Difference between revisions of "Iris Recognition"
(→History) |
(→Ethical Issues) |
||
| (67 intermediate revisions by 14 users not shown) | |||
| Line 1: | Line 1: | ||
| − | '''Iris recognition''' is a [ | + | '''Iris recognition''' is a [[Wikipedia:Biometrics|biometric]] verification method that utilizes the unique pattern of an individual's [https://en.wikipedia.org/wiki/Iris_(anatomy) iris], the colored circular structure in the eye, to confirm one’s identity. The authentication process begins by scanning an iris at a reasonable distance with near-infrared light to construct a template and comparing the acquired template to the individual's already existing templates in a database<ref>Wildes, Richard. Iris Recognition: an Emerging Biometric Technology - IEEE Journals & Magazine, Sept. 1997, ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=628669.</ref>. |
| − | Similar to [ | + | Similar to [[face recognition]] and [[Wikipedia:Fingerprint|fingerprinting]], [[Wikipedia:Iris_recognition|iris recognition]] uses human biological characteristics to distinguish one person from another for security purposes and efficiency. It is sometimes preferred over both face recognition and fingerprinting techniques due to the more unique structural attributes of the iris. As iris recognition is becoming more widely used, ethical concerns of identity, [[Wikipedia:Privacy|privacy]], and [[Wikipedia:Consent|consent]] regarding the issue have arisen. |
[[File:iris.jpg|thumbnail|right|iris recognition <ref>Thakkar, Danny. “Retinal vs. Iris Recognition: Your Eyes Can Get You Identified?” Bayometric, Bayometric, 8 Aug. 2018, www.bayometric.com/retinal-vs-iris-recognition/.</ref>]] | [[File:iris.jpg|thumbnail|right|iris recognition <ref>Thakkar, Danny. “Retinal vs. Iris Recognition: Your Eyes Can Get You Identified?” Bayometric, Bayometric, 8 Aug. 2018, www.bayometric.com/retinal-vs-iris-recognition/.</ref>]] | ||
| + | |||
==History== | ==History== | ||
| − | + | [[Wikipedia:John Daugman|John Daugman]] is the first person credited with creating iris recognition algorithms with the ability to be used in new technologies. In his paper, "How iris recognition works", his statistical analysis of iris patterns successfully distinguished and identified individuals and with high accuracy<ref name="Daugman"> J. Daugman, "How iris recognition works," in IEEE Transactions on Circuits and Systems for Video Technology, vol. 14, no. 1, pp. 21-30, Jan. 2004. doi: 10.1109/TCSVT.2003.818350</ref>. These findings paved the way for iris recognition technologies to be used by companies across different industries. Currently, the companies Iris ID Systems, CMITECH, Princeton Identity, Sensor Access Technology, Argus Global Limited, and EFG GZ all specialize in recognition technology utilizing some version of these iris identification algorithms<ref name="his iris">"Iris Recognition". IFSEC Global Directory. https://directory.ifsecglobal.com/iris-recognition-code004809.html</ref>. | |
| − | Since the adoption of iris recognition technology and | + | Since the adoption of iris recognition technology and the value of being able to produce it has risen, iris recognition has found many different usages with potential for monetary gains. Banks and various financial institutions have implemented iris scanning over other more traditional forms of [[Wikipedia:Authentication|authentication]] due to its convenience and higher level of security<ref name="usage">Thakkar, Danny. “Biometric Iris Recognition and Its Application.” Bayometric, Bayometric, 15 Aug. 2018, www.bayometric.com/biometric-iris-recognition-application/.</ref>. Phone companies like Samsung have even employed iris scanning as a means of accessing one's phone. This technology has also been found to be increasingly helpful in law and border enforcement agencies, which prioritize quick and correct identification of individuals.<ref name="usage"></ref>. |
| + | |||
| + | ====Examples==== | ||
| + | '''TSB Bank''' in the United Kingdom was one of the first banks, in September 2016, to incorporate Iris Recognition into their day to day banking operations. In order to log into the TSB application, you are now able to just glance at your mobile device. Iris Recognition is the next step in login technology after mobile fingerprints. Compared to the four traits the fingerprint scans for, Iris recognition is able to recognize two hundred and sixty-six traits, making it much more accurate than fingerprint scanning. <ref> "TSB to roll out iris scanning tech" Rory Cellan-Jones, July 20 2016. https://www.bbc.com/news/technology-40663365</ref> | ||
| + | |||
| + | '''Apple's''' iPhone XR includes a facial recognition software which incorporates iris recognition. Like the banks' technology, you no longer have to touch your phone to utilize the device. While facial recognition, used also by companies like Facebook and social media platforms, extends beyond iris recognition, the line between the two is being crossed as iris recognition has shown to be more accurate. | ||
| + | |||
| + | '''Country border controls''' also have the ability to utilize this technology. The United Arab Emirates employs this when any passengers enter through air, land or sea. <ref> "IRIS RECOGNITION BORDER-CROSSING SYSTEM IN THE UAE"https://trid.trb.org/view/741851 </ref> | ||
| + | |||
| + | '''Airport Security''' is now utilizing iris recognition. A company called Clear has come into play in airports in attempts to simplify and save time. Customer's eyes are scanned as a means of identity verification, saving them the time of having to take out their ID and have it checked by a TSA officer.<ref name = "clear"> "A Full Guide to Clear Airport Security: How It Works and Where You Can Use it" https://www.travelandleisure.com/airlines-airports/clear-airport-security </ref> | ||
| + | |||
| + | '''Major League Baseball games''' are now using this similar technology after partnering with Clear. Just as Clear is used in airports so that travelers can skip long lines, the same is going for MLB games. People can also use this technology as age verification to purchase alcohol in some stadiums. <ref name = "clear" /> | ||
| + | |||
| + | '''Google''' uses Iris Scanning as a component of its security measures used to secure its Data Centers.<ref>"Security and Data Protection in a Google Data Center | ||
| + | ", G Suite's Official YouTube https://www.youtube.com/watch?v=cLory3qLoY8</ref> | ||
| + | |||
| + | '''FBI''' is increasing its use for iris recognition for criminal investigations. Acting director of the FBI’s Criminal Justice Information Services Division, Kimberly Del Greco, has announced that the FBI Criminal Justice Information Services Division (CJIS) has been given permission to look further into expanding iris recognition technology. Previously, there was only a pilot program for this kind of technology. Next Generation Identification is where the FBI keeps fingerprint and facial records. The department wishes to eventually move iris recognition into the NGI soon. The argument for using this sort of technology is that fingerprints are not always at crime scenes, so with some improved technology, a person's eye could reveal crucial information using cameras. Leslie Cavis, from the FBI, has said that “There are people who are threats to our country, and we need to do everything that we can to circumvent those threats. Biometrics is helping us to do that in a major way.” <ref> Young, Charles. “FBI to Expand Iris Recognition Tech at Clarksburg, WV Campus.” WV News, 20 Apr. 2019, www.wvnews.com/news/wvnews/fbi-to-expand-iris-recognition-tech-at-clarksburg-wv-campus/article_d7d13a6d-d217-54c2-bce1-e80168c8f71b.html.</ref> | ||
| + | |||
| + | ==How Iris Recognition Works== | ||
| + | Iris recognition is a [[Wikipedia:Biometrics|biometric]] identification method that uses mathematical techniques in order to recognize patters on video images. Iris recognition works in two stages: | ||
| + | #Enrollment. The enrollment process is the first step in iris recognition and requires an individual to stand in front of a camera that digitally photographs their iris with a combination of ordinary light and invisible infrared light. The infrared light is an important step due the fact that the light is able to pick up on features of the eye that cannot be properly done with ordinary light. After eliminating unnecessary aspects of the photo, such as eyelashes, the computer system analyzes 240 distinct features that make every iris unique. This data is then stored into a database with other identifying information about you. | ||
| + | #Verification. The verification process occurs when an individual stands in front of a scanner in order to verify identification. The scanner takes a photograph of your eyes and extracts a number code that it can compare to other codes in its database. If your scan data is the same as the data that is in the database, you pass the scan, but if it is not, then you fail. | ||
== Advantages == | == Advantages == | ||
| − | === High Accuracy === | + | === High Accuracy Versus Other Biometric Methods === |
| − | Iris recognition is not guaranteed to be | + | Iris recognition is not guaranteed to be entirely correct or effective every time. Factors like lighting and different algorithms may affect accuracy. However, there is less room for deceit because it is more difficult to alter iris than other body parts. Iris traits are more permanent and stable.<ref>Jain, Anil K., and Sharath Pankanti. “BEYOND FINGERPRINTING.” Scientific American, vol. 299, no. 3, 2008, pp. 78–81. JSTOR, www.jstor.org/stable/26000805.</ref> An additional advantage of iris recognition technology is that it can also be used even when contacts are in or glasses are on. |
| − | + | Facial recognition has a high-error rate because facial features change across different environmental conditions and there can be almost exact faces existing among people such as identical twins.<ref>Daugman, John. “Iris Recognition: The Colored Part of the Eye Contains Delicate Patterns That Vary Randomly from Person to Person, Offering a Powerful Means of Identification.” American Scientist, vol. 89, no. 4, 2001, pp. 326–333. JSTOR, www.jstor.org/stable/27857501.</ref> Facial features may also change over time due to aging which reduces the accuracy of facial recognition technology overtime without adjustments and regular adjustments. Moreover, facial cosmetic surgery may make face recognition inaccurate and require additional adjustments. In 2018 alone, there were over 3 million facial cosmetic surgery procedures<ref>“Leading Surgical Cosmetic Procedures Globally 2017 | Statistic.” Statista, www.statista.com/statistics/293437/leading-surgical-cosmetic-procedures/.</ref> | |
| + | |||
| + | In addition to facial cosmetic surgery, there are also multiple ways of altering one’s fingerprints which creates an opportunity for ill-intentioned actors to successfully sneak through security checkpoints. According to a report in Forensic magazine, the FBI has caught hundreds of suspects who tried to alter their distinctive marks at their fingertips by deep cuts, burning, biting, or using sandpaper to avoid identification.<ref>Augenstein, Seth. “FBI Warns About Altered Fingerprints.” Forensic Magazine, 14 June 2016, www.forensicmag.com/article/2015/05/fbi-warns-about-altered-fingerprints.</ref> Genotypic and phenotypic methods have limitations on biometric performance, where genetic penetrance describes heritability of factors or "the extent to which the features expressed are genetically determined." For example, blood group and DNA sequence would fall under genotypic features. Phenotypic describes what genes are expressed, such as fingerprints and iris patterns. These influence two error rates, genotypic error rate, and phenotypic error rate, where theres concerns with genotypic penetrance causes a high false positive rate and phenotypic features from cause a high false negative rate.<ref>Daugman, MSU, Recognizing Persons By Their Iris Patterns http://www.cse.msu.edu/~stockman/Book/projects.html/F09Docs/Readings/daugemanRecognizingPersons.pdf</ref>. | ||
=== Remote Scan === | === Remote Scan === | ||
| − | Iris recognition | + | [[File:Iris-vs-fingerprint.jpg|250x250px|thumbnail|<ref name = "bayo">Thakkar, Danny. “Iris Recognition Scanners vs. Fingerprint Scanners.” Bayometric, Bayometric, 15 Aug. 2018, www.bayometric.com/iris-recognition-scanners-vs-fingerprint-scanners/</ref>]] |
| + | The way that the iris is scanned makes iris recognition technologies more efficient than other facial recognition software. While an iris scanner only needs to convert iris patterns to data and can do so at a considerable distance, face recognition demands close-proximity in order to scan many facial parts to collect essential features, and fingerprint detection requires people to physically press their fingers onto the machines. Iris recognition is only getting more remote. Researchers at Carnegie Mellon University have increased the distance from which iris recognition is able to work to more than ten meters away from a moving subject. This means that, in the future, it is very possible that an iris recognition [http://si410wiki.sites.uofmhosting.net/index.php/Surveillance_Technologies surveillance camera] can easily identify people from a far distance: as they walk through an airport or glance into a rear-view mirror while driving.<ref name="a">Stone, Jeff. “Iris Scanners, Widely Used By US Military, Could Be Coming To A Police Department Near You.” International Business Times, 12 May 2015, www.ibtimes.com/iris-scanners-widely-used-us-military-could-be-coming-police-department-near-you-1917018.</ref> | ||
| + | |||
| + | ===User Friendly=== | ||
| + | Iris recognition offers a lot of advantage in terms of usability and user experience. The process is non intrusive, meaning the user has no direct contact with any part of the machine that scans the eye. An individual only needs to stand in front of a camera in order for the scanning to occur. Along with this, after the initial enrollment, scanning and recognition is a process that only takes seconds. Lastly the process allows for a variety of individuals to use it regardless of problems with eyesight. Neither glasses nor contact lenses affect the ability for the scanning or recognition to occur. | ||
| + | |||
| + | ===Iris Recognition vs. Fingerprinting === | ||
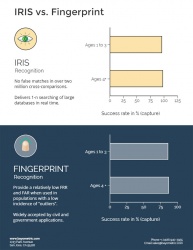
| + | Iris and fingerprint scanners are both popular biometric methods used for security purposes, specifically to confirm one’s identity. Both fingerprinting and iris recognition are accurate and reliable methods because they rely on unique features to every individual <ref name = "bayo"/>. Fingerprint scanners are generally more affordable and therefore are more common on personal devices. However, in regards to security, iris scanners are more favorable than fingerprinting <ref name = "bio"> Hassan, Mehedi, et al. “Iris Recognition Is Most Accurate Biometric Modality.” M2SYS Blog On Biometric Technology, 5 Feb. 2019, www.m2sys.com/blog/biometric-hardware/reliable-biometric-modality/.</ref>. The iris is more accurate because it remains the same throughout a person’s life, even when a person ages. The patterns that make up the iris are intricate and detailed, making it difficult to copy <ref name = "bio"/>. Alternatively, fingerprint results can be negatively effected due to skin type, environment, and age <ref name = "bio"/>. Although difficult, fingerprinting is also easier to replicate. In addition, Iris recognition is more preferable because it is cleaner since no physical contact is necessary to acquire the results <ref name = "bio"/>. | ||
| + | |||
| + | ==Technological Failures== | ||
| + | ===Iris Recognition Immigration System (IRIS)=== | ||
| + | The Iris Recognition Immigration System (IRIS) was initially implemented in the UK in 2004 to increase airport security efficiency and convenience by utilizing the up and coming iris recognition technology. | ||
| + | Though there were various qualifications that participating individuals needed to satisfy before registering with IRIS, (such as being 18 years or older, being a passenger from the U.S., Canada, Japan, New Zealand or Australia, and being a frequent traveler to the UK), the actual registration process involved biennially photographing each eye to document the unique iris patterns.<ref>"Gray, Michelle. “Iris Recognition Immigration System (IRIS).” Wayback Machine, Crown Copyright, 24 Sept. 2013, web.archive.org/web/20140109063540/http://www.ukba.homeoffice.gov.uk/customs-travel/Enteringtheuk/usingiris/."</ref> Under this program, foreign travelers in UK airports registered through IRIS were able to, in theory, bypass the standard passport presentation queue, and instead be granted clearance with an eye scan. However, despite a reported cost of 9 million euros invested into IRIS, the implementation of the program lacked the accuracy that it needed to be effective, considering that false rejections occurred with up to 10% of users.<ref>"Reporter, Daily Mail. “Iris Recognition Scheme in Airports Is Scrapped after Eight Years.” Daily Mail Online, Associated Newspapers, 17 Feb. 2012, www.dailymail.co.uk/travel/article-2102489/Iris-recognition-scheme-airports-scrapped-years.html."</ref> Consequentially, IRIS was decommissioned in 2013, replaced with a face recognition alternative through the use of biometric e-Passports,<ref>"“Eye Scanners at England Airports Turned Off.” BBC News, BBC, 16 Feb. 2012, www.bbc.com/news/uk-england-17058448."</ref> and ultimately amounted to an expensive failure. | ||
| + | |||
==Ethical Issues == | ==Ethical Issues == | ||
=== Identity === | === Identity === | ||
| − | Due to the high accuracy of iris recognition, many countries including the UK and the United Arab States are currently using this technology as a national ID for citizens and as a passport for travelers. Like Wikipedia bots and cyborgs, which combat vandalism more effectively than humans (though they also can create chaos when | + | Due to the high accuracy of iris recognition, many countries including the UK and the United Arab States are currently using this technology as a national ID for citizens and as a passport for travelers. Like Wikipedia bots and [[Wikipedia:Cyborg|cyborgs]], which combat vandalism more effectively than humans (though they also can create chaos when inappropriately taken advantage of by malicious users), the high accuracy of iris recognition brings about serious consequences such as the ease of identity theft by using high-resolution photos of someone else's iris.<ref>Halfaker, Aaron, and John Riedl. “Bots and Cyborgs: Wikipedia's Immune System.” Computer, vol. 45, no. 3, 2012, pp. 79–82., doi:10.1109/mc.2012.82.</ref> It is very likely that iris recognition will become a substitute for other legal documents - like drivers’ licenses - and will be applied to any situation that requires ID. |
| + | |||
| + | Because iris recognition identifies individuals based on an unchangeable aspect of their physical identity, it proves to be extremely difficult for individuals to circumvent security checkpoints. Preventing iris alterations may restrict autonomy and may violate individual privacy despite the possible benefits of security enforcement.<ref>Information Technology and Moral Philosophy "Plural Selves and Relational Identity" Dean Docking 2008</ref>. In addition, iris recognition causes us to question whether our informational privacy is being violated by allowing companies to collect highly valuable data that contributes to the construction of a human identity. By permitting organizations to store data on our irises, we are sacrificing part of our autonomy and control over the private information collected. If organizations want to continue with this practice, a more transparent explanation on the benefits of iris recognition and how participants' privacy will be protected needs to be produced for each case. | ||
=== Privacy === | === Privacy === | ||
[[File:Military-iris-scanner.jpg|thumbnail|right|iris recognition used by the U.S. military in Afghanistan<ref name="a"/>]] | [[File:Military-iris-scanner.jpg|thumbnail|right|iris recognition used by the U.S. military in Afghanistan<ref name="a"/>]] | ||
| − | Until recently, iris recognition has been used mainly by | + | Until recently, iris recognition has been used mainly by the U.S. military to identify captives taken from foreign battlefields, police departments to surveil law-breakers, the Department of Homeland Security to spot suspects on watch lists, law enforcement at borders to identify smugglers, and terrorists.<ref name="a"/> As more iris data is collected, and commercial iris scanners become cheaper and more accessible, iris scanning could be utilized for privacy intrusions. It may be possible that simple exposure to street cameras may provide governmental organizations and/or large corporations with each passerby's identity, acquaintances, daily routines, and other valuable pieces of information.<ref>Meyer, Robinson. “Long-Range Iris Scanning Is Here (and It's Creepy).” The Atlantic, Atlantic Media Company, 13 May 2015, www.theatlantic.com/technology/archive/2015/05/long-range-iris-scanning-is-here/393065/.</ref> Such a use of this technology would be dangerous in the hands of organizations, governments, and malicious actors that may want to hurt, control or impinge upon the right to privacy of individuals and/or groups. Furthermore, with the improvement of resolution techniques, it could be possible to use iris recognition to match and combine someone's online and offline identities. For example, how they identify strangers by using face recognition and photos on Facebook in the paper "Face Recognition and Privacy in the Age of Augmented Reality". This sort of technology is increasingly blurring the line between people's life online and offline, and calls for our attention in solving the rising privacy matters.<ref>Acquisti, A., R. Gross, and F. Stutzman. “Face Recognition and Privacy in the Age of Augmented Reality”. Journal of Privacy and Confidentiality, Vol. 6, no. 2, Dec. 2014, doi:10.29012/jpc.v6i2.638.</ref> |
=== Consent === | === Consent === | ||
| − | + | From a security point of view, iris records help police keep track of specific suspects who are attempting to escape from charges. However, the data could be used to track defendants even after the charge is dropped or the case is closed. The United States' New York City police department faced criticism in 2010 when reports were released stating that some police officers would hold detainees longer than necessary because those people refused to have their iris photographs taken.<ref>Moynihan, Colin. “Some Who Decline an Optional Iris Photo Are Kept Longer in Jail, Critics Say.” The New York Times, The New York Times, 13 Feb. 2012, www.nytimes.com/2012/02/13/nyregion/new-objections-to-nypds-iris-photographing-program.html.</ref> The ethical issue of collecting iris data without consent is further complicated by the lack of transparency that governments and organizations often employ when handling such data. Companies and legislation that fail to provide transparency or fail to effectively protect iris data prevent individuals from exerting control over their personal data and from consenting to the dissemination of that information.<ref>Turilli, M. & Floridi, L., "The ethics of information transparency", March 2009, p. 105-112</ref> Transparency enables the ethical concern of consent to persist among biometric identifiers, but groups like the Federal Trade Commission (FTC) have made efforts to improve this problem. In 2012, the FTC issued a report with recommended principles for companies and organizations to adopt such as practices related to the transparent information collection and use, the inclusion of privacy protections during product development, and providing consumers with more contextualized and timely information regarding the collection of their personal data.<ref>United States Government Accountability Office, [https://www.gao.gov/assets/680/671764.pdf "Facial Recognition Technology"], July 2015, p. 23-24</ref> | |
| + | |||
| + | It is also possible to conduct an iris scan without the knowledge or consent of an individual - with minimal difficulty. With an infrared camera, contact lenses, and a printer, a person wishing to forge someone's iris scan could take a photo of the victim's face from a medium distance, print a high-resolution image of the individual's eyes, and put contact lenses over the print to mimic their eye. Using this method, a research group in Germany was able to unlock the Samsung Galaxy 8 smartphone, which gives users the option to protect their phones through an iris scan unlocking mechanism<ref>media.ccc.de. YouTube, YouTube, 23 May 2017, www.youtube.com/watch?v=gtQ4yzbsi-c.</ref>. This provides an outlet for people with malicious intent to be able to steal someone's identity with relative ease and use it to their advantage. Given that iris recognition technology is currently the highest form of security, a breach to this privacy could be devastating to the victim. | ||
| + | |||
| + | === Design Bias === | ||
| + | With the creation of iris recognition software comes many assumptions among the creators about the users of these products. In the minds of the creators most likely from first-world countries, people will easily be able to walk up to an iris recognition device and be able to scan their eye in order to be given access to some sort of service. Unfortunately, this comes with the assumption of several things some of those being their eyes are clean and they have eyes, to begin with. When an ATM or another service is implemented with an iris recognition device as apart of it, it is important that all people can use these types of devices. In certain countries, many people are not able to clean themselves daily and thus have difficulty using iris recognition devices since the eye may not be able to be recognized due to dirt and other substances<ref>“Biometric Recognition: Challenges and Opportunities.” The National Academies Press, www.nap.edu/.</ref>. This type of difficulty is important to recognize since as in the future more and more iris recognition devices are going to be implemented with these services in order to maintain security, however when assuming certain assumptions these services start to discriminate against those that do not meet the presumed assumptions of the creators. | ||
== Reference == | == Reference == | ||
Latest revision as of 15:20, 28 April 2019
Iris recognition is a biometric verification method that utilizes the unique pattern of an individual's iris, the colored circular structure in the eye, to confirm one’s identity. The authentication process begins by scanning an iris at a reasonable distance with near-infrared light to construct a template and comparing the acquired template to the individual's already existing templates in a database[1].
Similar to face recognition and fingerprinting, iris recognition uses human biological characteristics to distinguish one person from another for security purposes and efficiency. It is sometimes preferred over both face recognition and fingerprinting techniques due to the more unique structural attributes of the iris. As iris recognition is becoming more widely used, ethical concerns of identity, privacy, and consent regarding the issue have arisen.

Contents
History
John Daugman is the first person credited with creating iris recognition algorithms with the ability to be used in new technologies. In his paper, "How iris recognition works", his statistical analysis of iris patterns successfully distinguished and identified individuals and with high accuracy[3]. These findings paved the way for iris recognition technologies to be used by companies across different industries. Currently, the companies Iris ID Systems, CMITECH, Princeton Identity, Sensor Access Technology, Argus Global Limited, and EFG GZ all specialize in recognition technology utilizing some version of these iris identification algorithms[4].
Since the adoption of iris recognition technology and the value of being able to produce it has risen, iris recognition has found many different usages with potential for monetary gains. Banks and various financial institutions have implemented iris scanning over other more traditional forms of authentication due to its convenience and higher level of security[5]. Phone companies like Samsung have even employed iris scanning as a means of accessing one's phone. This technology has also been found to be increasingly helpful in law and border enforcement agencies, which prioritize quick and correct identification of individuals.[5].
Examples
TSB Bank in the United Kingdom was one of the first banks, in September 2016, to incorporate Iris Recognition into their day to day banking operations. In order to log into the TSB application, you are now able to just glance at your mobile device. Iris Recognition is the next step in login technology after mobile fingerprints. Compared to the four traits the fingerprint scans for, Iris recognition is able to recognize two hundred and sixty-six traits, making it much more accurate than fingerprint scanning. [6]
Apple's iPhone XR includes a facial recognition software which incorporates iris recognition. Like the banks' technology, you no longer have to touch your phone to utilize the device. While facial recognition, used also by companies like Facebook and social media platforms, extends beyond iris recognition, the line between the two is being crossed as iris recognition has shown to be more accurate.
Country border controls also have the ability to utilize this technology. The United Arab Emirates employs this when any passengers enter through air, land or sea. [7]
Airport Security is now utilizing iris recognition. A company called Clear has come into play in airports in attempts to simplify and save time. Customer's eyes are scanned as a means of identity verification, saving them the time of having to take out their ID and have it checked by a TSA officer.[8]
Major League Baseball games are now using this similar technology after partnering with Clear. Just as Clear is used in airports so that travelers can skip long lines, the same is going for MLB games. People can also use this technology as age verification to purchase alcohol in some stadiums. [8]
Google uses Iris Scanning as a component of its security measures used to secure its Data Centers.[9]
FBI is increasing its use for iris recognition for criminal investigations. Acting director of the FBI’s Criminal Justice Information Services Division, Kimberly Del Greco, has announced that the FBI Criminal Justice Information Services Division (CJIS) has been given permission to look further into expanding iris recognition technology. Previously, there was only a pilot program for this kind of technology. Next Generation Identification is where the FBI keeps fingerprint and facial records. The department wishes to eventually move iris recognition into the NGI soon. The argument for using this sort of technology is that fingerprints are not always at crime scenes, so with some improved technology, a person's eye could reveal crucial information using cameras. Leslie Cavis, from the FBI, has said that “There are people who are threats to our country, and we need to do everything that we can to circumvent those threats. Biometrics is helping us to do that in a major way.” [10]
How Iris Recognition Works
Iris recognition is a biometric identification method that uses mathematical techniques in order to recognize patters on video images. Iris recognition works in two stages:
- Enrollment. The enrollment process is the first step in iris recognition and requires an individual to stand in front of a camera that digitally photographs their iris with a combination of ordinary light and invisible infrared light. The infrared light is an important step due the fact that the light is able to pick up on features of the eye that cannot be properly done with ordinary light. After eliminating unnecessary aspects of the photo, such as eyelashes, the computer system analyzes 240 distinct features that make every iris unique. This data is then stored into a database with other identifying information about you.
- Verification. The verification process occurs when an individual stands in front of a scanner in order to verify identification. The scanner takes a photograph of your eyes and extracts a number code that it can compare to other codes in its database. If your scan data is the same as the data that is in the database, you pass the scan, but if it is not, then you fail.
Advantages
High Accuracy Versus Other Biometric Methods
Iris recognition is not guaranteed to be entirely correct or effective every time. Factors like lighting and different algorithms may affect accuracy. However, there is less room for deceit because it is more difficult to alter iris than other body parts. Iris traits are more permanent and stable.[11] An additional advantage of iris recognition technology is that it can also be used even when contacts are in or glasses are on.
Facial recognition has a high-error rate because facial features change across different environmental conditions and there can be almost exact faces existing among people such as identical twins.[12] Facial features may also change over time due to aging which reduces the accuracy of facial recognition technology overtime without adjustments and regular adjustments. Moreover, facial cosmetic surgery may make face recognition inaccurate and require additional adjustments. In 2018 alone, there were over 3 million facial cosmetic surgery procedures[13]
In addition to facial cosmetic surgery, there are also multiple ways of altering one’s fingerprints which creates an opportunity for ill-intentioned actors to successfully sneak through security checkpoints. According to a report in Forensic magazine, the FBI has caught hundreds of suspects who tried to alter their distinctive marks at their fingertips by deep cuts, burning, biting, or using sandpaper to avoid identification.[14] Genotypic and phenotypic methods have limitations on biometric performance, where genetic penetrance describes heritability of factors or "the extent to which the features expressed are genetically determined." For example, blood group and DNA sequence would fall under genotypic features. Phenotypic describes what genes are expressed, such as fingerprints and iris patterns. These influence two error rates, genotypic error rate, and phenotypic error rate, where theres concerns with genotypic penetrance causes a high false positive rate and phenotypic features from cause a high false negative rate.[15].
Remote Scan
The way that the iris is scanned makes iris recognition technologies more efficient than other facial recognition software. While an iris scanner only needs to convert iris patterns to data and can do so at a considerable distance, face recognition demands close-proximity in order to scan many facial parts to collect essential features, and fingerprint detection requires people to physically press their fingers onto the machines. Iris recognition is only getting more remote. Researchers at Carnegie Mellon University have increased the distance from which iris recognition is able to work to more than ten meters away from a moving subject. This means that, in the future, it is very possible that an iris recognition surveillance camera can easily identify people from a far distance: as they walk through an airport or glance into a rear-view mirror while driving.[17]
User Friendly
Iris recognition offers a lot of advantage in terms of usability and user experience. The process is non intrusive, meaning the user has no direct contact with any part of the machine that scans the eye. An individual only needs to stand in front of a camera in order for the scanning to occur. Along with this, after the initial enrollment, scanning and recognition is a process that only takes seconds. Lastly the process allows for a variety of individuals to use it regardless of problems with eyesight. Neither glasses nor contact lenses affect the ability for the scanning or recognition to occur.
Iris Recognition vs. Fingerprinting
Iris and fingerprint scanners are both popular biometric methods used for security purposes, specifically to confirm one’s identity. Both fingerprinting and iris recognition are accurate and reliable methods because they rely on unique features to every individual [16]. Fingerprint scanners are generally more affordable and therefore are more common on personal devices. However, in regards to security, iris scanners are more favorable than fingerprinting [18]. The iris is more accurate because it remains the same throughout a person’s life, even when a person ages. The patterns that make up the iris are intricate and detailed, making it difficult to copy [18]. Alternatively, fingerprint results can be negatively effected due to skin type, environment, and age [18]. Although difficult, fingerprinting is also easier to replicate. In addition, Iris recognition is more preferable because it is cleaner since no physical contact is necessary to acquire the results [18].
Technological Failures
Iris Recognition Immigration System (IRIS)
The Iris Recognition Immigration System (IRIS) was initially implemented in the UK in 2004 to increase airport security efficiency and convenience by utilizing the up and coming iris recognition technology. Though there were various qualifications that participating individuals needed to satisfy before registering with IRIS, (such as being 18 years or older, being a passenger from the U.S., Canada, Japan, New Zealand or Australia, and being a frequent traveler to the UK), the actual registration process involved biennially photographing each eye to document the unique iris patterns.[19] Under this program, foreign travelers in UK airports registered through IRIS were able to, in theory, bypass the standard passport presentation queue, and instead be granted clearance with an eye scan. However, despite a reported cost of 9 million euros invested into IRIS, the implementation of the program lacked the accuracy that it needed to be effective, considering that false rejections occurred with up to 10% of users.[20] Consequentially, IRIS was decommissioned in 2013, replaced with a face recognition alternative through the use of biometric e-Passports,[21] and ultimately amounted to an expensive failure.
Ethical Issues
Identity
Due to the high accuracy of iris recognition, many countries including the UK and the United Arab States are currently using this technology as a national ID for citizens and as a passport for travelers. Like Wikipedia bots and cyborgs, which combat vandalism more effectively than humans (though they also can create chaos when inappropriately taken advantage of by malicious users), the high accuracy of iris recognition brings about serious consequences such as the ease of identity theft by using high-resolution photos of someone else's iris.[22] It is very likely that iris recognition will become a substitute for other legal documents - like drivers’ licenses - and will be applied to any situation that requires ID.
Because iris recognition identifies individuals based on an unchangeable aspect of their physical identity, it proves to be extremely difficult for individuals to circumvent security checkpoints. Preventing iris alterations may restrict autonomy and may violate individual privacy despite the possible benefits of security enforcement.[23]. In addition, iris recognition causes us to question whether our informational privacy is being violated by allowing companies to collect highly valuable data that contributes to the construction of a human identity. By permitting organizations to store data on our irises, we are sacrificing part of our autonomy and control over the private information collected. If organizations want to continue with this practice, a more transparent explanation on the benefits of iris recognition and how participants' privacy will be protected needs to be produced for each case.
Privacy

Until recently, iris recognition has been used mainly by the U.S. military to identify captives taken from foreign battlefields, police departments to surveil law-breakers, the Department of Homeland Security to spot suspects on watch lists, law enforcement at borders to identify smugglers, and terrorists.[17] As more iris data is collected, and commercial iris scanners become cheaper and more accessible, iris scanning could be utilized for privacy intrusions. It may be possible that simple exposure to street cameras may provide governmental organizations and/or large corporations with each passerby's identity, acquaintances, daily routines, and other valuable pieces of information.[24] Such a use of this technology would be dangerous in the hands of organizations, governments, and malicious actors that may want to hurt, control or impinge upon the right to privacy of individuals and/or groups. Furthermore, with the improvement of resolution techniques, it could be possible to use iris recognition to match and combine someone's online and offline identities. For example, how they identify strangers by using face recognition and photos on Facebook in the paper "Face Recognition and Privacy in the Age of Augmented Reality". This sort of technology is increasingly blurring the line between people's life online and offline, and calls for our attention in solving the rising privacy matters.[25]
Consent
From a security point of view, iris records help police keep track of specific suspects who are attempting to escape from charges. However, the data could be used to track defendants even after the charge is dropped or the case is closed. The United States' New York City police department faced criticism in 2010 when reports were released stating that some police officers would hold detainees longer than necessary because those people refused to have their iris photographs taken.[26] The ethical issue of collecting iris data without consent is further complicated by the lack of transparency that governments and organizations often employ when handling such data. Companies and legislation that fail to provide transparency or fail to effectively protect iris data prevent individuals from exerting control over their personal data and from consenting to the dissemination of that information.[27] Transparency enables the ethical concern of consent to persist among biometric identifiers, but groups like the Federal Trade Commission (FTC) have made efforts to improve this problem. In 2012, the FTC issued a report with recommended principles for companies and organizations to adopt such as practices related to the transparent information collection and use, the inclusion of privacy protections during product development, and providing consumers with more contextualized and timely information regarding the collection of their personal data.[28]
It is also possible to conduct an iris scan without the knowledge or consent of an individual - with minimal difficulty. With an infrared camera, contact lenses, and a printer, a person wishing to forge someone's iris scan could take a photo of the victim's face from a medium distance, print a high-resolution image of the individual's eyes, and put contact lenses over the print to mimic their eye. Using this method, a research group in Germany was able to unlock the Samsung Galaxy 8 smartphone, which gives users the option to protect their phones through an iris scan unlocking mechanism[29]. This provides an outlet for people with malicious intent to be able to steal someone's identity with relative ease and use it to their advantage. Given that iris recognition technology is currently the highest form of security, a breach to this privacy could be devastating to the victim.
Design Bias
With the creation of iris recognition software comes many assumptions among the creators about the users of these products. In the minds of the creators most likely from first-world countries, people will easily be able to walk up to an iris recognition device and be able to scan their eye in order to be given access to some sort of service. Unfortunately, this comes with the assumption of several things some of those being their eyes are clean and they have eyes, to begin with. When an ATM or another service is implemented with an iris recognition device as apart of it, it is important that all people can use these types of devices. In certain countries, many people are not able to clean themselves daily and thus have difficulty using iris recognition devices since the eye may not be able to be recognized due to dirt and other substances[30]. This type of difficulty is important to recognize since as in the future more and more iris recognition devices are going to be implemented with these services in order to maintain security, however when assuming certain assumptions these services start to discriminate against those that do not meet the presumed assumptions of the creators.
Reference
- ↑ Wildes, Richard. Iris Recognition: an Emerging Biometric Technology - IEEE Journals & Magazine, Sept. 1997, ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=628669.
- ↑ Thakkar, Danny. “Retinal vs. Iris Recognition: Your Eyes Can Get You Identified?” Bayometric, Bayometric, 8 Aug. 2018, www.bayometric.com/retinal-vs-iris-recognition/.
- ↑ J. Daugman, "How iris recognition works," in IEEE Transactions on Circuits and Systems for Video Technology, vol. 14, no. 1, pp. 21-30, Jan. 2004. doi: 10.1109/TCSVT.2003.818350
- ↑ "Iris Recognition". IFSEC Global Directory. https://directory.ifsecglobal.com/iris-recognition-code004809.html
- ↑ 5.0 5.1 Thakkar, Danny. “Biometric Iris Recognition and Its Application.” Bayometric, Bayometric, 15 Aug. 2018, www.bayometric.com/biometric-iris-recognition-application/.
- ↑ "TSB to roll out iris scanning tech" Rory Cellan-Jones, July 20 2016. https://www.bbc.com/news/technology-40663365
- ↑ "IRIS RECOGNITION BORDER-CROSSING SYSTEM IN THE UAE"https://trid.trb.org/view/741851
- ↑ 8.0 8.1 "A Full Guide to Clear Airport Security: How It Works and Where You Can Use it" https://www.travelandleisure.com/airlines-airports/clear-airport-security
- ↑ "Security and Data Protection in a Google Data Center ", G Suite's Official YouTube https://www.youtube.com/watch?v=cLory3qLoY8
- ↑ Young, Charles. “FBI to Expand Iris Recognition Tech at Clarksburg, WV Campus.” WV News, 20 Apr. 2019, www.wvnews.com/news/wvnews/fbi-to-expand-iris-recognition-tech-at-clarksburg-wv-campus/article_d7d13a6d-d217-54c2-bce1-e80168c8f71b.html.
- ↑ Jain, Anil K., and Sharath Pankanti. “BEYOND FINGERPRINTING.” Scientific American, vol. 299, no. 3, 2008, pp. 78–81. JSTOR, www.jstor.org/stable/26000805.
- ↑ Daugman, John. “Iris Recognition: The Colored Part of the Eye Contains Delicate Patterns That Vary Randomly from Person to Person, Offering a Powerful Means of Identification.” American Scientist, vol. 89, no. 4, 2001, pp. 326–333. JSTOR, www.jstor.org/stable/27857501.
- ↑ “Leading Surgical Cosmetic Procedures Globally 2017 | Statistic.” Statista, www.statista.com/statistics/293437/leading-surgical-cosmetic-procedures/.
- ↑ Augenstein, Seth. “FBI Warns About Altered Fingerprints.” Forensic Magazine, 14 June 2016, www.forensicmag.com/article/2015/05/fbi-warns-about-altered-fingerprints.
- ↑ Daugman, MSU, Recognizing Persons By Their Iris Patterns http://www.cse.msu.edu/~stockman/Book/projects.html/F09Docs/Readings/daugemanRecognizingPersons.pdf
- ↑ 16.0 16.1 Thakkar, Danny. “Iris Recognition Scanners vs. Fingerprint Scanners.” Bayometric, Bayometric, 15 Aug. 2018, www.bayometric.com/iris-recognition-scanners-vs-fingerprint-scanners/
- ↑ 17.0 17.1 17.2 Stone, Jeff. “Iris Scanners, Widely Used By US Military, Could Be Coming To A Police Department Near You.” International Business Times, 12 May 2015, www.ibtimes.com/iris-scanners-widely-used-us-military-could-be-coming-police-department-near-you-1917018.
- ↑ 18.0 18.1 18.2 18.3 Hassan, Mehedi, et al. “Iris Recognition Is Most Accurate Biometric Modality.” M2SYS Blog On Biometric Technology, 5 Feb. 2019, www.m2sys.com/blog/biometric-hardware/reliable-biometric-modality/.
- ↑ "Gray, Michelle. “Iris Recognition Immigration System (IRIS).” Wayback Machine, Crown Copyright, 24 Sept. 2013, web.archive.org/web/20140109063540/http://www.ukba.homeoffice.gov.uk/customs-travel/Enteringtheuk/usingiris/."
- ↑ "Reporter, Daily Mail. “Iris Recognition Scheme in Airports Is Scrapped after Eight Years.” Daily Mail Online, Associated Newspapers, 17 Feb. 2012, www.dailymail.co.uk/travel/article-2102489/Iris-recognition-scheme-airports-scrapped-years.html."
- ↑ "“Eye Scanners at England Airports Turned Off.” BBC News, BBC, 16 Feb. 2012, www.bbc.com/news/uk-england-17058448."
- ↑ Halfaker, Aaron, and John Riedl. “Bots and Cyborgs: Wikipedia's Immune System.” Computer, vol. 45, no. 3, 2012, pp. 79–82., doi:10.1109/mc.2012.82.
- ↑ Information Technology and Moral Philosophy "Plural Selves and Relational Identity" Dean Docking 2008
- ↑ Meyer, Robinson. “Long-Range Iris Scanning Is Here (and It's Creepy).” The Atlantic, Atlantic Media Company, 13 May 2015, www.theatlantic.com/technology/archive/2015/05/long-range-iris-scanning-is-here/393065/.
- ↑ Acquisti, A., R. Gross, and F. Stutzman. “Face Recognition and Privacy in the Age of Augmented Reality”. Journal of Privacy and Confidentiality, Vol. 6, no. 2, Dec. 2014, doi:10.29012/jpc.v6i2.638.
- ↑ Moynihan, Colin. “Some Who Decline an Optional Iris Photo Are Kept Longer in Jail, Critics Say.” The New York Times, The New York Times, 13 Feb. 2012, www.nytimes.com/2012/02/13/nyregion/new-objections-to-nypds-iris-photographing-program.html.
- ↑ Turilli, M. & Floridi, L., "The ethics of information transparency", March 2009, p. 105-112
- ↑ United States Government Accountability Office, "Facial Recognition Technology", July 2015, p. 23-24
- ↑ media.ccc.de. YouTube, YouTube, 23 May 2017, www.youtube.com/watch?v=gtQ4yzbsi-c.
- ↑ “Biometric Recognition: Challenges and Opportunities.” The National Academies Press, www.nap.edu/.