution towards founding legislative bills protecting politicians, as well as effectively censoring people who produce and distribute fake information about politicians during a presidential election<ref name="ICNA">“Amendment of the ICNA and the Korean Government’s plan to expand restrictions on the use and collection of resident registration numbers” LEXOLOGY, July. 2012, https://www.lexology.com/library/detail.aspx?g=94a8ed9d-31b4-4eda-8763-3053730fa511</ref>. In cases where there is a dispute regarding whether a content online is inappropriate, legal protection is provided in court to those conforming to this law. | ||
| − | |||
| − | |||
| − | |||
[[File:Woori.jpg|300px|thumb|right|Website of Woori-minjok-kkiri - North Korean Propaganda]] | [[File:Woori.jpg|300px|thumb|right|Website of Woori-minjok-kkiri - North Korean Propaganda]] | ||
| − | |||
=== Discussion about North Korean Websites === | === Discussion about North Korean Websites === | ||
South Korea actively blocks websites that are either pro-North Korean or directly hosted by the North Korean government. Since the advent of Internet technology, the North Korean government has been continuously putting an effort into propagandizing their ideology by publishing articles and announcements made in their country. As of 2004, the South Korean cybersecurity police had effectively discovered and censored 43 pro-North Korean websites. An investigation was also launched to track down IP addresses which North Korean developers were using to host propaganda websites, which found that most host servers were outside the country, with an especially high number of offending servers in Japan. Some of the websites hosted in Japan that were discovered by the South Korean cybersecurity police force include Joseon Infobank, Korea Book Center, Choseon Travel, Woori-minjok-kkiri (meaning "within our peoples"), [https://en.wikipedia.org/wiki/Sili_Bank Sili Bank], Choseon Lottery Cooperation, Jupesite, Goryeo Baduk (Baduk is Korean version of the board game checkers), Joseon Stamps, and [https://en.wikipedia.org/wiki/Choson_Sinbo Joseon Sinbo], Joseon Tongsin (Tongsin meaning correspondence), and Gukjeonseon (meaning channels between nations). Servers found in other foreign countries include Unification Arirang in China, Minjok Tongsin in the United States, and Korea Network<ref name="North Korean Websites Based In Japan">“Police Announce 43 Active Pro-North Korean Websites” THE DONG-A ILBO, 8 September. 2004, http://english.donga.com/List/3/all/26/237073/1</ref>. | South Korea actively blocks websites that are either pro-North Korean or directly hosted by the North Korean government. Since the advent of Internet technology, the North Korean government has been continuously putting an effort into propagandizing their ideology by publishing articles and announcements made in their country. As of 2004, the South Korean cybersecurity police had effectively discovered and censored 43 pro-North Korean websites. An investigation was also launched to track down IP addresses which North Korean developers were using to host propaganda websites, which found that most host servers were outside the country, with an especially high number of offending servers in Japan. Some of the websites hosted in Japan that were discovered by the South Korean cybersecurity police force include Joseon Infobank, Korea Book Center, Choseon Travel, Woori-minjok-kkiri (meaning "within our peoples"), [https://en.wikipedia.org/wiki/Sili_Bank Sili Bank], Choseon Lottery Cooperation, Jupesite, Goryeo Baduk (Baduk is Korean version of the board game checkers), Joseon Stamps, and [https://en.wikipedia.org/wiki/Choson_Sinbo Joseon Sinbo], Joseon Tongsin (Tongsin meaning correspondence), and Gukjeonseon (meaning channels between nations). Servers found in other foreign countries include Unification Arirang in China, Minjok Tongsin in the United States, and Korea Network<ref name="North Korean Websites Based In Japan">“Police Announce 43 Active Pro-North Korean Websites” THE DONG-A ILBO, 8 September. 2004, http://english.donga.com/List/3/all/26/237073/1</ref>. | ||
| − | |||
=== Pornography === | === Pornography === | ||
| Line 32: | Line 27: | ||
=== Mechanism === | === Mechanism === | ||
| − | SNI filtering (Server Name Indication)<ref name="SNI">“Server Name Indication” https://en.wikipedia.org/wiki/Server_Name_Indication</ref> is a new technology that is based on tracking | + | SNI filtering (Server Name Indication)<ref name="SNI">“Server Name Indication” https://en.wikipedia.org/wiki/Server_Name_Indication</ref> is a new technology that is based on tracking HTTPS websites. 10 years ago, website addresses all started with "http://", where HTTP stands for Hypertext Transfer Protocol<ref name="SNI opinion">“Is South Korea Sliding Toward Digital Dictatorship?” Forbes, 25 Feb. 2012, https://www.forbes.com/sites/davidvolodzko/2019/02/25/is-south-korea-sliding-toward-digital-dictatorship/#abab472648e2</ref>. Hypertext Transfer Protocol precedes the actual presentation of the assigned webpage, acting as a [https://en.wikipedia.org/wiki/Request%E2%80%93response request-response] protocol. Essentially, the user, also known as the client, send an HTTP request to a server, and the server sends a response to the request by providing the client with files needed to load the website, such as [https://en.wikipedia.org/wiki/HTML HTML] files, [https://en.wikipedia.org/wiki/Cascading_Style_Sheets CSS] files, and others. HTTP was developed with the purpose of leaving leeway for intermediate network agents between the client and the server to improve or enable the connection. It is this characteristic about HTTP that enables SNI filtering. |
| − | + | ||
| + | As numerous activities became available on the Internet, professionals felt the necessity to effectively secure sensitive data such as credit card numbers, social security numbers, and personal data. Out of this necessity, HTTPS was developed, where the extra S stands for "Secured", Using HTTPS, all sensitive data within the files being sent over the network is encrypted and sent over the Secure Sockets Layer (SSL), providing an added layer of security that does not improve someone's ability to eavesdrop on the communication but makes it incredibly difficult to actually understand the content<ref>“HTTPS Tutorials.” InstantSSL®, www.instantssl.com/https-tutorials-ssl-certificates.</ref>. In accordance context of this system, SNI filtering works by allowing connections only to servers that are enrolled in a certificate issued by the government, effectively filtering out websites that are not whitelisted by the government. | ||
=== Technical Challenge === | === Technical Challenge === | ||
Although Server Name Indication technology seems like a beauty overall, considering its power in ensuring cyber-security, there still is a challenge for Server Name Indication faces. The SNI technology is only applicable to legacy browsers or operating systems and well-known ones among them are Google Chrome, Firefox, Mozilla, Safari, which most of the people use in the world in their daily lives. This, however, means that those who do not use these type of legacy browsers are incompatible with this technology and are vulnerable to highly developed cyber attacks. Common non-legacy browsers currently used are Internet Explorer (a.k.a. the IE) on Windows XP (or older), Android 2.3 version or older. It is known these browsers may result in a cyber-fallacy during the certifying process, known as the handshaking, and end up with a common name mismatch error. A solution for this issue is to use a multi-domain TLS as a default certificate in order to avoid the name mismatch error since it lists all the domains when the IP addresses are shared <ref name="SNI challenge">“What is Server Name Indication (SNI)?” Globalsign, 1 June. 2018, https://www.globalsign.com/en/blog/what-is-server-name-indication/</ref>. | Although Server Name Indication technology seems like a beauty overall, considering its power in ensuring cyber-security, there still is a challenge for Server Name Indication faces. The SNI technology is only applicable to legacy browsers or operating systems and well-known ones among them are Google Chrome, Firefox, Mozilla, Safari, which most of the people use in the world in their daily lives. This, however, means that those who do not use these type of legacy browsers are incompatible with this technology and are vulnerable to highly developed cyber attacks. Common non-legacy browsers currently used are Internet Explorer (a.k.a. the IE) on Windows XP (or older), Android 2.3 version or older. It is known these browsers may result in a cyber-fallacy during the certifying process, known as the handshaking, and end up with a common name mismatch error. A solution for this issue is to use a multi-domain TLS as a default certificate in order to avoid the name mismatch error since it lists all the domains when the IP addresses are shared <ref name="SNI challenge">“What is Server Name Indication (SNI)?” Globalsign, 1 June. 2018, https://www.globalsign.com/en/blog/what-is-server-name-indication/</ref>. | ||
| − | |||
| − | |||
== Ethical Issues == | == Ethical Issues == | ||
| − | |||
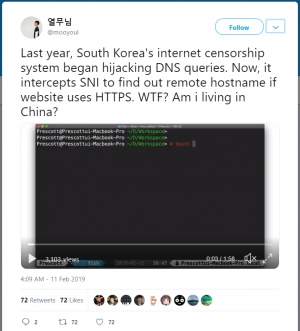
[[File:Twitterpic123.png|300px|thumb|right|Concerns about no privacy]] | [[File:Twitterpic123.png|300px|thumb|right|Concerns about no privacy]] | ||
| − | |||
| − | |||
=== Surveillance and Voyeurism by government === | === Surveillance and Voyeurism by government === | ||
| − | Newly adopted technology in South Korea - Server Name Indication filtering - is apparently hosted and conducted by the South Korean government. Users in South Korea will inevitably be restricted their range of freedom whether it is politics or pornography. But the technology itself has a backdoor which allows the host, or to make it more easy to understand, the boss to gain access to sensitive information. The host is able to read 1) where the protocol was made and 2) where the protocol is headed to. The location of where the protocol is headed to means, what users are looking up for. This technically infers continuous surveillance, and in this case, the South Korean government is the one who is watching all of the users. On top of that, there is no way for the general public to figure out whether your searching history is being kept eyes on or might not even know that they are actually being watched until they learn this information. From a wider point of view, it can be | + | Newly adopted technology in South Korea - Server Name Indication filtering - is apparently hosted and conducted by the South Korean government. Users in South Korea will inevitably be restricted their range of freedom whether it is politics or pornography. But the technology itself has a backdoor which allows the host, or to make it more easy to understand, the boss to gain access to sensitive information. The host is able to read 1) where the protocol was made and 2) where the protocol is headed to. The location of where the protocol is headed to means, what users are looking up for. This technically infers continuous surveillance, and in this case, the South Korean government is the one who is watching all of the users. On top of that, there is no way for the general public to figure out whether your searching history is being kept eyes on or might not even know that they are actually being watched until they learn this information. From a wider point of view, it can be perfect surveillance which completely counters cyber ethics. The Internet environment was known to be a free space with anonymity, privacy, and no surveillance but with this new censorship policy, users are in stake of turning into a bunch of fish in a fishbowl kept in guard. There is not a problem and no one really puts attention to fish that 'behave' in the fishbowl, but once it makes 'trouble', the boss outside immediately catches them - the bowl is ''transparent''. The same thing is applied to SNI technology in South Korea - users will not know until the voyeur gains intention and acts upon them <ref> Doyle, T., 2009. Privacy and Perfect Voyeurism. ''Ethics Inf Technol'', ''11'', 181–189</ref>. As Doyle argued, perfect voyeurism cannot be justified in any case even though there was no bad voyeur's preference or ''intentional'' spying on the victim because the voyeur is already violating the victim's right to privacy which is intrinsically wrong. |
=== Invasion of privacy === | === Invasion of privacy === | ||
SNI filtering technology was meant to be programmed in such a way that it only polices inappropriate websites. But the problem with using SNI filtering technology is that it gives too much authority to the person who is in control. The essence of this technology is that the programmer can obtain information about what kind of information users are trying to reach out to<ref name="privacy problems">“South Korea Expands Site Blocking Efforts with SNI Eavesdropping” TorrentFreak, 14 Feb. 2019, https://torrentfreak.com/south-korea-expands-site-blocking-efforts-with-sni-eavesdropping-190214/</ref>. The technology does not precisely track down every single step of access, but it does give data about keywords that were browsed or at least attempted to be used<ref name="SNI traffic">“South Korea is Censoring the Internet by Snooping on SNI Traffic” BleepingComputer, 13 Feb. 2019, https://www.bleepingcomputer.com/news/security/south-korea-is-censoring-the-internet-by-snooping-on-sni-traffic/</ref>. The Korean government acknowledged the concerns that professionals raised and announced that they will not be used in such a way where every single person is censored of what they are doing. People in South Korea are very concerned they will lose their freedom of expression, which seemed to be well preserved for at least the last 20 years, and show the anxiety of being watched all the time by the government. One citizen illustrated this situation as a disaster by comparing to the People's Republic of China, where the government actively censors materials that are posted on the Internet and banning global search engines such as Google and Youtube. | SNI filtering technology was meant to be programmed in such a way that it only polices inappropriate websites. But the problem with using SNI filtering technology is that it gives too much authority to the person who is in control. The essence of this technology is that the programmer can obtain information about what kind of information users are trying to reach out to<ref name="privacy problems">“South Korea Expands Site Blocking Efforts with SNI Eavesdropping” TorrentFreak, 14 Feb. 2019, https://torrentfreak.com/south-korea-expands-site-blocking-efforts-with-sni-eavesdropping-190214/</ref>. The technology does not precisely track down every single step of access, but it does give data about keywords that were browsed or at least attempted to be used<ref name="SNI traffic">“South Korea is Censoring the Internet by Snooping on SNI Traffic” BleepingComputer, 13 Feb. 2019, https://www.bleepingcomputer.com/news/security/south-korea-is-censoring-the-internet-by-snooping-on-sni-traffic/</ref>. The Korean government acknowledged the concerns that professionals raised and announced that they will not be used in such a way where every single person is censored of what they are doing. People in South Korea are very concerned they will lose their freedom of expression, which seemed to be well preserved for at least the last 20 years, and show the anxiety of being watched all the time by the government. One citizen illustrated this situation as a disaster by comparing to the People's Republic of China, where the government actively censors materials that are posted on the Internet and banning global search engines such as Google and Youtube. | ||
| − | |||
| − | |||
== See Also For Comparison and Reference == | == See Also For Comparison and Reference == | ||
Revision as of 08:11, 16 April 2019
Internet Censorship in South Korea is fairly restrictive since it censors any type of pro-North Korean material online and actively regulates the production/distribution of pornography. Due to these reasons, South Korea's (Republic of Korea) unique traits can be seen represented in its Internet environment. While freedom of expression online is guaranteed in South Korea, like many other developed countries in the world, certain aspects are still considered to be conservative or oppressed. There is a clear contradiction between democratic values of the country and level of government censorship [1].
As of 2012, the OpenNet Initiative has ranked South Korea's internet censorship in the sector of security/conflict as "pervasive filtering" due to the censorship of pro-North Korean content. In terms of social content, the level of filtering was deemed "selective, and in the sector of political and internet tools, no evidence of filtering was found. Other factors, such as transparency and consistency, were ranked as "high"[2].
Contents
Basic censorship
Politics
Since 1948, the Republic of Korea has actively exercised the National Security Act (NSA)[3], which states that those who show empathy or favoritism for pro-North Korean materials can be criminally prosecuted. This is based on the fact that the government of South Korea is established under the ideology of liberalism; an ideology strongly opposed to communism, which is the fundamental basis of the North Korean government infrastructure. The 1990 Act on Exchanges and Collaboration[3] depicts that citizens of South Korea should report to the government should they interact in any way with North Korean citizens or come in contact with materials related to them on any level. This act was passed by the government in an effort to hinder South Koreans from the spreading North Korean communist ideologies. The Information and Communications Network Act (ICNA)[3] also acts as a barrier in the realm of the Internet by promoting website hosts to censor illegal or problematic materials as soon as they detect them. In addition, the Information and Communications Network Act (ICNA) made a significant contribution towards founding legislative bills protecting politicians, as well as effectively censoring people who produce and distribute fake information about politicians during a presidential election[4]. In cases where there is a dispute regarding whether a content online is inappropriate, legal protection is provided in court to those conforming to this law.
Discussion about North Korean Websites
South Korea actively blocks websites that are either pro-North Korean or directly hosted by the North Korean government. Since the advent of Internet technology, the North Korean government has been continuously putting an effort into propagandizing their ideology by publishing articles and announcements made in their country. As of 2004, the South Korean cybersecurity police had effectively discovered and censored 43 pro-North Korean websites. An investigation was also launched to track down IP addresses which North Korean developers were using to host propaganda websites, which found that most host servers were outside the country, with an especially high number of offending servers in Japan. Some of the websites hosted in Japan that were discovered by the South Korean cybersecurity police force include Joseon Infobank, Korea Book Center, Choseon Travel, Woori-minjok-kkiri (meaning "within our peoples"), Sili Bank, Choseon Lottery Cooperation, Jupesite, Goryeo Baduk (Baduk is Korean version of the board game checkers), Joseon Stamps, and Joseon Sinbo, Joseon Tongsin (Tongsin meaning correspondence), and Gukjeonseon (meaning channels between nations). Servers found in other foreign countries include Unification Arirang in China, Minjok Tongsin in the United States, and Korea Network[5].
Pornography
South Korea actively censors pornography and has been since the early 1980s when political censorship began to pick up speed. Prior to the ubiquitination of Internet technology, the South Korean government enthusiastically censored materials containing pornography by confiscating seditious books or banning adult video production. In modern times, regulations have changed to banning websites containing keywords that the government has set, including "porn", "child porn", "gay", and "lesbian"[6]. Since the early 2000s, the South Korean government has adopted a method of pornography censorship utilizing the tracking of HTTP host servers. Upon detecting pornography or other inappropriate content on a website, the information about the host server is quickly forwarded to the cybersecurity police through HTTP filtering.
The South Korean government also exercises an age verification system in search engines, which is triggered upon searching a keyword that is blacklisted as inappropriate for minors. In order to view mature content, Internet users in South Korea must enter their national identity number verifying their age, whereas non-citizens must enter passport information[7].
Korea Communications Commission
The Korea Communications Commission (KCC), was created in February of 2008 and works to regulate all media in Korea. Around this time, the Korea Communications Standards Commission (KCSC), replaced the Information and Communication Ethics Committee. The KCSC works within the KCC to regulate specifically the Internet. The KCC and the KCSC work closely together as the KCC identifies and monitors inappropriate content and the KCSC consequently takes it down. The Korean Internet Self-Governance Organization, KISO is another organization involved in media monitoring and censorship. While the KISO is not run by the government, it still works closely with the KCC and KCSC, collectively using a method coined "Real Name Verification" to coerce Internet users to give up a certain amount of personal information in order to be able to post information online. The KISO works specifically with the largest Internet providers in Korea - Naver, DaumKakao, SK Communications, and KT [1].
A noteworthy rule that the KCSC implemented is the requirement of citizens of South Korea to enter their identification number issued by the government in order to post political comments online. Following this, the KSCS was barraged with heavy criticism from citizens, who argued the unethicality of having their social media networks and personal mobile apps monitored.
SNI filtering
Recently, in February 2019, the Korean government announced that they will reinforce their Internet censorship by adopting a new technology called SNI filtering. This act was passed with the intent to enhance cyber network security levels by censoring materials classified as 'inappropriate' and protect citizens from fraud or hacking.
Mechanism
SNI filtering (Server Name Indication)[8] is a new technology that is based on tracking HTTPS websites. 10 years ago, website addresses all started with "http://", where HTTP stands for Hypertext Transfer Protocol[9]. Hypertext Transfer Protocol precedes the actual presentation of the assigned webpage, acting as a request-response protocol. Essentially, the user, also known as the client, send an HTTP request to a server, and the server sends a response to the request by providing the client with files needed to load the website, such as HTML files, CSS files, and others. HTTP was developed with the purpose of leaving leeway for intermediate network agents between the client and the server to improve or enable the connection. It is this characteristic about HTTP that enables SNI filtering.
As numerous activities became available on the Internet, professionals felt the necessity to effectively secure sensitive data such as credit card numbers, social security numbers, and personal data. Out of this necessity, HTTPS was developed, where the extra S stands for "Secured", Using HTTPS, all sensitive data within the files being sent over the network is encrypted and sent over the Secure Sockets Layer (SSL), providing an added layer of security that does not improve someone's ability to eavesdrop on the communication but makes it incredibly difficult to actually understand the content[10]. In accordance context of this system, SNI filtering works by allowing connections only to servers that are enrolled in a certificate issued by the government, effectively filtering out websites that are not whitelisted by the government.
Technical Challenge
Although Server Name Indication technology seems like a beauty overall, considering its power in ensuring cyber-security, there still is a challenge for Server Name Indication faces. The SNI technology is only applicable to legacy browsers or operating systems and well-known ones among them are Google Chrome, Firefox, Mozilla, Safari, which most of the people use in the world in their daily lives. This, however, means that those who do not use these type of legacy browsers are incompatible with this technology and are vulnerable to highly developed cyber attacks. Common non-legacy browsers currently used are Internet Explorer (a.k.a. the IE) on Windows XP (or older), Android 2.3 version or older. It is known these browsers may result in a cyber-fallacy during the certifying process, known as the handshaking, and end up with a common name mismatch error. A solution for this issue is to use a multi-domain TLS as a default certificate in order to avoid the name mismatch error since it lists all the domains when the IP addresses are shared [11].
Ethical Issues
Surveillance and Voyeurism by government
Newly adopted technology in South Korea - Server Name Indication filtering - is apparently hosted and conducted by the South Korean government. Users in South Korea will inevitably be restricted their range of freedom whether it is politics or pornography. But the technology itself has a backdoor which allows the host, or to make it more easy to understand, the boss to gain access to sensitive information. The host is able to read 1) where the protocol was made and 2) where the protocol is headed to. The location of where the protocol is headed to means, what users are looking up for. This technically infers continuous surveillance, and in this case, the South Korean government is the one who is watching all of the users. On top of that, there is no way for the general public to figure out whether your searching history is being kept eyes on or might not even know that they are actually being watched until they learn this information. From a wider point of view, it can be perfect surveillance which completely counters cyber ethics. The Internet environment was known to be a free space with anonymity, privacy, and no surveillance but with this new censorship policy, users are in stake of turning into a bunch of fish in a fishbowl kept in guard. There is not a problem and no one really puts attention to fish that 'behave' in the fishbowl, but once it makes 'trouble', the boss outside immediately catches them - the bowl is transparent. The same thing is applied to SNI technology in South Korea - users will not know until the voyeur gains intention and acts upon them [12]. As Doyle argued, perfect voyeurism cannot be justified in any case even though there was no bad voyeur's preference or intentional spying on the victim because the voyeur is already violating the victim's right to privacy which is intrinsically wrong.
Invasion of privacy
SNI filtering technology was meant to be programmed in such a way that it only polices inappropriate websites. But the problem with using SNI filtering technology is that it gives too much authority to the person who is in control. The essence of this technology is that the programmer can obtain information about what kind of information users are trying to reach out to[13]. The technology does not precisely track down every single step of access, but it does give data about keywords that were browsed or at least attempted to be used[14]. The Korean government acknowledged the concerns that professionals raised and announced that they will not be used in such a way where every single person is censored of what they are doing. People in South Korea are very concerned they will lose their freedom of expression, which seemed to be well preserved for at least the last 20 years, and show the anxiety of being watched all the time by the government. One citizen illustrated this situation as a disaster by comparing to the People's Republic of China, where the government actively censors materials that are posted on the Internet and banning global search engines such as Google and Youtube.
See Also For Comparison and Reference
References
- ↑ 1.0 1.1 “South Korea and Internet Censorship” University of Washington, November. 2017, https://jsis.washington.edu/news/south-korea-internet-censorship/
- ↑ “South Korea.” South Korea | OpenNet Initiative, opennet.net/research/profiles/south-korea.
- ↑ 3.0 3.1 3.2 “Internet Laws: South Korea” lawless.tech, 15 Nov. 2018, https://lawless.tech/internet-laws-south-korea/ Political Censorship
- ↑ “Amendment of the ICNA and the Korean Government’s plan to expand restrictions on the use and collection of resident registration numbers” LEXOLOGY, July. 2012, https://www.lexology.com/library/detail.aspx?g=94a8ed9d-31b4-4eda-8763-3053730fa511
- ↑ “Police Announce 43 Active Pro-North Korean Websites” THE DONG-A ILBO, 8 September. 2004, http://english.donga.com/List/3/all/26/237073/1
- ↑ “South Korea crusades against online pornography” LEXOLOGY, July. 2012, https://www.usatoday.com/story/news/world/2012/12/10/south-korea-porn/1758277/
- ↑ Schwartz, Barry., "Searching For An Adult Topic? You’ll Have To Prove Your Age To Google Korea" May 17, 2007
- ↑ “Server Name Indication” https://en.wikipedia.org/wiki/Server_Name_Indication
- ↑ “Is South Korea Sliding Toward Digital Dictatorship?” Forbes, 25 Feb. 2012, https://www.forbes.com/sites/davidvolodzko/2019/02/25/is-south-korea-sliding-toward-digital-dictatorship/#abab472648e2
- ↑ “HTTPS Tutorials.” InstantSSL®, www.instantssl.com/https-tutorials-ssl-certificates.
- ↑ “What is Server Name Indication (SNI)?” Globalsign, 1 June. 2018, https://www.globalsign.com/en/blog/what-is-server-name-indication/
- ↑ Doyle, T., 2009. Privacy and Perfect Voyeurism. Ethics Inf Technol, 11, 181–189
- ↑ “South Korea Expands Site Blocking Efforts with SNI Eavesdropping” TorrentFreak, 14 Feb. 2019, https://torrentfreak.com/south-korea-expands-site-blocking-efforts-with-sni-eavesdropping-190214/
- ↑ “South Korea is Censoring the Internet by Snooping on SNI Traffic” BleepingComputer, 13 Feb. 2019, https://www.bleepingcomputer.com/news/security/south-korea-is-censoring-the-internet-by-snooping-on-sni-traffic/