Difference between revisions of "Decentralized Networks"
(→Piracy) |
|||
| (37 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
'''Decentralized networks''' are systems which inherently have no central authority or governance. These systems often operate on individual computers spread across the globe, interconnected by the Internet, also known as peer-to-peer networking. These computers act in unison towards a common goal. <ref>Kremenova, Iveta, and Milan Gajdos. "Decentralized networks: The future internet." Mobile Networks and Applications 24.6 (2019): 2016-2023.</ref> | '''Decentralized networks''' are systems which inherently have no central authority or governance. These systems often operate on individual computers spread across the globe, interconnected by the Internet, also known as peer-to-peer networking. These computers act in unison towards a common goal. <ref>Kremenova, Iveta, and Milan Gajdos. "Decentralized networks: The future internet." Mobile Networks and Applications 24.6 (2019): 2016-2023.</ref> | ||
| − | Computers within decentralized networks are capable of operating independently of each other. As a result, the variety of services and applications built on decentralized networks are often difficult for third parties, such as governments, to shut down. | + | Computers within decentralized networks are capable of operating independently of each other.<ref>https://www.gemini.com/cryptopedia/blockchain-network-decentralized-distributed-centralized</ref> As a result, the variety of services and applications built on decentralized networks are often difficult for third parties, such as governments, to shut down. As such, ethical concerns have arisen from the usage of decentralized networks, with most directly related to the lack of regulation on it. The applications of it include cryptocurrencies, dark web marketplaces, and the dissemination of data, which calls into question the lack of traceability and accountability in these systems as they can be used for illicit activities. Energy consumption concerns and computer hardware shortages have also been attributed to cryptocurrency mining. |
| − | + | ||
| − | + | ||
==Notable applications== | ==Notable applications== | ||
===Decentralized finance (DeFi)=== | ===Decentralized finance (DeFi)=== | ||
| − | Decentralized finance applications use blockchain technology to provide access to financial instruments without the need of going through conventional financial intermediaries such as banks, brokerages, or exchanges. People may trade digital assets on these platforms much like in physical markets. However, DeFi allows for pseudo-anonymous cryptocurrency trading, market speculation based on derivates, borrowing and lending of cryptocurrencies. | + | Decentralized finance applications use blockchain technology to provide access to financial instruments without the need of going through conventional financial intermediaries such as banks, brokerages, or exchanges. People may trade digital assets on these platforms much like in physical markets.<ref>https://www.bloomberg.com/news/articles/2020-08-26/why-defi-utopia-would-be-finance-without-financiers-quicktake</ref> However, DeFi allows for pseudo-anonymous cryptocurrency trading, market speculation based on derivates, borrowing and lending of cryptocurrencies.<ref>https://www.forbes.com/sites/forbestechcouncil/2021/11/17/three-big-myths-about-decentralized-finance/?sh=1ef717557c54</ref> |
| − | Decentralized finance operates on smart contracts, which are essentially software made to run on decentralized networks such as the Ethereum blockchain. Since the blockchain is publicly accessible, anyone may audit the smart contracts used in DeFi to ensure it is not malicious. This presents a stark contrast from traditional financial institutions, which typically do not release the source code of banking software, but also presents risk in that security vulnerabilities present in smart contracts may be exploited for individual gain. | + | Decentralized finance operates on smart contracts, which are essentially software made to run on decentralized networks such as the Ethereum blockchain. Since the blockchain is publicly accessible, anyone may audit the smart contracts used in DeFi to ensure it is not malicious.<ref>https://ethereum.org/en/defi/</ref> This presents a stark contrast from traditional financial institutions, which typically do not release the source code of banking software, but also presents risk in that security vulnerabilities present in smart contracts may be exploited for individual gain. |
====Cryptocurrency==== | ====Cryptocurrency==== | ||
| − | Cryptocurrencies are digital assets designed to be virtual stores of value which are independent of centralized governance. Transactions involving cryptocurrencies are typically stored on a digital ledger, with the transactions being processed based on a consensus model within the cryptocurrency's decentralized network, with proof-of-work being the dominant protocol. | + | Cryptocurrencies are digital assets designed to be virtual stores of value which are independent of centralized governance. Transactions involving cryptocurrencies are typically stored on a digital ledger, with the transactions being processed based on a consensus model within the cryptocurrency's decentralized network, with proof-of-work being the dominant protocol.<ref name=consensus>Judmayer, Aljosha, et al. "Blocks and chains: introduction to bitcoin, cryptocurrencies, and their consensus mechanisms." Synthesis Lectures on Information Security, Privacy, & Trust 9.1 (2017): 1-123.</ref> |
| − | The first cryptocurrency, Bitcoin, was released in 2009, and as of | + | The first cryptocurrency, Bitcoin, was released in 2009, and as of February 2022 has a market capitalization of US$838 billion.<ref>https://finance.yahoo.com/quote/BTC-USD/</ref> Numerous other cryptocurrencies, known as altcoins, have emerged since Bitcoin, seeking to provide additional or improved functionality over Bitcoin. Examples include Ethereum which has the capability of running smart contracts, Ripple which provides real-time settlements, and ZCash which provides true anonymity for transactions. |
| − | Cryptocurrencies operate on a consensus model to decide parameters of the system, such as how often new currency is created and how much is created. The decentralized network of users, each have a proportional share in deciding the consensus by proxy of their computing resources, or ownership of the currency. Cryptocurrencies are defined by the parameters of the network which has majority consensus, so any diverging networks would typically cease to be recognized by the community and thus lose value. Occasionally, such as in the case of the Ethereum and Ethereum Classic networks, the consensus diverges but both are still recognized as valid networks and retain some value, such an event is known as a chain split. | + | Cryptocurrencies operate on a consensus model to decide parameters of the system, such as how often new currency is created and how much is created. The decentralized network of users, each have a proportional share in deciding the consensus by proxy of their computing resources, or ownership of the currency.<ref name=consensus></ref> Cryptocurrencies are defined by the parameters of the network which has majority consensus, so any diverging networks would typically cease to be recognized by the community and thus lose value. Occasionally, such as in the case of the Ethereum and Ethereum Classic networks, the consensus diverges but both are still recognized as valid networks and retain some value, such an event is known as a chain split.<ref>https://coinmarketcap.com/alexandria/glossary/chain-split</ref> |
| + | |||
| + | Cryptocurrencies networks have also enabled the creation and trading of non-fungible tokens (NFTs), which are supposed to represent rights to digital assets such as artwork, pictures, or videos. NFTs are stored on cryptocurrency blockchains, which are used to verify ownership of the NFT. <ref>Wilson, Kathleen Bridget, Adam Karg, and Hadi Ghaderi. "Prospecting non-fungible tokens in the digital economy: Stakeholders and ecosystem, risk and opportunity." Business Horizons (2021).</ref> | ||
===File sharing networks=== | ===File sharing networks=== | ||
| Line 24: | Line 24: | ||
====BitTorrent==== | ====BitTorrent==== | ||
| + | [[File:Torrentcomp_small.gif|thumb|right|A visualization of how the BitTorrent protocol shares a file from one server to several clients. Wikiadd, [http://creativecommons.org/licenses/by-sa/3.0/ CC BY-SA 3.0], via Wikimedia Commons]] | ||
| + | |||
BitTorrent is a peer-to-peer file sharing protocol which allows for electronic data distribution over a decentralized network. The protocol is designed such that it reduces the computing resources needed to distribute large files. Files are segmented, then distributed to different computers which then simultaneously upload segments others need and download segments it needs from other computers. Doing so reduces the impact on global internet traffic, as users may download files from a more local source rather than a server located in distant geographic regions. | BitTorrent is a peer-to-peer file sharing protocol which allows for electronic data distribution over a decentralized network. The protocol is designed such that it reduces the computing resources needed to distribute large files. Files are segmented, then distributed to different computers which then simultaneously upload segments others need and download segments it needs from other computers. Doing so reduces the impact on global internet traffic, as users may download files from a more local source rather than a server located in distant geographic regions. | ||
In 2019, the BitTorrent protocol accounted for 2.46% of downstream, and 27.58% of upstream internet traffic. <ref>Marozzo, Fabrizio, Domenico Talia, and Paolo Trunfio. "A sleep‐and‐wake technique for reducing energy consumption in BitTorrent networks." Concurrency and Computation: Practice and Experience 32.14 (2020): e5723. | In 2019, the BitTorrent protocol accounted for 2.46% of downstream, and 27.58% of upstream internet traffic. <ref>Marozzo, Fabrizio, Domenico Talia, and Paolo Trunfio. "A sleep‐and‐wake technique for reducing energy consumption in BitTorrent networks." Concurrency and Computation: Practice and Experience 32.14 (2020): e5723. | ||
</ref> | </ref> | ||
| − | |||
| − | |||
====InterPlanetary File System (IPFS)==== | ====InterPlanetary File System (IPFS)==== | ||
IPFS is a peer-to-peer decentralized network used to preserve and share data in a distributed file system. The data stored on it is duplicated across several computers on the network, so if one computer goes offline, the data is still accessible. It is designed as an easy to use, global store of information, with a defined naming scheme, IPNS, to uniquely locate items by.<ref>https://ipfs.io/</ref> It has been used for archival efforts such as for the Genesis Library, which archives books and journals.<ref>https://web.archive.org/web/20201127164841/http://freeread.org/ipfs/</ref> Similar to BitTorrent, users have the option of preserving media it accesses and redistributing it to others. | IPFS is a peer-to-peer decentralized network used to preserve and share data in a distributed file system. The data stored on it is duplicated across several computers on the network, so if one computer goes offline, the data is still accessible. It is designed as an easy to use, global store of information, with a defined naming scheme, IPNS, to uniquely locate items by.<ref>https://ipfs.io/</ref> It has been used for archival efforts such as for the Genesis Library, which archives books and journals.<ref>https://web.archive.org/web/20201127164841/http://freeread.org/ipfs/</ref> Similar to BitTorrent, users have the option of preserving media it accesses and redistributing it to others. | ||
| − | |||
===Onion Routing=== | ===Onion Routing=== | ||
Onion routing is a communication protocol used to communicate anonymously and securely on computer networks, utilizing a decentralized onion network. Instead of communicating directly between two computers, onion routing encapsulates the data in several layers of encryption, and passes it on through a series of computers on the onion network. As the data transits through each computer on the way to its destination, a layer of the encryption is 'peeled' away, revealing the next destination of the data. This ensures the intermediary computers do not simultaneously know the initial source and the final destination of the data it is transmitting, protecting the anonymity of the sender from the intermediaries. <ref>Syverson, Paul, D. Goldschlag, and M. Reed. "Onion routing for anonymous and private internet connections." Communications of the ACM 42.2 (1999): 5. | Onion routing is a communication protocol used to communicate anonymously and securely on computer networks, utilizing a decentralized onion network. Instead of communicating directly between two computers, onion routing encapsulates the data in several layers of encryption, and passes it on through a series of computers on the onion network. As the data transits through each computer on the way to its destination, a layer of the encryption is 'peeled' away, revealing the next destination of the data. This ensures the intermediary computers do not simultaneously know the initial source and the final destination of the data it is transmitting, protecting the anonymity of the sender from the intermediaries. <ref>Syverson, Paul, D. Goldschlag, and M. Reed. "Onion routing for anonymous and private internet connections." Communications of the ACM 42.2 (1999): 5. | ||
</ref> | </ref> | ||
| − | |||
====Tor and the Dark Web==== | ====Tor and the Dark Web==== | ||
| − | Tor, which is an abbreviation of The Onion Router, is a free, open-source implementation of onion routing. For ease of use, Tor has been implemented into a web browser based on Chromium, the Tor Browser. It allows users to visit internet websites anonymously, and prevents eavesdropping by third parties. Content which is region locked, or blocked by local governments can also be accessed through the use of Tor. | + | Tor, which is an abbreviation of The Onion Router, is a free, open-source implementation of onion routing. For ease of use, Tor has been implemented into a web browser based on Chromium, the Tor Browser. It allows users to visit internet websites anonymously, and prevents eavesdropping by third parties. Content which is region locked, or blocked by local governments can also be accessed through the use of Tor.<ref>https://www.torproject.org/about/history/</ref> |
| − | The use of a Tor-enabled network also allows users to access the Dark Web, a collection of websites not normally accessible via the Internet. These websites are hosted on servers whose physical locations are effectively hidden due to onion routing. | + | The use of a Tor-enabled network also allows users to access the Dark Web, a collection of websites not normally accessible via the Internet. These websites are hosted on servers whose physical locations are effectively hidden due to onion routing.<ref>Jardine, Eric. "The Dark Web dilemma: Tor, anonymity and online policing." Global Commission on Internet Governance Paper Series 21 (2015).</ref> |
==Security concerns== | ==Security concerns== | ||
| + | The open source nature of decentralized networks allows malicious actors to find and exploit vulnerabilities present on the network. In 2016, a vulnerability in the DAO's smart contract on the Ethereum network allowed attackers to drain 3.6 million Ether out of the DAO's accounts. This caused the price of ether to drop from $20 to $13 and triggered proposals of a soft-fork or hard-fork to reverse the attack. <ref>https://www.coindesk.com/learn/2016/06/25/understanding-the-dao-attack/</ref> | ||
| + | |||
| + | Cryptocurrency "mining", the process of exchanging computing resources for a cryptocurrency can be done anonymously. In 2013, ESEA, a private CS:GO server, which requires its users to install an anti-cheat application on their computers to access game servers, was exposed for embedding a bitcoin miner within the anti-cheat application. The miner was embedded by a single rogue employee and could have affected the over 500,000 users of ESEA. <ref>https://www.theverge.com/2013/5/2/4292672/esea-gaming-network-bitcoin-botnet</ref> | ||
| + | |||
| + | Cryptocurrency exchanges, where users can trade cryptocurrencies for other assets have also become a popular target of hacks. In 2014, 744,408 bitcoins, worth US$350 million then, were stolen from what was then the largest bitcoin exchange, Mt. Gox. This later led to Mt. Gox declaring bankruptcy. <ref>https://www.wired.com/2014/02/bitcoins-mt-gox-implodes-2/</ref> In 2016, 119,756 bitcoins, worth US$72 million then and US$5 billion today, were stolen from the cryptocurrency exchange Bitfinex, which opted to split the loss between all users on its platform. <ref>https://www.nytimes.com/2016/08/04/business/dealbook/bitcoin-bitfinex-hacked.html</ref> | ||
| + | |||
| + | |||
| + | ==Regulatory efforts== | ||
| + | ===United States=== | ||
| + | The Stop Online Piracy Act (SOPA) was passed in 2011<ref>https://www.congress.gov/bill/112th-congress/house-bill/3261?q=hr3261</ref>, which aims to crack down on copyright infringement by restricting access to sites that host or facilitate the trading of pirated content.<ref>https://money.cnn.com/2012/01/17/technology/sopa_explained/index.htm</ref> However the act has since been postponed in 2021 due to backlash from the public.<ref>https://money.cnn.com/2012/01/20/technology/SOPA_PIPA_postponed/index.htm?iid=EL</ref> | ||
| + | |||
| + | The Securities and Exchange Commission has published a statement on DeFi Risks, Regulations, and Opportunities in 2021. The statement notes that "DeFi is a shared opportunity and challenge. Some DeFi projects fit neatly within our jurisdiction, and others may struggle to comply with the rules as currently applied. It is not enough to just say it is too hard to regulate or to say it is too hard to comply with regulations."<ref>https://www.sec.gov/news/statement/crenshaw-defi-20211109</ref> | ||
| + | |||
| + | Thirty-three states and Puerto Rico have pending legislation regarding cryptocurrencies in the 2021 legislative session. Seventeen states enacted legislation or adopted resolutions.<ref>https://www.ncsl.org/research/financial-services-and-commerce/cryptocurrency-2021-legislation.aspx</ref> On the federal level, the 117th Congress has introduced 35 bills in 2021 focused on cryptocurrency and blockchain policy, focused on regulation, applications, and central bank digital currency. The Infrastructure Investment and Jobs Act made headlines with language on cryptocurrency tax reporting.<ref>https://www.forbes.com/sites/jasonbrett/2021/12/27/in-2021-congress-has-introduced-35-bills-focused-on-us-crypto-policy/?sh=21c2a39ec9e8</ref> | ||
| + | However, this new legislation still has several open issues with regards to the wording in the act.<ref>https://www.natlawreview.com/article/cracking-crypto-code-new-reporting-obligations-current-developments-world-blockchain</ref> | ||
| + | |||
==Ethical concerns== | ==Ethical concerns== | ||
===Traceability=== | ===Traceability=== | ||
| − | The anonymity provided by decentralized financial platforms prevents value transactions from being tracked. KYC/AML laws, which would typically apply to conventional financial institutions, do not apply to these platforms. In addition, even though many cryptocurrency transactions are publicly viewable, there exists cryptocurrency shuffling protocols which allow users to hide their transactions by pooling multiple users' holdings into a shared account then splitting it in small amounts.<ref>Ruffing, Tim, Pedro Moreno-Sanchez, and Aniket Kate. "Coinshuffle: Practical decentralized coin mixing for bitcoin." European Symposium on Research in Computer Security. Springer, Cham, 2014.</ref> Such protocols significantly hinder third parties' abilities to trace the exchange of cryptocurrency between people, making it difficult to tie a particular transaction with the identities of the people involved, | + | The anonymity provided by decentralized financial platforms prevents value transactions from being tracked. KYC/AML laws, which would typically apply to conventional financial institutions, do not apply to these platforms. In addition, even though many cryptocurrency transactions are publicly viewable, there exists cryptocurrency shuffling protocols which allow users to hide their transactions by pooling multiple users' holdings into a shared account then splitting it in small amounts.<ref name=shuffle>Ruffing, Tim, Pedro Moreno-Sanchez, and Aniket Kate. "Coinshuffle: Practical decentralized coin mixing for bitcoin." European Symposium on Research in Computer Security. Springer, Cham, 2014.</ref> Such protocols significantly hinder third parties' abilities to trace the exchange of cryptocurrency between people, making it difficult to tie a particular transaction with the identities of the people involved. Thus, decentralized finance has become an ideal utility for illicit activities.<ref name=shuffle></ref> |
In 2017, it was estimated that bitcoin was involved in around $76 billion worth of illegal transactions, and that a quarter of bitcoin users were partaking in illegal activities.<ref name=foley>Foley, Sean, Jonathan R. Karlsen, and Tālis J. Putniņš. "Sex, drugs, and bitcoin: How much illegal activity is financed through cryptocurrencies?." The Review of Financial Studies 32.5 (2019): 1798-1853.</ref> Bitcoin enabled anonymous payments for dark web marketplaces, and became crucial to their operators' evasion of law enforcement. In the case of Silk Road, a marketplace which sold and shipped marijuana, LSD, and other drugs to US based customers.<ref>http://www.ibtimes.com/marijuana-lsd-now-illegal-drugs-delivered-your-doorstep-290021</ref> Its operator, Ross Ulbricht, evaded authorities for two years before being arrested, resulting in Silk Road shutting down.<ref>https://arstechnica.com/tech-policy/2013/10/how-the-feds-took-down-the-dread-pirate-roberts/</ref> | In 2017, it was estimated that bitcoin was involved in around $76 billion worth of illegal transactions, and that a quarter of bitcoin users were partaking in illegal activities.<ref name=foley>Foley, Sean, Jonathan R. Karlsen, and Tālis J. Putniņš. "Sex, drugs, and bitcoin: How much illegal activity is financed through cryptocurrencies?." The Review of Financial Studies 32.5 (2019): 1798-1853.</ref> Bitcoin enabled anonymous payments for dark web marketplaces, and became crucial to their operators' evasion of law enforcement. In the case of Silk Road, a marketplace which sold and shipped marijuana, LSD, and other drugs to US based customers.<ref>http://www.ibtimes.com/marijuana-lsd-now-illegal-drugs-delivered-your-doorstep-290021</ref> Its operator, Ross Ulbricht, evaded authorities for two years before being arrested, resulting in Silk Road shutting down.<ref>https://arstechnica.com/tech-policy/2013/10/how-the-feds-took-down-the-dread-pirate-roberts/</ref> | ||
Dark web marketplaces also pose a risk in that they lack accountability. The funds buyers use to pay for products is often held in escrow by the platform, which is then released to the seller upon successful a successful transaction. Disputes are resolved by marketplace administrators, and the losing side would have zero recourse as all parties remain anonymous. This leaves room for marketplace operators to perform "exit scams", whereby trading operations are ceased but escrow is not returned to their rightful owners. <ref name=foley></ref> | Dark web marketplaces also pose a risk in that they lack accountability. The funds buyers use to pay for products is often held in escrow by the platform, which is then released to the seller upon successful a successful transaction. Disputes are resolved by marketplace administrators, and the losing side would have zero recourse as all parties remain anonymous. This leaves room for marketplace operators to perform "exit scams", whereby trading operations are ceased but escrow is not returned to their rightful owners. <ref name=foley></ref> | ||
| + | |||
| + | Furthermore, the dark web is sometimes used for the distribution of child pornography and terrorism. A 2 year investigation by the Brazilian Federal Police, which began in 2014, resulted in the identification of 182 targets (out of almost 10,000 users), several prison sentences, search warrants and in the rescue of at least 6 children that were being abused.<ref>da Cunha, Bruno Requião, et al. "Assessing police topological efficiency in a major sting operation on the dark web." Scientific reports 10.1 (2020): 1-10.</ref> | ||
| + | |||
| + | Others have asserted that anecdotal evidence suggests that people often resort to using online anonymity services, like the Tor network, because they are concerned about the possibility of their government infringing their civil and political rights, especially in highly repressive regimes. Very high and very low levels of political repression tend to drive use of Tor the most.<ref>Jardine, Eric. "Tor, what is it good for? Political repression and the use of online anonymity-granting technologies." New media & society 20.2 (2018): 435-452.</ref><ref>Jardine, Eric. "Privacy, censorship, data breaches and Internet freedom: The drivers of support and opposition to Dark Web technologies." new media & society 20.8 (2018): 2824-2843.</ref> | ||
===Energy consumption=== | ===Energy consumption=== | ||
| + | Decentralized networks typically have several hundred, if not thousands, of computers online simultaneously. This presents an inefficiency in power consumption. In particular, cryptocurrency blockchains are secured by 'proof-of-work' algorithms which require intense, repetitive computation. This is necessary in order prevent the double spending of funds, and the tampering of past transactions. In 2017, it was estimated that the energy consumption of the Bitcoin network alone is in the range of 100-500MW. <ref>Vranken, Harald. "Sustainability of bitcoin and blockchains." Current opinion in environmental sustainability 28 (2017): 1-9.</ref> In November 2018, a new estimate put the power consumption of the bitcoin network at 5.22GW, marking a significant increase over previous years. Annual carbon emissions from bitcoin mining has been calculated to be between 22.0 and 22.9 MtCO2, an amount which is between that produced by Jordan and Sri Lanka and is comparable to the level of Kansas City. <ref name=stoll>Stoll, Christian, Lena Klaaßen, and Ulrich Gallersdörfer. "The carbon footprint of bitcoin." Joule 3.7 (2019): 1647-1661.</ref> Source of the this power have been speculated to include among other things, Chinese coal, Icelandic geothermal power, and Venezuelan subsidies.<ref>The Economist | ||
| + | www.economist.com/the-economist-explains/2018/04/03/why-are-venezuelans-mining-so-much-bitcoin (2018)</ref>. In 2022, the Cambridge Centre for Alternative Finance estimated bitcoin's energy usage to be 14.66GW. <ref>https://ccaf.io/cbeci/index</ref> At this power consumption, and the roughly 300,000 daily transactions on the network, each transaction requires approximately 1173KWh to process. <ref>https://www.ase.org/blog/congress-taking-note-cryptocurrencys-extraordinary-energy-use-heres-what-means#:~:text=Bitcoin%20is%20now%20estimated%20to,per%20transaction%20is%20approximately%20%24176.</ref> The energy required to validate just one Ethereum transaction could power a U.S. home for more than a week, the energy required for a Bitcoin transaction could power a home for more than 70 days.<ref>https://www.forbes.com/sites/tedknutson/2022/01/20/crypto-energy-consumption-enormous-but-it-neednt-be-congressional-panel-hears/?sh=6352df454abb</ref> | ||
| + | |||
| + | There have been proposals to extend the proof-of-work algorithm using proof-of-stake, which instead uses the bitcoin balances of users to secure the network rather than computation, thus cutting down on energy consumption. <ref>Bentov, Iddo, et al. "Proof of activity: Extending bitcoin's proof of work via proof of stake [extended abstract] y." ACM SIGMETRICS Performance Evaluation Review 42.3 (2014): 34-37.</ref> However, as of 2022, no such proposal has materialized as an official update to the bitcoin network. In contrast, the Ethereum network is planned to switch to the proof-of-stake algorithm in 2022, which is expected to cut environmental impact by 99%.<ref>https://www.cnbc.com/2021/10/28/what-to-know-about-ethereum-altair-upgrade-and-proof-of-stake.html</ref> | ||
| + | |||
| + | ===Hardware shortages=== | ||
| + | As cryptocurrency prices increased in 2020 and 2021, Ethereum mining in particular has been blamed for causing consumer graphics processing unit (GPU) shortages. Popular consumer GPUs have continued to sell out as fast as they're produced. <ref>https://www.tomshardware.com/news/gpu-shortages-worsen-cryptocurrency-coin-miners-ethereum</ref> This has to price increases of GPUs due to lack of supply. GPU scalpers, who buy many GPUs to sell at higher than the manufacture suggested retail price (MSRP), were estimated to have raked in US$61.5 million in sales in January 2021 <ref>https://www.pcmag.com/news/scalpers-have-sold-50000-nvidia-rtx-3000-gpus-through-ebay-stockx</ref>. As of January 2022, GPU prices on eBay are up roughly 100% compared to MSRP <ref>https://www.tomshardware.com/news/gpu-pricing-index</ref>. Everyday consumers have been forced to resort to using the service of bots in order to purchase GPUs at closer to retail prices, with bots competed against each other in purchasing GPUs on vendor websites. <ref>https://www.theverge.com/2021/12/3/22698588/falcodrin-gpu-hunters-nvidia-amd-graphics-card-tricks-bots-scalpers-miners-gamers</ref> In 2021, to alleviate the excess demand caused by Ethereum miners, GPU maker Nvidia stepped in and created a new line of GPUs which limited the performance of their GPUs in Ethereum mining, dubbed "LHR" GPUs. <ref name=nv>https://blogs.nvidia.com/blog/2021/05/18/lhr/</ref> Nvidia asserted that they "believe this additional step will get more GeForce cards at better prices into the hands of gamers everywhere."<ref name=nv></ref> However, the effectiveness of Nvidia's LHR GPUs has largely been considered a failure as it has been riddled with workarounds. <ref>https://www.pcmag.com/news/cryptocurrency-miners-nvidias-lite-hash-rate-limiter-did-little-to-stop</ref><ref>https://www.digitaltrends.com/computing/crypto-miners-bypass-nvidia-rtx-lhr-again/</ref> | ||
===Piracy=== | ===Piracy=== | ||
| + | Decentralized networks in the form of torrenting and IPFS have the potential to be used to share copyrighted works, leading to what is known as online piracy. Pirated content is not paid for, and the owners do not receive a direct for its usage. As such, digital piracy has posed a significant threat to the development of the software industry and the growth of the digital media industry. <ref>Yoon, Cheolho. "Theory of planned behavior and ethics theory in digital piracy: An integrated model." Journal of business ethics 100.3 (2011): 405-417.</ref> | ||
| − | == | + | In 1999, an audio streaming service, Napster, was launched. It resulted in an uptick of online piracy of music, as it allowed users to share content via peer-to-peer file sharing, much like modern day torrenting <ref>Giesler, Markus. "Consumer gift systems." Journal of consumer research 33.2 (2006): 283-290.</ref> Almost immediately, the Recording Industry Association of America filed a lawsuit against Napster<ref>https://www.wired.com/2009/12/1207riaa-sues-napster/</ref>, alleging that it was liable for contributory or vicarious copyright violations since it was allowing millions of users to obtain copyrighted music for free. By July 2000 however, a federal judge ordered that it be shut down, which Napster complied with in July 2001. <ref>https://abcnews.go.com/Technology/story?id=119627&page=1</ref> |
| − | == | + | In 2003, The Pirate Bay was launched, and began serving as an online library of digital content of entertainment media and software. Although efforts have been made by governments to block access to The Pirate Bay, proxies which bypass these censorship attempts emerged. <ref>https://torrentfreak.com/pirate-bay-censorship-backfires-as-new-proxies-bloom-121222/</ref> |
| + | |||
| + | Google's executive chairman in 2011, Eric Schmidt, has regarded governments' efforts to prevent access to illicit filesharing websites could set a "disastrous precedent" for freedom of speech. Schmidt likened such efforts as being equivalent to that of China's great firewall, which monitors and filters internet traffic crossing China's international borders.<ref>https://www.theguardian.com/technology/2011/may/18/google-eric-schmidt-piracy</ref> | ||
| + | |||
| + | A similar filesharing service, but focusing on providing access to academic journals and books, Sci-Hub, was launched in 2011 in response to high cost of research papers behind paywalls.<ref>Himmelstein, D. S., et al. "Sci-Hub provides access to nearly all scholarly literature. eLife, 7." (2018).</ref> As of February 2022, Sci-Hub provides access to more than 88,485,426 papers.<ref>https://sci-hub.se/</ref> A spokesperson for the International Association of Scientific, Technical and Medical Publishers has noted that “Sci-Hub does not add any value to the scholarly community. It neither fosters scientific advancement nor does it value researchers’ achievements. It is simply a place for someone to go to download stolen content and then leave.”<ref name=ntr17>Schiermeier, Quirin. "US court grants Elsevier millions in damages from Sci-Hub." Nature News (2017).</ref> Journal publisher Elsevier has claimed that it was losing hundreds to thousands of dollars for each of its articles which are pirated on Sci-Hub, and have filed a lawsuit to shut Sci-Hub down.<ref>https://americanlibrariesmagazine.org/2016/05/31/why-sci-hub-matters/</ref> Elsevier also named Library Genesis as a defendant in the same lawsuit.<ref name=ntr17></ref> Though the lawsuit was resolved in Elsevier's favor, awarding them $15 million from Sci-Hub, the fine has not been paid as of December 2021.<ref>Else, Holly. "What Sci-Hub’s latest court battle means for research." Nature 600.7889 (2021): 370-371.</ref> | ||
| + | |||
| + | In the first nine months of 2021, at least 132 billion visits were made to pirate sites, which represents a 16% increase compared to the same period in the previous year. 50% of traffic represented TV piracy sites, 23% represented publishing, films represented 11%, music represented 8% and software represented 7%.<ref>https://torrentfreak.com/pirate-site-traffic-surged-in-2021-research-finds-220127/</ref> | ||
| + | |||
| + | ===Permanence=== | ||
| + | Torrenting and IPFS allows for a single file to exist across multiple computers. This makes the deletion of files from the internet difficult, if not impossible. In 2014, a collection of private pictures of celebrities was obtained and leaked to the internet, in an event known as Celebgate.<ref>https://www.washingtonpost.com/news/morning-mix/wp/2014/09/02/the-shadowy-world-of-4chan-the-shock-post-site-that-hosted-the-private-jennifer-lawrence-photos/</ref> The photos were initially spread through link-sharing websites such as Reddit, but soon administrators of the site shut down the activity due to concerns of child pornography being present within the collection. <ref>https://www.reddit.com/r/announcements/comments/2fpdax/time_to_talk/</ref> However, this collection was also disseminated through the use of torrents,<ref>Lawson, Caitlin. "Cascading exploitations: The celebrity nude photo hack as digital phenomenon." AoIR Selected Papers of Internet Research (2015).</ref> which have no governing authority which can prevent the spread of its contents. | ||
| − | |||
==References== | ==References== | ||
Latest revision as of 21:49, 11 February 2022
Decentralized networks are systems which inherently have no central authority or governance. These systems often operate on individual computers spread across the globe, interconnected by the Internet, also known as peer-to-peer networking. These computers act in unison towards a common goal. [1]
Computers within decentralized networks are capable of operating independently of each other.[2] As a result, the variety of services and applications built on decentralized networks are often difficult for third parties, such as governments, to shut down. As such, ethical concerns have arisen from the usage of decentralized networks, with most directly related to the lack of regulation on it. The applications of it include cryptocurrencies, dark web marketplaces, and the dissemination of data, which calls into question the lack of traceability and accountability in these systems as they can be used for illicit activities. Energy consumption concerns and computer hardware shortages have also been attributed to cryptocurrency mining.
Contents
Notable applications
Decentralized finance (DeFi)
Decentralized finance applications use blockchain technology to provide access to financial instruments without the need of going through conventional financial intermediaries such as banks, brokerages, or exchanges. People may trade digital assets on these platforms much like in physical markets.[3] However, DeFi allows for pseudo-anonymous cryptocurrency trading, market speculation based on derivates, borrowing and lending of cryptocurrencies.[4]
Decentralized finance operates on smart contracts, which are essentially software made to run on decentralized networks such as the Ethereum blockchain. Since the blockchain is publicly accessible, anyone may audit the smart contracts used in DeFi to ensure it is not malicious.[5] This presents a stark contrast from traditional financial institutions, which typically do not release the source code of banking software, but also presents risk in that security vulnerabilities present in smart contracts may be exploited for individual gain.
Cryptocurrency
Cryptocurrencies are digital assets designed to be virtual stores of value which are independent of centralized governance. Transactions involving cryptocurrencies are typically stored on a digital ledger, with the transactions being processed based on a consensus model within the cryptocurrency's decentralized network, with proof-of-work being the dominant protocol.[6]
The first cryptocurrency, Bitcoin, was released in 2009, and as of February 2022 has a market capitalization of US$838 billion.[7] Numerous other cryptocurrencies, known as altcoins, have emerged since Bitcoin, seeking to provide additional or improved functionality over Bitcoin. Examples include Ethereum which has the capability of running smart contracts, Ripple which provides real-time settlements, and ZCash which provides true anonymity for transactions.
Cryptocurrencies operate on a consensus model to decide parameters of the system, such as how often new currency is created and how much is created. The decentralized network of users, each have a proportional share in deciding the consensus by proxy of their computing resources, or ownership of the currency.[6] Cryptocurrencies are defined by the parameters of the network which has majority consensus, so any diverging networks would typically cease to be recognized by the community and thus lose value. Occasionally, such as in the case of the Ethereum and Ethereum Classic networks, the consensus diverges but both are still recognized as valid networks and retain some value, such an event is known as a chain split.[8]
Cryptocurrencies networks have also enabled the creation and trading of non-fungible tokens (NFTs), which are supposed to represent rights to digital assets such as artwork, pictures, or videos. NFTs are stored on cryptocurrency blockchains, which are used to verify ownership of the NFT. [9]
File sharing networks
Decentralized networks can be used to run file sharing services which are immensely redundant and thus provide high availability. The essential concept behind these networks is that many computers each store a copy of a file, and transmit it (or a part thereof) to other computers which request the same file.
BitTorrent
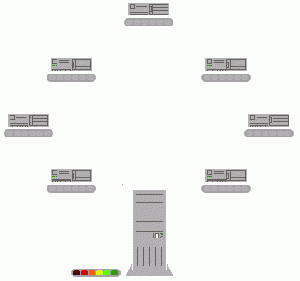
BitTorrent is a peer-to-peer file sharing protocol which allows for electronic data distribution over a decentralized network. The protocol is designed such that it reduces the computing resources needed to distribute large files. Files are segmented, then distributed to different computers which then simultaneously upload segments others need and download segments it needs from other computers. Doing so reduces the impact on global internet traffic, as users may download files from a more local source rather than a server located in distant geographic regions.
In 2019, the BitTorrent protocol accounted for 2.46% of downstream, and 27.58% of upstream internet traffic. [10]
InterPlanetary File System (IPFS)
IPFS is a peer-to-peer decentralized network used to preserve and share data in a distributed file system. The data stored on it is duplicated across several computers on the network, so if one computer goes offline, the data is still accessible. It is designed as an easy to use, global store of information, with a defined naming scheme, IPNS, to uniquely locate items by.[11] It has been used for archival efforts such as for the Genesis Library, which archives books and journals.[12] Similar to BitTorrent, users have the option of preserving media it accesses and redistributing it to others.
Onion Routing
Onion routing is a communication protocol used to communicate anonymously and securely on computer networks, utilizing a decentralized onion network. Instead of communicating directly between two computers, onion routing encapsulates the data in several layers of encryption, and passes it on through a series of computers on the onion network. As the data transits through each computer on the way to its destination, a layer of the encryption is 'peeled' away, revealing the next destination of the data. This ensures the intermediary computers do not simultaneously know the initial source and the final destination of the data it is transmitting, protecting the anonymity of the sender from the intermediaries. [13]
Tor and the Dark Web
Tor, which is an abbreviation of The Onion Router, is a free, open-source implementation of onion routing. For ease of use, Tor has been implemented into a web browser based on Chromium, the Tor Browser. It allows users to visit internet websites anonymously, and prevents eavesdropping by third parties. Content which is region locked, or blocked by local governments can also be accessed through the use of Tor.[14]
The use of a Tor-enabled network also allows users to access the Dark Web, a collection of websites not normally accessible via the Internet. These websites are hosted on servers whose physical locations are effectively hidden due to onion routing.[15]
Security concerns
The open source nature of decentralized networks allows malicious actors to find and exploit vulnerabilities present on the network. In 2016, a vulnerability in the DAO's smart contract on the Ethereum network allowed attackers to drain 3.6 million Ether out of the DAO's accounts. This caused the price of ether to drop from $20 to $13 and triggered proposals of a soft-fork or hard-fork to reverse the attack. [16]
Cryptocurrency "mining", the process of exchanging computing resources for a cryptocurrency can be done anonymously. In 2013, ESEA, a private CS:GO server, which requires its users to install an anti-cheat application on their computers to access game servers, was exposed for embedding a bitcoin miner within the anti-cheat application. The miner was embedded by a single rogue employee and could have affected the over 500,000 users of ESEA. [17]
Cryptocurrency exchanges, where users can trade cryptocurrencies for other assets have also become a popular target of hacks. In 2014, 744,408 bitcoins, worth US$350 million then, were stolen from what was then the largest bitcoin exchange, Mt. Gox. This later led to Mt. Gox declaring bankruptcy. [18] In 2016, 119,756 bitcoins, worth US$72 million then and US$5 billion today, were stolen from the cryptocurrency exchange Bitfinex, which opted to split the loss between all users on its platform. [19]
Regulatory efforts
United States
The Stop Online Piracy Act (SOPA) was passed in 2011[20], which aims to crack down on copyright infringement by restricting access to sites that host or facilitate the trading of pirated content.[21] However the act has since been postponed in 2021 due to backlash from the public.[22]
The Securities and Exchange Commission has published a statement on DeFi Risks, Regulations, and Opportunities in 2021. The statement notes that "DeFi is a shared opportunity and challenge. Some DeFi projects fit neatly within our jurisdiction, and others may struggle to comply with the rules as currently applied. It is not enough to just say it is too hard to regulate or to say it is too hard to comply with regulations."[23]
Thirty-three states and Puerto Rico have pending legislation regarding cryptocurrencies in the 2021 legislative session. Seventeen states enacted legislation or adopted resolutions.[24] On the federal level, the 117th Congress has introduced 35 bills in 2021 focused on cryptocurrency and blockchain policy, focused on regulation, applications, and central bank digital currency. The Infrastructure Investment and Jobs Act made headlines with language on cryptocurrency tax reporting.[25] However, this new legislation still has several open issues with regards to the wording in the act.[26]
Ethical concerns
Traceability
The anonymity provided by decentralized financial platforms prevents value transactions from being tracked. KYC/AML laws, which would typically apply to conventional financial institutions, do not apply to these platforms. In addition, even though many cryptocurrency transactions are publicly viewable, there exists cryptocurrency shuffling protocols which allow users to hide their transactions by pooling multiple users' holdings into a shared account then splitting it in small amounts.[27] Such protocols significantly hinder third parties' abilities to trace the exchange of cryptocurrency between people, making it difficult to tie a particular transaction with the identities of the people involved. Thus, decentralized finance has become an ideal utility for illicit activities.[27]
In 2017, it was estimated that bitcoin was involved in around $76 billion worth of illegal transactions, and that a quarter of bitcoin users were partaking in illegal activities.[28] Bitcoin enabled anonymous payments for dark web marketplaces, and became crucial to their operators' evasion of law enforcement. In the case of Silk Road, a marketplace which sold and shipped marijuana, LSD, and other drugs to US based customers.[29] Its operator, Ross Ulbricht, evaded authorities for two years before being arrested, resulting in Silk Road shutting down.[30]
Dark web marketplaces also pose a risk in that they lack accountability. The funds buyers use to pay for products is often held in escrow by the platform, which is then released to the seller upon successful a successful transaction. Disputes are resolved by marketplace administrators, and the losing side would have zero recourse as all parties remain anonymous. This leaves room for marketplace operators to perform "exit scams", whereby trading operations are ceased but escrow is not returned to their rightful owners. [28]
Furthermore, the dark web is sometimes used for the distribution of child pornography and terrorism. A 2 year investigation by the Brazilian Federal Police, which began in 2014, resulted in the identification of 182 targets (out of almost 10,000 users), several prison sentences, search warrants and in the rescue of at least 6 children that were being abused.[31]
Others have asserted that anecdotal evidence suggests that people often resort to using online anonymity services, like the Tor network, because they are concerned about the possibility of their government infringing their civil and political rights, especially in highly repressive regimes. Very high and very low levels of political repression tend to drive use of Tor the most.[32][33]
Energy consumption
Decentralized networks typically have several hundred, if not thousands, of computers online simultaneously. This presents an inefficiency in power consumption. In particular, cryptocurrency blockchains are secured by 'proof-of-work' algorithms which require intense, repetitive computation. This is necessary in order prevent the double spending of funds, and the tampering of past transactions. In 2017, it was estimated that the energy consumption of the Bitcoin network alone is in the range of 100-500MW. [34] In November 2018, a new estimate put the power consumption of the bitcoin network at 5.22GW, marking a significant increase over previous years. Annual carbon emissions from bitcoin mining has been calculated to be between 22.0 and 22.9 MtCO2, an amount which is between that produced by Jordan and Sri Lanka and is comparable to the level of Kansas City. [35] Source of the this power have been speculated to include among other things, Chinese coal, Icelandic geothermal power, and Venezuelan subsidies.[36]. In 2022, the Cambridge Centre for Alternative Finance estimated bitcoin's energy usage to be 14.66GW. [37] At this power consumption, and the roughly 300,000 daily transactions on the network, each transaction requires approximately 1173KWh to process. [38] The energy required to validate just one Ethereum transaction could power a U.S. home for more than a week, the energy required for a Bitcoin transaction could power a home for more than 70 days.[39]
There have been proposals to extend the proof-of-work algorithm using proof-of-stake, which instead uses the bitcoin balances of users to secure the network rather than computation, thus cutting down on energy consumption. [40] However, as of 2022, no such proposal has materialized as an official update to the bitcoin network. In contrast, the Ethereum network is planned to switch to the proof-of-stake algorithm in 2022, which is expected to cut environmental impact by 99%.[41]
Hardware shortages
As cryptocurrency prices increased in 2020 and 2021, Ethereum mining in particular has been blamed for causing consumer graphics processing unit (GPU) shortages. Popular consumer GPUs have continued to sell out as fast as they're produced. [42] This has to price increases of GPUs due to lack of supply. GPU scalpers, who buy many GPUs to sell at higher than the manufacture suggested retail price (MSRP), were estimated to have raked in US$61.5 million in sales in January 2021 [43]. As of January 2022, GPU prices on eBay are up roughly 100% compared to MSRP [44]. Everyday consumers have been forced to resort to using the service of bots in order to purchase GPUs at closer to retail prices, with bots competed against each other in purchasing GPUs on vendor websites. [45] In 2021, to alleviate the excess demand caused by Ethereum miners, GPU maker Nvidia stepped in and created a new line of GPUs which limited the performance of their GPUs in Ethereum mining, dubbed "LHR" GPUs. [46] Nvidia asserted that they "believe this additional step will get more GeForce cards at better prices into the hands of gamers everywhere."[46] However, the effectiveness of Nvidia's LHR GPUs has largely been considered a failure as it has been riddled with workarounds. [47][48]
Piracy
Decentralized networks in the form of torrenting and IPFS have the potential to be used to share copyrighted works, leading to what is known as online piracy. Pirated content is not paid for, and the owners do not receive a direct for its usage. As such, digital piracy has posed a significant threat to the development of the software industry and the growth of the digital media industry. [49]
In 1999, an audio streaming service, Napster, was launched. It resulted in an uptick of online piracy of music, as it allowed users to share content via peer-to-peer file sharing, much like modern day torrenting [50] Almost immediately, the Recording Industry Association of America filed a lawsuit against Napster[51], alleging that it was liable for contributory or vicarious copyright violations since it was allowing millions of users to obtain copyrighted music for free. By July 2000 however, a federal judge ordered that it be shut down, which Napster complied with in July 2001. [52]
In 2003, The Pirate Bay was launched, and began serving as an online library of digital content of entertainment media and software. Although efforts have been made by governments to block access to The Pirate Bay, proxies which bypass these censorship attempts emerged. [53]
Google's executive chairman in 2011, Eric Schmidt, has regarded governments' efforts to prevent access to illicit filesharing websites could set a "disastrous precedent" for freedom of speech. Schmidt likened such efforts as being equivalent to that of China's great firewall, which monitors and filters internet traffic crossing China's international borders.[54]
A similar filesharing service, but focusing on providing access to academic journals and books, Sci-Hub, was launched in 2011 in response to high cost of research papers behind paywalls.[55] As of February 2022, Sci-Hub provides access to more than 88,485,426 papers.[56] A spokesperson for the International Association of Scientific, Technical and Medical Publishers has noted that “Sci-Hub does not add any value to the scholarly community. It neither fosters scientific advancement nor does it value researchers’ achievements. It is simply a place for someone to go to download stolen content and then leave.”[57] Journal publisher Elsevier has claimed that it was losing hundreds to thousands of dollars for each of its articles which are pirated on Sci-Hub, and have filed a lawsuit to shut Sci-Hub down.[58] Elsevier also named Library Genesis as a defendant in the same lawsuit.[57] Though the lawsuit was resolved in Elsevier's favor, awarding them $15 million from Sci-Hub, the fine has not been paid as of December 2021.[59]
In the first nine months of 2021, at least 132 billion visits were made to pirate sites, which represents a 16% increase compared to the same period in the previous year. 50% of traffic represented TV piracy sites, 23% represented publishing, films represented 11%, music represented 8% and software represented 7%.[60]
Permanence
Torrenting and IPFS allows for a single file to exist across multiple computers. This makes the deletion of files from the internet difficult, if not impossible. In 2014, a collection of private pictures of celebrities was obtained and leaked to the internet, in an event known as Celebgate.[61] The photos were initially spread through link-sharing websites such as Reddit, but soon administrators of the site shut down the activity due to concerns of child pornography being present within the collection. [62] However, this collection was also disseminated through the use of torrents,[63] which have no governing authority which can prevent the spread of its contents.
References
- ↑ Kremenova, Iveta, and Milan Gajdos. "Decentralized networks: The future internet." Mobile Networks and Applications 24.6 (2019): 2016-2023.
- ↑ https://www.gemini.com/cryptopedia/blockchain-network-decentralized-distributed-centralized
- ↑ https://www.bloomberg.com/news/articles/2020-08-26/why-defi-utopia-would-be-finance-without-financiers-quicktake
- ↑ https://www.forbes.com/sites/forbestechcouncil/2021/11/17/three-big-myths-about-decentralized-finance/?sh=1ef717557c54
- ↑ https://ethereum.org/en/defi/
- ↑ 6.0 6.1 Judmayer, Aljosha, et al. "Blocks and chains: introduction to bitcoin, cryptocurrencies, and their consensus mechanisms." Synthesis Lectures on Information Security, Privacy, & Trust 9.1 (2017): 1-123.
- ↑ https://finance.yahoo.com/quote/BTC-USD/
- ↑ https://coinmarketcap.com/alexandria/glossary/chain-split
- ↑ Wilson, Kathleen Bridget, Adam Karg, and Hadi Ghaderi. "Prospecting non-fungible tokens in the digital economy: Stakeholders and ecosystem, risk and opportunity." Business Horizons (2021).
- ↑ Marozzo, Fabrizio, Domenico Talia, and Paolo Trunfio. "A sleep‐and‐wake technique for reducing energy consumption in BitTorrent networks." Concurrency and Computation: Practice and Experience 32.14 (2020): e5723.
- ↑ https://ipfs.io/
- ↑ https://web.archive.org/web/20201127164841/http://freeread.org/ipfs/
- ↑ Syverson, Paul, D. Goldschlag, and M. Reed. "Onion routing for anonymous and private internet connections." Communications of the ACM 42.2 (1999): 5.
- ↑ https://www.torproject.org/about/history/
- ↑ Jardine, Eric. "The Dark Web dilemma: Tor, anonymity and online policing." Global Commission on Internet Governance Paper Series 21 (2015).
- ↑ https://www.coindesk.com/learn/2016/06/25/understanding-the-dao-attack/
- ↑ https://www.theverge.com/2013/5/2/4292672/esea-gaming-network-bitcoin-botnet
- ↑ https://www.wired.com/2014/02/bitcoins-mt-gox-implodes-2/
- ↑ https://www.nytimes.com/2016/08/04/business/dealbook/bitcoin-bitfinex-hacked.html
- ↑ https://www.congress.gov/bill/112th-congress/house-bill/3261?q=hr3261
- ↑ https://money.cnn.com/2012/01/17/technology/sopa_explained/index.htm
- ↑ https://money.cnn.com/2012/01/20/technology/SOPA_PIPA_postponed/index.htm?iid=EL
- ↑ https://www.sec.gov/news/statement/crenshaw-defi-20211109
- ↑ https://www.ncsl.org/research/financial-services-and-commerce/cryptocurrency-2021-legislation.aspx
- ↑ https://www.forbes.com/sites/jasonbrett/2021/12/27/in-2021-congress-has-introduced-35-bills-focused-on-us-crypto-policy/?sh=21c2a39ec9e8
- ↑ https://www.natlawreview.com/article/cracking-crypto-code-new-reporting-obligations-current-developments-world-blockchain
- ↑ 27.0 27.1 Ruffing, Tim, Pedro Moreno-Sanchez, and Aniket Kate. "Coinshuffle: Practical decentralized coin mixing for bitcoin." European Symposium on Research in Computer Security. Springer, Cham, 2014.
- ↑ 28.0 28.1 Foley, Sean, Jonathan R. Karlsen, and Tālis J. Putniņš. "Sex, drugs, and bitcoin: How much illegal activity is financed through cryptocurrencies?." The Review of Financial Studies 32.5 (2019): 1798-1853.
- ↑ http://www.ibtimes.com/marijuana-lsd-now-illegal-drugs-delivered-your-doorstep-290021
- ↑ https://arstechnica.com/tech-policy/2013/10/how-the-feds-took-down-the-dread-pirate-roberts/
- ↑ da Cunha, Bruno Requião, et al. "Assessing police topological efficiency in a major sting operation on the dark web." Scientific reports 10.1 (2020): 1-10.
- ↑ Jardine, Eric. "Tor, what is it good for? Political repression and the use of online anonymity-granting technologies." New media & society 20.2 (2018): 435-452.
- ↑ Jardine, Eric. "Privacy, censorship, data breaches and Internet freedom: The drivers of support and opposition to Dark Web technologies." new media & society 20.8 (2018): 2824-2843.
- ↑ Vranken, Harald. "Sustainability of bitcoin and blockchains." Current opinion in environmental sustainability 28 (2017): 1-9.
- ↑ Stoll, Christian, Lena Klaaßen, and Ulrich Gallersdörfer. "The carbon footprint of bitcoin." Joule 3.7 (2019): 1647-1661.
- ↑ The Economist www.economist.com/the-economist-explains/2018/04/03/why-are-venezuelans-mining-so-much-bitcoin (2018)
- ↑ https://ccaf.io/cbeci/index
- ↑ https://www.ase.org/blog/congress-taking-note-cryptocurrencys-extraordinary-energy-use-heres-what-means#:~:text=Bitcoin%20is%20now%20estimated%20to,per%20transaction%20is%20approximately%20%24176.
- ↑ https://www.forbes.com/sites/tedknutson/2022/01/20/crypto-energy-consumption-enormous-but-it-neednt-be-congressional-panel-hears/?sh=6352df454abb
- ↑ Bentov, Iddo, et al. "Proof of activity: Extending bitcoin's proof of work via proof of stake [extended abstract] y." ACM SIGMETRICS Performance Evaluation Review 42.3 (2014): 34-37.
- ↑ https://www.cnbc.com/2021/10/28/what-to-know-about-ethereum-altair-upgrade-and-proof-of-stake.html
- ↑ https://www.tomshardware.com/news/gpu-shortages-worsen-cryptocurrency-coin-miners-ethereum
- ↑ https://www.pcmag.com/news/scalpers-have-sold-50000-nvidia-rtx-3000-gpus-through-ebay-stockx
- ↑ https://www.tomshardware.com/news/gpu-pricing-index
- ↑ https://www.theverge.com/2021/12/3/22698588/falcodrin-gpu-hunters-nvidia-amd-graphics-card-tricks-bots-scalpers-miners-gamers
- ↑ 46.0 46.1 https://blogs.nvidia.com/blog/2021/05/18/lhr/
- ↑ https://www.pcmag.com/news/cryptocurrency-miners-nvidias-lite-hash-rate-limiter-did-little-to-stop
- ↑ https://www.digitaltrends.com/computing/crypto-miners-bypass-nvidia-rtx-lhr-again/
- ↑ Yoon, Cheolho. "Theory of planned behavior and ethics theory in digital piracy: An integrated model." Journal of business ethics 100.3 (2011): 405-417.
- ↑ Giesler, Markus. "Consumer gift systems." Journal of consumer research 33.2 (2006): 283-290.
- ↑ https://www.wired.com/2009/12/1207riaa-sues-napster/
- ↑ https://abcnews.go.com/Technology/story?id=119627&page=1
- ↑ https://torrentfreak.com/pirate-bay-censorship-backfires-as-new-proxies-bloom-121222/
- ↑ https://www.theguardian.com/technology/2011/may/18/google-eric-schmidt-piracy
- ↑ Himmelstein, D. S., et al. "Sci-Hub provides access to nearly all scholarly literature. eLife, 7." (2018).
- ↑ https://sci-hub.se/
- ↑ 57.0 57.1 Schiermeier, Quirin. "US court grants Elsevier millions in damages from Sci-Hub." Nature News (2017).
- ↑ https://americanlibrariesmagazine.org/2016/05/31/why-sci-hub-matters/
- ↑ Else, Holly. "What Sci-Hub’s latest court battle means for research." Nature 600.7889 (2021): 370-371.
- ↑ https://torrentfreak.com/pirate-site-traffic-surged-in-2021-research-finds-220127/
- ↑ https://www.washingtonpost.com/news/morning-mix/wp/2014/09/02/the-shadowy-world-of-4chan-the-shock-post-site-that-hosted-the-private-jennifer-lawrence-photos/
- ↑ https://www.reddit.com/r/announcements/comments/2fpdax/time_to_talk/
- ↑ Lawson, Caitlin. "Cascading exploitations: The celebrity nude photo hack as digital phenomenon." AoIR Selected Papers of Internet Research (2015).