Difference between revisions of "Virtual Private Network"
(→Access Remote Sites) |
(stylistic changes) |
||
| (110 intermediate revisions by 8 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | A [https://en.wikipedia.org/wiki/Virtual_private_network virtual private network] (VPN) is a service that protects a user's online privacy and anonymity by creating a private network from a public internet connection. VPNs mask a user's internet protocol (IP) address, making their online activities virtually untraceable. Moreover, VPN services establish secure and encrypted connections to provide greater privacy than even a secured Wi-Fi hotspot. <ref name="Norton">[https://us.norton.com/internetsecurity-privacy-what-is-a-vpn.html Symanovich, Steve. "What is a VPN?" <i>Norton</i>, 14 Jan. 2021, us.norton.com/internetsecurity-privacy-what-is-a-vpn.html. Accessed 8 Apr. 2021.]</ref> VPNs are classified into three main categories: remote access, intranet-based site-to-site, and extranet-based site-to-site. Aside from the various types of VPNs, it also includes a number of other services and features such as VPN protocols, security features, auto-connect settings, and real-time chat support. <ref>[https://www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/ Greenberg, Ran. "Different Types of VPNs and When to Use Them" <i>VPNMentor</i>, 15 Apr. 2021, https://www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/ Accessed 19 Apr. 2021.]</ref> As the use of VPNs grows in popularity, so do ethical concerns about VPN users, such as piracy, security, and misleading advertisements. | |
| + | ==History== | ||
| + | Gurdeep Pall, a Microsoft software developer, created the first VPN in 1996. It was designed as an efficient way for employees to securely access company data from remote locations, and it was built on the Point-to-Point Tunneling Protocol (PPTP), a method that is still in use today. <ref>[https://www.vyprvpn.com/blog/brief-history-of-vpns "A Brief History of VPNs." vypervpn, 21 June 2016, https://www.vyprvpn.com/blog/brief-history-of-vpns. Accessed 10 April 2021.]</ref> | ||
| + | VPNs evolved from a method for employees to work from home to much broader applications over time. Transport Layer Security (TLS), or its predecessor Secure Sockets Layer (SSL) encryption is one of the most common applications today. This is a feature of the vast majority of websites on the internet, and it is frequently indicated by a lock icon in the browser's search bar and labeled "Connection Secure." | ||
| + | <ref>[https://searchsecurity.techtarget.com/definition/SSL-VPN Rosencrance, Linda. "SSL VPN (Secure Sockets Layer virtual private network)." SearchSecurity, April 2020, https://searchsecurity.techtarget.com/definition/SSL-VPN. Accessed 10 April 2021.]</ref> | ||
| − | == | + | ==Types of VPNs== |
| + | [[File:TunnelBear.png|525px|right|thumb|A screenshot from the TunnelBear homepage.<ref>[https://www.tunnelbear.com/ <i>TunnelBear</i>. www.tunnelbear.com/. Accessed 9 Apr. 2021.]</ref>]] | ||
| + | ===Site-to-Site=== | ||
| + | A Site-to-Site VPN, also called a Router-to-Router VPN, occurs when at least one user's network connects to another.<ref name="Geeks">[https://www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/ "Types of Virtual Private Network (VPN) and its Protocols." <i>Geeks for Geeks</i>, 10 Apr. 2019, www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/. Accessed 8 Apr. 2021.]</ref> According to cybersecurity company Fortinet, these types of VPNs are often found in business settings. These routers connect to essentially form one large network comprised of local networks.<ref name="Fortinet">[https://www.fortinet.com/resources/cyberglossary/what-is-site-to-site-vpn "What is a Site-to-Site VPN?" <i>Fortinet</i>, www.fortinet.com/resources/cyberglossary/what-is-site-to-site-vpn. Accessed 8 Apr. 2021.]</ref> This allows someone on one of the local connections to access information from any of the other local networks connected to the VPN. One subtype of this category is an Intranet-Based Site-to-Site VPN. Intranet-Based Site-to-Site VPNs are often used within a company when the flow of information is relatively free. That is, all networks involved in the VPN have equal access and sharing of all resources. This helps simulate the experience of everyone working on the same local network.<ref name="Fortinet"/><ref name="Geeks"/> Conversely, Extranet-Based Site-to-Site VPNs are used for more selective sharing.<ref name="Fortinet"/> <i>GeeksforGeeks</i>, a popular educational programming website, describes them as "companies [using] ... VPN ... to connect to the office of another company."<ref name="Geeks"/> | ||
| − | === | + | ===Remote Access=== |
| + | With a [[Remote Access]] VPN, rather than connecting to another router, the user connects securely to a remote network.<ref>[https://www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/ “Different Types of VPNs and When to Use Them.” <i>VPNMentor</i>, www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/. Accessed 12 Mar 2021.]</ref> By using a remote access VPN, an encrypted "tunnel" is created from the user's location to the VPN destination. This destination is determined by the creator of the private network being accessed, and some VPNs allow the user to choose their destination.<ref name="Norton"></ref> [https://en.wikipedia.org/wiki/TunnelBear TunnelBear] is an example of a VPN service where the user is able to choose where they would like to "tunnel" their data. | ||
| + | |||
| + | * Intranet-based VPN: When several offices of the same company are connected using a Site-to-Site VPN type, it is called an Intranet-based VPN. <ref name='Geeks'></ref> | ||
| + | * Extranet-based VPN: When companies use a Site-to-site VPN type to connect to the office of another company, it is called an Extranet based VPN. <ref name='Geeks'></ref> | ||
| + | |||
| + | ==Types of VPN Protocols== | ||
| + | A VPN protocol is a set of rules or instructions that will determine how your data routes between your device and the VPN server. VPN providers rely on protocols to ensure a stable and secure connection. VPN protocols have unique specifications that offer benefits to the VPN user based on the circumstances. Some specialize in privacy while others put an emphasis on speed. VPNs utilize different protocols depending on the device being used, what you want to do, and how you want to do it. <ref name='reflearnlearn'>[https://learn.g2.com/vpn-protocols Calvello, Mara. "VPN Protocols: Are You Using the Right One?" <i>Learn Hub</i>, https://learn.g2.com/vpn-protocols 28 April. 2020, Accessed 19 Apr. 2021.]</ref> | ||
| + | |||
| + | [[File:Vpn protocols.png|400px|right|thumb|An image showing the relationship between the client, VPN protocol, and the VPN.<ref name='reflearnlearn'></ref>]] | ||
| + | |||
| + | ===Internet Protocol Security (IPSec)=== | ||
| + | An IPSec is used to secure internet communication across an IP network. IPSec secures internet protocol communication by verifying the sessions and encrypts each data packet during the connection. <ref name='VPN GFG'>[https://www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/ pp_pankaj. "Types of Virtual Private Network (VPN) and its Protocols" <i>GeeksforGeeks</i>, https://www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/ 10 Apr. 2019, Accessed 19 Apr. 2021.]</ref> | ||
| + | |||
| + | ===Point-to-Point Tunneling Protocol (PPTP)=== | ||
| + | Point-to-point tunneling protocol is one of the oldest VPN protocols in existence. A PPTP generates a tunnel and confines the data packet. <ref name='VPN GFG'></ref> The point-to-point part of the protocol refers to the connection created by PPTP. It allows one point (user computer) to access another specific point (remote network) over the internet. The tunneling part of the protocol refers to the way one protocol is encapsulated within another protocol. In PPTP, the point-to-point protocol is wrapped inside the TCP/IP protocol, which provides the internet connection. <ref>[https://techterms.com/definition/pptp Christensson, P. "PPTP definition" <i>TechTerms</i>, https://techterms.com/definition/pptp 2006, Accessed 19 Apr. 2021.]</ref> | ||
| + | |||
| + | ===OpenVPN=== | ||
| + | OpenVPN is an open-source protocol that allows developers access to its underlying code. This protocol has grown in popularity due to its use of (virtually unbreakable) AES-256 bit key with 2048-bit RSA authentication and a 160-bit SHA1 hash algorithm. <ref name='refnetmotion'>[https://www.netmotionsoftware.com/blog/connectivity/vpn-protocols Harkness, Adam. "5 Common VPN protocols explained" <i>NetMotion</i>, https://www.netmotionsoftware.com/blog/connectivity/vpn-protocols 15 May. 2019, Accessed 19 Apr. 2021.]</ref> | ||
| + | |||
| + | ===Secure Socket Tunneling Protocol (SSTP)=== | ||
| + | An SSTP is a popular option due to its full integration with every Microsoft operating system since Windows Vista SP 1. It utilizes 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption. <ref name='refnetmotion'></ref> | ||
| + | |||
| + | ===Internet Key Exchange version 2 (IKEv2)=== | ||
| + | IKEv2 is a common VPN tunneling protocol that provides a secure key exchange session. Similar to L2TP, it is normally paired with IPSec for encryption and authentication. This protocol is very good at re-establishing the link after temporary connection loss and excels at switching connections across network types. <ref name='refnetmotion'></ref> | ||
| + | |||
| + | ==Uses== | ||
===Access Remote Sites=== | ===Access Remote Sites=== | ||
| − | + | Using a remote access VPN, users from across the globe can access a singular private network.<ref>[https://ieeexplore.ieee.org/abstract/document/913204 “Virtual private networks.” <i>IEEE Potentials</i>, vol. 20, no. 1, 2001, pp. 11-15, doi:10.1109/45.913204. Accessed 12 Mar. 2021.]</ref> At the University of Michigan, a VPN is used to allow students to access the University's encrypted data when not on the campus internet. This allows students to remotely access information stored at the university, such as databases, or to take advantage of network protection provided through the university.<ref>[https://its.umich.edu/enterprise/wifi-networks/vpn “Virtual Private Network (VPN).” <i>Information and Technology Services</i>, University of Michigan, its.umich.edu/enterprise/wifi-networks/vpn. Accessed 12 Mar. 2021.]</ref> Throughout the Covid-19 pandemic, companies have relied on VPNs to grant employees access to servers, internal applications, and data hosted on-site. These actions were taken to limit the exposure of sensitive data.<ref name="Cloudflare Business VPN">[https://www.cloudflare.com/learning/access-management/what-is-a-business-vpn/ “What is a business VPN?” <i>Cloudflare</i>, www.cloudflare.com/learning/access-management/what-is-a-business-vpn/. Accessed 12 Mar. 2021.]</ref><ref>[https://openvpn.net/why-companies-are-turning-to-vpns-during-the-coronavirus-outbreak/ “Why Companies Are Turning To VPNs During The Coronavirus Outbreak.” <i>OpenVPN</i>, openvpn.net/why-companies-are-turning-to-vpns-during-the-coronavirus-outbreak. Accessed 12 Mar. 2021.]</ref> | |
| + | |||
| + | [[File:Vpnvisual.jpg|400px|left|thumb|This image shows who cannot see a user's data while they are using a VPN. Note that the VPN provider is not in the image.<ref>[https://cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers “The ultimate guide to VPN encryption, protocols, and ciphers.” <i>ATT</i>, 31 July 2019, cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers. Accessed 25 Mar. 2021.]</ref>]] | ||
| + | |||
| + | ===Privacy=== | ||
| + | As a VPN [https://en.wikipedia.org/wiki/Encryption encrypts] the data between the user and the network, it can help keep a user's information private.<ref name="Cloudflare Business VPN"/> This functionality is similar to how VPNs are used to access remote sites, as they help a user access data without having to worry about the WiFi network they're connected to.<ref>[https://www.cnn.com/2020/09/17/cnn-underscored/how-to-setup-a-vpn Levin, Benjamin. “A VPN is vital when working from home, so here’s everything you need to know.” <i>CNN</i>, 17 Sept. 2020, www.cnn.com/2020/09/17/cnn-underscored/how-to-setup-a-vpn. Accessed 12 Mar. 2021.]</ref> By encrypting the information, the internet provider, government, and others who control the network face more difficulty in seeing what the user is doing on the network. Not only does this limit what data is collected about the user, but it can also decrease the number of targeted advertisements that can occur when browsing data is sold. Additionally, it can help to hide the user's location.<ref name="What is a VPN">[https://www.cloudflare.com/learning/access-management/what-is-a-vpn/ “What is a VPN.” <i>Cloudflare</i>, www.cloudflare.com/learning/access-management/what-is-a-vpn/. Accessed 12 Mar. 2021.]</ref> | ||
| + | |||
| + | ===Accessing Information From Other Countries=== | ||
| + | A VPN can also allow a user to access region-locked content or information that would otherwise be unavailable by making it appear as if they are located in a different location. | ||
| + | |||
| + | ====Circumventing Government Censorship==== | ||
| + | By disguising the [https://en.wikipedia.org/wiki/IP_address IP address] that a request comes from, a VPN can help to access sites blocked by the government in the country where the user is located. In China, [https://en.wikipedia.org/wiki/Great_Firewall "The Great Firewall"] is a name given to the country-wide censorship of the internet. By using a VPN, Chinese citizens are able to access information that would otherwise be restricted by their government.<ref>[https://www.theguardian.com/news/2018/jun/29/the-great-firewall-of-china-xi-jinpings-internet-shutdown Economy, Elizabeth C. “The great firewall of China: Xi Jinping’s internet shutdown.” <i>The Guardian</i>, 29 June 2018, www.theguardian.com/news/2018/jun/29/the-great-firewall-of-china-xi-jinpings-internet-shutdown. Accessed 12 Mar. 2021.]</ref> This has also allowed Chinese companies to conduct business with overseas partners. As new programs in China seek to control internet usage, some argue that VPNs can be useful tools to avoid these restrictions.<ref>[https://www.wsj.com/articles/chinas-vpn-crackdown-weighs-on-foreign-companies-there-1501680195 Shanghai, Liza Linin and Josh Chin. "China’s VPN Crackdown Weighs on Foreign Companies There." <i>The Wall Street Journal</i>, 2017 Aug. 2, www.wsj.com/articles/chinas-vpn-crackdown-weighs-on-foreign-companies-there-1501680195. Accessed 8 Apr. 2021.]</ref> China is not the only location where VPNs are used to access blocked content. In Kashmir, citizens use VPNs to access social media sites such as WhatsApp or Instagram that have been banned by the government.<ref>[https://www.reuters.com/article/us-india-kashmir-internet/india-cracks-down-on-use-of-vpns-in-kashmir-to-get-around-social-media-ban-idUSKBN20D0LT Bukhari, Fayaz. “India cracks down on use of VPNs in Kashmir to get around social media ban.” <i>Reuters</i>, 19 Feb. 2020, www.reuters.com/article/us-india-kashmir-internet/india-cracks-down-on-use-of-vpns-in-kashmir-to-get-around-social-media-ban-idUSKBN20D0LT. Accessed 12 Mar. 2021.]</ref> | ||
| + | |||
| + | ====Streaming Services==== | ||
| + | Another common use for a VPN is accessing streaming services that are not available in a given country. Viewers use VPNs to access the libraries of these services, primarily Netflix, by changing their virtual location to that of another country that has the desired content.<ref>[https://www.cnet.com/news/vpn-use-surges-during-the-coronavirus-lockdown-but-so-do-security-risks/ Hodge, Rae. “VPN use surges during the coronavirus lockdown, but so do security risks.” <i>CNET</i>, 23 Apr. 2020, www.cnet.com/news/vpn-use-surges-during-the-coronavirus-lockdown-but-so-do-security-risks/. Accessed 12 Mar. 2021.]</ref> For example, as of November 2020, <i>Star Trek: Discovery</i> was not available on Netflix in the US and Canada but was in other countries.<ref>[https://www.pcmag.com/how-to/how-to-unblock-netflix-with-a-vpn Eddy, Max. "How to Use a VPN to Watch Netflix From Other Countries." <i>PCMag</i>, 20 Nov. 2020, www.pcmag.com/how-to/how-to-unblock-netflix-with-a-vpn. Accessed 9 Apr. 2021.]</ref> In 2016, Netflix began taking steps to prevent the use of VPNs, though the CEO described the number of VPN users to be “really inconsequential.” <ref> [https://www.wired.com/2016/04/netflixs-ceo-says-vpn-users-really-arent-big-deal/. Greenberg, Julia. "Netflix's CEO Says VPN Users Really Aren't a Big Deal." Wired, 18 April 2020, https://www.wired.com/2016/04/netflixs-ceo-says-vpn-users-really-arent-big-deal/. Accessed 10 April 2021.]</ref> | ||
| + | They did this by comparing the location of the user's IP address (which the VPN has altered) and their [https://en.wikipedia.org/wiki/Domain_Name_System Domain Name Server (DNS)] which could still reveal the user's true location.<ref>[https://www.techradar.com/vpn/how-does-netflix-detect-and-block-vpn-use Parker, Jacob. "How does Netflix detect and block VPN use?" <i>TechRader</i>, 30 June 2020, www.techradar.com/vpn/how-does-netflix-detect-and-block-vpn-use. Accessed 9 Apr. 2021.]</ref> | ||
| + | |||
| + | Netflix’s measures have reduced the general effectiveness of VPNs, rendering many services incompatible. However, there is still a multitude of options available that still bypass the region locking of the platform [https://www.vpnmentor.com/blog/5-best-vpns-netflix-actually-work/ Hochstadt, Ariel. "8 Best Netflix VPNs That Still Work Reliably [Tested in 2021]." vpnMentor, 5 April 2021, https://www.vpnmentor.com/blog/5-best-vpns-netflix-actually-work/. Accessed 10 April 2021.]</ref> | ||
| + | |||
| + | ==The 5 Eyes, 9 Eyes, and 14 Eyes Agreements== | ||
| + | After World War II, the United States and the United Kingdom signed the BRUSA Agreement to share intelligence between the two countries. (The BRUSA Agreement is now known as the [https://en.wikipedia.org/wiki/UKUSA_Agreement UKUSA Agreement].<ref>[https://www.nsa.gov/news-features/declassified-documents/ukusa/ "UKUSA Agreement Release." <i>National Security Agency Central Security Service</i>, www.nsa.gov/news-features/declassified-documents/ukusa/. Accessed 1 Apr. 2021.]</ref> Over time, this agreement grew to include more countries, eventually leading to the 5 Eyes, 9 Eyes, and 14 Eyes agreements (each one involving a different group of countries). | ||
| + | |||
| + | The initial intent of these agreements was to gather intelligence on the Soviet Union. The member countries of the official 5 Eyes treaty included the United States, Canada, the United Kingdom, Australia, and New Zealand. In 1982, the 14 Eyes group was formed, consisting of Germany, Italy, Spain, France, Sweden, the Netherlands, Norway, Belgium, and Denmark on top of the existing members of the 5 Eyes treaty. 9 Eyes is not outlined in a specific treaty but consists of the 5 Eyes members plus Denmark, Norway, France, and the Netherlands. <ref>[https://protonvpn.com/blog/5-eyes-global-surveillance/ Koch, Richie. "What countries are in the 5 Eyes, 9 Eyes, and 14 Eyes aggreements?" ProtonVPN, 30 August 2018, https://protonvpn.com/blog/5-eyes-global-surveillance/. Accessed 10 April 2021.]</ref> | ||
| + | |||
| + | As a part of this agreement, any intelligence gained by one country is automatically shared with all other countries in the agreement.<ref name="privacy">[https://privacyinternational.org/learn/five-eyes "Five Eyes." <i>Privacy International</i>, privacyinternational.org/learn/five-eyes. Accessed 8 Apr. 2021.]</ref> Some VPN companies, such as Restore Privacy, highlight this arrangement in support of using their services. These services claim that they can help users escape government surveillance, and hence prevent information sharing between countries with the 5, 9, and 14 Eyes agreements.<ref>[https://restoreprivacy.com/5-eyes-9-eyes-14-eyes/ Taylor, Sven. "Five Eyes, Nine Eyes, 14 Eyes – Explained." <i>Restore Privacy</i>, 3 Sep. 2020, restoreprivacy.com/5-eyes-9-eyes-14-eyes/. Accessed 8 Apr. 2021.]</ref> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==Ethical Concerns== | ==Ethical Concerns== | ||
| − | ===Pirating of | + | ===Pirating of Paid Content=== |
| − | + | Since VPNs can help make a user's web access history a secret from their [https://en.wikipedia.org/wiki/Internet_service_provider Internet Service Provider (ISP)], VPNs have become popular tools for illegally obtaining copyrighted material. This has resulted in lawsuits from producers who argue that VPN companies promote and facilitate pirating.<ref>[https://www.techradar.com/news/this-top-vpn-is-being-sued-by-filmmakers Sharma, Mayank. “This top VPN is being sued by filmmakers.” <i>Future US</i>, 11 Mar 2021, www.techradar.com/news/this-top-vpn-is-being-sued-by-filmmakers. Accessed 12 Mar. 2021.]</ref> One popular method of pirating material like this is "torrenting" copyrighted material like movies, music, or video games. "Torrenting" refers to a method of [https://en.wikipedia.org/wiki/Peer-to-peer_file_sharing peer-to-peer file sharing] that uses the [https://en.wikipedia.org/wiki/BitTorrent BitTorrent] protocol. VPNs are often used in conjunction with this method because it hides the illegal file-sharing activity from Internet Service Providers.<ref>[https://www.comparitech.com/blog/vpn-privacy/is-torrenting-safe-illegal-will-you-be-caught/ Bischoff, Paul. "What is Torrenting? Is it Safe? Is it illegal? Are you likely to be caught?" <i>Comparitech</i>, 8 Apr. 2021, www.comparitech.com/blog/vpn-privacy/is-torrenting-safe-illegal-will-you-be-caught/. Accessed 9 Apr. 2021.]</ref> | |
| − | + | ||
| − | + | ||
| + | [[File:Liquid VPN Torrenting.png|thumbnail|right|Liquid VPN Advertising their service to access torrenting websites primarily used for pirating.<ref>[https://www.liquidvpn.com/popcorn-time-vpn/ “Popcorn Time VPN.” <i>LiquidVPN</i>, www.liquidvpn.com/popcorn-time-vpn/. Accessed 25 Mar 2021.]</ref>]] | ||
| + | |||
| + | ===Security of a VPN=== | ||
| + | Using a VPN does not hide the information being sent from the user, but instead shifts the ability to see the information from the user's internet service provider to the VPN provider.<ref>[https://www.youtube.com/watch?v=WVDQEoe6ZWY “This Video Is Sponsored By ███ VPN.” <i>YouTube</i>, uploaded by Tom Scott, 28 Oct 2019, www.youtube.com/watch?v=WVDQEoe6ZWY.]</ref> Some argue, however, that VPNs are not completely safe because the user is still dependent on the VPN company for their security. As an example, [https://en.wikipedia.org/wiki/NordVPN NordVPN], a leading provider, got hacked in 2019 and did not disclose the hack for several months.<ref>[https://techcrunch.com/2019/10/21/nordvpn-confirms-it-was-hacked/ Whittaker, Zack. “NordVPN confirms it was hacked.” <i>TechCrunched</i>, 21 Oct. 2019, techcrunch.com/2019/10/21/nordvpn-confirms-it-was-hacked/. Accessed 12 Mar. 2021.]</ref> | ||
| + | |||
| + | According to M.T. Khan and others, users rely on virtual private network services for a number of reasons: to preserve their privacy, circumvent censorship, and access geo-filtered content. A 2018 evaluation of sixty-two commercial VPN providers showed that while the services seem less likely to intercept or tamper with user traffic, some VPNs do leak user traffic through a variety of means. From the study, in 10% of the providers studied, between 5 and 30% of the VPNs appeared to be hosted on servers located in countries other than those advertised to users.<ref name="khan">[https://dl.acm.org/doi/abs/10.1145/3278532.3278570? Khan, M. T., et al. "An Empirical Analysis of the Commercial VPN Ecosystem." <i>In Proceedings of the Internet Measurement Conference 2018</i>, Association for Computing Machinery, 31 Oct. 2018, pp. 443-56, doi.org/10.1145/3278532.3278570. Accessed 9 Apr. 2021.]</ref> Perta et al. analyzed fourteen of the most popular commercial VPN services in 2015 and inspected their internals and infrastructures. They found that the majority of VPN services suffer from IPv6 traffic leakage. A sophisticated DNS hijacking attack would allow all traffic to be transparently captured. <ref name="perta">[https://qmro.qmul.ac.uk/xmlui/bitstream/handle/123456789/10855/Tyson%20A%20Glance%20through%20the%20VPN%202015%20Published.pdf Perta, V. et al. "A Glance through the VPN Looking Glass: IPv6 Leakage and DNS Hijacking in Commercial VPN clients." <i>Proceedings on Privacy Enhancing Technologies</i>, vol. 2015, no. 1, 2015, pp. 77-91, doi:10.1515/popets-2015-0006. Accessed 9 Apr. 2021.].</ref> | ||
| + | |||
| + | ===Misleading Advertisements=== | ||
| + | Several VPN companies have been found to have made misleading claims about their product. In 2019, NordVPN had an advertisement banned in the UK when they made false claims suggesting that users without a VPN are broadcasting their passwords to hackers on public WiFi. The Advertising Standards Agency found that the ad incorrectly made viewers believe that public networks are inherently insecure.<ref>[https://www.pcmag.com/news/nordvpn-ad-banned-for-exaggerating-threat-of-public-wi-fi Smith, Adam. “NordVPN Ad Banned for Exaggerating Threat of Public Wi-Fi.” <i>PCMag</i>, 1 May 2019, www.pcmag.com/news/nordvpn-ad-banned-for-exaggerating-threat-of-public-wi-fi. Accessed 12 Mar 2021.]</ref> Other companies have claimed that they keep no logs on user information, but independent investigations have found that several of these companies, including UFO VPN, have kept logs.<ref>[https://www.comparitech.com/blog/vpn-privacy/ufo-vpn-data-exposure/ Bischoff, Paul. "'Zero logs' VPN exposes millions of logs including user passwords, claims data is anonymous." <i>Comparitech</i>, 21 July 2020, www.comparitech.com/blog/vpn-privacy/ufo-vpn-data-exposure/. Accessed 12 Mar 2021.]</ref>. | ||
| + | |||
| + | ===Legality of VPN in China=== | ||
| + | VPN is legal in most countries and regions in the world. However, unauthorized VPNs are not allowed in China. To prevent citizens from accessing external contents that may contain reactionary speech and controversial events, Chinese government establish a Internet censorship system, which is also known as the Great Firewall. This system blocks from accessing websites such as BBC News, Wikipedia, Google, and Youtube. However, the existence of VPN can encrypt accessing request and therefore bypass the censorship system. Therefore, according to the Ministry of Industry and Information Technology of PRC, all legal VPN needs to be registered and authorized. According to Article 6 of the "Interim Regulations on the Management of International Networking of Computer Information Networks of the People's Republic of China", "The direct international networking of computer information networks must use the international access channels provided by the National Public Telecommunications Network of the Ministry of Posts and Telecommunications. Any Units and individuals are not allowed to establish or use other channels for international networking". Security organs can warn those who violate this regulation and impose a fine of up to 15,000 yuan. <ref> Chinese Government Website [http://www.gov.cn/gongbao/content/2011/content_1860856.htmPublic "Measures for the Administration of the Security Protection of the International Networking of Computer Information Networks"] </ref>According to , about 20-30 million Chinese citizens are using VPN to access external websites. Individual use of an unauthorized VPN used to be a legal "grey area" in China. It was illegal but was seldom actually controlled. However, starting 2017, Chinese government has launched a series of operations to restrict personal VPN usage, including banning VPN apps from app stores. One of the largest VPN provider GreenVPN was shut down and removed from Apple's App Store in request of the authorities. <ref> Josh Ye [https://www.scmp.com/news/china/policies-politics/article/2064587/chinas-move-clean-vpns-and-strengthen-great-firewall "China tightens Great Firewall by declaring unauthorised VPN services illegal"] South China Morning Post </ref> <ref> Saheli Roy Choudhury [https://www.cnbc.com/2017/07/31/apple-removes-vpn-apps-in-china-app-store.html "Apple removes VPN apps in China as Beijing doubles down on censorship"] CNBC News </ref> Besides, a series of reports show that the Public Security Bureau starts to punish individual usage of VPN. In 2017, | ||
| + | In 2019, Gao Yu, a Chinese citizen, was harassed by police for her posts on social media network Twitter. The police also had here son fired from his job. <ref> Dahai Han [https://www.voanews.com/east-asia-pacific/voa-news-china/chinese-authorities-punish-citizens-using-foreign-social-media "Chinese Authorities Punish Citizens for Using Foreign Social Media"] Voice of America </ref> In 2017, a man was fine 500,000 yuan and sentenced for 5 years for running VPN server. <ref> Haas Benjamin [https://www.theguardian.com/world/2017/dec/22/man-in-china-sentenced-to-five-years-jail-for-running-vpn Man in China sentenced to five years' jail for running VPN] The Guardian] | ||
==See Also== | ==See Also== | ||
*[[Censorship in China]] | *[[Censorship in China]] | ||
*[[Digital Piracy]] | *[[Digital Piracy]] | ||
| + | *[[Remote Access]] | ||
==References== | ==References== | ||
<references/> | <references/> | ||
| − | |||
| − | |||
[[Category:Services]] | [[Category:Services]] | ||
| − | [[Category: | + | [[Category:Software]] |
([[Topics|back to index]]) | ([[Topics|back to index]]) | ||
Latest revision as of 16:53, 21 April 2021
A virtual private network (VPN) is a service that protects a user's online privacy and anonymity by creating a private network from a public internet connection. VPNs mask a user's internet protocol (IP) address, making their online activities virtually untraceable. Moreover, VPN services establish secure and encrypted connections to provide greater privacy than even a secured Wi-Fi hotspot. [1] VPNs are classified into three main categories: remote access, intranet-based site-to-site, and extranet-based site-to-site. Aside from the various types of VPNs, it also includes a number of other services and features such as VPN protocols, security features, auto-connect settings, and real-time chat support. [2] As the use of VPNs grows in popularity, so do ethical concerns about VPN users, such as piracy, security, and misleading advertisements.
Contents
History
Gurdeep Pall, a Microsoft software developer, created the first VPN in 1996. It was designed as an efficient way for employees to securely access company data from remote locations, and it was built on the Point-to-Point Tunneling Protocol (PPTP), a method that is still in use today. [3]
VPNs evolved from a method for employees to work from home to much broader applications over time. Transport Layer Security (TLS), or its predecessor Secure Sockets Layer (SSL) encryption is one of the most common applications today. This is a feature of the vast majority of websites on the internet, and it is frequently indicated by a lock icon in the browser's search bar and labeled "Connection Secure." [4]
Types of VPNs
Site-to-Site
A Site-to-Site VPN, also called a Router-to-Router VPN, occurs when at least one user's network connects to another.[6] According to cybersecurity company Fortinet, these types of VPNs are often found in business settings. These routers connect to essentially form one large network comprised of local networks.[7] This allows someone on one of the local connections to access information from any of the other local networks connected to the VPN. One subtype of this category is an Intranet-Based Site-to-Site VPN. Intranet-Based Site-to-Site VPNs are often used within a company when the flow of information is relatively free. That is, all networks involved in the VPN have equal access and sharing of all resources. This helps simulate the experience of everyone working on the same local network.[7][6] Conversely, Extranet-Based Site-to-Site VPNs are used for more selective sharing.[7] GeeksforGeeks, a popular educational programming website, describes them as "companies [using] ... VPN ... to connect to the office of another company."[6]
Remote Access
With a Remote Access VPN, rather than connecting to another router, the user connects securely to a remote network.[8] By using a remote access VPN, an encrypted "tunnel" is created from the user's location to the VPN destination. This destination is determined by the creator of the private network being accessed, and some VPNs allow the user to choose their destination.[1] TunnelBear is an example of a VPN service where the user is able to choose where they would like to "tunnel" their data.
- Intranet-based VPN: When several offices of the same company are connected using a Site-to-Site VPN type, it is called an Intranet-based VPN. [6]
- Extranet-based VPN: When companies use a Site-to-site VPN type to connect to the office of another company, it is called an Extranet based VPN. [6]
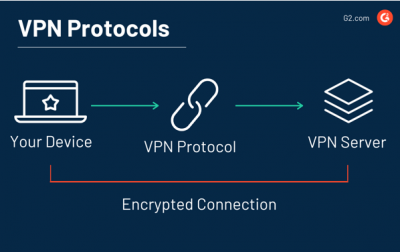
Types of VPN Protocols
A VPN protocol is a set of rules or instructions that will determine how your data routes between your device and the VPN server. VPN providers rely on protocols to ensure a stable and secure connection. VPN protocols have unique specifications that offer benefits to the VPN user based on the circumstances. Some specialize in privacy while others put an emphasis on speed. VPNs utilize different protocols depending on the device being used, what you want to do, and how you want to do it. [9]
Internet Protocol Security (IPSec)
An IPSec is used to secure internet communication across an IP network. IPSec secures internet protocol communication by verifying the sessions and encrypts each data packet during the connection. [10]
Point-to-Point Tunneling Protocol (PPTP)
Point-to-point tunneling protocol is one of the oldest VPN protocols in existence. A PPTP generates a tunnel and confines the data packet. [10] The point-to-point part of the protocol refers to the connection created by PPTP. It allows one point (user computer) to access another specific point (remote network) over the internet. The tunneling part of the protocol refers to the way one protocol is encapsulated within another protocol. In PPTP, the point-to-point protocol is wrapped inside the TCP/IP protocol, which provides the internet connection. [11]
OpenVPN
OpenVPN is an open-source protocol that allows developers access to its underlying code. This protocol has grown in popularity due to its use of (virtually unbreakable) AES-256 bit key with 2048-bit RSA authentication and a 160-bit SHA1 hash algorithm. [12]
Secure Socket Tunneling Protocol (SSTP)
An SSTP is a popular option due to its full integration with every Microsoft operating system since Windows Vista SP 1. It utilizes 2048-bit SSL/TLS certificates for authentication and 256-bit SSL keys for encryption. [12]
Internet Key Exchange version 2 (IKEv2)
IKEv2 is a common VPN tunneling protocol that provides a secure key exchange session. Similar to L2TP, it is normally paired with IPSec for encryption and authentication. This protocol is very good at re-establishing the link after temporary connection loss and excels at switching connections across network types. [12]
Uses
Access Remote Sites
Using a remote access VPN, users from across the globe can access a singular private network.[13] At the University of Michigan, a VPN is used to allow students to access the University's encrypted data when not on the campus internet. This allows students to remotely access information stored at the university, such as databases, or to take advantage of network protection provided through the university.[14] Throughout the Covid-19 pandemic, companies have relied on VPNs to grant employees access to servers, internal applications, and data hosted on-site. These actions were taken to limit the exposure of sensitive data.[15][16]
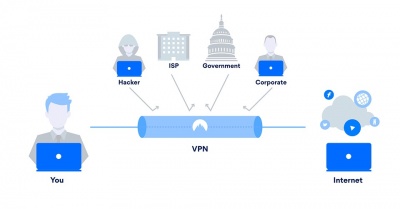
Privacy
As a VPN encrypts the data between the user and the network, it can help keep a user's information private.[15] This functionality is similar to how VPNs are used to access remote sites, as they help a user access data without having to worry about the WiFi network they're connected to.[18] By encrypting the information, the internet provider, government, and others who control the network face more difficulty in seeing what the user is doing on the network. Not only does this limit what data is collected about the user, but it can also decrease the number of targeted advertisements that can occur when browsing data is sold. Additionally, it can help to hide the user's location.[19]
Accessing Information From Other Countries
A VPN can also allow a user to access region-locked content or information that would otherwise be unavailable by making it appear as if they are located in a different location.
Circumventing Government Censorship
By disguising the IP address that a request comes from, a VPN can help to access sites blocked by the government in the country where the user is located. In China, "The Great Firewall" is a name given to the country-wide censorship of the internet. By using a VPN, Chinese citizens are able to access information that would otherwise be restricted by their government.[20] This has also allowed Chinese companies to conduct business with overseas partners. As new programs in China seek to control internet usage, some argue that VPNs can be useful tools to avoid these restrictions.[21] China is not the only location where VPNs are used to access blocked content. In Kashmir, citizens use VPNs to access social media sites such as WhatsApp or Instagram that have been banned by the government.[22]
Streaming Services
Another common use for a VPN is accessing streaming services that are not available in a given country. Viewers use VPNs to access the libraries of these services, primarily Netflix, by changing their virtual location to that of another country that has the desired content.[23] For example, as of November 2020, Star Trek: Discovery was not available on Netflix in the US and Canada but was in other countries.[24] In 2016, Netflix began taking steps to prevent the use of VPNs, though the CEO described the number of VPN users to be “really inconsequential.” [25] They did this by comparing the location of the user's IP address (which the VPN has altered) and their Domain Name Server (DNS) which could still reveal the user's true location.[26]
Netflix’s measures have reduced the general effectiveness of VPNs, rendering many services incompatible. However, there is still a multitude of options available that still bypass the region locking of the platform Hochstadt, Ariel. "8 Best Netflix VPNs That Still Work Reliably [Tested in 2021." vpnMentor, 5 April 2021, https://www.vpnmentor.com/blog/5-best-vpns-netflix-actually-work/. Accessed 10 April 2021.]</ref>
The 5 Eyes, 9 Eyes, and 14 Eyes Agreements
After World War II, the United States and the United Kingdom signed the BRUSA Agreement to share intelligence between the two countries. (The BRUSA Agreement is now known as the UKUSA Agreement.[27] Over time, this agreement grew to include more countries, eventually leading to the 5 Eyes, 9 Eyes, and 14 Eyes agreements (each one involving a different group of countries).
The initial intent of these agreements was to gather intelligence on the Soviet Union. The member countries of the official 5 Eyes treaty included the United States, Canada, the United Kingdom, Australia, and New Zealand. In 1982, the 14 Eyes group was formed, consisting of Germany, Italy, Spain, France, Sweden, the Netherlands, Norway, Belgium, and Denmark on top of the existing members of the 5 Eyes treaty. 9 Eyes is not outlined in a specific treaty but consists of the 5 Eyes members plus Denmark, Norway, France, and the Netherlands. [28]
As a part of this agreement, any intelligence gained by one country is automatically shared with all other countries in the agreement.[29] Some VPN companies, such as Restore Privacy, highlight this arrangement in support of using their services. These services claim that they can help users escape government surveillance, and hence prevent information sharing between countries with the 5, 9, and 14 Eyes agreements.[30]
Ethical Concerns
Pirating of Paid Content
Since VPNs can help make a user's web access history a secret from their Internet Service Provider (ISP), VPNs have become popular tools for illegally obtaining copyrighted material. This has resulted in lawsuits from producers who argue that VPN companies promote and facilitate pirating.[31] One popular method of pirating material like this is "torrenting" copyrighted material like movies, music, or video games. "Torrenting" refers to a method of peer-to-peer file sharing that uses the BitTorrent protocol. VPNs are often used in conjunction with this method because it hides the illegal file-sharing activity from Internet Service Providers.[32]
Security of a VPN
Using a VPN does not hide the information being sent from the user, but instead shifts the ability to see the information from the user's internet service provider to the VPN provider.[34] Some argue, however, that VPNs are not completely safe because the user is still dependent on the VPN company for their security. As an example, NordVPN, a leading provider, got hacked in 2019 and did not disclose the hack for several months.[35]
According to M.T. Khan and others, users rely on virtual private network services for a number of reasons: to preserve their privacy, circumvent censorship, and access geo-filtered content. A 2018 evaluation of sixty-two commercial VPN providers showed that while the services seem less likely to intercept or tamper with user traffic, some VPNs do leak user traffic through a variety of means. From the study, in 10% of the providers studied, between 5 and 30% of the VPNs appeared to be hosted on servers located in countries other than those advertised to users.[36] Perta et al. analyzed fourteen of the most popular commercial VPN services in 2015 and inspected their internals and infrastructures. They found that the majority of VPN services suffer from IPv6 traffic leakage. A sophisticated DNS hijacking attack would allow all traffic to be transparently captured. [37]
Misleading Advertisements
Several VPN companies have been found to have made misleading claims about their product. In 2019, NordVPN had an advertisement banned in the UK when they made false claims suggesting that users without a VPN are broadcasting their passwords to hackers on public WiFi. The Advertising Standards Agency found that the ad incorrectly made viewers believe that public networks are inherently insecure.[38] Other companies have claimed that they keep no logs on user information, but independent investigations have found that several of these companies, including UFO VPN, have kept logs.[39].
Legality of VPN in China
VPN is legal in most countries and regions in the world. However, unauthorized VPNs are not allowed in China. To prevent citizens from accessing external contents that may contain reactionary speech and controversial events, Chinese government establish a Internet censorship system, which is also known as the Great Firewall. This system blocks from accessing websites such as BBC News, Wikipedia, Google, and Youtube. However, the existence of VPN can encrypt accessing request and therefore bypass the censorship system. Therefore, according to the Ministry of Industry and Information Technology of PRC, all legal VPN needs to be registered and authorized. According to Article 6 of the "Interim Regulations on the Management of International Networking of Computer Information Networks of the People's Republic of China", "The direct international networking of computer information networks must use the international access channels provided by the National Public Telecommunications Network of the Ministry of Posts and Telecommunications. Any Units and individuals are not allowed to establish or use other channels for international networking". Security organs can warn those who violate this regulation and impose a fine of up to 15,000 yuan. [40]According to , about 20-30 million Chinese citizens are using VPN to access external websites. Individual use of an unauthorized VPN used to be a legal "grey area" in China. It was illegal but was seldom actually controlled. However, starting 2017, Chinese government has launched a series of operations to restrict personal VPN usage, including banning VPN apps from app stores. One of the largest VPN provider GreenVPN was shut down and removed from Apple's App Store in request of the authorities. [41] [42] Besides, a series of reports show that the Public Security Bureau starts to punish individual usage of VPN. In 2017,
In 2019, Gao Yu, a Chinese citizen, was harassed by police for her posts on social media network Twitter. The police also had here son fired from his job. [43] In 2017, a man was fine 500,000 yuan and sentenced for 5 years for running VPN server. [44]- ↑ 1.0 1.1 Symanovich, Steve. "What is a VPN?" Norton, 14 Jan. 2021, us.norton.com/internetsecurity-privacy-what-is-a-vpn.html. Accessed 8 Apr. 2021.
- ↑ Greenberg, Ran. "Different Types of VPNs and When to Use Them" VPNMentor, 15 Apr. 2021, https://www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/ Accessed 19 Apr. 2021.
- ↑ "A Brief History of VPNs." vypervpn, 21 June 2016, https://www.vyprvpn.com/blog/brief-history-of-vpns. Accessed 10 April 2021.
- ↑ Rosencrance, Linda. "SSL VPN (Secure Sockets Layer virtual private network)." SearchSecurity, April 2020, https://searchsecurity.techtarget.com/definition/SSL-VPN. Accessed 10 April 2021.
- ↑ TunnelBear. www.tunnelbear.com/. Accessed 9 Apr. 2021.
- ↑ 6.0 6.1 6.2 6.3 6.4 "Types of Virtual Private Network (VPN) and its Protocols." Geeks for Geeks, 10 Apr. 2019, www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/. Accessed 8 Apr. 2021.
- ↑ 7.0 7.1 7.2 "What is a Site-to-Site VPN?" Fortinet, www.fortinet.com/resources/cyberglossary/what-is-site-to-site-vpn. Accessed 8 Apr. 2021.
- ↑ “Different Types of VPNs and When to Use Them.” VPNMentor, www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/. Accessed 12 Mar 2021.
- ↑ 9.0 9.1 Calvello, Mara. "VPN Protocols: Are You Using the Right One?" Learn Hub, https://learn.g2.com/vpn-protocols 28 April. 2020, Accessed 19 Apr. 2021.
- ↑ 10.0 10.1 pp_pankaj. "Types of Virtual Private Network (VPN) and its Protocols" GeeksforGeeks, https://www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/ 10 Apr. 2019, Accessed 19 Apr. 2021.
- ↑ Christensson, P. "PPTP definition" TechTerms, https://techterms.com/definition/pptp 2006, Accessed 19 Apr. 2021.
- ↑ 12.0 12.1 12.2 Harkness, Adam. "5 Common VPN protocols explained" NetMotion, https://www.netmotionsoftware.com/blog/connectivity/vpn-protocols 15 May. 2019, Accessed 19 Apr. 2021.
- ↑ “Virtual private networks.” IEEE Potentials, vol. 20, no. 1, 2001, pp. 11-15, doi:10.1109/45.913204. Accessed 12 Mar. 2021.
- ↑ “Virtual Private Network (VPN).” Information and Technology Services, University of Michigan, its.umich.edu/enterprise/wifi-networks/vpn. Accessed 12 Mar. 2021.
- ↑ 15.0 15.1 “What is a business VPN?” Cloudflare, www.cloudflare.com/learning/access-management/what-is-a-business-vpn/. Accessed 12 Mar. 2021.
- ↑ “Why Companies Are Turning To VPNs During The Coronavirus Outbreak.” OpenVPN, openvpn.net/why-companies-are-turning-to-vpns-during-the-coronavirus-outbreak. Accessed 12 Mar. 2021.
- ↑ “The ultimate guide to VPN encryption, protocols, and ciphers.” ATT, 31 July 2019, cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers. Accessed 25 Mar. 2021.
- ↑ Levin, Benjamin. “A VPN is vital when working from home, so here’s everything you need to know.” CNN, 17 Sept. 2020, www.cnn.com/2020/09/17/cnn-underscored/how-to-setup-a-vpn. Accessed 12 Mar. 2021.
- ↑ “What is a VPN.” Cloudflare, www.cloudflare.com/learning/access-management/what-is-a-vpn/. Accessed 12 Mar. 2021.
- ↑ Economy, Elizabeth C. “The great firewall of China: Xi Jinping’s internet shutdown.” The Guardian, 29 June 2018, www.theguardian.com/news/2018/jun/29/the-great-firewall-of-china-xi-jinpings-internet-shutdown. Accessed 12 Mar. 2021.
- ↑ Shanghai, Liza Linin and Josh Chin. "China’s VPN Crackdown Weighs on Foreign Companies There." The Wall Street Journal, 2017 Aug. 2, www.wsj.com/articles/chinas-vpn-crackdown-weighs-on-foreign-companies-there-1501680195. Accessed 8 Apr. 2021.
- ↑ Bukhari, Fayaz. “India cracks down on use of VPNs in Kashmir to get around social media ban.” Reuters, 19 Feb. 2020, www.reuters.com/article/us-india-kashmir-internet/india-cracks-down-on-use-of-vpns-in-kashmir-to-get-around-social-media-ban-idUSKBN20D0LT. Accessed 12 Mar. 2021.
- ↑ Hodge, Rae. “VPN use surges during the coronavirus lockdown, but so do security risks.” CNET, 23 Apr. 2020, www.cnet.com/news/vpn-use-surges-during-the-coronavirus-lockdown-but-so-do-security-risks/. Accessed 12 Mar. 2021.
- ↑ Eddy, Max. "How to Use a VPN to Watch Netflix From Other Countries." PCMag, 20 Nov. 2020, www.pcmag.com/how-to/how-to-unblock-netflix-with-a-vpn. Accessed 9 Apr. 2021.
- ↑ Greenberg, Julia. "Netflix's CEO Says VPN Users Really Aren't a Big Deal." Wired, 18 April 2020, https://www.wired.com/2016/04/netflixs-ceo-says-vpn-users-really-arent-big-deal/. Accessed 10 April 2021.
- ↑ Parker, Jacob. "How does Netflix detect and block VPN use?" TechRader, 30 June 2020, www.techradar.com/vpn/how-does-netflix-detect-and-block-vpn-use. Accessed 9 Apr. 2021.
- ↑ "UKUSA Agreement Release." National Security Agency Central Security Service, www.nsa.gov/news-features/declassified-documents/ukusa/. Accessed 1 Apr. 2021.
- ↑ Koch, Richie. "What countries are in the 5 Eyes, 9 Eyes, and 14 Eyes aggreements?" ProtonVPN, 30 August 2018, https://protonvpn.com/blog/5-eyes-global-surveillance/. Accessed 10 April 2021.
- ↑ "Five Eyes." Privacy International, privacyinternational.org/learn/five-eyes. Accessed 8 Apr. 2021.
- ↑ Taylor, Sven. "Five Eyes, Nine Eyes, 14 Eyes – Explained." Restore Privacy, 3 Sep. 2020, restoreprivacy.com/5-eyes-9-eyes-14-eyes/. Accessed 8 Apr. 2021.
- ↑ Sharma, Mayank. “This top VPN is being sued by filmmakers.” Future US, 11 Mar 2021, www.techradar.com/news/this-top-vpn-is-being-sued-by-filmmakers. Accessed 12 Mar. 2021.
- ↑ Bischoff, Paul. "What is Torrenting? Is it Safe? Is it illegal? Are you likely to be caught?" Comparitech, 8 Apr. 2021, www.comparitech.com/blog/vpn-privacy/is-torrenting-safe-illegal-will-you-be-caught/. Accessed 9 Apr. 2021.
- ↑ “Popcorn Time VPN.” LiquidVPN, www.liquidvpn.com/popcorn-time-vpn/. Accessed 25 Mar 2021.
- ↑ “This Video Is Sponsored By ███ VPN.” YouTube, uploaded by Tom Scott, 28 Oct 2019, www.youtube.com/watch?v=WVDQEoe6ZWY.
- ↑ Whittaker, Zack. “NordVPN confirms it was hacked.” TechCrunched, 21 Oct. 2019, techcrunch.com/2019/10/21/nordvpn-confirms-it-was-hacked/. Accessed 12 Mar. 2021.
- ↑ Khan, M. T., et al. "An Empirical Analysis of the Commercial VPN Ecosystem." In Proceedings of the Internet Measurement Conference 2018, Association for Computing Machinery, 31 Oct. 2018, pp. 443-56, doi.org/10.1145/3278532.3278570. Accessed 9 Apr. 2021.
- ↑ Perta, V. et al. "A Glance through the VPN Looking Glass: IPv6 Leakage and DNS Hijacking in Commercial VPN clients." Proceedings on Privacy Enhancing Technologies, vol. 2015, no. 1, 2015, pp. 77-91, doi:10.1515/popets-2015-0006. Accessed 9 Apr. 2021..
- ↑ Smith, Adam. “NordVPN Ad Banned for Exaggerating Threat of Public Wi-Fi.” PCMag, 1 May 2019, www.pcmag.com/news/nordvpn-ad-banned-for-exaggerating-threat-of-public-wi-fi. Accessed 12 Mar 2021.
- ↑ Bischoff, Paul. "'Zero logs' VPN exposes millions of logs including user passwords, claims data is anonymous." Comparitech, 21 July 2020, www.comparitech.com/blog/vpn-privacy/ufo-vpn-data-exposure/. Accessed 12 Mar 2021.
- ↑ Chinese Government Website "Measures for the Administration of the Security Protection of the International Networking of Computer Information Networks"
- ↑ Josh Ye "China tightens Great Firewall by declaring unauthorised VPN services illegal" South China Morning Post
- ↑ Saheli Roy Choudhury "Apple removes VPN apps in China as Beijing doubles down on censorship" CNBC News
- ↑ Dahai Han "Chinese Authorities Punish Citizens for Using Foreign Social Media" Voice of America
- ↑ Haas Benjamin Man in China sentenced to five years' jail for running VPN The Guardian]
See Also
References
- ↑ 1.0 1.1 Symanovich, Steve. "What is a VPN?" Norton, 14 Jan. 2021, us.norton.com/internetsecurity-privacy-what-is-a-vpn.html. Accessed 8 Apr. 2021.
- ↑ Greenberg, Ran. "Different Types of VPNs and When to Use Them" VPNMentor, 15 Apr. 2021, https://www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/ Accessed 19 Apr. 2021.
- ↑ "A Brief History of VPNs." vypervpn, 21 June 2016, https://www.vyprvpn.com/blog/brief-history-of-vpns. Accessed 10 April 2021.
- ↑ Rosencrance, Linda. "SSL VPN (Secure Sockets Layer virtual private network)." SearchSecurity, April 2020, https://searchsecurity.techtarget.com/definition/SSL-VPN. Accessed 10 April 2021.
- ↑ TunnelBear. www.tunnelbear.com/. Accessed 9 Apr. 2021.
- ↑ 6.0 6.1 6.2 6.3 6.4 "Types of Virtual Private Network (VPN) and its Protocols." Geeks for Geeks, 10 Apr. 2019, www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/. Accessed 8 Apr. 2021.
- ↑ 7.0 7.1 7.2 "What is a Site-to-Site VPN?" Fortinet, www.fortinet.com/resources/cyberglossary/what-is-site-to-site-vpn. Accessed 8 Apr. 2021.
- ↑ “Different Types of VPNs and When to Use Them.” VPNMentor, www.vpnmentor.com/blog/different-types-of-vpns-and-when-to-use-them/. Accessed 12 Mar 2021.
- ↑ 9.0 9.1 Calvello, Mara. "VPN Protocols: Are You Using the Right One?" Learn Hub, https://learn.g2.com/vpn-protocols 28 April. 2020, Accessed 19 Apr. 2021.
- ↑ 10.0 10.1 pp_pankaj. "Types of Virtual Private Network (VPN) and its Protocols" GeeksforGeeks, https://www.geeksforgeeks.org/types-of-virtual-private-network-vpn-and-its-protocols/ 10 Apr. 2019, Accessed 19 Apr. 2021.
- ↑ Christensson, P. "PPTP definition" TechTerms, https://techterms.com/definition/pptp 2006, Accessed 19 Apr. 2021.
- ↑ 12.0 12.1 12.2 Harkness, Adam. "5 Common VPN protocols explained" NetMotion, https://www.netmotionsoftware.com/blog/connectivity/vpn-protocols 15 May. 2019, Accessed 19 Apr. 2021.
- ↑ “Virtual private networks.” IEEE Potentials, vol. 20, no. 1, 2001, pp. 11-15, doi:10.1109/45.913204. Accessed 12 Mar. 2021.
- ↑ “Virtual Private Network (VPN).” Information and Technology Services, University of Michigan, its.umich.edu/enterprise/wifi-networks/vpn. Accessed 12 Mar. 2021.
- ↑ 15.0 15.1 “What is a business VPN?” Cloudflare, www.cloudflare.com/learning/access-management/what-is-a-business-vpn/. Accessed 12 Mar. 2021.
- ↑ “Why Companies Are Turning To VPNs During The Coronavirus Outbreak.” OpenVPN, openvpn.net/why-companies-are-turning-to-vpns-during-the-coronavirus-outbreak. Accessed 12 Mar. 2021.
- ↑ “The ultimate guide to VPN encryption, protocols, and ciphers.” ATT, 31 July 2019, cybersecurity.att.com/blogs/security-essentials/the-ultimate-guide-to-vpn-encryption-protocols-and-ciphers. Accessed 25 Mar. 2021.
- ↑ Levin, Benjamin. “A VPN is vital when working from home, so here’s everything you need to know.” CNN, 17 Sept. 2020, www.cnn.com/2020/09/17/cnn-underscored/how-to-setup-a-vpn. Accessed 12 Mar. 2021.
- ↑ “What is a VPN.” Cloudflare, www.cloudflare.com/learning/access-management/what-is-a-vpn/. Accessed 12 Mar. 2021.
- ↑ Economy, Elizabeth C. “The great firewall of China: Xi Jinping’s internet shutdown.” The Guardian, 29 June 2018, www.theguardian.com/news/2018/jun/29/the-great-firewall-of-china-xi-jinpings-internet-shutdown. Accessed 12 Mar. 2021.
- ↑ Shanghai, Liza Linin and Josh Chin. "China’s VPN Crackdown Weighs on Foreign Companies There." The Wall Street Journal, 2017 Aug. 2, www.wsj.com/articles/chinas-vpn-crackdown-weighs-on-foreign-companies-there-1501680195. Accessed 8 Apr. 2021.
- ↑ Bukhari, Fayaz. “India cracks down on use of VPNs in Kashmir to get around social media ban.” Reuters, 19 Feb. 2020, www.reuters.com/article/us-india-kashmir-internet/india-cracks-down-on-use-of-vpns-in-kashmir-to-get-around-social-media-ban-idUSKBN20D0LT. Accessed 12 Mar. 2021.
- ↑ Hodge, Rae. “VPN use surges during the coronavirus lockdown, but so do security risks.” CNET, 23 Apr. 2020, www.cnet.com/news/vpn-use-surges-during-the-coronavirus-lockdown-but-so-do-security-risks/. Accessed 12 Mar. 2021.
- ↑ Eddy, Max. "How to Use a VPN to Watch Netflix From Other Countries." PCMag, 20 Nov. 2020, www.pcmag.com/how-to/how-to-unblock-netflix-with-a-vpn. Accessed 9 Apr. 2021.
- ↑ Greenberg, Julia. "Netflix's CEO Says VPN Users Really Aren't a Big Deal." Wired, 18 April 2020, https://www.wired.com/2016/04/netflixs-ceo-says-vpn-users-really-arent-big-deal/. Accessed 10 April 2021.
- ↑ Parker, Jacob. "How does Netflix detect and block VPN use?" TechRader, 30 June 2020, www.techradar.com/vpn/how-does-netflix-detect-and-block-vpn-use. Accessed 9 Apr. 2021.
- ↑ "UKUSA Agreement Release." National Security Agency Central Security Service, www.nsa.gov/news-features/declassified-documents/ukusa/. Accessed 1 Apr. 2021.
- ↑ Koch, Richie. "What countries are in the 5 Eyes, 9 Eyes, and 14 Eyes aggreements?" ProtonVPN, 30 August 2018, https://protonvpn.com/blog/5-eyes-global-surveillance/. Accessed 10 April 2021.
- ↑ "Five Eyes." Privacy International, privacyinternational.org/learn/five-eyes. Accessed 8 Apr. 2021.
- ↑ Taylor, Sven. "Five Eyes, Nine Eyes, 14 Eyes – Explained." Restore Privacy, 3 Sep. 2020, restoreprivacy.com/5-eyes-9-eyes-14-eyes/. Accessed 8 Apr. 2021.
- ↑ Sharma, Mayank. “This top VPN is being sued by filmmakers.” Future US, 11 Mar 2021, www.techradar.com/news/this-top-vpn-is-being-sued-by-filmmakers. Accessed 12 Mar. 2021.
- ↑ Bischoff, Paul. "What is Torrenting? Is it Safe? Is it illegal? Are you likely to be caught?" Comparitech, 8 Apr. 2021, www.comparitech.com/blog/vpn-privacy/is-torrenting-safe-illegal-will-you-be-caught/. Accessed 9 Apr. 2021.
- ↑ “Popcorn Time VPN.” LiquidVPN, www.liquidvpn.com/popcorn-time-vpn/. Accessed 25 Mar 2021.
- ↑ “This Video Is Sponsored By ███ VPN.” YouTube, uploaded by Tom Scott, 28 Oct 2019, www.youtube.com/watch?v=WVDQEoe6ZWY.
- ↑ Whittaker, Zack. “NordVPN confirms it was hacked.” TechCrunched, 21 Oct. 2019, techcrunch.com/2019/10/21/nordvpn-confirms-it-was-hacked/. Accessed 12 Mar. 2021.
- ↑ Khan, M. T., et al. "An Empirical Analysis of the Commercial VPN Ecosystem." In Proceedings of the Internet Measurement Conference 2018, Association for Computing Machinery, 31 Oct. 2018, pp. 443-56, doi.org/10.1145/3278532.3278570. Accessed 9 Apr. 2021.
- ↑ Perta, V. et al. "A Glance through the VPN Looking Glass: IPv6 Leakage and DNS Hijacking in Commercial VPN clients." Proceedings on Privacy Enhancing Technologies, vol. 2015, no. 1, 2015, pp. 77-91, doi:10.1515/popets-2015-0006. Accessed 9 Apr. 2021..
- ↑ Smith, Adam. “NordVPN Ad Banned for Exaggerating Threat of Public Wi-Fi.” PCMag, 1 May 2019, www.pcmag.com/news/nordvpn-ad-banned-for-exaggerating-threat-of-public-wi-fi. Accessed 12 Mar 2021.
- ↑ Bischoff, Paul. "'Zero logs' VPN exposes millions of logs including user passwords, claims data is anonymous." Comparitech, 21 July 2020, www.comparitech.com/blog/vpn-privacy/ufo-vpn-data-exposure/. Accessed 12 Mar 2021.
- ↑ Chinese Government Website "Measures for the Administration of the Security Protection of the International Networking of Computer Information Networks"
- ↑ Josh Ye "China tightens Great Firewall by declaring unauthorised VPN services illegal" South China Morning Post
- ↑ Saheli Roy Choudhury "Apple removes VPN apps in China as Beijing doubles down on censorship" CNBC News
- ↑ Dahai Han "Chinese Authorities Punish Citizens for Using Foreign Social Media" Voice of America
- ↑ Haas Benjamin Man in China sentenced to five years' jail for running VPN The Guardian]
See Also
References
<references/>